|
JMP (x86 Instruction)
In the x86 assembly language, the JMP instruction performs an unconditional jump. Such an instruction transfers the flow of execution by changing the program counter. There are a number of different opcodes that perform a jump; depending on whether the processor is in real mode or protected mode, and an override instruction is used, the instructions may take 16-bit, 32-bit, or segment:offset pointers. There are many different forms of jumps: relative, conditional, absolute and register-indirect jumps. The following examples illustrate: # a relative jump with a 16-bit pointer; # a long jump (inter-segment), a relative jump with a 32-bit pointer; # and a register-indirect absolute jump using the EAX register. (Note that although the first and second jumps are relative, commonly the destination address is shown instead of the relative offset as encoded in the opcode.) Example one: Load IP with the new value 0x89AB, then load CS with 0xACDC and IP with 0x5578. JMP 0x89AB JMP 0 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
X86 Assembly Language
x86 assembly language is a family of Low-level programming language, low-level programming languages that are used to produce object code for the x86 class of processors. These languages provide backward compatibility with CPUs dating back to the Intel 8008 microprocessor, introduced in April 1972. As assembly languages, they are closely tied to the architecture's machine code instructions, allowing for precise control over hardware. In x86 assembly languages, mnemonics are used to represent fundamental CPU instructions, making the code more human-readable compared to raw machine code. Each mnemonics corresponds to a basic operation performed by the processor, such as arithmetic calculations, data movement, or Control flow, control flow decisions. Assembly languages are most commonly used in applications where performance and efficiency are critical. This includes Real-time operating system, real-time embedded systems, operating system, operating-system Kernel (operating system) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Instruction (computer Science)
In computer science, an instruction set architecture (ISA) is an abstract model that generally defines how software controls the CPU in a computer or a family of computers. A device or program that executes instructions described by that ISA, such as a central processing unit (CPU), is called an ''implementation'' of that ISA. In general, an ISA defines the supported Machine code, instructions, data types, Register (computer), registers, the hardware support for managing Computer memory, main memory, fundamental features (such as the memory consistency, addressing modes, virtual memory), and the input/output model of implementations of the ISA. An ISA specifies the behavior of machine code running on implementations of that ISA in a fashion that does not depend on the characteristics of that implementation, providing binary compatibility between implementations. This enables multiple implementations of an ISA that differ in characteristics such as Computer performance, performa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
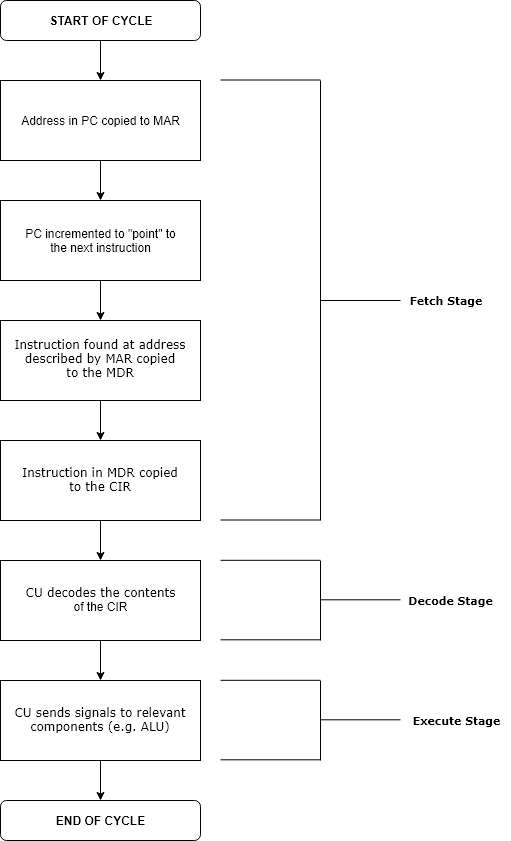
Execution (computers)
Execution in computer engineering, computer and software engineering is the process by which a computer or virtual machine interprets and acts on the instructions of a computer program. Each instruction of a program is a description of a particular action which must be carried out, in order for a specific problem to be solved. Execution involves repeatedly following a "Instruction cycle, fetch–decode–execute" cycle for each instruction done by the control unit. As the executing machine follows the instructions, specific effects are produced in accordance with the Formal semantics of programming languages, semantics of those instructions. Programs for a computer may be executed in a Batch processing, batch process without human interaction or a User (computing), user may type Command (computing), commands in an Session (computer science), interactive session of an Interpreter (computing), interpreter. In this case, the "commands" are simply program instructions, whose executio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Program Counter
The program counter (PC), commonly called the instruction pointer (IP) in Intel x86 and Itanium microprocessors, and sometimes called the instruction address register (IAR), the instruction counter, or just part of the instruction sequencer, is a processor register that indicates where a computer is in its program sequence. Usually, the PC is incremented after fetching an instruction, and holds the memory address of (" points to") the next instruction that would be executed. Processors usually fetch instructions sequentially from memory, but ''control transfer'' instructions change the sequence by placing a new value in the PC. These include branches (sometimes called jumps), subroutine calls, and returns. A transfer that is conditional on the truth of some assertion lets the computer follow a different sequence under different conditions. A branch provides that the next instruction is fetched from elsewhere in memory. A subroutine call not only branches but saves the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Opcode
In computing, an opcode (abbreviated from operation code) is an enumerated value that specifies the operation to be performed. Opcodes are employed in hardware devices such as arithmetic logic units (ALUs), central processing units (CPUs), and software instruction sets. In ALUs, the opcode is directly applied to circuitry via an input signal bus. In contrast, in CPUs, the opcode is the portion of a machine language instruction that specifies the operation to be performed. CPUs Opcodes are found in the machine language instructions of CPUs as well as in some abstract computing machines. In CPUs, an opcode may be referred to as an instruction machine code, instruction code, instruction syllable, instruction parcel, or opstring. For any particular processor (which may be a general CPU or a more specialized processing unit), the opcodes are defined by the processor's instruction set architecture (ISA). They can be described using an opcode table. The types of operations may in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Real Mode
Real mode, also called real address mode, is an operating mode of all x86-compatible CPUs. The mode gets its name from the fact that addresses in real mode always correspond to real locations in memory. Real mode is characterized by a 20- bit segmented memory address space (giving 1 MB of addressable memory) and unlimited direct software access to all addressable memory, I/O addresses and peripheral hardware. Real mode provides no support for memory protection, multitasking, or code privilege levels. Before the introduction of protected mode with the release of the 80286, real mode was the only available mode for x86 CPUs; and for backward compatibility, all x86 CPUs start in real mode when reset, though it is possible to emulate real mode on other systems when starting in other modes. History The 80286 architecture introduced protected mode, allowing for (among other things) hardware-level memory protection. Using these new features, however, required a new operating system ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Protected Mode
In computing, protected mode, also called protected virtual address mode, is an operational mode of x86-compatible central processing units (CPUs). It allows system software to use features such as Memory_segmentation, segmentation, virtual memory, paging and safe computer multitasking, multi-tasking designed to increase an operating system's control over application software. When a processor that supports x86 protected mode is powered on, it begins executing instructions in real mode, in order to maintain backward compatibility with earlier x86 processors. Protected mode may only be entered after the system software sets up one descriptor table and enables the Protection Enable (PE) bit in the control register 0 (CR0). Protected mode was first added to the x86 architecture in 1982, with the release of Intel's 80286 (286) processor, and later extended with the release of the 80386 (386) in 1985. Due to the enhancements added by protected mode, it has become widely adopted and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
16-bit
16-bit microcomputers are microcomputers that use 16-bit microprocessors. A 16-bit register can store 216 different values. The range of integer values that can be stored in 16 bits depends on the integer representation used. With the two most common representations, the range is 0 through 65,535 (216 − 1) for representation as an ( unsigned) binary number, and −32,768 (−1 × 215) through 32,767 (215 − 1) for representation as two's complement. Since 216 is 65,536, a processor with 16-bit memory addresses can directly access 64 KB (65,536 bytes) of byte-addressable memory. If a system uses segmentation with 16-bit segment offsets, more can be accessed. As of 2025, 16-bit microcontrollers cost well under a dollar (similar to close in price legacy 8-bit); the cheapest 16-bit microcontrollers cost less than other types including any 8-bit (and are more powerful, and easier to program generally), making 8-bit legacy microcontrollers not worth it for new applicatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
32-bit
In computer architecture, 32-bit computing refers to computer systems with a processor, memory, and other major system components that operate on data in a maximum of 32- bit units. Compared to smaller bit widths, 32-bit computers can perform large calculations more efficiently and process more data per clock cycle. Typical 32-bit personal computers also have a 32-bit address bus, permitting up to 4 GiB of RAM to be accessed, far more than previous generations of system architecture allowed. 32-bit designs have been used since the earliest days of electronic computing, in experimental systems and then in large mainframe and minicomputer systems. The first hybrid 16/32-bit microprocessor, the Motorola 68000, was introduced in the late 1970s and used in systems such as the original Apple Macintosh. Fully 32-bit microprocessors such as the HP FOCUS, Motorola 68020 and Intel 80386 were launched in the early to mid 1980s and became dominant by the early 1990s. This gener ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pointer (computer Programming)
In computer science, a pointer is an object in many programming languages that stores a memory address. This can be that of another value located in computer memory, or in some cases, that of memory-mapped computer hardware. A pointer ''references'' a location in memory, and obtaining the value stored at that location is known as ''dereferencing'' the pointer. As an analogy, a page number in a book's index could be considered a pointer to the corresponding page; dereferencing such a pointer would be done by flipping to the page with the given page number and reading the text found on that page. The actual format and content of a pointer variable is dependent on the underlying computer architecture. Using pointers significantly improves performance for repetitive operations, like traversing iterable data structures (e.g. strings, lookup tables, control tables, linked lists, and tree structures). In particular, it is often much cheaper in time and space to copy and deref ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |