|
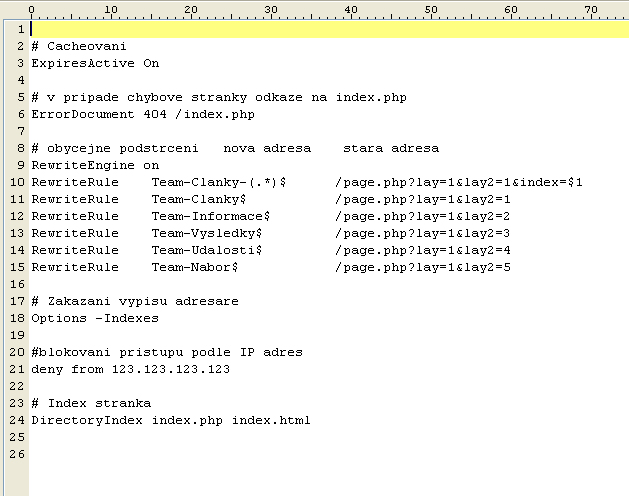
Htaccess
An .htaccess (''hypertext access'') file is a directory-level configuration file supported by several web servers, used for configuration of website-access issues, such as URL redirection, URL shortening, access control (for different web pages and files), and more. The 'dot' ( period or full stop) before the file name makes it a hidden file in Unix-based environments. A site could have more than one .htaccess file, and the files are placed inside the web tree (i.e. inside directories and their sub-directories), and hence their other name ''distributed configuration files''. .htaccess files act as a subset of the server's global configuration file (like ) for the directory that they are in, or all sub-directories. The original purpose of .htaccess—reflected in its name—was to allow per-directory access control by, for example, requiring a password to access |
Common Gateway Interface
file:Common Gateway Interface logo.svg, The official CGI logo from the spec announcement In computing, Common Gateway Interface (CGI) is an interface specification that enables web servers to execute an external program to process HTTP or HTTPS user requests. Such programs are often written in a scripting language and are commonly referred to as ''CGI scripts'', but they may include compiler, compiled programs. A typical use case occurs when a web user submits a web form on a web page that uses CGI. The form's data is sent to the web server within a HTTP request with a URL denoting a CGI script. The web server then launches the CGI script in a new computer process, passing the form data to it. The CGI script passes its output, usually in the form of HTML, to the Web server, and the server relays it back to the browser as its HTTP response, response to the browser's request. Developed in the early 1990s, CGI was the earliest common method available that allowed a web page to be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Custom Error Page
In computer network communications, the HTTP 404, 404 not found, 404, 404 error, page not found, or file not found error message is a hypertext transfer protocol (HTTP) standard response code, to indicate that the browser was able to communicate with a given server, but the server could not find what was requested. The error may also be used when a server does not wish to disclose whether it has the requested information. The website hosting server will typically generate a "404 Not Found" web page when a user attempts to follow a broken or dead link; hence the 404 error is one of the most recognizable errors encountered on the World Wide Web. Overview When communicating via HTTP, a server is required to respond to a request, such as a web browser request for a web page, with a numeric response code and an optional, mandatory, or disallowed (based upon the status code) message. In code 404, the first digit indicates a client error, such as a mistyped Uniform Resource ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Server-side Include
Server Side Includes (SSI) is a simple interpreted server-side scripting language used almost exclusively for the World Wide Web. It is most useful for including the contents of one or more files into a web page on a web server (see below), using its #include directive. This could commonly be a common piece of code throughout a site, such as a page header, a page footer and a navigation menu. SSI also contains control directives for conditional features and directives for calling external programs. It is supported by Apache, LiteSpeed, nginx, IIS as well as W3C's Jigsaw. It has its roots in NCSA HTTPd. In order for a web server to recognize an SSI-enabled HTML file and therefore carry out these instructions, either the filename should end with a special extension, by default .shtml, .stm, .shtm, or, if the server is configured to allow this, set the execution bit of the file. Design As a simple programming language, SSI supports only one type: text. Its control flow is rather ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rewriting
In mathematics, computer science, and logic, rewriting covers a wide range of methods of replacing subterms of a formula with other terms. Such methods may be achieved by rewriting systems (also known as rewrite systems, rewrite engines, or reduction systems). In their most basic form, they consist of a set of objects, plus relations on how to transform those objects. Rewriting can be non-deterministic. One rule to rewrite a term could be applied in many different ways to that term, or more than one rule could be applicable. Rewriting systems then do not provide an algorithm for changing one term to another, but a set of possible rule applications. When combined with an appropriate algorithm, however, rewrite systems can be viewed as computer programs, and several theorem provers and declarative programming languages are based on term rewriting. Example cases Logic In logic, the procedure for obtaining the conjunctive normal form (CNF) of a formula can be implemented as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
URL Rewriting
In web applications, a rewrite engine is a software component that performs rewriting on URLs (Uniform Resource Locators), modifying their appearance. This modification is called URL rewriting. It is a way of implementing URL mapping or routing within a web application. The engine is typically a component of a web server or web application framework. Rewritten URLs (sometimes known as short, pretty or fancy URLs, search engine friendly - SEF URLs, or slugs) are used to provide shorter and more relevant-looking links to web pages. The technique adds a layer of abstraction between the files used to generate a web page and the URL that is presented to the outside world. Usage Web sites with dynamic content can use URLs that generate pages from the server using query string parameters. These are often rewritten to resemble URLs for static pages on a site with a subdirectory hierarchy. For example, the URL to a wiki page with title ''Rewrite_engine'' might be: http://example.c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Password
A password, sometimes called a passcode, is secret data, typically a string of characters, usually used to confirm a user's identity. Traditionally, passwords were expected to be memorized, but the large number of password-protected services that a typical individual accesses can make memorization of unique passwords for each service impractical. Using the terminology of the NIST Digital Identity Guidelines, the secret is held by a party called the ''claimant'' while the party verifying the identity of the claimant is called the ''verifier''. When the claimant successfully demonstrates knowledge of the password to the verifier through an established authentication protocol, the verifier is able to infer the claimant's identity. In general, a password is an arbitrary String (computer science), string of character (computing), characters including letters, digits, or other symbols. If the permissible characters are constrained to be numeric, the corresponding secret is sometimes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Username
A user is a person who uses a computer or Computer network, network Service (systems architecture), service. A user often has a user account and is identified to the system by a username (or user name). Some software products provide services to other systems and have no direct end users. End user End users are the ultimate human users (also referred to as Operator (profession), operators) of a software product. The end user stands in contrast to users who support or maintain the product such as sysops, database administrators and computer technicians. The term is used to abstract and distinguish those who only use the software from the developers of the system, who enhance the software for end users. In user-centered design, it also distinguishes the software operator from the client who pays for its development and other Stakeholder (corporate), stakeholders who may not directly use the software, but help establish its Software requirements, requirements. This abstracti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Htpasswd
.htpasswd is a flat-file used to store usernames and password for basic authentication on an Apache HTTP Server. The name of the file is given in the .htaccess configuration, and can be anything, although ".htpasswd" is the canonical name. The file name starts with a dot, because most Unix-like operating systems consider any file that begins with a dot to be hidden. The htpasswd command is used to manage .htpasswd file entries. History htpasswd was first added in the NCSA HTTPd server, which is the predecessor to Apache. The hash historically used "UNIX crypt" style with MD5 or SHA1 as common alternatives. In Apache 2.4, the bcrypt algorithm was added. Usage The file consists of lines, with each line containing a username, followed by a colon, followed by a string containing the hashed password optionally prepended by an algorithm specifier ("$2y$", "$apr1$" or "") and/or salt. Athelstan:RLjXiyxx56D9s Mama:RLMzFazUFPVRE Papa:RL8wKTlBoVLKk Resources available from the Apac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authentication
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an Logical assertion, assertion, such as the Digital identity, identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. Authentication is relevant to multiple fields. In art, antiques, and anthropology, a common problem is verifying that a given artifact was produced by a certain person, or in a certain place (i.e. to assert that it is not counterfeit), or in a given period of history (e.g. by determining the age via carbon dating). In computer science, verifying a user's identity is often required to allow access to confidential data or systems. It might involve validating personal identity documents. In art, antiques and anthropology Authentication can be considered to be of three types: The ''first'' type of authentication is accep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authorization
Authorization or authorisation (see American and British English spelling differences#-ise, -ize (-isation, -ization), spelling differences), in information security, computer security and identity management, IAM (Identity and Access Management), is the function of specifying rights/privileges for accessing resources, in most cases through an access policy, and then deciding whether a particular ''subject'' has privilege to access a particular ''resource''. Examples of ''subjects'' include human users, computer software and other Computer hardware, hardware on the computer. Examples of ''resources'' include individual files or an item's data, computer programs, computer Computer hardware, devices and functionality provided by computer applications. For example, user accounts for human resources staff are typically configured with authorization for accessing employee records. Authorization is closely related to access control, which is what enforces the authorization policy by d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zeus Web Server
Zeus Web Server is a discontinued proprietary high-performance web server for Unix and Unix-like platforms (including Solaris, FreeBSD, HP-UX and Linux). It was developed by Zeus Technology, a software company located in Cambridge, England England is a Countries of the United Kingdom, country that is part of the United Kingdom. It is located on the island of Great Britain, of which it covers about 62%, and List of islands of England, more than 100 smaller adjacent islands. It ... that was founded in 1995 by University of Cambridge graduates Damian Reeves and Adam Twiss. History Zeus was designed to be a high-performance web server since the beginning of its development in 1995. Until the first decade of the 2000s, it was known as one of the fastest and most scalable web servers available on market. Despite its excellent performance, it never gained more than a few percentage points (less than 3%) in the global usage of most popular web servers. However, it was ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |