|
MPack Hearing Closeup
In computer security, MPack is a PHP-based malware kit produced by Russian crackers. The first version was released in December 2006. Since then a new version is thought to have been released roughly every month. It is thought to have been used to infect up to 160,000 PCs with keylogging software. In August 2007 it was believed to have been used in an attack on the web site of the Bank of India which originated from the Russian Business Network. Unusual for such kits, MPack is sold as commercial software (costing $500 to $1,000 US), and is provided by its developers with technical support and regular updates of the software vulnerabilities it exploits. Modules are sold by the developers containing new exploits. These cost between $50 and $150 US depending on how severe the exploit is. The developers also charge to make the scripts and executables undetectable by antivirus software. The server-side software in the kit is able to customize attacks to a variety of web browse ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mpack (Unix)
mpack and munpack are utilities used to encode and decode binaries for use in mail messages following the MIME standard. It was originally written by John Gardiner Myers of Carnegie Mellon University in 1993, and has been ported to the classic Mac OS and Windows Windows is a group of several proprietary graphical operating system families developed and marketed by Microsoft. Each family caters to a certain sector of the computing industry. For example, Windows NT for consumers, Windows Server for .... References External links Unix source Windows port Email 1993 software {{unix-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Internet Explorer
Internet Explorer (formerly Microsoft Internet Explorer and Windows Internet Explorer, commonly abbreviated IE or MSIE) is a series of graphical web browsers developed by Microsoft which was used in the Windows line of operating systems (in Windows 11, Windows Server Insider Build 22463 and Windows Server Insider Build 25110, it is replaced by the Chromium version of Microsoft Edge). Starting in 1995, It was first released as part of the add-on package Plus! for Windows 95 that year. Later versions were available as free downloads, or in-service packs, and included in the original equipment manufacturer (OEM) service releases of Windows 95 and later versions of Windows. Microsoft spent over per year on Internet Explorer in the late 1990s, with over 1,000 people involved in the project by 1999. New feature development for the browser was discontinued in 2016 in favor of new browser Microsoft Edge. Microsoft Teams ended support for IE on November 30, 2020, Microsoft 365 ended it ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backdoor (computing)
A backdoor is a typically covert method of bypassing normal authentication or encryption in a computer, product, embedded device (e.g. a home router), or its embodiment (e.g. part of a cryptosystem, algorithm, chipset, or even a "homunculus computer" —a tiny computer-within-a-computer such as that found in Intel's AMT technology). Backdoors are most often used for securing remote access to a computer, or obtaining access to plaintext in cryptographic systems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information within autoschediastic networks. A backdoor may take the form of a hidden part of a program, a separate program (e.g. Back Orifice may subvert the system through a rootkit), code in the firmware of the hardware, or parts of an operating system such as Windows. Trojan horses can be used to create vulnerabilities in a device. A Trojan horse may appear to be an entirely leg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Virus
A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Computer viruses generally require a host program. The virus writes its own code into the host program. When the program runs, the written virus program is executed first, causing infection and damage. A computer worm does not need a host program, as it is an independent program or code chunk. Therefore, it is not restricted by the host program, but can run independently and actively carry out attacks. Virus writers use social engineering deceptions and exploit detailed knowledge of security vulnerabilities to initially infect systems and to spread the virus. Viruses use complex anti-detection/stealth strategies to evade antivirus software. Motives for creating viruses can inclu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Botnet
A botnet is a group of Internet-connected devices, each of which runs one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and " network". The term is usually used with a negative or malicious connotation. Overview A botnet is a logical collection of Internet-connected devices, such as computers, smartphones or Internet of things (IoT) devices whose security have been breached and control ceded to a third party. Each compromised device, known as a "bot," is created when a device is penetrated by software from a ''malware'' (malicious software) distribution. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spyware
Spyware (a portmanteau for spying software) is software with malicious behaviour that aims to gather information about a person or organization and send it to another entity in a way that harms the user—for example, by violating their privacy or endangering their device's security. This behaviour may be present in malware as well as in legitimate software. Websites may engage in spyware behaviours like web tracking. Hardware devices may also be affected. Spyware is frequently associated with advertising and involves many of the same issues. Because these behaviors are so common, and can have non-harmful uses, providing a precise definition of spyware is a difficult task.FTC Report (2005)." History The first recorded use of the term :wikt:spyware, spyware occurred on October 16, 1995 in a Usenet post that poked fun at Microsoft's business model.Vossen, Roland (attributed); October 21, 1995Win 95 Source code in c!!posted to rec..programmer; retrieved from groups.google.co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trojan Horse (computing)
In computing, a Trojan horse is any malware that misleads users of its true intent. The term is derived from the Ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy. Trojans generally spread by some form of social engineering; for example, where a user is duped into executing an email attachment disguised to appear innocuous (e.g., a routine form to be filled in), or by clicking on some fake advertisement on social media or anywhere else. Although their payload can be anything, many modern forms act as a backdoor, contacting a controller who can then have unauthorized access to the affected computer. Ransomware attacks are often carried out using a Trojan. Unlike computer viruses and worms, Trojans generally do not attempt to inject themselves into other files or otherwise propagate themselves. Use of the term It's not clear where or when the concept, and this term for it, was first used, but by 1971 the first Unix manual assumed it ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exploit Kit
An exploit kit is a tool used for automatically managing and deploying exploits against a target computer. Exploit kits allow attackers to deliver malware without having advanced knowledge of the exploits being used. Browser exploits are typically used, although they may also include exploits targeting common software, such as Adobe Reader, or the operating system itself. Most kits are written in PHP. Exploit kits are often sold on the black market, both as standalone kits, and as a service. History Some of the first exploit kits were WebAttacker and MPack, both created in 2006. They were sold on black markets, enabling attackers to use exploits without advanced knowledge of computer security. The Blackhole exploit kit was released in 2010, and could either be purchased outright, or rented for a fee. Malwarebytes stated that Blackhole was the primary method of delivering malware in 2012 and much of 2013. After the arrest of the authors in late 2013, use of the kit shar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exploit (computer Security)
An exploit (from the English verb ''to exploit'', meaning "to use something to one’s own advantage") is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic (usually computerized). Such behavior frequently includes things like gaining control of a computer system, allowing privilege escalation, or a denial-of-service (DoS or related DDoS) attack. In lay terms, some exploit is akin to a 'hack'. Classification There are several methods of classifying exploits. The most common is by how the exploit communicates to the vulnerable software. A ''remote exploit'' works over a network and exploits the security vulnerability without any prior access to the vulnerable system. A ''local exploit'' requires prior access to the vulnerable system and usually increases the privileges of the person running the exploit past t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTML Element
An HTML element is a type of HTML (HyperText Markup Language) document component, one of several types of HTML nodes (there are also text nodes, comment nodes and others). The first used version of HTML was written by Tim Berners-Lee in 1993 and there have since been many versions of HTML. The most commonly used version is HTML 4.01, which became official standard in December 1999. An HTML document is composed of a tree of simple HTML nodes, such as text nodes, and HTML elements, which add semantics and formatting to parts of document (e.g., make text bold, organize it into paragraphs, lists and tables, or embed hyperlinks and images). Each element can have HTML attributes specified. Elements can also have content, including other elements and text. Concepts Elements vs. tags As is generally understood, the position of an element is indicated as spanning from a start tag and is terminated by an end tag. This is the case for many, but not all, elements within an HTML docu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Opera (web Browser)
Opera is a multi-platform web browser developed by its namesake company Opera. The browser is based on Chromium, but distinguishes itself from other Chromium-based browsers (Chrome, Edge, etc.) through its user interface and other features. Opera was initially released on 10 April 1995, making it one of the oldest desktop web browsers still actively developed. It was commercial software for its first ten years and had its own proprietary layout engine, Presto. In 2013, it switched from the Presto engine to Chromium. Opera is available on Windows, macOS, Linux, Android, and iOS (Safari WebKit engine). There are also mobile versions called Opera Mobile and Opera Mini. Opera users also have access to Opera News, a news app based on an AI platform. The company released a gaming-oriented version of the browser, Opera GX, in 2019, and a blockchain-focused Opera Crypto Browser into public beta in January 2022. History In 1994, Jon Stephenson von Tetzchner and Geir Ivarsøy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
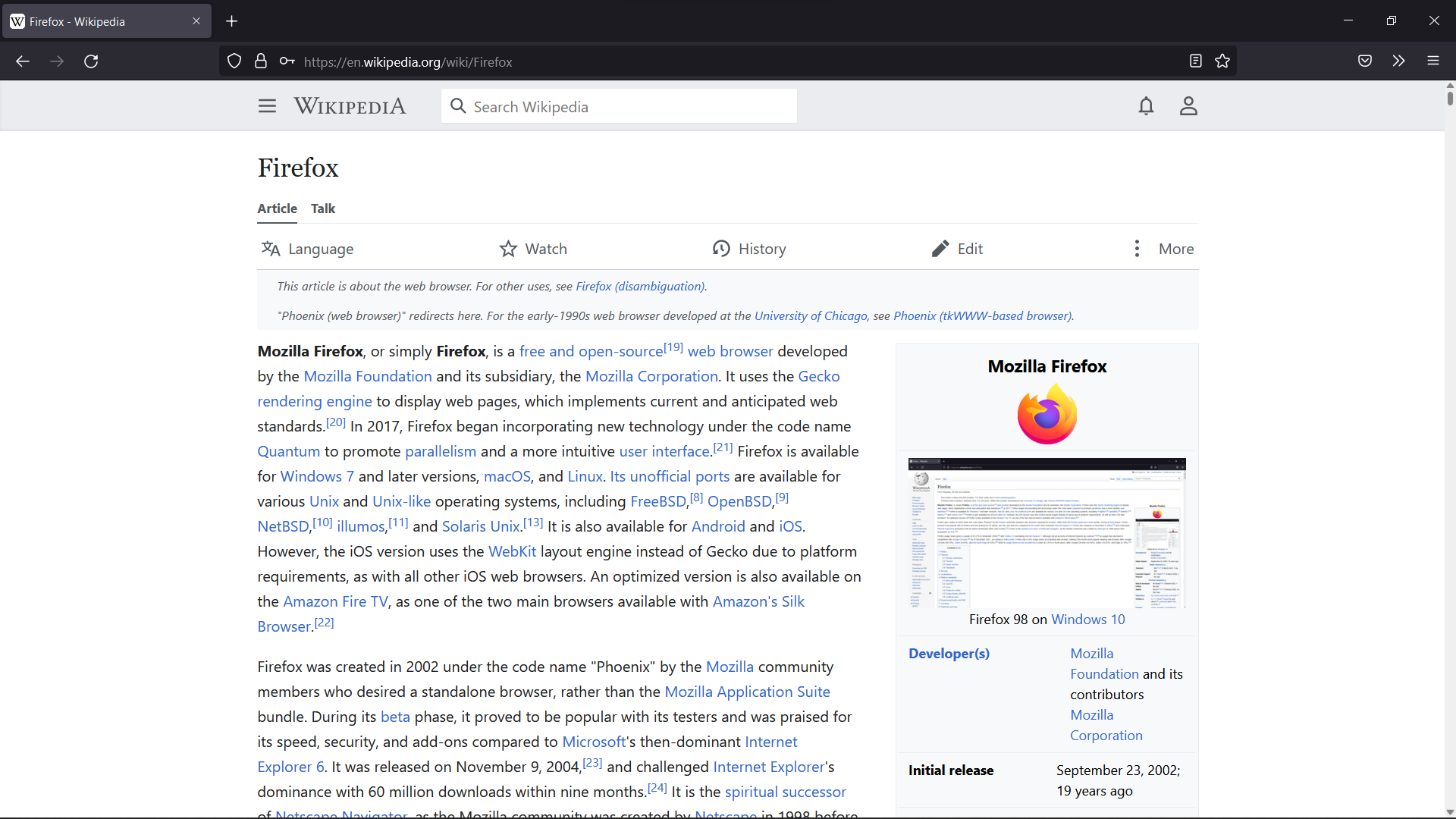
Mozilla Firefox
Mozilla Firefox, or simply Firefox, is a free and open-source web browser developed by the Mozilla Foundation and its subsidiary, the Mozilla Corporation. It uses the Gecko rendering engine to display web pages, which implements current and anticipated web standards. In November 2017, Firefox began incorporating new technology under the code name " Quantum" to promote parallelism and a more intuitive user interface. Firefox is available for Windows 7 and later versions, macOS, and Linux. Its unofficial ports are available for various Unix and Unix-like operating systems, including FreeBSD, OpenBSD, NetBSD, illumos, and Solaris Unix. It is also available for Android and iOS. However, as with all other iOS web browsers, the iOS version uses the WebKit layout engine instead of Gecko due to platform requirements. An optimized version is also available on the Amazon Fire TV as one of the two main browsers available with Amazon's Silk Browser. Firefox was created in 2002 u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |