|
Mining Pool
In the context of cryptocurrency mining, a mining pool is the pooling of resources by miners, who share their processing power over a network, to split the reward equally, according to the amount of work they contributed to the probability of finding a block. A "share" is awarded to members of the mining pool who present a valid partial proof-of-work. Mining in pools began when the difficulty for mining increased to the point where it could take centuries for slower miners to generate a block. The solution to this problem was for miners to pool their resources so they could generate blocks more quickly and therefore receive a portion of the block reward on a consistent basis, rather than randomly once every few years. History * November 2010: Slush launched in 2010 and is the first mining pool. * 2011–2013: The era of deepbit, which at its peak held up to 45% of the network hashrate. * 2013–2014: Since the introduction of ASIC, and when deepbit failed to support the new ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptocurrency Mining
A cryptocurrency, crypto-currency, or crypto is a digital currency designed to work as a medium of exchange through a computer network that is not reliant on any central authority, such as a government or bank, to uphold or maintain it. It is a decentralized system for verifying that the parties to a transaction have the money they claim to have, eliminating the need for traditional intermediaries, such as banks, when funds are being transferred between two entities. Individual coin ownership records are stored in a digital ledger, which is a computerized database using strong cryptography to secure transaction records, control the creation of additional coins, and verify the transfer of coin ownership. Despite their name, cryptocurrencies are not considered to be currencies in the traditional sense, and while varying treatments have been applied to them, including classification as commodities, securities, and currencies, cryptocurrencies are generally viewed as a distinct a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bitcoin
Bitcoin ( abbreviation: BTC; sign: ₿) is a decentralized digital currency that can be transferred on the peer-to-peer bitcoin network. Bitcoin transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. The cryptocurrency was invented in 2008 by an unknown person or group of people using the name Satoshi Nakamoto. The currency began use in 2009, when its implementation was released as open-source software. The word "''bitcoin''" was defined in a white paper published on October 31, 2008. It is a compound of the words ''bit'' and ''coin''. The legality of bitcoin varies by region. Nine countries have fully banned bitcoin use, while a further fifteen have implicitly banned it. A few governments have used bitcoin in some capacity. El Salvador has adopted Bitcoin as legal tender, although use by merchants remains low. Ukraine has accepted cryptocurrency donations to fund the resistance to the 2022 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Money
Digital currency (digital money, electronic money or electronic currency) is any currency, money, or money-like asset that is primarily managed, stored or exchanged on digital computer systems, especially over the internet. Types of digital currencies include cryptocurrency, virtual currency and central bank digital currency. Digital currency may be recorded on a distributed database on the internet, a centralized electronic computer database owned by a company or bank, within digital files or even on a stored-value card. Digital currencies exhibit properties similar to traditional currencies, but generally do not have a classical physical form of fiat currency historically that you can directly hold in your hand, like currencies with printed banknotes or minted coins - however they do have a physical form in an unclassical sense coming from the computer to computer and computer to human interactions and the information and processing power of the servers that store and keep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digital Currency Exchanger
A cryptocurrency exchange, or a digital currency exchange (DCE), is a business that allows customers to trade cryptocurrencies or digital currencies for other assets, such as conventional fiat money or other digital currencies. Exchanges may accept credit card payments, wire transfers or other forms of payment in exchange for digital currencies or cryptocurrencies. A cryptocurrency exchange can be a market maker that typically takes the bid–ask spreads as a transaction commission for its service or, as a matching platform, simply charges fees. Some brokerages which also focus on other assets such as stocks, like Robinhood and eToro, let users purchase but not withdraw cryptocurrencies to cryptocurrency wallets. Dedicated cryptocurrency exchanges such as Binance and Coinbase do allow cryptocurrency withdrawals, however. Operation A cryptocurrency exchange can typically send cryptocurrency to a user's personal cryptocurrency wallet. Some can convert digital currency balan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptographic Protocol
A security protocol (cryptographic protocol or encryption protocol) is an abstract or concrete protocol that performs a security-related function and applies cryptographic methods, often as sequences of cryptographic primitives. A protocol describes how the algorithms should be used and includes details about data structures and representations, at which point it can be used to implement multiple, interoperable versions of a program. Cryptographic protocols are widely used for secure application-level data transport. A cryptographic protocol usually incorporates at least some of these aspects: * Key agreement or establishment * Entity authentication * Symmetric encryption and message authentication material construction * Secured application-level data transport * Non-repudiation methods * Secret sharing methods * Secure multi-party computation For example, Transport Layer Security (TLS) is a cryptographic protocol that is used to secure web (HTTPS) connections. It has a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Proof Of Space
Proof of space (PoS) is a type of consensus algorithm achieved by demonstrating one's legitimate interest in a service (such as sending an email) by allocating a non-trivial amount of memory or disk space to solve a challenge presented by the service provider. The concept was formulated in 2013 by Dziembowski ''et al.'' and (with a different formulation) by Ateniese ''et al.''. Proofs of space are very similar to proofs of work (PoW), except that instead of computation, storage is used to earn cryptocurrency. Proof-of-space is different from memory-hard functions in that the bottleneck is not in the number of memory access events, but in the amount of memory required. After the release of Bitcoin, alternatives to its PoW mining mechanism were researched, and PoS was studied in the context of cryptocurrencies. Proofs of space are seen as a fairer and greener alternative by blockchain enthusiasts due to the general-purpose nature of storage and the lower energy cost required by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NiceHash
NiceHash is a global cryptocurrency hash power broker and cryptocurrency exchange with an open marketplace that connects sellers of hashing power (cryptominers) with buyers of hashing power using the sharing economy approach. The company provides software for cryptocurrency mining. The company was founded in 2014 by two Slovenian university students, Marko Kobal and Matjaž Škorjanc. The company is based in The British Virgin Islands and has offices in Maribor, Slovenia. NiceHash users are primarily video gamers who have powerful graphics cards (GPUs) suited to cryptocurrency mining. The company has over 2.5 million users in 190 countries worldwide as of November 2021. History NiceHash was founded in 2014, a former medical student turned computer programmer, and Marko Kobal. NiceHash's original founder Matjaž Škorjanc was allegedly one of the creators of malware called Mariposa botnet and served four years and ten months in a Slovenian prison. On June 5, 2019, US law ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cloud Mining
Cloud mining is the process of cryptocurrency mining utilizing a remote datacenter with shared processing power. This type of cloud mining enables users to mine bitcoins or alternative cryptocurrencies without managing the hardware. The mining rigs are housed and maintained in a facility owned by mining company and the customer simply needs to register and purchase mining contracts or shares. Since cloud mining is provided as a service, there is generally some cost and this can result in lower returns for the miner. Types of hosting Users of hosted mining equipment can either lease a physical mining server or a virtual private server and install mining software on the machine. Instead of leasing a dedicated server, some services offer hashing power hosted in data centers for sale denominated in Gigahash/seconds (GH/s); users either select a desired amount of hashing power and a period for the contract or in some cases can trade their hashing power. See also *Mining pool In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bitcoin
Bitcoin ( abbreviation: BTC; sign: ₿) is a decentralized digital currency that can be transferred on the peer-to-peer bitcoin network. Bitcoin transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. The cryptocurrency was invented in 2008 by an unknown person or group of people using the name Satoshi Nakamoto. The currency began use in 2009, when its implementation was released as open-source software. The word "''bitcoin''" was defined in a white paper published on October 31, 2008. It is a compound of the words ''bit'' and ''coin''. The legality of bitcoin varies by region. Nine countries have fully banned bitcoin use, while a further fifteen have implicitly banned it. A few governments have used bitcoin in some capacity. El Salvador has adopted Bitcoin as legal tender, although use by merchants remains low. Ukraine has accepted cryptocurrency donations to fund the resistance to the 2022 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Altcoin
A cryptocurrency, crypto-currency, or crypto is a digital currency designed to work as a medium of exchange through a computer network that is not reliant on any central authority, such as a government or bank, to uphold or maintain it. It is a decentralized system for verifying that the parties to a transaction have the money they claim to have, eliminating the need for traditional intermediaries, such as banks, when funds are being transferred between two entities. Individual coin ownership records are stored in a digital ledger, which is a computerized database using strong cryptography to secure transaction records, control the creation of additional coins, and verify the transfer of coin ownership. Despite their name, cryptocurrencies are not considered to be currencies in the traditional sense, and while varying treatments have been applied to them, including classification as commodities, securities, and currencies, cryptocurrencies are generally viewed as a distinct as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
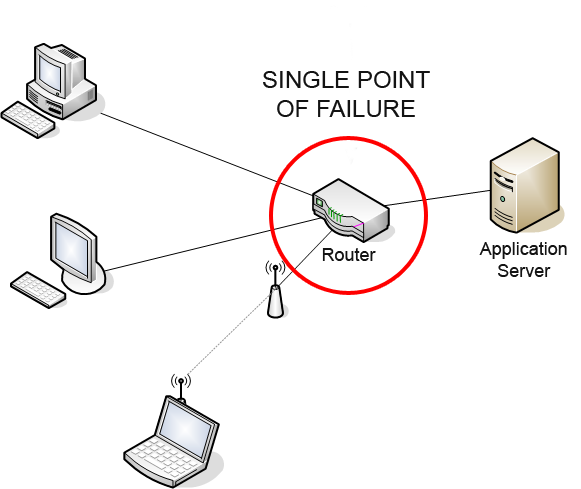
Single Point Of Failure
A single point of failure (SPOF) is a part of a system that, if it fails, will stop the entire system from working. SPOFs are undesirable in any system with a goal of high availability or reliability, be it a business practice, software application, or other industrial system. Overview Systems can be made robust by adding redundancy in all potential SPOFs. Redundancy can be achieved at various levels. The assessment of a potential SPOF involves identifying the critical components of a complex system that would provoke a total systems failure in case of malfunction. Highly reliable systems should not rely on any such individual component. For instance, the owner of a small tree care company may only own one woodchipper. If the chipper breaks, he may be unable to complete his current job and may have to cancel future jobs until he can obtain a replacement. The owner of the tree care company may have spare parts ready for the repair of the wood chipper, in case it fails. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |