|
Masking (Electronic Health Record)
In Electronic health records, Electronic Health Records (EHR’s) data masking, or controlled access, is the process of concealing patient health data from certain healthcare providers. Patients have the right to request the masking of their personal information, making it inaccessible to any physician, or a particular physician, unless a specific reason is provided. Data masking is also performed by healthcare agencies to restrict the amount of information that can be accessed by external bodies such as researchers, health insurance agencies and unauthorised individuals. It is a method used to protect patients’ sensitive information so that privacy and confidentiality are less of a concern. Techniques used to alter information within a patient’s Electronic health record, EHR include data encryption, obfuscation, Cryptographic hash function, hashing, exclusion and perturbation. Confidentiality The increased access that transpires from introducing EHR's is seen as a large concern ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Health Records
An electronic health record (EHR) is the systematized collection of patient and population electronically stored health information in a digital format. These records can be shared across different health care settings. Records are shared through network-connected, enterprise-wide information systems or other information networks and exchanges. EHRs may include a range of data, including demographics, medical history, medication and allergies, immunization status, laboratory test results, radiology images, vital signs, personal statistics like age and weight, and billing information. For several decades, electronic health records (EHRs) have been touted as key to increasing of quality care. Electronic health records are used for other reasons than charting for patients; today, providers are using data from patient records to improve quality outcomes through their care management programs. EHR combines all patients demographics into a large pool, and uses this information to assi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
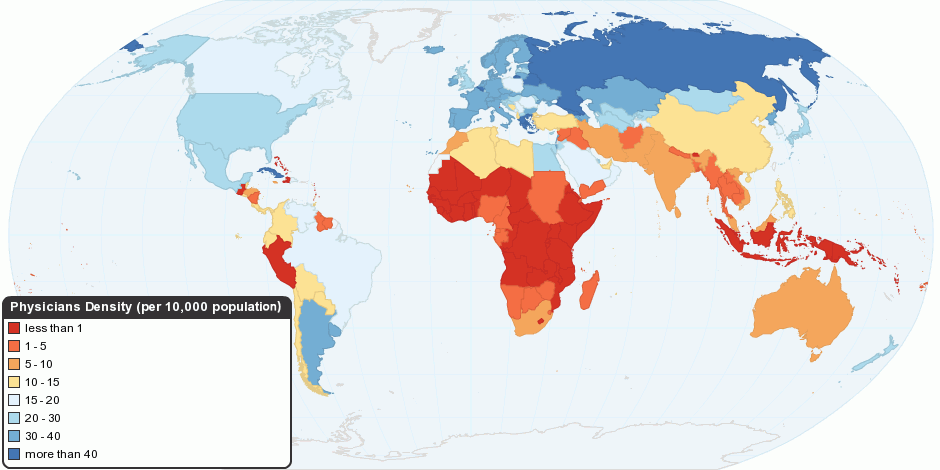
Physicians
A physician (American English), medical practitioner (Commonwealth English), medical doctor, or simply doctor, is a health professional who practices medicine, which is concerned with promoting, maintaining or restoring health through the study, diagnosis, prognosis and treatment of disease, injury, and other physical and mental impairments. Physicians may focus their practice on certain disease categories, types of patients, and methods of treatment—known as specialities—or they may assume responsibility for the provision of continuing and comprehensive medical care to individuals, families, and communities—known as general practice. Medical practice properly requires both a detailed knowledge of the academic disciplines, such as anatomy and physiology, underlying diseases and their treatment—the ''science'' of medicine—and also a decent competence in its applied practice—the art or ''craft'' of medicine. Both the role of the physician and the meaning ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Patient Privacy
Medical privacy or health privacy is the practice of maintaining the security and confidentiality of patient records. It involves both the conversational discretion of health care providers and the security of medical records. The terms can also refer to the physical privacy of patients from other patients and providers while in a medical facility, and to modesty in medical settings. Modern concerns include the degree of disclosure to insurance companies, employers, and other third parties. The advent of electronic medical records (EMR) and patient care management systems (PCMS) have raised new concerns about privacy, balanced with efforts to reduce duplication of services and medical errors. Most developed countries including Australia, Canada, Turkey, the United Kingdom, the United States, New Zealand, and the Netherlands have enacted laws protecting people's medical health privacy. However, many of these health securing privacy laws have proven less effective in practice than in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Continuity Of Care
Transitional care refers to the coordination and continuity of health care during a movement from one healthcare setting to either another or to home, called care transition, between health care practitioners and settings as their condition and care needs change during the course of a chronic or acute illness. Older adults who suffer from a variety of health conditions often need health care services in different settings to meet their many needs. For young people the focus is on moving successfully from child to adult health services. A recent position statement from the American Geriatrics Society defines transitional care as follows: For the purpose of this position statement, transitional care is defined as a set of actions designed to ensure the coordination and continuity of health care as patients transfer between different locations or different levels of care within the same location. Representative locations include (but are not limited to) hospitals, sub-acute and post-ac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Epidemiologists
Epidemiology is the study and analysis of the distribution (who, when, and where), patterns and determinants of health and disease conditions in a defined population. It is a cornerstone of public health, and shapes policy decisions and evidence-based practice by identifying risk factors for disease and targets for preventive healthcare. Epidemiologists help with study design, collection, and statistical analysis of data, amend interpretation and dissemination of results (including peer review and occasional systematic review). Epidemiology has helped develop methodology used in clinical research, public health studies, and, to a lesser extent, basic research in the biological sciences. Major areas of epidemiological study include disease causation, transmission, outbreak investigation, disease surveillance, environmental epidemiology, forensic epidemiology, occupational epidemiology, screening, biomonitoring, and comparisons of treatment effects such as in clinical trials. Epid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anonymity
Anonymity describes situations where the acting person's identity is unknown. Some writers have argued that namelessness, though technically correct, does not capture what is more centrally at stake in contexts of anonymity. The important idea here is that a person be non-identifiable, unreachable, or untrackable. Anonymity is seen as a technique, or a way of realizing, a certain other values, such as privacy, or liberty. Over the past few years, anonymity tools used on the dark web by criminals and malicious users have drastically altered the ability of law enforcement to use conventional surveillance techniques. An important example for anonymity being not only protected, but enforced by law is the vote in free elections. In many other situations (like conversation between strangers, buying some product or service in a shop), anonymity is traditionally accepted as natural. There are also various situations in which a person might choose to withhold their identity. Acts of cha ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Decrypt
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in military ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker (computer Security)
A security hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, information gathering, challenge, recreation, or evaluation of a system weaknesses to assist in formulating defenses against potential hackers. The subculture that has evolved around hackers is often referred to as the "computer underground". Longstanding controversy surrounds the meaning of the term "hacker." In this controversy, computer programmers reclaim the term ''hacker'', arguing that it refers simply to someone with an advanced understanding of computers and computer networks and that ''cracker'' is the more appropriate term for those who break into computers, whether computer criminals ( black hats) or computer security experts ( white hats). A 2014 article noted that "the black-hat meaning still prevails among the general public". History Birth of subcult ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sensitive Information
Information sensitivity is the control of access to information or knowledge that might result in loss of an advantage or level of security if disclosed to others. Loss, misuse, modification, or unauthorized access to sensitive information can adversely affect the privacy or welfare of an individual, trade secrets of a business or even the security and international relations of a nation depending on the level of sensitivity and nature of the information. Non-sensitive information Public information This refers to information that is already a matter of public record or knowledge. With regard to government and private organizations, access to or release of such information may be requested by any member of the public, and there are often formal processes laid out for how to do so. The accessibility of government-held public records is an important part of government transparency, accountability to its citizens, and the values of democracy. Public records may furthermore refer t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Epidemiological Research
Epidemiology is the study and analysis of the distribution (who, when, and where), patterns and determinants of health and disease conditions in a defined population. It is a cornerstone of public health, and shapes policy decisions and evidence-based practice by identifying risk factors for disease and targets for preventive healthcare. Epidemiologists help with study design, collection, and statistical analysis of data, amend interpretation and dissemination of results (including peer review and occasional systematic review). Epidemiology has helped develop methodology used in clinical research, public health studies, and, to a lesser extent, basic research in the biological sciences. Major areas of epidemiological study include disease causation, transmission, outbreak investigation, disease surveillance, environmental epidemiology, forensic epidemiology, occupational epidemiology, screening, biomonitoring, and comparisons of treatment effects such as in clinical trials. Epid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Audited
An audit is an "independent examination of financial information of any entity, whether profit oriented or not, irrespective of its size or legal form when such an examination is conducted with a view to express an opinion thereon.” Auditing also attempts to ensure that the books of accounts are properly maintained by the concern as required by law. Auditors consider the propositions before them, obtain evidence, and evaluate the propositions in their auditing report. Audits provide third-party assurance to various stakeholders that the subject matter is free from material misstatement. The term is most frequently applied to audits of the financial information relating to a legal person. Other commonly audited areas include: secretarial and compliance, internal controls, quality management, project management, water management, and energy conservation. As a result of an audit, stakeholders may evaluate and improve the effectiveness of risk management, control, and governanc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Patient Care
Health care or healthcare is the improvement of health via the prevention, diagnosis, treatment, amelioration or cure of disease, illness, injury, and other physical and mental impairments in people. Health care is delivered by health professionals and allied health fields. Medicine, dentistry, pharmacy, midwifery, nursing, optometry, audiology, psychology, occupational therapy, physical therapy, athletic training, and other health professions all constitute health care. It includes work done in providing primary care, secondary care, and tertiary care, as well as in public health. Access to health care may vary across countries, communities, and individuals, influenced by social and economic conditions as well as health policies. Providing health care services means "the timely use of personal health services to achieve the best possible health outcomes". Factors to consider in terms of health care access include financial limitations (such as insurance coverage), geograph ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |