|
HiperLAN
HiperLAN (High Performance Radio LAN) is a wireless LAN standard. It is a European alternative for the IEEE 802.11 standards (the IEEE is an international organization). It is defined by the European Telecommunications Standards Institute (ETSI). In ETSI the standards are defined by the BRAN project (Broadband Radio Access Networks). The HiperLAN standard family has four different versions. HiperLAN/1 Planning for the first version of the standard, called HiperLAN/1, started 1992, when planning of 802.11 was already going on. The goal of the HiperLAN was the high data rate, higher than 802.11. The standard was approved in 1997. The functional specification is EN300652, the rest is in ETS300836. The standard covers the Physical layer and the Media Access Control part of the Data link layer like 802.11. There is a new sublayer called Channel Access and Control sublayer (CAC). This sublayer deals with the access requests to the channels. The accomplishing of the request is depend ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireless LAN
A wireless LAN (WLAN) is a wireless computer network A wireless network is a computer network that uses wireless data connections between network nodes. Wireless networking is a method by which homes, telecommunications networks and business installations avoid the costly process of introducing c ... that links two or more devices using wireless communication to form a local area network (LAN) within a limited area such as a home, school, computer laboratory, campus, or office building. This gives users the ability to move around within the area and remain connected to the network. Through a Gateway (telecommunications), gateway, a WLAN can also provide a connection to the wider Internet. Wireless LANs based on the IEEE 802.11 standards are the most widely used computer networks in the world. These are commonly called Wi-Fi, which is a trademark belonging to the Wi-Fi Alliance. They are used for home and small office networks that link together laptop computers, printer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Asynchronous Transfer Mode
Asynchronous Transfer Mode (ATM) is a telecommunications standard defined by American National Standards Institute (ANSI) and ITU-T (formerly CCITT) for digital transmission of multiple types of traffic. ATM was developed to meet the needs of the Broadband Integrated Services Digital Network as defined in the late 1980s, and designed to integrate telecommunication networks. It can handle both traditional high-throughput data traffic and real-time, low-latency content such as telephony (voice) and video.ATM Forum, The User Network Interface (UNI), v. 3.1, , Prentice Hall PTR, 1995, page 2. ATM provides functionality that uses features of circuit switching and packet switching networks by using asynchronous time-division multiplexing.McDysan (1999), p. 287. In the OSI reference model data link layer (layer 2), the basic transfer units are called '' frames''. In ATM these frames are of a fixed length (53 octets) called ''cells''. This differs from approaches such as Internet Pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireless Access Point
In computer networking, a wireless access point (WAP), or more generally just access point (AP), is a networking hardware device that allows other Wi-Fi devices to connect to a wired network. As a standalone device, the AP may have a wired connection to a router, but, in a wireless router, it can also be an integral component of the router itself. An AP is differentiated from a hotspot which is a physical location where Wi-Fi access is available. Connections An AP connects directly to a wired local area network, typically Ethernet, and the AP then provides wireless connections using wireless LAN technology, typically Wi-Fi, for other devices to use that wired connection. APs support the connection of multiple wireless devices through their one wired connection. Wireless data standards There are many wireless data standards that have been introduced for wireless access point and wireless router technology. New standards have been created to accommodate the increasing n ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Triple DES
In cryptography, Triple DES (3DES or TDES), officially the Triple Data Encryption Algorithm (TDEA or Triple DEA), is a symmetric-key block cipher, which applies the DES cipher algorithm three times to each data block. The Data Encryption Standard's (DES) 56-bit key is no longer considered adequate in the face of modern cryptanalytic techniques and supercomputing power. A CVE released in 2016, CVE-2016-2183' disclosed a major security vulnerability in DES and 3DES encryption algorithms. This CVE, combined with the inadequate key size of DES and 3DES, NIST has deprecated DES and 3DES for ''new'' applications in 2017, and for ''all'' applications by the end of 2023. It has been replaced with the more secure, more robust AES. While the government and industry standards abbreviate the algorithm's name as TDES (Triple DES) and TDEA (Triple Data Encryption Algorithm), RFC 1851 referred to it as 3DES from the time it first promulgated the idea, and this namesake has since come into wi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Encryption Standard
The Data Encryption Standard (DES ) is a symmetric-key algorithm for the encryption of digital data. Although its short key length of 56 bits makes it too insecure for modern applications, it has been highly influential in the advancement of cryptography. Developed in the early 1970s at IBM and based on an earlier design by Horst Feistel, the algorithm was submitted to the National Bureau of Standards (NBS) following the agency's invitation to propose a candidate for the protection of sensitive, unclassified electronic government data. In 1976, after consultation with the National Security Agency (NSA), the NBS selected a slightly modified version (strengthened against differential cryptanalysis, but weakened against brute-force attacks), which was published as an official Federal Information Processing Standard (FIPS) for the United States in 1977. The publication of an NSA-approved encryption standard led to its quick international adoption and widespread academic scrutiny. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Orthogonal Frequency-division Multiplexing
In telecommunications, orthogonal frequency-division multiplexing (OFDM) is a type of digital transmission and a method of encoding digital data on multiple carrier frequencies. OFDM has developed into a popular scheme for wideband digital communication, used in applications such as digital television and audio broadcasting, DSL internet access, wireless networks, power line networks, and 4G/ 5G mobile communications. OFDM is a frequency-division multiplexing (FDM) scheme that was introduced by Robert W. Chang of Bell Labs in 1966. In OFDM, multiple closely spaced orthogonal subcarrier signals with overlapping spectra are transmitted to carry data in parallel.webe.org - 2GHz BAS Relocation Tech-Fair, COFDM Technology Basics 2007-03-02 Demodula ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
64QAM
Quadrature amplitude modulation (QAM) is the name of a family of digital modulation methods and a related family of analog modulation methods widely used in modern telecommunications to transmit information. It conveys two analog message signals, or two digital bit streams, by changing (''modulating'') the amplitudes of two carrier waves, using the amplitude-shift keying (ASK) digital modulation scheme or amplitude modulation (AM) analog modulation scheme. The two carrier waves are of the same frequency and are out of phase with each other by 90°, a condition known as orthogonality or quadrature. The transmitted signal is created by adding the two carrier waves together. At the receiver, the two waves can be coherently separated (demodulated) because of their orthogonality property. Another key property is that the modulations are low-frequency/low-bandwidth waveforms compared to the carrier frequency, which is known as the narrowband assumption. Phase modulation (analog PM) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quadrature Amplitude Modulation
Quadrature amplitude modulation (QAM) is the name of a family of digital modulation methods and a related family of analog modulation methods widely used in modern telecommunications to transmit information. It conveys two analog message signals, or two digital bit streams, by changing (''modulating'') the amplitudes of two carrier waves, using the amplitude-shift keying (ASK) digital modulation scheme or amplitude modulation (AM) analog modulation scheme. The two carrier waves are of the same frequency and are out of phase with each other by 90°, a condition known as orthogonality or quadrature. The transmitted signal is created by adding the two carrier waves together. At the receiver, the two waves can be coherently separated (demodulated) because of their orthogonality property. Another key property is that the modulations are low-frequency/low-bandwidth waveforms compared to the carrier frequency, which is known as the narrowband assumption. Phase modulation (analog PM) ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
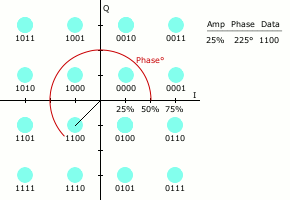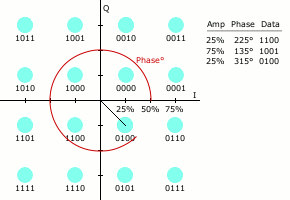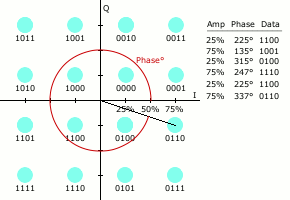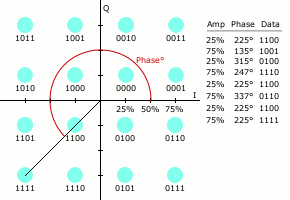
QPSK
Phase-shift keying (PSK) is a digital modulation process which conveys data by changing (modulating) the phase of a constant frequency reference signal (the carrier wave). The modulation is accomplished by varying the sine and cosine inputs at a precise time. It is widely used for wireless LANs, RFID and Bluetooth communication. Any digital modulation scheme uses a finite number of distinct signals to represent digital data. PSK uses a finite number of phases, each assigned a unique pattern of binary digits. Usually, each phase encodes an equal number of bits. Each pattern of bits forms the symbol that is represented by the particular phase. The demodulator, which is designed specifically for the symbol-set used by the modulator, determines the phase of the received signal and maps it back to the symbol it represents, thus recovering the original data. This requires the receiver to be able to compare the phase of the received signal to a reference signal such a system is termed c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
BPSK
Phase-shift keying (PSK) is a digital modulation process which conveys Data (computing), data by changing (modulating) the Phase (waves), phase of a constant frequency reference signal (the carrier wave). The modulation is accomplished by varying the sine wave, sine and cosine wave, cosine inputs at a precise time. It is widely used for wireless LANs, RFID and Bluetooth communication. Any digital modulation scheme uses a finite number of distinct signals to represent digital data. PSK uses a finite number of phases, each assigned a unique pattern of bit, binary digits. Usually, each phase encodes an equal number of bits. Each pattern of bits forms the symbol rate, symbol that is represented by the particular phase. The demodulator, which is designed specifically for the symbol-set used by the modulator, determines the phase of the received signal and maps it back to the symbol it represents, thus recovering the original data. This requires the receiver to be able to compare the ph ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quality Of Service
Quality of service (QoS) is the description or measurement of the overall performance of a service, such as a telephony or computer network, or a cloud computing service, particularly the performance seen by the users of the network. To quantitatively measure quality of service, several related aspects of the network service are often considered, such as packet loss, bit rate, throughput, transmission delay, availability, jitter, etc. In the field of computer networking and other packet-switched telecommunication networks, quality of service refers to traffic prioritization and resource reservation control mechanisms rather than the achieved service quality. Quality of service is the ability to provide different priorities to different applications, users, or data flows, or to guarantee a certain level of performance to a data flow. Quality of service is particularly important for the transport of traffic with special requirements. In particular, developers have introduced Voice ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CSMA/CA
Carrier-sense multiple access with collision avoidance (CSMA/CA) in computer networking, is a network multiple access method in which carrier sensing is used, but nodes attempt to avoid collisions by beginning transmission only after the channel is sensed to be "idle". When they do transmit, nodes transmit their packet data in its entirety. It is particularly important for wireless networks, where the alternative with collision detection CSMA/CD, is not possible due to wireless transmitters desensing (turning off) their receivers during packet transmission. CSMA/CA is unreliable due to the hidden node problem. CSMA/CA is a protocol that operates in the data link layer (Layer 2) of the OSI model. Details Collision avoidance is used to improve the performance of the CSMA method by attempting to divide the channel somewhat equally among all transmitting nodes within the collision domain. # Carrier Sense: prior to transmitting, a node first listens to the shared medium (such as l ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |