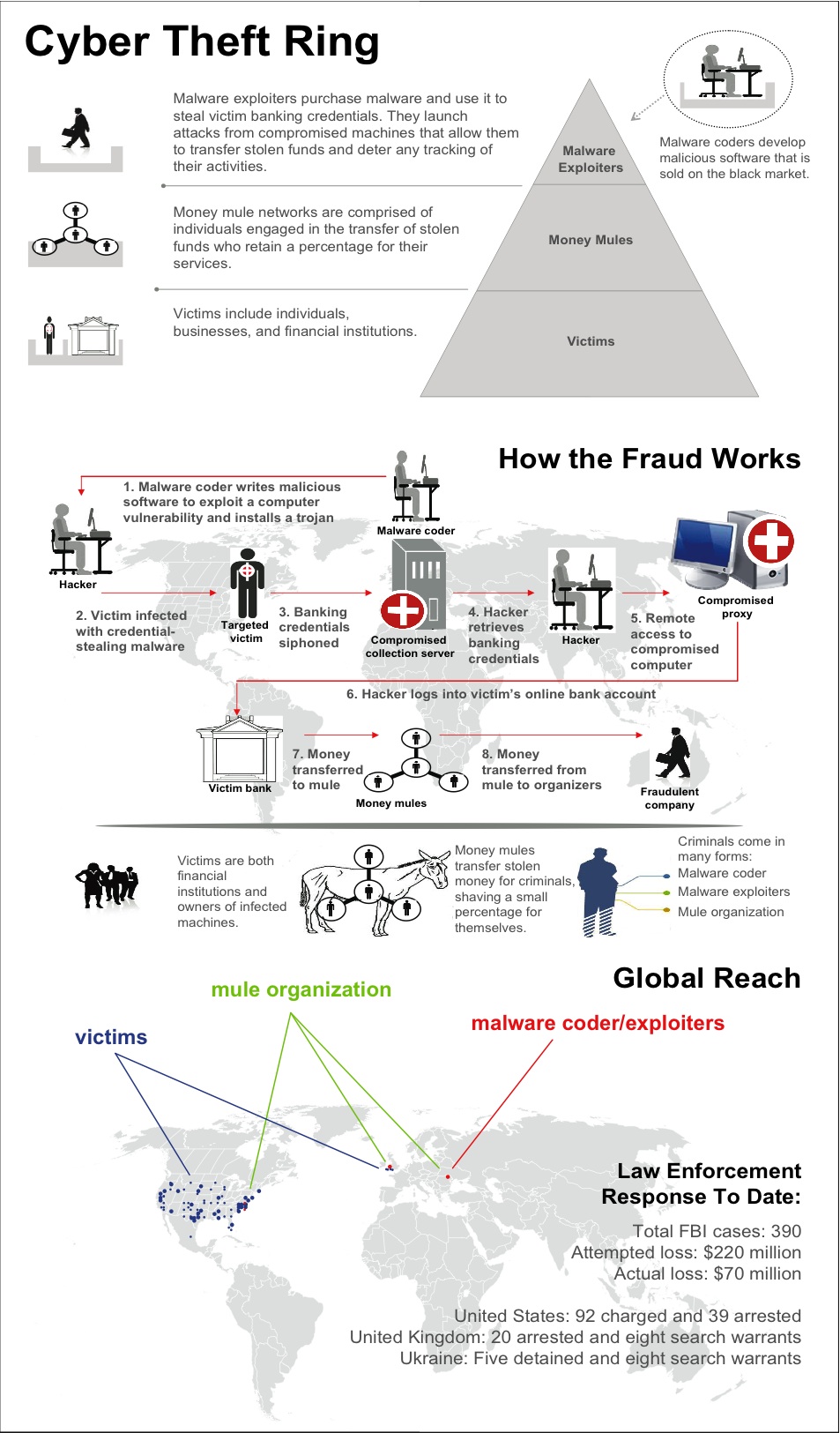
|
Mevade Botnet
The Mevade Botnet, also known as Sefnit or SBC, is a massive botnet. Its operators are unknown and its motives seems to be multi-purpose. In late 2013 the Tor anonymity network saw a very sudden and significant increase in users, from 800,000 daily to more than 5,000,000. A botnet was suspected and fingers pointed at Mevade. Trend Micro reported that its Smart Protection Network saw a tor module being distributed to Mevade Trojans. See also * * C ...[...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Botnet
A botnet is a group of Internet-connected devices, each of which runs one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and " network". The term is usually used with a negative or malicious connotation. Overview A botnet is a logical collection of Internet-connected devices, such as computers, smartphones or Internet of things (IoT) devices whose security have been breached and control ceded to a third party. Each compromised device, known as a "bot," is created when a device is penetrated by software from a ''malware'' (malicious software) distribution. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tor (anonymity Network)
Tor, short for The Onion Router, is free and open-source software for enabling anonymous communication. It directs Internet traffic through a free, worldwide, volunteer overlay network, consisting of more than seven thousand relays, to conceal a user's location and usage from anyone performing network surveillance or traffic analysis. Using Tor makes it more difficult to trace a user's Internet activity. Tor's intended use is to protect the personal privacy of its users, as well as their freedom and ability to communicate confidentially through IP address anonymity using Tor exit nodes. History The core principle of Tor, onion routing, was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag, to protect American intelligence communications online. Onion routing is implemented by means of encryption in the application layer of the communication pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trend Micro
is an American-Japanese multinational cyber security software company with global headquarters in Tokyo, Japan and Irving, Texas, United State.Other regional headquarters and R&D centers are located around East Asia, Southeast Asia, Europe, and North America. The company develops enterprise security software for servers, containers, & cloud computing environments, networks, and end points. Its cloud and virtualization security products provide automated security for customers of VMware, Amazon Web Services, Amazon AWS, Microsoft Azure, and Google Cloud Platform. Eva Chen, who is the founder, currently serves as Trend Micro's chief executive officer, a position she has held since 2005. She succeeded founding CEO Steve Chang, who now serves as chairman. History 1988–1999 The company was founded in 1988 in Los Angeles by Steve Chang, his wife, Jenny Chang, and her sister, Eva Chen (陳怡樺). The company was established with proceeds from Steve Chang's previous sale of a cop ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trojan Horse (computing)
In computing, a Trojan horse (or simply Trojan) is any malware that misleads users of its true intent by disguising itself as a standard program. The term is derived from the ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy. Trojans are generally spread by some form of social engineering. For example, where a user is duped into executing an email attachment disguised to appear innocuous (e.g., a routine form to be filled in), or by clicking on a fake advertisement on social media or anywhere else. Although their payload can be anything, many modern forms act as a backdoor, contacting a controller who can then have unauthorized access to the affected computer. Ransomware attacks are often carried out using a Trojan. Unlike computer viruses and worms, Trojans generally do not attempt to inject themselves into other files or otherwise propagate themselves. Use of the term It is not clear where or when the concept, and this term for it, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Conficker
Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in November 2008. It uses flaws in Windows OS software and dictionary attacks on administrator passwords to propagate while forming a botnet, and has been unusually difficult to counter because of its combined use of many advanced malware techniques. The Conficker worm infected millions of computers including government, business and home computers in over 190 countries, making it the largest known computer worm infection since the 2003 Welchia. Despite its wide propagation, the worm did not do much damage, perhaps because its authors – believed to have been Ukrainian citizens – did not dare use it because of the attention it drew. Four men were arrested, and one pled guilty and was sentenced to four years in prison. Prevalence Estimates of the number of infected computers were difficult because the virus changed its propagatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Command And Control (malware)
A botnet is a group of Internet-connected devices, each of which runs one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and " network". The term is usually used with a negative or malicious connotation. Overview A botnet is a logical collection of Internet-connected devices, such as computers, smartphones or Internet of things (IoT) devices whose security have been breached and control ceded to a third party. Each compromised device, known as a "bot," is created when a device is penetrated by software from a ''malware'' (malicious software) distribution. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Gameover ZeuS
GameOverZeus is a peer-to-peer botnet based on components from the earlier ZeuS trojan. The malware was created by Russian hacker Evgeniy Mikhailovich Bogachev. It is believed to have been spread through use of the Cutwail botnet. Unlike its predecessor the ZeuS trojan, Gameover ZeuS uses an encrypted peer-to-peer communication system to communicate between its nodes and its command and control servers, greatly reducing its vulnerability to law enforcement operations. The algorithm used appears to be modeled on the Kademlia P2P protocol. Scammers control and monitor Gameover ZeuS via command and control (C&C) servers. The virus establishes the connection to the server as soon as its malicious executable installs on the computer, at which point it can disable certain system processes, download and launch executables, or delete essential system files, making the system unusable. According to a report by Symantec, Gameover ZeuS has largely been used for banking fraud and distributi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operation Tovar
Operation Tovar is an international collaborative operation carried out by law enforcement agencies from multiple countries against the Gameover ZeuS botnet, which is believed by the investigators to have been used in bank fraud and the distribution of the CryptoLocker ransomware. Participants include the U.S. Department of Justice, Europol, the FBI and the U.K. National Crime Agency, South African Police Service, together with a number of security companies and academic researchers, including Dell SecureWorks, Deloitte Cyber Risk Services, Microsoft Corporation, Abuse.ch, Afilias, F-Secure, Level 3 Communications, McAfee, Neustar, Shadowserver, Anubisnetworks, Symantec, Heimdal Security, Sophos and Trend Micro, and academic researchers from Carnegie Mellon University, the Georgia Institute of Technology, VU University Amsterdam and Saarland University. Other law enforcement organizations involved include the Australian Federal Police; the National Police of the Netherland ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Timeline Of Computer Viruses And Worms
A timeline is a display of a list of events in chronological order. It is typically a graphic design showing a long bar labelled with dates paralleling it, and usually contemporaneous events. Timelines can use any suitable scale representing time, suiting the subject and data; many use a linear scale, in which a unit of distance is equal to a set amount of time. This timescale is dependent on the events in the timeline. A timeline of evolution can be over millions of years, whereas a timeline for the day of the September 11 attacks can take place over minutes, and that of an explosion over milliseconds. While many timelines use a linear timescale—especially where very large or small timespans are relevant -- logarithmic timelines entail a logarithmic scale of time; some "hurry up and wait" chronologies are depicted with zoom lens metaphors. History Time and space, particularly the line, are intertwined concepts in human thought. The line is ubiquitous in clocks in t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tiny Banker Trojan
Tiny Banker Trojan, also called Tinba, is a malware program that targets financial institution websites. It is a modified form of an older form of viruses known as Banker Trojans, yet it is much smaller in size and more powerful. It works by establishing man-in-the-browser attacks and network sniffing. Since its discovery, it has been found to have infected more than two dozen major banking institutions in the United States, including TD Bank, Chase, HSBC, Wells Fargo, PNC, and Bank of America. It is designed to steal users' sensitive data, such as account login information and banking codes. History Tiny Banker was first discovered in 2012 when it was found to have infected thousands of computers in Turkey. After it was discovered, the original source code for the malware was leaked online and began undergoing individual revisions, making the process of detecting it harder for the institutions. It is a highly modified version of the Zeus Trojan, which had a very similar attack m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Torpig
Torpig, also known as Anserin or Sinowal is a type of botnet spread through systems compromised by the Mebroot rootkit by a variety of trojan horses for the purpose of collecting sensitive personal and corporate data such as bank account and credit card information. It targets computers that use Microsoft Windows, recruiting a network of zombies for the botnet. Torpig circumvents antivirus software through the use of rootkit technology and scans the infected system for credentials, accounts and passwords as well as potentially allowing attackers full access to the computer. It is also purportedly capable of modifying data on the computer, and can perform man-in-the-browser attacks. By November 2008, it was estimated that Torpig had stolen the details of about 500,000 online bank accounts and credit and debit cards and was described as "one of the most advanced pieces of crimeware ever created". History Torpig reportedly began development in 2005, evolving from that point to m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zeus (malware)
Zeus, ZeuS, or Zbot is a Trojan horse malware package that runs on versions of Microsoft Windows. While it can be used to carry out many malicious and criminal tasks, it is often used to steal banking information by man-in-the-browser keystroke logging and form grabbing. It is also used to install the CryptoLocker ransomware. Zeus is spread mainly through drive-by downloads and phishing schemes. First identified in July 2007 when it was used to steal information from the United States Department of Transportation, it became more widespread in March 2009. In June 2009 security company Prevx discovered that Zeus had compromised over 74,000 FTP accounts on websites of such companies as the Bank of America, NASA, Monster.com, ABC, Oracle, Play.com, Cisco, Amazon, and ''BusinessWeek''. Similarly to Koobface, Zeus has also been used to trick victims of technical support scams into giving the scam artists money through pop-up messages that claim the user has a virus, when in real ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |