|
Navidad Virus
W32.Navidad is a mass-mailing worm program or virus, discovered in December 2000 that ran on Windows 95, Windows 98, Windows NT, and Windows 2000 systems. It was designed to spread through email clients such as Microsoft Outlook while masquerading as an executable electronic Christmas card. Infected computers can be identified by blue eye icons which appear in the Windows system tray. Description When the navidad.exe email attachment is run the files installs itself as "WINSVRC.VXD" in the \Windows\System directory. The worm modifies the default EXE file startup key in the Windows Registry, KEY_CLASSES_ROOT\exefile\shell\open\command to allow the program to run any time any exe file is run. The worm also creates a startup key to ensure that it runs on startup. A bug in the Navidad virus installs the Registry Keys for "WINSVRC.EXE" even though the worm itself is installed with a .VXD file extension, as a result the worm prevents .exe files from running and does not run on sta ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Worm
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. It often uses a computer network to spread itself, relying on security failures on the target computer to access it. It will use this machine as a host to scan and infect other computers. When these new worm-invaded computers are controlled, the worm will continue to scan and infect other computers using these computers as hosts, and this behaviour will continue. Computer worms use recursive methods to copy themselves without host programs and distribute themselves based on the law of exponential growth, thus controlling and infecting more and more computers in a short time. Worms almost always cause at least some harm to the network, even if only by consuming Bandwidth (computing), bandwidth, whereas Computer virus, viruses almost always corrupt or modify files on a targeted computer. Many worms are designed only to spread, and do not attempt to change the sy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
System Tray
A taskbar is an element of a graphical user interface which has various purposes. It typically shows which programs are currently running. The specific design and layout of the taskbar varies between individual operating systems, but generally assumes the form of a strip located along one edge of the screen. On this strip are various icons which correspond to the windows open within a program. Clicking these icons allow the user to easily switch between programs or windows, with the currently active program or window usually appearing differently from the rest. In more recent versions of operating systems, users can also "pin" programs or files so that they can be accessed quickly, often with a single click. Due to its prominence on the screen, the taskbar usually also has a notification area, which uses interactive icons to display real-time information about the state of the computer system and some of the programs active on it. With the rapid development of operating systems ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
McAfee
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American global computer security software company headquartered in San Jose, California. The company was purchased by Intel in February 2011, and became part of the Intel Security division. In 2017, Intel had a strategic deal with TPG Capital and converted Intel Security into a joint venture between both companies called McAfee. Thoma Bravo took a minority stake in the new company, and Intel retained a 49% stake. The owners took McAfee public on the NASDAQ in 2020, and in 2022 an investor group led by Advent International Corporation took it private again. History 1987–1999 The company was founded in 1987 as McAfee Associates, named for its founder John McAfee, who resigned from the company in 1994. McAfee was incorporated in the state of Delaware in 1992. In 1993, McAfee stepped ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ILOVEYOU
ILOVEYOU, sometimes referred to as Love Bug or Love Letter for you, is a computer worm that infected over ten million Windows personal computers on and after 5 May 2000. It started spreading as an email message with the subject line "ILOVEYOU" and the attachment "LOVE-LETTER-FOR-YOU.TXT.vbs." At the time, Windows computers often hid the latter file extension (" VBS," a type of interpreted file) by default because it is an extension for a file type that Windows knows, leading unwitting users to think it was a normal text file. Opening the attachment activates the Visual Basic script. First, the worm inflicts damage on the local machine, overwriting random files (including Office files and image files; however, it hides MP3 files instead of deleting them), then, it copies itself to all addresses in the Windows Address Book used by Microsoft Outlook, allowing it to spread much faster than any other previous email worm. Onel de Guzman, a then-24-year-old resident of Manila, Philip ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Melissa Virus
The Melissa virus is a mass-mailing macro virus released on or around March 26, 1999. It targets Microsoft Word and Outlook-based systems and created considerable network traffic. The virus infects computers via email; the email is titled "Important Message From," followed by the current username. Upon clicking the message, the body reads, "Here's that document you asked for. Don't show anyone else ;)." Attached is a Word document titled "list.doc," containing a list of pornographic sites and accompanying logins for each. It then mass-mails itself to the first fifty people in the user's contact list and disables multiple safeguard features on Microsoft Word and Microsoft Outlook. Description The virus was released on March 26, 1999, by David L. Smith. Smith used a hijacked AOL account to post the virus onto an Internet newsgroup called "alt.sex." And it soon ended up on similar sex groups and pornographic sites before spreading to corporate networks. However, the virus itself ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Patch (computing)
A patch is a set of changes to a computer program or its supporting data designed to update, fix, or improve it. This includes fixing security vulnerabilities and other bugs, with such patches usually being called bugfixes or bug fixes. Patches are often written to improve the functionality, usability, or performance of a program. The majority of patches are provided by software vendors for operating system and application updates. Patches may be installed either under programmed control or by a human programmer using an editing tool or a debugger. They may be applied to program files on a storage device, or in computer memory. Patches may be permanent (until patched again) or temporary. Patching makes possible the modification of compiled and machine language object programs when the source code is unavailable. This demands a thorough understanding of the inner workings of the object code by the person creating the patch, which is difficult without close study of the sourc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
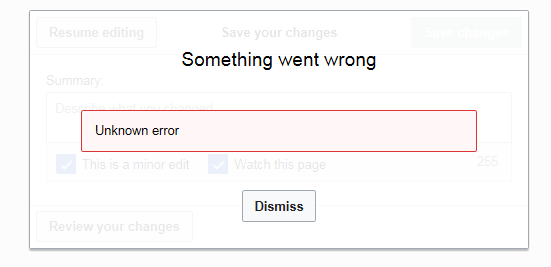
Error Message
An error message is information displayed when an unforeseen occurs, usually on a computer or other device. On modern operating systems with graphical user interfaces, error messages are often displayed using dialog boxes. Error messages are used when user intervention is required, to indicate that a desired operation has failed, or to relay important warnings (such as warning a computer user that they are almost out of hard disk space). Error messages are seen widely throughout computing, and are part of every operating system or computer hardware device. Proper design of error messages is an important topic in usability and other fields of human–computer interaction. Common error messages The following error messages are commonly seen by modern computer users: ;Access denied :This error occurs if the user doesn't have privileges to a file, or if it has been locked by some program or user. ;Device not ready :This error most often occurs when there is no floppy disk (or a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Registry Keys
The Windows Registry is a hierarchical database that stores low-level settings for the Microsoft Windows operating system and for applications that opt to use the registry. The kernel, device drivers, services, Security Accounts Manager, and user interfaces can all use the registry. The registry also allows access to counters for profiling system performance. In other words, the registry or Windows Registry contains information, settings, options, and other values for programs and hardware installed on all versions of Microsoft Windows operating systems. For example, when a program is installed, a new subkey containing settings such as a program's location, its version, and how to start the program, are all added to the Windows Registry. When introduced with Windows 3.1, the Windows Registry primarily stored configuration information for COM-based components. Windows 95 and Windows NT extended its use to rationalize and centralize the information in the profusion of INI fil ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows Registry
The Windows Registry is a hierarchical database that stores low-level settings for the Microsoft Windows operating system and for applications that opt to use the registry. The kernel, device drivers, services, Security Accounts Manager, and user interfaces can all use the registry. The registry also allows access to counters for profiling system performance. In other words, the registry or Windows Registry contains information, settings, options, and other values for programs and hardware installed on all versions of Microsoft Windows operating systems. For example, when a program is installed, a new subkey containing settings such as a program's location, its version, and how to start the program, are all added to the Windows Registry. When introduced with Windows 3.1, the Windows Registry primarily stored configuration information for COM-based components. Windows 95 and Windows NT extended its use to rationalize and centralize the information in the profusion of INI f ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Windows
Windows is a group of several Proprietary software, proprietary graphical user interface, graphical operating system families developed and marketed by Microsoft. Each family caters to a certain sector of the computing industry. For example, Windows NT for consumers, Windows Server for servers, and Windows IoT for embedded systems. Defunct Windows families include Windows 9x, Windows Mobile, and Windows Phone. The first version of Windows was released on November 20, 1985, as a graphical operating system shell for MS-DOS in response to the growing interest in graphical user interfaces (GUIs). Windows is the most popular desktop operating system in the world, with Usage share of operating systems, 75% market share , according to StatCounter. However, Windows is not the most used operating system when including both mobile and desktop OSes, due to Android (operating system), Android's massive growth. , the most recent version of Windows is Windows 11 for consumer Personal compu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Virus
A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. A computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the host program, but can run independently and actively carry out attacks. Virus writers use social engineering deceptions and exploit detailed knowledge of security vulnerabilities to initially infect systems and to spread the virus. Viruses use complex anti-detection/stealth strategies to evade antivirus software. Motives for creating viruses can inclu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Christmas Card
A Christmas card is a greeting card sent as part of the traditional celebration of Christmas in order to convey between people a range of sentiments related to Christmastide and the holiday season. Christmas cards are usually exchanged during the weeks preceding Christmas Day by many people (including some non-Christians) in Western society and in Asia. The traditional greeting reads "wishing you a Merry Christmas and a Happy New Year". There are innumerable variations on this greeting, many cards expressing more religious sentiment, or containing a poem, prayer, Christmas song lyrics or Biblical verse; others focus on the general holiday season with an all-inclusive "Season's greetings". The first modern Christmas card was by John Calcott Horsley. A Christmas card is generally commercially designed and purchased for the occasion. The content of the design might relate directly to the Christmas narrative with depictions of the Nativity of Jesus, or have Christian symbols su ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |