|
IBM API Management
IBM API Management (with version 5 renamed to IBM API Connect) is an API Management platform for use in the API Economy. IBM API Connect enables users to create, assemble, manage, secure and socialize web application programming interfaces (APIs). It runs as a Virtual appliance on a Virtual machine and uses the IBM WebSphere DataPower SOA Appliances as gateways. It provides a developer portal for application developers and to view published APIs. An administration portal allows users to establish policies for APIs such as self-registration, quotas, key management and security policies. An analytics engine provides role-based analytics for API owners, solution administrators and application developers in order to manage APIs and ensure service levels are being achieved. There is also a service called Cloud Manager where the platform is set up with servers, clusters, gateways, user repositories, etc. Swagger (now called OpenAPI) and WSDL documents can be loaded and parsed into ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Appliance
A virtual appliance is a pre-configured virtual machine image, ready to run on a hypervisor; virtual appliances are a subset of the broader class of software appliances. Installation of a software appliance on a virtual machine and packaging that into an image creates a virtual appliance. Like software appliances, virtual appliances are intended to eliminate the installation, configuration and maintenance costs associated with running complex stacks of software. A virtual appliance is not a complete virtual machine platform, but rather a software image containing a software stack designed to run on a virtual machine platform which may be a Type 1 or Type 2 hypervisor. File formats Virtual appliances are provided to the user or customer as files, via either electronic downloads or physical distribution. The file format most commonly used is the Open Virtualization Format (OVF). It may also be distributed as Open Virtual Appliance (OVA), the .ova file format is interchangeable wi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Docker (software)
Docker is a set of platform as a service (PaaS) products that use OS-level virtualization to deliver software in packages called ''containers''. The service has both free and premium tiers. The software that hosts the containers is called Docker Engine. It was first released in 2013 and is developed by Docker, Inc. Docker is a tool that is used to automate the deployment of applications in lightweight containers so that applications can work efficiently in different environments in isolation. Background Containers are isolated from one another and bundle their own software, libraries and configuration files; they can communicate with each other through well-defined channels. Because all of the containers share the services of a single operating system kernel, they use fewer resources than virtual machines. Operation Docker can package an application and its dependencies in a virtual container that can run on any Linux, Windows, or macOS computer. This enables the appli ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Machine
In computing, a virtual machine (VM) is the virtualization or emulator, emulation of a computer system. Virtual machines are based on computer architectures and provide the functionality of a physical computer. Their implementations may involve specialized hardware, software, or a combination of the two. Virtual machines differ and are organized by their function, shown here: * ''System virtual machines'' (also called full virtualization VMs, or SysVMs) provide a substitute for a real machine. They provide the functionality needed to execute entire operating systems. A hypervisor uses native code, native execution to share and manage hardware, allowing for multiple environments that are isolated from one another yet exist on the same physical machine. Modern hypervisors use hardware-assisted virtualization, with virtualization-specific hardware features on the host CPUs providing assistance to hypervisors. * ''Process virtual machines'' are designed to execute computer programs ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IBM WebSphere DataPower SOA Appliances
IBM WebSphere DataPower SOA Appliances is a family of pre-built, pre-configured rack-mountable network devices (XML appliances) designed to accelerate XML and Web Services deployments while extending SOA infrastructure. Originally these devices were created by DataPower Technology Inc., which was acquired by IBM in October 2005. This WebSphere family consists of hardware and virtual appliances. The appliances are designed to be scalable, with options for high availability and clustering for increased performance and reliability. Appliance list Based on Hardware Model 9235 * WebSphere DataPower Caching Appliance XC10 * WebSphere DataPower XML Accelerator XA35 * WebSphere DataPower Security Appliance XS40 * WebSphere DataPower Integration Appliance XI50 * WebSphere DataPower B2B Appliance XB60 * WebSphere DataPower Messaging Appliance XM70 This hardware model is a 1U rack mountable appliance that has four Gigabit Ethernet connections. Based on Hardware Model 7198 * WebSphere ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Key Management
Key management refers to management of Key (cryptography), cryptographic keys in a cryptosystem. This includes dealing with the generation, exchange, storage, use, crypto-shredding (destruction) and replacement of keys. It includes cryptographic protocol design, Key server (cryptographic), key servers, user procedures, and other relevant protocols. Key management concerns keys at the user level, either between users or systems. This is in contrast to key scheduling, which typically refers to the internal handling of keys within the operation of a cipher. Successful key management is critical to the security of a cryptosystem. It is the more challenging side of cryptography in a sense that it involves aspects of social engineering such as system policy, user training, organizational and departmental interactions, and coordination between all of these elements, in contrast to pure mathematical practices that can be automated. Types of keys Cryptographic systems may use different ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Swagger (computer Science)
The OpenAPI Specification, previously known as the Swagger Specification, is a specification for a machine-readable interface definition language for describing, producing, consuming and visualizing web services. Originally developed to support the Swagger framework, it became a separate project in 2015, overseen by the OpenAPI Initiative, an open-source collaboration project of the Linux Foundation. An OpenAPI Description (OAD) represents a formal description of an API that tools can use to generate code, documentation, test cases, and more. History Swagger development began in early 2010 by Tony Tam, who was working at online dictionary company Wordnik. In March 2015, SmartBear Software acquired the open-source Swagger API specification from Reverb Technologies, Wordnik's parent company. In November 2015, SmartBear announced that it was donating the Swagger specification to a new organization called the OpenAPI Initiative, under the sponsorship of the Linux Foundation. O ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
WSDL
The Web Services Description Language (WSDL ) is an XML-based interface description language that is used for describing the functionality offered by a web service. The acronym is also used for any specific WSDL description of a web service (also referred to as a ''WSDL file''), which provides a machine-readable description of how the service can be called, what parameters it expects, and what data structures it returns. Therefore, its purpose is roughly like a type signature in a programming language. The latest version of WSDL, which became a W3C recommendation in 2007, is WSDL 2.0. The meaning of the acronym has changed from version 1.1 where the "D" stood for "Definition". Description The WSDL describes services as collections of network endpoints, or ports. The WSDL specification provides an XML format for documents for this purpose. The abstract definitions of ports and messages are separated from their concrete use or instance, allowing the reuse of these definitions. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
REST
REST (Representational State Transfer) is a software architectural style that was created to describe the design and guide the development of the architecture for the World Wide Web. REST defines a set of constraints for how the architecture of a distributed, Internet-scale hypermedia system, such as the Web, should behave. The REST architectural style emphasises uniform API, interfaces, independent deployment of Software component, components, the scalability of interactions between them, and creating a Multitier architecture, layered architecture to promote caching to reduce user-perceived latency (engineering), latency, enforce computer security, security, and encapsulate legacy systems. REST has been employed throughout the software industry to create stateless protocol, stateless, reliable, web application, web-based applications. An application that adheres to the #Architectural constraints, REST architectural constraints may be informally described as ''RESTful'', althoug ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
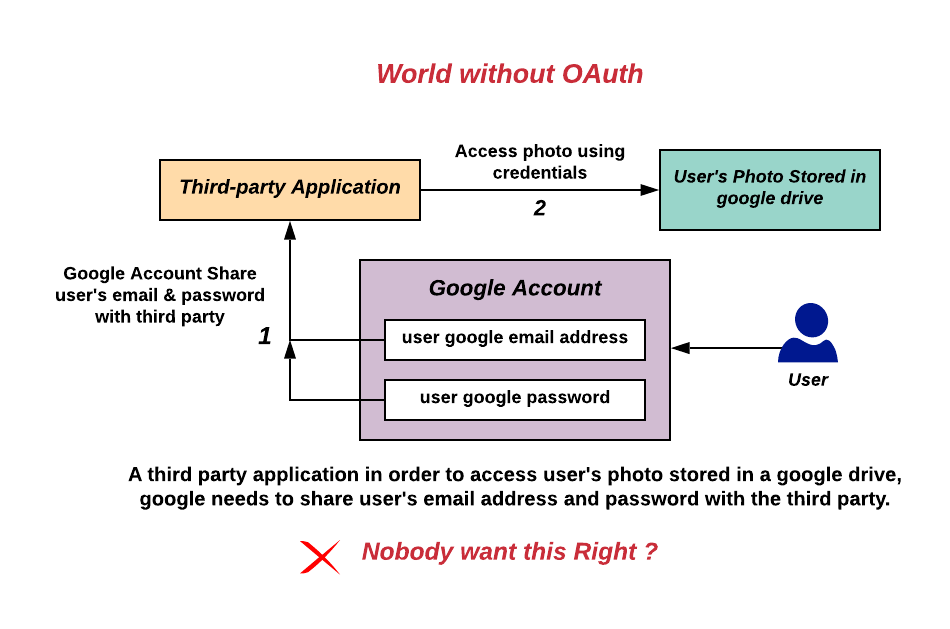
OAuth
OAuth (short for open authorization) is an open standard for access delegation, commonly used as a way for internet users to grant websites or applications access to their information on other websites but without giving them the passwords. This mechanism is used by companies such as Amazon, Google, Meta Platforms, Microsoft, and Twitter to permit users to share information about their accounts with third-party applications or websites. Generally, the OAuth protocol provides a way for resource owners to provide a client application with secure delegated access to server resources. It specifies a process for resource owners to authorize third-party access to their server resources without providing credentials. Designed specifically to work with Hypertext Transfer Protocol (HTTP), OAuth essentially allows access tokens to be issued to third-party clients by an authorization server, with the approval of the resource owner. The third party then uses the access token to access th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cross-origin Resource Sharing
Cross-origin resource sharing (CORS) is a mechanism to safely bypass the same-origin policy, that is, it allows a web page to access restricted resources from a server on a domain different than the domain that served the web page. A web page may freely embed cross-origin images, stylesheets, scripts, iframes, and videos. Certain "cross-domain" requests, notably Ajax requests, are forbidden by default by the same-origin security policy. CORS defines a way in which a browser and server can interact to determine whether it is safe to allow the cross-origin request. It allows for more freedom and functionality than purely same-origin requests, but is more secure than simply allowing all cross-origin requests. The specification for CORS is included as part of the WHATWG's Fetch Living Standard. This specification describes how CORS is currently implemented in browsers. An earlier specification was published as a W3C Recommendation. Technical overview For HTTP requests made from ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |