|
IBM Israel
IBM is a globally integrated enterprise operating in 170 countries. IBM's R&D history in Israel began in 1972 when Professor Josef Raviv established the IBM Israel Scientific Center in the Technion's Computer Science Building in Haifa. Today, over 1000 individuals work at IBM R&D locations across Israel, including Haifa, Tel Aviv, Herzliya, Rehovot, and the Jerusalem Technology Park. IBM research and development activities in Israel include a number of labs. Haifa Research Lab IBM Haifa Research Laboratory (HRL) is located in Haifa, Israel. It is an IBM R&D Lab in Israel. It handles projects in the spheres of cloud computing, healthcare and life sciences, verification technologies, multimedia, event processing, information retrieval, programming environments, business transformation, and optimization technologies. HRL is the biggest IBM research center outside the US. Established back in 1972 as the IBM Israel Scientific Center, the IBM Haifa Research Lab has grown fro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Business Transformation
In management it has been said that business transformation involves making fundamental changes in how business is conducted in order to help cope with shifts in market environment. However this is a relatively narrow definition that overlooks other reasons and ignores other rationales. A better understanding is achieved by considering that "transformation .is generally a response to two things. First, there are underlying problems or causes of organisational pain that need to be addressed. They have to be properly understood but nevertheless they are a key component. Second, there is a desire by the top management and other senior stakeholders to use the opportunity of addressing these causes in ways that fundamentally alter the paradigm of the organisation." Others describe Business Transformation as "the process of fundamentally changing the systems, processes, people and technology across a whole business or business unit. As such, a business transformation project is likely ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rational Software
Rational Machines is an enterprise founded by Paul Levy and Mike Devlin in 1981 to provide tools to expand the use of modern software engineering practices, particularly explicit modular architecture and iterative development. It changed its name in 1994 to Rational Software, and was sold for US$2.1 billion (equivalent to current US$) to IBM on February 20, 2003. See also *Rational Automation Framework *Rational ClearCase * Rational DOORS *Rational Performance Tester *Rational Rhapsody * Rational Rose *Rational Software Architect * Rational Software Modeler *Rational Synergy *Rational Unified Process The Rational Unified Process (RUP) is an iterative software development process framework created by the Rational Software Corporation, a division of IBM since 2003. RUP is not a single concrete prescriptive process, but rather an adaptable pro ... References External links {{Authority control Defunct software companies IBM acquisitions ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IBM Information Management System
The IBM Information Management System (IMS) is a joint hierarchical database and information management system that supports transaction processing. History IBM designed the IMS with Rockwell and Caterpillar starting in 1966 for the Apollo program, where it was used to inventory the very large bill of materials (BOM) for the Saturn V moon rocket and Apollo space vehicle. The first "IMS READY" message appeared on an IBM 2740 terminal in Downey, California, on August 14, 1968. In the interim period, IMS has undergone many developments as IBM System/360 technology evolved into the current z/OS and IBM zEnterprise System technologies. For example, IMS now supports the Java programming language, JDBC, XML, and, since late 2005, web services. Vern Watts was IMS's chief architect for many years. Watts joined IBM in 1956 and worked at IBM's Silicon Valley development labs until his death on April 4, 2009. He had continuously worked on IMS since the 1960s. Database The IMS D ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Lotus Sametime
HCL Sametime Premium (formerly IBM Sametime and IBM Lotus Sametime) is a client–server application and middleware platform that provides real-time, unified communications and collaboration for enterprises. Those capabilities include presence information, enterprise instant messaging, web conferencing, community collaboration, and telephony capabilities and integration. Currently it is developed and sold by HCL Software, a division of Indian company HCL Technologies, until 2019 by the Lotus Software division of IBM. Because HCL Sametime is middleware, it supports enterprise software and business process integration ( Communication Enabled Business Process), either through an HCL Sametime plugin or by surfacing HCL Sametime capabilities through third-party applications. HCL Sametime integrates with a wide variety of software, including Lotus collaboration products, Microsoft Office productivity software, and portal and Web applications. Features HCL Sametime Premium Features: ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Service-oriented Architecture
In software engineering, service-oriented architecture (SOA) is an architectural style that focuses on discrete services instead of a monolithic design. By consequence, it is also applied in the field of software design where services are provided to the other components by application components, through a communication protocol over a network. A service is a discrete unit of functionality that can be accessed remotely and acted upon and updated independently, such as retrieving a credit card statement online. SOA is also intended to be independent of vendors, products and technologies. Service orientation is a way of thinking in terms of services and service-based development and the outcomes of services. A service has four properties according to one of many definitions of SOA: # It logically represents a repeatable business activity with a specified outcome. # It is self-contained. # It is a black box for its consumers, meaning the consumer does not have to be aware of the ser ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Application Security
Application security (short AppSec) includes all tasks that introduce a secure software development life cycle to development teams. Its final goal is to improve security practices and, through that, to find, fix and preferably prevent security issues within applications. It encompasses the whole application life cycle from requirements analysis, design, implementation, verification as well as maintenance. Approaches Different approaches will find different subsets of the security vulnerabilities lurking in an application and are most effective at different times in the software lifecycle. They each represent different tradeoffs of time, effort, cost and vulnerabilities found. * Design review. Before code is written the application's architecture and design can be reviewed for security problems. A common technique in this phase is the creation of a threat model. * Whitebox security review, or code review. This is a security engineer deeply understanding the application through ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Metadata
Metadata is "data that provides information about other data", but not the content of the data, such as the text of a message or the image itself. There are many distinct types of metadata, including: * Descriptive metadata – the descriptive information about a resource. It is used for discovery and identification. It includes elements such as title, abstract, author, and keywords. * Structural metadata – metadata about containers of data and indicates how compound objects are put together, for example, how pages are ordered to form chapters. It describes the types, versions, relationships, and other characteristics of digital materials. * Administrative metadata – the information to help manage a resource, like resource type, permissions, and when and how it was created. * Reference metadata – the information about the contents and quality of Statistical data type, statistical data. * Statistical metadata – also called process data, may describe processes that collect, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
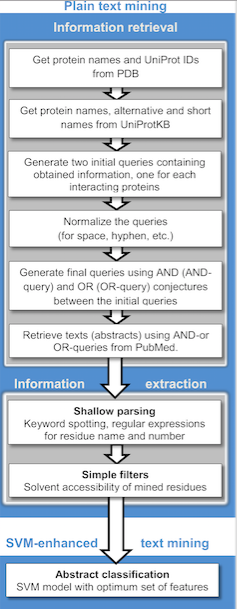
Text Analytics
Text mining, also referred to as ''text data mining'', similar to text analytics, is the process of deriving high-quality information from text. It involves "the discovery by computer of new, previously unknown information, by automatically extracting information from different written resources." Written resources may include websites, books, emails, reviews, and articles. High-quality information is typically obtained by devising patterns and trends by means such as statistical pattern learning. According to Hotho et al. (2005) we can distinguish between three different perspectives of text mining: information extraction, data mining, and a KDD (Knowledge Discovery in Databases) process. Text mining usually involves the process of structuring the input text (usually parsing, along with the addition of some derived linguistic features and the removal of others, and subsequent insertion into a database), deriving patterns within the structured data, and finally evaluation and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Deduplication
In computing, data deduplication is a technique for eliminating duplicate copies of repeating data. Successful implementation of the technique can improve storage utilization, which may in turn lower capital expenditure by reducing the overall amount of storage media required to meet storage capacity needs. It can also be applied to network data transfers to reduce the number of bytes that must be sent. The deduplication process requires comparison of data 'chunks' (also known as 'byte patterns') which are unique, contiguous blocks of data. These chunks are identified and stored during a process of analysis, and compared to other chunks within existing data. Whenever a match occurs, the redundant chunk is replaced with a small reference that points to the stored chunk. Given that the same byte pattern may occur dozens, hundreds, or even thousands of times (the match frequency is dependent on the chunk size), the amount of data that must be stored or transferred can be greatly reduc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Data Storage
Computer data storage is a technology consisting of computer components and recording media that are used to retain digital data. It is a core function and fundamental component of computers. The central processing unit (CPU) of a computer is what manipulates data by performing computations. In practice, almost all computers use a storage hierarchy, which puts fast but expensive and small storage options close to the CPU and slower but less expensive and larger options further away. Generally, the fast volatile technologies (which lose data when off power) are referred to as "memory", while slower persistent technologies are referred to as "storage". Even the first computer designs, Charles Babbage's Analytical Engine and Percy Ludgate's Analytical Machine, clearly distinguished between processing and memory (Babbage stored numbers as rotations of gears, while Ludgate stored numbers as displacements of rods in shuttles). This distinction was extended in the Von Neuma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |