|
Low-level Programming
A low-level programming language is a programming language that provides little or no abstraction from a computer's instruction set architecture—commands or functions in the language map that are structurally similar to processor's instructions. Generally, this refers to either machine code or assembly language. Because of the low (hence the word) abstraction between the language and machine language, low-level languages are sometimes described as being "close to the hardware". Programs written in low-level languages tend to be relatively non-portable, due to being optimized for a certain type of system architecture. Low-level languages can convert to machine code without a compiler or interpreter—second-generation programming languages use a simpler processor called an assembler—and the resulting code runs directly on the processor. A program written in a low-level language can be made to run very quickly, with a small memory footprint. An equivalent program in a high-le ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Programming Language
A programming language is a system of notation for writing computer programs. Most programming languages are text-based formal languages, but they may also be graphical. They are a kind of computer language. The description of a programming language is usually split into the two components of syntax (form) and semantics (meaning), which are usually defined by a formal language. Some languages are defined by a specification document (for example, the C programming language is specified by an ISO Standard) while other languages (such as Perl) have a dominant implementation that is treated as a reference. Some languages have both, with the basic language defined by a standard and extensions taken from the dominant implementation being common. Programming language theory is the subfield of computer science that studies the design, implementation, analysis, characterization, and classification of programming languages. Definitions There are many considerations when defining ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Octal
The octal numeral system, or oct for short, is the radix, base-8 number system, and uses the Numerical digit, digits 0 to 7. This is to say that 10octal represents eight and 100octal represents sixty-four. However, English, like most languages, uses a Base 10, base-10 number system, hence a true octal system might use different vocabulary. In the decimal system, each place is a power of ten. For example: : \mathbf_ = \mathbf \times 10^1 + \mathbf \times 10^0 In the octal system, each place is a power of eight. For example: : \mathbf_8 = \mathbf \times 8^2 + \mathbf \times 8^1 + \mathbf \times 8^0 By performing the calculation above in the familiar decimal system, we see why 112 in octal is equal to 64+8+2=74 in decimal. Octal numerals can be easily converted from Binary numeral system, binary representations (similar to a quaternary numeral system) by grouping consecutive binary digits into groups of three (starting from the right, for integers). For example, the binary repr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Machine Instruction (computing)
In computer programming, machine code is any low-level programming language, consisting of machine language instructions, which are used to control a computer's central processing unit (CPU). Each instruction causes the CPU to perform a very specific task, such as a load, a store, a jump, or an arithmetic logic unit (ALU) operation on one or more units of data in the CPU's registers or memory. Early CPUs had specific machine code that might break backwards compatibility with each new CPU released. The notion of an instruction set architecture (ISA)Â defines and specifies the behavior and encoding in memory of the instruction set of the system, without specifying its exact implementation. This acts as an abstraction layer, enabling compatibility within the same family of CPUs, so that machine code written or generated according to the ISA for the family will run on all CPUs in the family, including future CPUs. In general, each architecture family (e.g. x86, ARM) has its ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
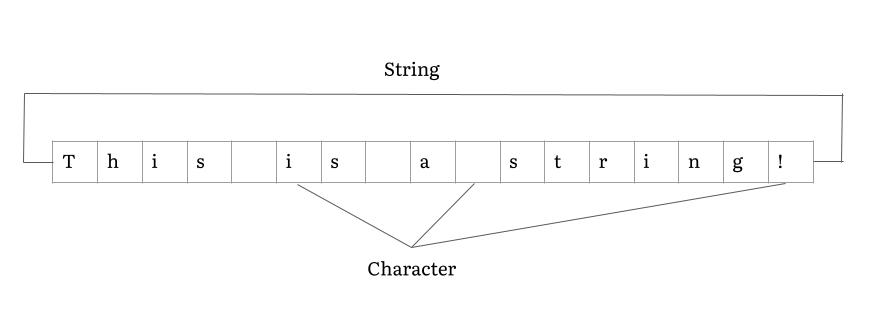
String (computer Science)
In computer programming, a string is traditionally a sequence of characters, either as a literal constant or as some kind of variable. The latter may allow its elements to be mutated and the length changed, or it may be fixed (after creation). A string is generally considered as a data type and is often implemented as an array data structure of bytes (or words) that stores a sequence of elements, typically characters, using some character encoding. ''String'' may also denote more general arrays or other sequence (or list) data types and structures. Depending on the programming language and precise data type used, a variable declared to be a string may either cause storage in memory to be statically allocated for a predetermined maximum length or employ dynamic allocation to allow it to hold a variable number of elements. When a string appears literally in source code, it is known as a string literal or an anonymous string. In formal languages, which are used in mathemati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Memory Address
In computing, a memory address is a reference to a specific memory location used at various levels by software and hardware. Memory addresses are fixed-length sequences of digits conventionally displayed and manipulated as unsigned integers. Such numerical semantic bases itself upon features of CPU (such as the instruction pointer and incremental address registers), as well upon use of the memory like an array endorsed by various programming languages. Types Physical addresses A digital computer's main memory consists of many memory locations. Each memory location has a physical address which is a code. The CPU (or other device) can use the code to access the corresponding memory location. Generally only system software, i.e. the BIOS, operating systems, and some specialized utility programs (e.g., memory testers), address physical memory using machine code operands or processor registers, instructing the CPU to direct a hardware device, called the memory controller ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Opcode
In computing, an opcode (abbreviated from operation code, also known as instruction machine code, instruction code, instruction syllable, instruction parcel or opstring) is the portion of a machine language instruction that specifies the operation to be performed. Beside the opcode itself, most instructions also specify the data they will process, in the form of operands. In addition to opcodes used in the instruction set architectures of various CPUs, which are hardware devices, they can also be used in abstract computing machines as part of their byte code specifications. Overview Specifications and format of the opcodes are laid out in the instruction set architecture (ISA) of the processor in question, which may be a general CPU or a more specialized processing unit. Opcodes for a given instruction set can be described through the use of an opcode table detailing all possible opcodes. Apart from the opcode itself, an instruction normally also has one or more specifiers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Semantics (computer Science)
In programming language theory, semantics is the rigorous mathematical study of the meaning of programming languages. Semantics assigns computational meaning to valid strings in a programming language syntax. Semantics describes the processes a computer follows when executing a program in that specific language. This can be shown by describing the relationship between the input and output of a program, or an explanation of how the program will be executed on a certain platform, hence creating a model of computation. History In 1967, Robert W. Floyd publishes the paper ''Assigning meanings to programs''; his chief aim is "a rigorous standard for proofs about computer programs, including proofs of correctness, equivalence, and termination". Floyd further writes: A semantic definition of a programming language, in our approach, is founded on a syntactic definition. It must specify which of the phrases in a syntactically correct program represent commands, and what cond ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker Culture
The hacker culture is a subculture of individuals who enjoy—often in collective effort—the intellectual challenge of creatively overcoming the limitations of software systems or electronic hardware (mostly digital electronics), to achieve novel and clever outcomes. The act of engaging in activities (such as programming or other mediaThe Hacker Community and Ethics: An Interview with Richard M. Stallman, 2002 (gnu.org)) in a spirit of playfulness and exploration is termed ''hacking''. However, the defining characteristic of a is not the activities performed themselves (e.g. [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
PDP-1
The PDP-1 (''Programmed Data Processor-1'') is the first computer in Digital Equipment Corporation's PDP series and was first produced in 1959. It is famous for being the computer most important in the creation of hacker culture at Massachusetts Institute of Technology, BBN and elsewhere. The PDP-1 is the original hardware for playing history's first game on a minicomputer, Steve Russell's '' Spacewar!'' Description The PDP-1 uses an 18-bit word size and has 4096 words as standard main memory (equivalent to 9,216 eight-bit bytes, though the system actually divides an 18-bit word into six-bit characters), upgradable to 65,536 words. The magnetic-core memory's cycle time is 5.35 microseconds (corresponding roughly to a clock speed of 187 kilohertz); consequently most arithmetic instructions take 10.7 microseconds (93,458 operations per second) because they use two memory cycles: the first to fetch the instruction, the second to fetch or store the data word. Signed numbers ar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TX-0
The TX-0, for ''Transistorized Experimental computer zero'', but affectionately referred to as tixo (pronounced "tix oh"), was an early fully transistorized computer and contained a then-huge 64 K of 18-bit words of magnetic-core memory. Construction of the TX-0 began in 1955 and ended in 1956.Highlights from ''The Computer Museum Report'' Volume 8 Spring 1984 The Computer Museum, Boston, MA, archived at ed-thelen.org, retrieved 2010-2-19 It was used continually through the 1960s at MIT. The TX-0 incorporated around 3,600 [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fibonacci Number
In mathematics, the Fibonacci numbers, commonly denoted , form a integer sequence, sequence, the Fibonacci sequence, in which each number is the sum of the two preceding ones. The sequence commonly starts from 0 and 1, although some authors start the sequence from 1 and 1 or sometimes (as did Fibonacci) from 1 and 2. Starting from 0 and 1, the first few values in the sequence are: :0, 1, 1, 2, 3, 5, 8, 13, 21, 34, 55, 89, 144. The Fibonacci numbers were first described in Indian mathematics, as early as 200 BC in work by Pingala on enumerating possible patterns of Sanskrit poetry formed from syllables of two lengths. They are named after the Italian mathematician Leonardo of Pisa, later known as Fibonacci, who introduced the sequence to Western European mathematics in his 1202 book ''Liber Abaci''. Fibonacci numbers appear unexpectedly often in mathematics, so much so that there is an entire journal dedicated to their study, the ''Fibonacci Quarterly''. Applications of Fibonacci ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Core Dump
In computing, a core dump, memory dump, crash dump, storage dump, system dump, or ABEND dump consists of the recorded state of the working Computer storage, memory of a computer program at a specific time, generally when the program has crash (computing), crashed or otherwise terminated abnormally. In practice, other key pieces of Context switch, program state are usually dumped at the same time, including the processor registers, which may include the program counter and stack pointer, memory management information, and other processor and operating system flags and information. A snapshot dump (or snap dump) is a memory dump requested by the computer operator or by the running program, after which the program is able to continue. Core dumps are often used to assist in diagnosing and debugging errors in computer programs. On many operating systems, a fatal exception in a program automatically triggers a core dump. By extension, the phrase "to dump core" has come to mean in many c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |