|
Lincoln (surveillance)
Lincoln, manufactured by the company Pen-Link, Ltd., is a class of electronic data interception products—including both computer hardware and software packages—whose function is to extract and analyze internet traffic for mass surveillance purposes, such as those outlined under the Communications Assistance For Law Enforcement Act (CALEA). Lincoln systems enable law enforcement and intelligence agencies to monitor numerous types of intercepted electronic communications—including telephone (landline & wireless), VoIP, 3G and IP (web/email/IM traffic). Lincoln systems are generally implemented along with other Pen-Link products to enable features such as databases to store intercepted communications, mapping software (to monitor the locations of surveillance targets), visualization software, and link analysis features. See also *Communications Assistance For Law Enforcement Act *Verint Systems * Mass surveillance References Crashing The Wiretappers Ball ''Wired.com ' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pen-Link, Ltd
Pen-Link, Ltd., (PenLink) is a software company that develops enterprise-grade communications surveillance data collection and analysis solutions for domestic law enforcement. Their flagship products include PLX and PenPoint. One of the more publicized uses of PenLink's products was during the Laci Peterson murder case, where wiretaps taken with Pen-Link 8 and LINCOLN2 were used as evidence against Scott Peterson. See also * Lawful interception * Communications Assistance For Law Enforcement Act The Communications Assistance for Law Enforcement Act (CALEA), also known as the "Digital Telephony Act," is a United States wiretapping law passed in 1994, during the presidency of Bill Clinton (Pub. L. No. 103-414, 108 Stat. 4279, codified at 47 ... References https://www.kearneyhub.com/news/local/pen-link-employees-cash-in-on-growing-surveillance-business/article_80216234-5028-5e21-9e8d-6ae6edcbae08.html Surveillance {{US-telecom-company-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Surveillance
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as Human intelligence (intelligence gathering), human intelligence gathering and postal interception. Surveillance is used by citizens for protecting their neighborhoods. And by governments for intelligence gathering - including espionage, prevention of crime, the protection of a process, person, group or object, or the investigation of crime. It is also used by criminal organizations to plan and commit crimes, and by businesses to Industrial espionage, gather intelligence on criminals, their competitors, suppliers or customers. Religious organisations charged with detecting he ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mass Surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizations, such as organizations like the NSA, but it may also be carried out by corporations (either on behalf of governments or at their own initiative). Depending on each nation's laws and judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is the single most indicative distinguishing trait of totalitarian regimes. It is also often distinguished from targeted surveillance. Mass surveillance has often been cited as necessary to fight terrorism, prevent crime and social unrest, protect national security, and control the population. At the same time, mass surveillance has equally often been criticized for violating privacy rights, limiting civil and political rights and freedoms, and being il ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Communications Assistance For Law Enforcement Act
The Communications Assistance for Law Enforcement Act (CALEA), also known as the "Digital Telephony Act," is a United States wiretapping law passed in 1994, during the presidency of Bill Clinton (Pub. L. No. 103-414, 108 Stat. 4279, codified at 47 USC 1001-1010). CALEA's purpose is to enhance the ability of law enforcement agencies to conduct lawful interception of communication by requiring that telecommunications carriers and manufacturers of telecommunications equipment modify and design their equipment, facilities, and services to ensure that they have built-in capabilities for targeted surveillance, allowing federal agencies to selectively wiretap any telephone traffic; it has since been extended to cover broadband Internet and VoIP traffic. Some government agencies argue that it covers mass surveillance of communications rather than just tapping specific lines and that not all CALEA-based access requires a warrant. The original reason for adopting CALEA was the Federal Burea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
VoIP
Voice over Internet Protocol (VoIP), also called IP telephony, is a method and group of technologies for the delivery of voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet. The terms Internet telephony, broadband telephony, and broadband phone service specifically refer to the provisioning of communications services (voice, fax, SMS, voice-messaging) over the Internet, rather than via the public switched telephone network (PSTN), also known as plain old telephone service (POTS). Overview The steps and principles involved in originating VoIP telephone calls are similar to traditional digital telephony and involve signaling, channel setup, digitization of the analog voice signals, and encoding. Instead of being transmitted over a circuit-switched network, the digital information is packetized and transmission occurs as IP packets over a packet-switched network. They transport media streams using special media delivery protocols t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Protocol
The Internet Protocol (IP) is the network layer communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet. IP has the task of delivering packets from the source host to the destination host solely based on the IP addresses in the packet headers. For this purpose, IP defines packet structures that encapsulate the data to be delivered. It also defines addressing methods that are used to label the datagram with source and destination information. IP was the connectionless datagram service in the original Transmission Control Program introduced by Vint Cerf and Bob Kahn in 1974, which was complemented by a connection-oriented service that became the basis for the Transmission Control Protocol (TCP). The Internet protocol suite is therefore often referred to as ''TCP/IP''. The first major version of IP, Internet Protocol Version 4 (IPv4), is the do ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
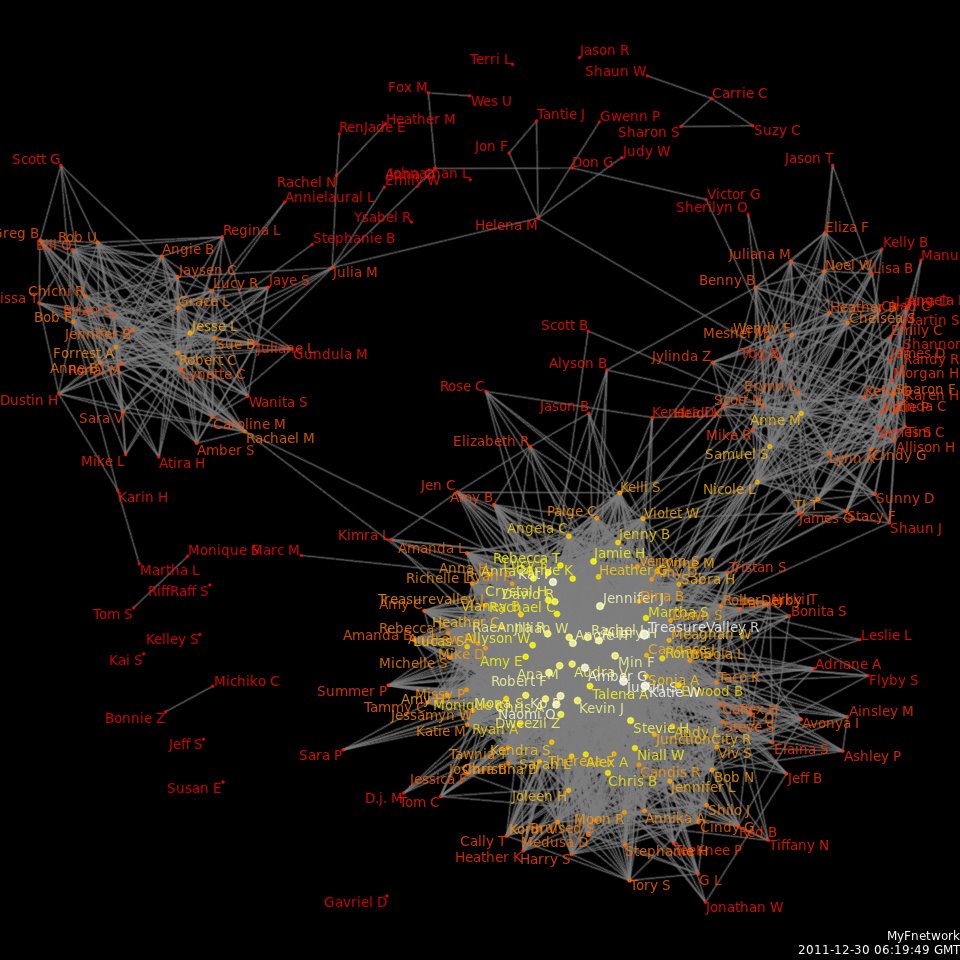
Social Network Analysis
Social network analysis (SNA) is the process of investigating social structures through the use of networks and graph theory. It characterizes networked structures in terms of ''nodes'' (individual actors, people, or things within the network) and the ''ties'', ''edges'', or ''links'' (relationships or interactions) that connect them. Examples of social structures commonly visualized through social network analysis include social media networks, memes spread, information circulation, friendship and acquaintance networks, business networks, knowledge networks, difficult working relationships, social networks, collaboration graphs, kinship, disease transmission, and sexual relationships. These networks are often visualized through ''sociograms'' in which nodes are represented as points and ties are represented as lines. These visualizations provide a means of qualitatively assessing networks by varying the visual representation of their nodes and edges to reflect attributes of in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Verint Systems
Verint Systems is a Melville, New York-based analytics company which was founded in 2002. The company sells software and hardware products for customer engagement management and business intelligence. Their products are designed to assist clients in data analysis, specifically large data sets. In 2021, Verint has 9,800+ clients in more than 175 countries, and has 4,300+ employees in various locations internationally. The company was previously a majority-owned subsidiary of Comverse Technology and it was formerly known as Comverse Infosys. As with Comverse, approximately half of Verint's employees have been located in Israel."Verint to raise $75m. in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mass Surveillance
Mass surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens. The surveillance is often carried out by local and federal governments or governmental organizations, such as organizations like the NSA, but it may also be carried out by corporations (either on behalf of governments or at their own initiative). Depending on each nation's laws and judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is the single most indicative distinguishing trait of totalitarian regimes. It is also often distinguished from targeted surveillance. Mass surveillance has often been cited as necessary to fight terrorism, prevent crime and social unrest, protect national security, and control the population. At the same time, mass surveillance has equally often been criticized for violating privacy rights, limiting civil and political rights and freedoms, and being il ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wired
''Wired'' (stylized as ''WIRED'') is a monthly American magazine, published in print and online editions, that focuses on how emerging technologies affect culture, the economy, and politics. Owned by Condé Nast, it is headquartered in San Francisco, California, and has been in publication since March/April 1993. Several spin-offs have been launched, including ''Wired UK'', ''Wired Italia'', ''Wired Japan'', and ''Wired Germany''. From its beginning, the strongest influence on the magazine's editorial outlook came from founding editor and publisher Louis Rossetto. With founding creative director John Plunkett, Rossetto in 1991 assembled a 12-page prototype, nearly all of whose ideas were realized in the magazine's first several issues. In its earliest colophons, ''Wired'' credited Canadian media theorist Marshall McLuhan as its "patron saint". ''Wired'' went on to chronicle the evolution of digital technology and its impact on society. ''Wired'' quickly became recognized as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |