|
Integer Overflow
In computer programming, an integer overflow occurs when an arithmetic operation on integers attempts to create a numeric value that is outside of the range that can be represented with a given number of digits – either higher than the maximum or lower than the minimum representable value. The most common result of an overflow is that the least significant representable digits of the result are stored; the result is said to ''wrap'' around the maximum (i.e. modulo a power of the radix, usually two in modern computers, but sometimes ten or other number). On some processors like graphics processing units (GPUs) and digital signal processors (DSPs) which support saturation arithmetic, overflowed results would be ''clamped'', i.e. set to the minimum value in the representable range if the result is below the minimum and set to the maximum value in the representable range if the result is above the maximum, rather than wrapped around. An overflow condition may give results lead ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Odometer Rollover
An odometer or odograph is an instrument used for measuring the distance traveled by a vehicle, such as a bicycle or car. The device may be electronic, mechanical, or a combination of the two (electromechanical). The noun derives from ancient Greek , ''hodómetron'', from , ''hodós'' ("path" or "gateway") and , ''métron'' ("measure"). Early forms of the odometer existed in the ancient Greco-Roman world as well as in ancient China. In countries using Imperial units or US customary units it is sometimes called a mileometer or milometer, the former name especially being prevalent in the United Kingdom and among members of the Commonwealth. History Classical Era Possibly the first evidence for the use of an odometer can be found in the works of the ancient Roman Pliny (NH 6. 61-62) and the ancient Greek Strabo (11.8.9). Both authors list the distances of routes traveled by Alexander the Great (r. 336-323 BC) as by his bematists Diognetus and Baeton. However, the high accu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
64-bit Computing
In computer architecture, 64-bit integers, memory addresses, or other data units are those that are 64 bits wide. Also, 64-bit central processing units (CPU) and arithmetic logic units (ALU) are those that are based on processor registers, address buses, or data buses of that size. A computer that uses such a processor is a 64-bit computer. From the software perspective, 64-bit computing means the use of machine code with 64-bit virtual memory addresses. However, not all 64-bit instruction sets support full 64-bit virtual memory addresses; x86-64 and AArch64, for example, support only 48 bits of virtual address, with the remaining 16 bits of the virtual address required to be all zeros (000...) or all ones (111...), and several 64-bit instruction sets support fewer than 64 bits of physical memory address. The term ''64-bit'' also describes a generation of computers in which 64-bit processors are the norm. 64 bits is a Word (computer architecture), word size that defines ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ada (programming Language)
Ada is a structured, statically typed, imperative, and object-oriented high-level programming language, inspired by Pascal and other languages. It has built-in language support for '' design by contract'' (DbC), extremely strong typing, explicit concurrency, tasks, synchronous message passing, protected objects, and non-determinism. Ada improves code safety and maintainability by using the compiler to find errors in favor of runtime errors. Ada is an international technical standard, jointly defined by the International Organization for Standardization (ISO), and the International Electrotechnical Commission (IEC). , the standard, ISO/IEC 8652:2023, is called Ada 2022 informally. Ada was originally designed by a team led by French computer scientist Jean Ichbiah of Honeywell under contract to the United States Department of Defense (DoD) from 1977 to 1983 to supersede over 450 programming languages then used by the DoD. Ada was named after Ada Lovelace (1815–185 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Undefined Behavior
In computer programming, a program exhibits undefined behavior (UB) when it contains, or is executing code for which its programming language specification does not mandate any specific requirements. This is different from unspecified behavior, for which the language specification does not prescribe a result, and implementation-defined behavior that defers to the documentation of another component of the platform (such as the ABI or the translator documentation). In the C programming community, undefined behavior may be humorously referred to as "nasal demons", after a comp.std.c post that explained undefined behavior as allowing the compiler to do anything it chooses, even "to make demons fly out of your nose". Overview Some programming languages allow a program to operate differently or even have a different control flow from the source code, as long as it exhibits the same user-visible side effects, ''if undefined behavior never happens during program execution''. Undef ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rust (programming Language)
Rust is a General-purpose programming language, general-purpose programming language emphasizing Computer performance, performance, type safety, and Concurrency (computer science), concurrency. It enforces memory safety, meaning that all Reference (computer science), references point to valid memory. It does so without a conventional Garbage collection (computer science), garbage collector; instead, memory safety errors and data races are prevented by the "borrow checker", which tracks the object lifetime of references Compiler, at compile time. Rust does not enforce a programming paradigm, but was influenced by ideas from functional programming, including Immutable object, immutability, higher-order functions, algebraic data types, and pattern matching. It also supports object-oriented programming via structs, Enumerated type, enums, traits, and methods. It is popular for systems programming. Software developer Graydon Hoare created Rust as a personal project while working at ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
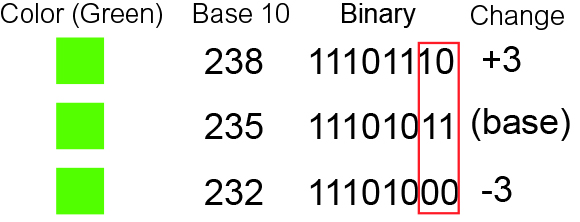
Overflow Flag
In computer processors, the overflow flag (sometimes called the V flag) is usually a single bit in a system status register used to indicate when an arithmetic overflow has occurred in an operation, indicating that the signed two's-complement result would not fit in the number of bits used for the result. Some architectures may be configured to automatically generate an exception on an operation resulting in overflow. An example, suppose we add 127 and 127 using 8-bit registers. 127+127 is 254, but using 8-bit arithmetic the result would be 1111 1110 binary, which is the two's complement encoding of −2, a negative number. A negative sum of positive operands (or vice versa) is an overflow. The overflow flag would then be set so the program can be aware of the problem and mitigate this or signal an error. The overflow flag is thus set when the most significant bit (here considered the sign bit) is changed by adding two numbers with the same sign (or subtracting two numbers with ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Most Significant Bit
In computing, bit numbering is the convention used to identify the bit positions in a binary numeral system, binary number. Bit significance and indexing In computing, the least significant bit (LSb) is the bit position in a Binary numeral system, binary Integer (computer science), integer representing the lowest-order place of the integer. Similarly, the most significant bit (MSb) represents the highest-order place of the binary integer. The LSb is sometimes referred to as the ''low-order bit''. Due to the convention in positional notation of writing less significant digits further to the right, the LSb also might be referred to as the ''right-most bit''. The MSb is similarly referred to as the ''high-order bit'' or ''left-most bit''. In both cases, the LSb and MSb correlate directly to the least significant Numerical digit, digit and most significant digit of a decimal integer. Bit indexing correlates to the positional notation of the value in base 2. For this reason, bit in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Carry (arithmetic)
In elementary arithmetic, a carry is a Numerical digit, digit that is transferred from one column of digits to another column of more significant digits. It is part of the standard algorithm to addition, add numbers together by starting with the rightmost digits and working to the left. For example, when 6 and 7 are added to make 13, the "3" is written to the same column and the "1" is carried to the left. When used in subtraction the operation is called a borrow. Carrying is emphasized in traditional mathematics, while curricula based on reform mathematics do not emphasize any specific method to find a correct answer. Carrying makes a few appearances in higher mathematics as well. In computing, carrying is an important function of adder (electronics), adder circuits. Manual arithmetic A typical example of carry is in the following pencil-and-paper addition: 1 27 + 59 ---- 86 7 + 9 = 16, and the digit 1 (number), 1 is the carry. The opposite is a borrow, as in − ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Carry Flag
In computer processors, the carry flag (usually indicated as the C flag) is a single bit in a system status register A status register, flag register, or condition code register (CCR) is a collection of status Flag (computing), flag bits for a Central processing unit, processor. Examples of such registers include FLAGS register (computing), FLAGS register in the .../flag register used to indicate when an arithmetic carry (arithmetic), carry or borrow has been generated out of the most significant bit, most significant arithmetic logic unit (ALU) bit position. The carry flag enables numbers larger than a single ALU width to be added/subtracted by carrying (adding) a binary digit from a partial addition/subtraction to the least significant bit position of a more significant word. This is typically programmed by the user of the processor on the assembly or machine code level, but can also happen internally in certain processors, via digital logic or microcode, where some processors ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Signed Number Representations
In computing, signed number representations are required to encode negative numbers in binary number systems. In mathematics, negative numbers in any base are represented by prefixing them with a minus sign ("−"). However, in RAM or CPU registers, numbers are represented only as sequences of bits, without extra symbols. The four best-known methods of extending the binary numeral system to represent signed numbers are: sign–magnitude, ones' complement, two's complement, and offset binary. Some of the alternative methods use implicit instead of explicit signs, such as negative binary, using the base −2. Corresponding methods can be devised for other bases, whether positive, negative, fractional, or other elaborations on such themes. There is no definitive criterion by which any of the representations is universally superior. For integers, the representation used in most current computing devices is two's complement, although the Unisys ClearPath Dorado series mainf ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Two's Complement
Two's complement is the most common method of representing signed (positive, negative, and zero) integers on computers, and more generally, fixed point binary values. Two's complement uses the binary digit with the ''greatest'' value as the ''sign'' to indicate whether the binary number is positive or negative; when the most significant bit is ''1'' the number is signed as negative and when the most significant bit is ''0'' the number is signed as positive. As a result, non-negative numbers are represented as themselves: 6 is 0110, zero is 0000, and −6 is 1010 (the result of applying the bitwise NOT operator to 6 and adding 1). However, while the number of binary bits is fixed throughout a computation it is otherwise arbitrary. Unlike the ones' complement scheme, the two's complement scheme has only one representation for zero. Furthermore, arithmetic implementations can be used on signed as well as unsigned integers and differ only in the integer overflow situations. Proce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |