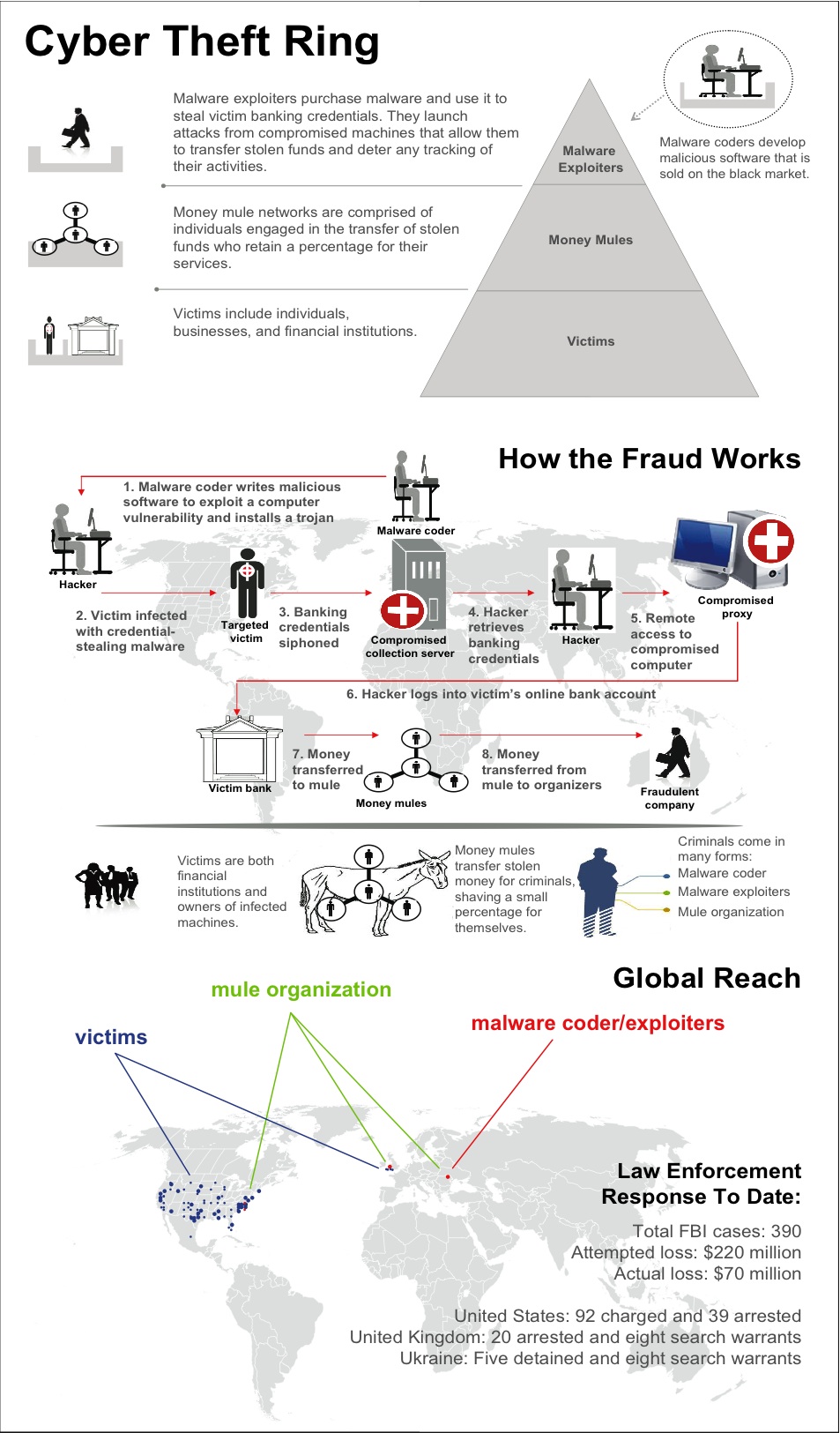
|
Kronos (malware)
Kronos was a type of banking malware first reported in 2014. It was sold for $7,000. It was developed as a followup to the UPAS Kit which has been released in 2012. Similar to Zeus, it was focused on stealing banking login credentials from browser sessions via a combination of keylogging and web injection. In 2015, its attacks were focused on British banks. In August 2017, British security researcher Marcus Hutchins (aka 'MalwareTech'), previously notable for his involvement stopping the May 2017 WannaCry ransomware attack, was arrested by the FBI whilst visiting the United States. He was alleged to have created the software in 2014, and to have sold it in 2015 via the AlphaBay forums. Hutchins later admitted to being paid to work on Kronos and its predecessor UPAS Kit (named after the toxic Upas tree ''Antiaris toxicaria'' is a tree in the mulberry and fig family, Moraceae. It is the only species currently recognized in the genus ''Antiaris''. The genus ''Antiaris'' was at on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware
Malware (a portmanteau for ''malicious software'') is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. By contrast, software that causes harm due to some deficiency is typically described as a software bug. Malware poses serious problems to individuals and businesses on the Internet. According to Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 669,947,865 in 2017, which is twice as many malware variants as in 2016. Cybercrime, which includes malware attacks as well as other crimes committed by computer, was predicted to cost the world economy $6 trillion USD in 2021, and is increasing at a rate of 15% per year. Many types of malware exist, including computer viruses, worms, Trojan ho ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zeus (malware)
Zeus, ZeuS, or Zbot is a Trojan horse malware package that runs on versions of Microsoft Windows. While it can be used to carry out many malicious and criminal tasks, it is often used to steal banking information by man-in-the-browser keystroke logging and form grabbing. It is also used to install the CryptoLocker ransomware. Zeus is spread mainly through drive-by downloads and phishing schemes. First identified in July 2007 when it was used to steal information from the United States Department of Transportation, it became more widespread in March 2009. In June 2009 security company Prevx discovered that Zeus had compromised over 74,000 FTP accounts on websites of such companies as the Bank of America, NASA, Monster.com, ABC, Oracle, Play.com, Cisco, Amazon, and ''BusinessWeek''. Similarly to Koobface, Zeus has also been used to trick victims of technical support scams into giving the scam artists money through pop-up messages that claim the user has a virus, when in real ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Keylogging
Keystroke logging, often referred to as keylogging or keyboard capturing, is the action of recording (logging) the keys struck on a keyboard, typically covertly, so that a person using the keyboard is unaware that their actions are being monitored. Data can then be retrieved by the person operating the logging program. A keystroke recorder or keylogger can be either software or hardware. While the programs themselves are legal, with many designed to allow employers to oversee the use of their computers, keyloggers are most often used for stealing passwords and other confidential information. Keylogging can also be used to study keystroke dynamics or human-computer interaction. Numerous keylogging methods exist, ranging from hardware and software-based approaches to acoustic cryptanalysis. Application of keylogger Software-based keyloggers A software-based keylogger is a computer program designed to record any input from the keyboard. Keyloggers are used in IT organization ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Skimming
Web skimming, formjacking or a magecart attack is an attack where the attacker injects malicious code into a website and extracts data from an HTML form that the user has filled in. That data is then submitted to a server under control of the attacker. Mitigation Subresource Integrity or a Content Security Policy can be used to protect against formjacking, although this does not protect against supply chain attacks. A web application firewall can also be used. Prevalence A report in 2016 suggested as many as 6,000 e-commerce sites may have been compromised via this class of attack. In 2018, British Airways had 380,000 card details stolen in via this class of attack. A similar attack affected Ticketmaster the same year with 40,000 customers affected by maliciously injected code on payment pages. Magecart Magecart is software used by a range of hacking groups for injecting malicious code into ecommerce sites to steal payment details. As well as targeted attacks such as o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Marcus Hutchins
Marcus Hutchins (born 1994), also known online as MalwareTech, is a British computer security researcher known for stopping the WannaCry ransomware attack. He is employed by cybersecurity firm Kryptos Logic. Hutchins is from Ilfracombe in Devon. Early life Hutchins is the elder son of Janet Hutchins, a Scottish nurse, and Desmond Hutchins, a Jamaican social worker. Around 2003, when Hutchins was nine years old, the parents moved the family from urban Bracknell, near London, to rural Devon. Hutchins had shown early aptitude with computers and learned simple hacking skills early on such as bypassing security on school computers to install video game software. In addition, he spent time learning to be a surf lifeguard. He became involved with an online forum that promoted malware development, more as a means to show off their skills to each other rather than for nefarious purposes. When he was about 14 years old, he created his own contribution, a password stealer based on Inter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
WannaCry Ransomware Attack
The WannaCry ransomware attack was a worldwide cyberattack in May 2017 by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency. It propagated by using EternalBlue, an exploit developed by the United States National Security Agency (NSA) for Windows systems. EternalBlue was stolen and leaked by a group called The Shadow Brokers a month prior to the attack. While Microsoft had released patches previously to close the exploit, much of WannaCry's spread was from organizations that had not applied these, or were using older Windows systems that were past their end-of-life. These patches were imperative to organizations' cyber security but many were not implemented due to ignorance of their importance. Some have claimed a need for 24/7 operation, aversion to risking having formerly working applications breaking because of patch changes, lack of pers ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
AlphaBay
AlphaBay is a darknet market operating both as an onion service on the Tor network and as an I2P node on I2P. After it was shut down in July 2017 following law enforcement action in the United States, Canada, and Thailand as part of Operation Bayonet, it was relaunched in August 2021 by the self-described co-founder and security administrator DeSnake. The alleged original founder, Alexandre Cazes, a Canadian citizen born on 19 October 1991, was found dead in his cell in Thailand several days after his arrest, with police suspecting suicide. History AlphaBay reportedly launched in September 2014, pre-launched in November 2014 and officially launched on December 22, 2014. It saw a steady growth, with 14,000 new users in the first 90 days of operation. The darknet informer website Gwern.net placed AlphaBay Market in the top tier of markets regarding the 6-month survival probability and it had proven to be successful. In October 2015, it was recognized as the largest online dar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Upas Tree
''Antiaris toxicaria'' is a tree in the mulberry and fig family, Moraceae. It is the only species currently recognized in the genus ''Antiaris''. The genus ''Antiaris'' was at one time considered to consist of several species, but is now regarded as just one variable species which can be further divided into five subspecies. One significant difference within the species is that the size of the fruit decreases as one travels from Africa to Polynesia. Antiaris has a remarkably wide distribution in tropical regions, occurring in Australia, tropical Asia, tropical Africa, Indonesia, the Philippines, Tonga, and various other tropical islands. Its seeds are spread by various birds and bats, and it is not clear how many of the populations are essentially invasive. The species is of interest as a source of wood, bark cloth, and pharmacological or toxic substances. Naming and etymology The generic epithet ''Antiaris'' is derived directly from the Javanese name for it: ''ancar''Heyne, K. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rootkits
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed (for example, to an unauthorized user) and often masks its existence or the existence of other software. The term ''rootkit'' is a compound of "root" (the traditional name of the privileged account on Unix-like operating systems) and the word "kit" (which refers to the software components that implement the tool). The term "rootkit" has negative connotations through its association with malware. Rootkit installation can be automated, or an attacker can install it after having obtained root or administrator access. Obtaining this access is a result of direct attack on a system, i.e. exploiting a vulnerability (such as privilege escalation) or a password (obtained by cracking or social engineering tactics like "phishing"). Once installed, it becomes possible to hide the intrusion as well as to maintain privileged ac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trojan Horses
The Trojan Horse was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war. The Trojan Horse is not mentioned in Homer's ''Iliad'', with the poem ending before the war is concluded, and it is only briefly mentioned in the ''Odyssey''. But in the ''Aeneid'' by Virgil, after a fruitless 10-year siege, the Greeks constructed a huge wooden horse at the behest of Odysseus, and hid a select force of men inside, including Odysseus himself. The Greeks pretended to sail away, and the Trojans pulled the horse into their city as a victory trophy. That night, the Greek force crept out of the horse and opened the gates for the rest of the Greek army, which had sailed back under cover of darkness. The Greeks entered and destroyed the city, ending the war. Metaphorically, a "Trojan horse" has come to mean any trick or stratagem that causes a target to invite a foe into a securely protected bastion or place. A malicious computer pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows Trojans
Windows is a group of several proprietary graphical operating system families developed and marketed by Microsoft. Each family caters to a certain sector of the computing industry. For example, Windows NT for consumers, Windows Server for servers, and Windows IoT for embedded systems. Defunct Windows families include Windows 9x, Windows Mobile, and Windows Phone. The first version of Windows was released on November 20, 1985, as a graphical operating system shell for MS-DOS in response to the growing interest in graphical user interfaces (GUIs). Windows is the most popular desktop operating system in the world, with 75% market share , according to StatCounter. However, Windows is not the most used operating system when including both mobile and desktop OSes, due to Android's massive growth. , the most recent version of Windows is Windows 11 for consumer PCs and tablets, Windows 11 Enterprise for corporations, and Windows Server 2022 for servers. Genealogy B ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware Toolkits
Malware (a portmanteau for ''malicious software'') is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. By contrast, software that causes harm due to some deficiency is typically described as a software bug. Malware poses serious problems to individuals and businesses on the Internet. According to Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 669,947,865 in 2017, which is twice as many malware variants as in 2016. Cybercrime, which includes malware attacks as well as other crimes committed by computer, was predicted to cost the world economy $6 trillion USD in 2021, and is increasing at a rate of 15% per year. Many types of malware exist, including computer viruses, worms, Trojan horse ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |