|
IEEE 802.22
IEEE 802.22, is a standard for wireless regional area network (WRAN) using white spaces in the television (TV) frequency spectrum. The development of the IEEE 802.22 WRAN standard is aimed at using cognitive radio (CR) techniques to allow sharing of geographically unused spectrum allocated to the television broadcast service, on a non-interfering basis, to bring broadband access to hard-to-reach, low population density areas, typical of rural environments, and is therefore timely and has the potential for a wide applicability worldwide. It is the first worldwide effort to define a standardized air interface based on CR techniques for the opportunistic use of TV bands on a non-interfering basis. IEEE 802.22 WRANs are designed to operate in the TV broadcast bands while assuring that no harmful interference is caused to the incumbent operation: digital TV and analog TV broadcasting, and low power licensed devices such as wireless microphones. The standard was expected to be finalize ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
International Standard
international standard is a technical standard developed by one or more international standards organization, standards organizations. International standards are available for consideration and use worldwide. The most prominent such organization is the International Organization for Standardization (ISO). Other prominent international standards organizations including the International Telecommunication Union (ITU) and the International Electrotechnical Commission (IEC). Together, these three organizations have formed the World Standards Cooperation alliance. Purpose International standards may be used either by direct application or by a process of modifying an international standard to suit local conditions. Adopting international standards results in creating national standards that are equivalent, or substantially the same as international standards in technical content, but may have (i) editorial differences as to appearance, use of symbols and measurement units, substitution ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
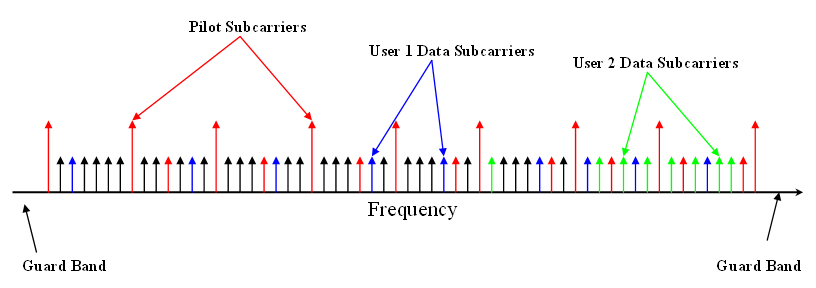
OFDMA
Orthogonal frequency-division multiple access (OFDMA) is a multi-user version of the popular orthogonal frequency-division multiplexing (OFDM) digital modulation scheme. Multiple access is achieved in OFDMA by assigning subsets of subcarriers to individual users. This allows simultaneous low-data-rate transmission from several users. Comparisons OFDMA is often compared to the combination of OFDM with statistical time-division multiplexing. The advantages and disadvantages summarized below are further discussed in the Characteristics and principles of operation section. See also the list of OFDM key features. Advantages * Allows simultaneous low-data-rate transmission from several users. * Pulsed carrier can be avoided. * Lower maximal transmission power for low-data-rate users. * Shorter delay and constant delay. * Contention-based multiple access (collision avoidance) is simplified. * Further improves OFDM robustness to fading and interference. * Combat narrow-band in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SIM Lock
SIM lock, simlock, network lock, carrier lock or (master) subsidy lock is a technical restriction built into GSM and CDMA mobile phones by mobile phone manufacturers for use by service providers to restrict the use of these phones to specific countries and/or networks. This is in contrast to a phone (retrospectively called SIM-free or unlocked) that does not impose any SIM restrictions. Generally phones can be locked to accept only SIM cards with certain International Mobile Subscriber Identities (IMSIs); IMSIs may be restricted by: * Mobile country code (MCC; e.g., will only work with SIM issued in one country) * Mobile network code (MNC; e.g., AT&T Mobility, T-Mobile, Vodafone, Bell Mobility etc.) * Mobile subscriber identification number (MSIN; i.e., only one SIM can be used with the phone) Additionally, some phones, especially Nokia phones, are locked by group IDs (GIDs), restricting them to a single Mobile virtual network operator (MVNO) of a certain operator. Most mo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Certificate Authority
In cryptography, a certificate authority or certification authority (CA) is an entity that stores, signs, and issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. A CA acts as a trusted third party—trusted both by the subject (owner) of the certificate and by the party relying upon the certificate. The format of these certificates is specified by the X.509 or EMV standard. One particularly common use for certificate authorities is to sign certificates used in HTTPS, the secure browsing protocol for the World Wide Web. Another common use is in issuing identity cards by national governments for use in electronically signing documents. Overview Trusted certificates can be used to create secure connections to a server via the Internet. A certificate ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chain Of Trust
In computer security, a chain of trust is established by validating each component of hardware and software from the end entity up to the root certificate. It is intended to ensure that only trusted software and hardware can be used while still retaining flexibility. Introduction A chain of trust is designed to allow multiple users to create and use software on the system, which would be more difficult if all the keys were stored directly in hardware. It starts with hardware that will only boot from software that is digitally signed. The signing authority will only sign boot programs that enforce security, such as only running programs that are themselves signed, or only allowing signed code to have access to certain features of the machine. This process may continue for several layers. This process results in a chain of trust. The final software can be trusted to have certain properties, because if it had been illegally modified its signature would be invalid, and the previous ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Vendor Lock-in
In economics, vendor lock-in, also known as proprietary lock-in or customer lock-in, makes a customer dependent on a vendor for products, unable to use another vendor without substantial switching costs. The use of open standards and alternative options makes systems tolerant of change, so that decisions can be postponed until more information is available or unforeseen events are addressed. Vendor lock-in does the opposite: it makes it difficult to move from one solution to another. Lock-in costs that create barriers to market entry may result in antitrust action against a monopoly. Lock-in types ; Monopolistic : Whether a single vendor controls the market for the method or technology being locked in to. Distinguishes between being locked to the mere technology, or specifically the vendor of it. This class of lock-in is potentially technologically hard to overcome if the monopoly is held up by barriers to market that are nontrivial to circumvent, such as patents, secre ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MAC Address
A media access control address (MAC address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment. This use is common in most IEEE 802 networking technologies, including Ethernet, Wi-Fi, and Bluetooth. Within the Open Systems Interconnection (OSI) network model, MAC addresses are used in the medium access control protocol sublayer of the data link layer. As typically represented, MAC addresses are recognizable as six groups of two hexadecimal digits, separated by hyphens, colons, or without a separator. MAC addresses are primarily assigned by device manufacturers, and are therefore often referred to as the burned-in address, or as an Ethernet hardware address, hardware address, or physical address. Each address can be stored in hardware, such as the card's read-only memory, or by a firmware mechanism. Many network interfaces, however, support changing their MAC address. The address ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authorization
Authorization or authorisation (see spelling differences) is the function of specifying access rights/privileges to resources, which is related to general information security and computer security, and to access control in particular. More formally, "to authorize" is to define an access policy. For example, human resources staff are normally authorized to access employee records and this policy is often formalized as access control rules in a computer system. During operation, the system uses the access control rules to decide whether access requests from ( authenticated) consumers shall be approved (granted) or disapproved (rejected). Resources include individual files or an item's data, computer programs, computer devices and functionality provided by computer applications. Examples of consumers are computer users, computer software and other hardware on the computer. Overview Access control in computer systems and networks rely on access policies. The access control p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authentication
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. It might involve validating personal identity documents, verifying the authenticity of a website with a digital certificate, determining the age of an artifact by carbon dating, or ensuring that a product or document is not counterfeit. Methods Authentication is relevant to multiple fields. In art, antiques, and anthropology, a common problem is verifying that a given artifact was produced by a certain person or in a certain place or period of history. In computer science, verifying a user's identity is often required to allow access to confidential data or systems. Authentication can be considered to be of three types: The first type of a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
EAP-TTLS
Extensible Authentication Protocol (EAP) is an authentication framework frequently used in network and internet connections. It is defined in , which made obsolete, and is updated by . EAP is an authentication framework for providing the transport and usage of material and parameters generated by EAP methods. There are many methods defined by RFCs, and a number of vendor-specific methods and new proposals exist. EAP is not a wire protocol; instead it only defines the information from the interface and the formats. Each protocol that uses EAP defines a way to encapsulate by the user EAP messages within that protocol's messages. EAP is in wide use. For example, in IEEE 802.11 (WiFi) the WPA and WPA2 standards have adopted IEEE 802.1X (with various EAP types) as the canonical authentication mechanism. Methods EAP is an authentication framework, not a specific authentication mechanism. It provides some common functions and negotiation of authentication methods called EAP methods. Ther ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authenticated Encryption
Authenticated Encryption (AE) and Authenticated Encryption with Associated Data (AEAD) are forms of encryption which simultaneously assure the confidentiality and authenticity of data. Programming interface A typical programming interface for an AE implementation provides the following functions: * Encryption ** Input: ''plaintext'', ''key'', and optionally a ''header'' in plaintext that will not be encrypted, but will be covered by authenticity protection. ** Output: ''ciphertext'' and ''authentication tag'' ( message authentication code or MAC). * Decryption ** Input: ''ciphertext'', ''key'', ''authentication tag'', and optionally a ''header'' (if used during the encryption). ** Output: ''plaintext'', or an error if the ''authentication tag'' does not match the supplied ''ciphertext'' or ''header''. The ''header'' part is intended to provide authenticity and integrity protection for networking or storage metadata for which confidentiality is unnecessary, but authenticity is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |