|
Need To Know (Nicki Bluhm Album)
The term "need to know", when used by government and other organizations (particularly those related to the military or espionage), describes the restriction of data which is considered very sensitive. Under need-to-know restrictions, even if one has all the necessary official approvals (such as a security clearance) to access certain information, one would not be given access to such information, or read into a clandestine operation, unless one has a specific ''need to know''; that is, access to the information must be necessary for one to conduct one's official duties. This term also includes anyone that the people with the knowledge deemed necessary to share it with. As with most security mechanisms, the aim is to make it difficult for unauthorized access to occur, without inconveniencing legitimate access. Need-to-know also aims to discourage "browsing" of sensitive material by limiting access to the smallest possible number of people. Examples The Battle of Normandy in 1944 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Government
A government is the system or group of people governing an organized community, generally a state. In the case of its broad associative definition, government normally consists of legislature, executive, and judiciary. Government is a means by which organizational policies are enforced, as well as a mechanism for determining policy. In many countries, the government has a kind of constitution, a statement of its governing principles and philosophy. While all types of organizations have governance, the term ''government'' is often used more specifically to refer to the approximately 200 independent national governments and subsidiary organizations. The major types of political systems in the modern era are democracies, monarchies, and authoritarian and totalitarian regimes. Historically prevalent forms of government include monarchy, aristocracy, timocracy, oligarchy, democracy, theocracy, and tyranny. These forms are not always mutually exclusive, and m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Discretionary Access Control
In computer security, discretionary access control (DAC) is a type of access control In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process. The act of ''accessing'' may mean consuming ... defined by the Trusted Computer System Evaluation Criteria (TCSEC) as a means of restricting access to objects based on the identity of subjects and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission (perhaps indirectly) on to any other subject (unless restrained by mandatory access control). Discretionary access control is commonly discussed in contrast to mandatory access control (MAC). Occasionally, a system as a whole is said to have "discretionary" or "purely discretionary" access control when that system lacks mandatory access co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Through Obscurity
Security through obscurity (or security by obscurity) is the reliance in security engineering on design or implementation secrecy as the main method of providing security to a system or component. History An early opponent of security through obscurity was the locksmith Alfred Charles Hobbs, who in 1851 demonstrated to the public how state-of-the-art locks could be picked. In response to concerns that exposing security flaws in the design of locks could make them more vulnerable to criminals, he said: "Rogues are very keen in their profession, and know already much more than we can teach them." There is scant formal literature on the issue of security through obscurity. Books on security engineering cite Kerckhoffs' doctrine from 1883, if they cite anything at all. For example, in a discussion about secrecy and openness in Nuclear Command and Control: e benefits of reducing the likelihood of an accidental war were considered to outweigh the possible benefits of secrecy. This ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Principle Of Least Privilege
In information security, computer science, and other fields, the principle of least privilege (PoLP), also known as the principle of minimal privilege (PoMP) or the principle of least authority (PoLA), requires that in a particular abstraction layer of a computing environment, every module (such as a process, a user, or a program, depending on the subject) must be able to access only the information and resources that are necessary for its legitimate purpose. Details The principle means giving a user account or process only those privileges which are essential to perform its intended function. For example, a user account for the sole purpose of creating backups does not need to install software: hence, it has rights only to run backup and backup-related applications. Any other privileges, such as installing new software, are blocked. The principle applies also to a personal computer user who usually does work in a normal user account, and opens a privileged, password protected ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
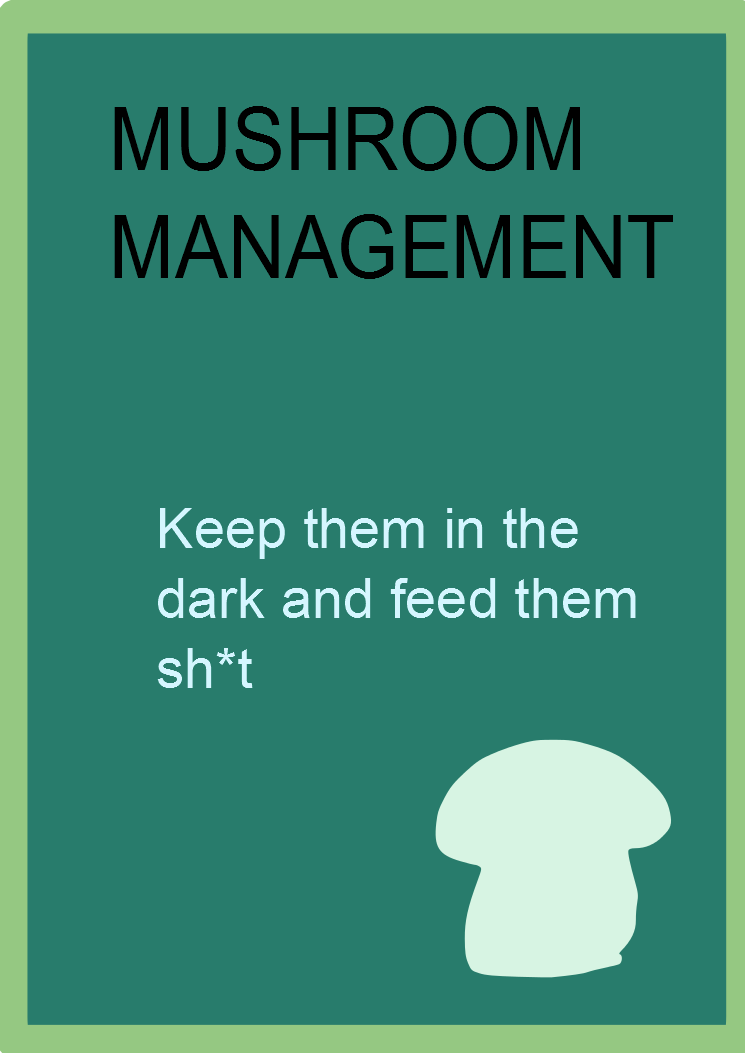
Mushroom Management
Mushroom management is the management of a company where the communication channels between the employers and the employees do not work effectively, and where employees are 'kept in the dark' by management in regards to business decisions that affect their work and employment. The term 'mushroom management' alludes to the stereotypical (and somewhat inaccurate) view of mushroom cultivation: kept in the dark and fed bullshit. Description Mushroom management is a style of management in which the personnel are not familiar with the ideas or the general state of the company, and are given work without knowing the purpose of this work, in contrast with open-book management. Mushroom management means that workers' curiosity and self-expression are not supported. The employees often have no idea what the company's overall situation is, because the leaders tend to make all the decisions on their own, without asking anyone else to give their opinion. This problem can occur when the ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Freedom Of Information Laws By Country
Freedom of information laws allow access by the general public to data held by national governments and, where applicable, by state and local governments. The emergence of freedom of information legislation was a response to increasing dissatisfaction with the secrecy surrounding government policy development and decision making. In recent years Access to Information Act has also been used. They establish a "right-to-know" legal process by which requests may be made for government-held information, to be received freely or at minimal cost, barring standard exceptions. Also variously referred to as open records, or sunshine laws (in the United States), governments are typically bound by a duty to publish and promote openness. In many countries there are constitutional guarantees for the right of access to information, but these are usually unused if specific support legislation does not exist. Additionally, the United Nations Sustainable Development Goal 16 has a target to ensure ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Compartmentalization (information Security)
Compartmentalization or compartmentalisation may refer to: * Compartmentalization (biology) * Compartmentalization (engineering) * Compartmentalization (fire protection) * Compartmentalization (information security) * Compartmentalization (psychology) * Compartmentalization of decay in trees {{Disambiguation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
User Interface
In the industrial design field of human–computer interaction, a user interface (UI) is the space where interactions between humans and machines occur. The goal of this interaction is to allow effective operation and control of the machine from the human end, while the machine simultaneously feeds back information that aids the operators' decision-making process. Examples of this broad concept of user interfaces include the interactive aspects of computer operating systems, hand tools, heavy machinery operator controls and process controls. The design considerations applicable when creating user interfaces are related to, or involve such disciplines as, ergonomics and psychology. Generally, the goal of user interface design is to produce a user interface that makes it easy, efficient, and enjoyable (user-friendly) to operate a machine in the way which produces the desired result (i.e. maximum usability). This generally means that the operator needs to provide minimal in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Graphical User Interface
The GUI ( "UI" by itself is still usually pronounced . or ), graphical user interface, is a form of user interface that allows User (computing), users to Human–computer interaction, interact with electronic devices through graphical icon (computing), icons and audio indicator such as primary notation, instead of text-based user interface, text-based UIs, typed command labels or text navigation. GUIs were introduced in reaction to the perceived steep learning curve of CLIs (command-line interfaces), which require commands to be typed on a computer keyboard. The actions in a GUI are usually performed through Direct manipulation interface, direct manipulation of the graphical elements. Beyond computers, GUIs are used in many handheld mobile devices such as MP3 players, portable media players, gaming devices, smartphones and smaller household, office and Distributed control system, industrial controls. The term ''GUI'' tends not to be applied to other lower-display resolution User ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mandatory Access Control
In computer security, mandatory access control (MAC) refers to a type of access control by which the operating system or database constrains the ability of a ''subject'' or ''initiator'' to access or generally perform some sort of operation on an ''object'' or ''target''. In the case of operating systems, a subject is usually a process or thread; objects are constructs such as files, directories, TCP/ UDP ports, shared memory segments, IO devices, etc. Subjects and objects each have a set of security attributes. Whenever a subject attempts to access an object, an authorization rule enforced by the operating system kernel examines these security attributes and decides whether the access can take place. Any operation by any subject on any object is tested against the set of authorization rules (aka ''policy'') to determine if the operation is allowed. A database management system, in its access control mechanism, can also apply mandatory access control; in this case, the objects ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operating System
An operating system (OS) is system software that manages computer hardware, software resources, and provides common daemon (computing), services for computer programs. Time-sharing operating systems scheduler (computing), schedule tasks for efficient use of the system and may also include accounting software for cost allocation of Scheduling (computing), processor time, mass storage, printing, and other resources. For hardware functions such as input and output and memory allocation, the operating system acts as an intermediary between programs and the computer hardware, although the application code is usually executed directly by the hardware and frequently makes system calls to an OS function or is interrupted by it. Operating systems are found on many devices that contain a computer from cellular phones and video game consoles to web servers and supercomputers. The dominant general-purpose personal computer operating system is Microsoft Windows with a market share of aroun ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Surely You're Joking, Mr
"Surely" is a 1995 single by British pop group Five Star. The single was a U.S. only release, available in the UK as an import. Although it missed the ''Billboard'' Hot 100 chart, it peaked at number 125 in October of that year (see 1995 in music). The song includes a rap by Junior P Junior or Juniors may refer to: Arts and entertainment Music * ''Junior'' (Junior Mance album), 1959 * ''Junior'' (Röyksopp album), 2009 * ''Junior'' (Kaki King album), 2010 * ''Junior'' (LaFontaines album), 2019 Films * ''Junior'' (1994 .... This was the first time Five Star had used a rapper on one of their songs. Track listing #Surely (Radio Mix) #Surely (Sure Funk) #Surely (Dub Mix) #Surely (Instrumental) #Surely (Album Version featuring Junior P) #Surely (Club Jam Mix featuring Junior P) References {{Five Star 1995 singles Five Star songs Songs written by Delroy Pearson Songs written by Doris Pearson ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |