|
Ho Chi Minh City University Of Information Technology
VNUHCM-University of Information Technology (VNUHCM-UIT; vi, Trường Đại học Công nghệ thông tin, Đại học Quốc gia Thành phố Hồ Chí Minh, links=no) is a public university located in Ho Chi Minh City, Vietnam, a member of Vietnam National University, Ho Chi Minh City. Although its name is about information technology, this university teaches many computer studies. The first course was inaugurated on 6 November 2006. History The predecessor of this university was Center for IT Development. On 8 June 2006, the Vietnamese prime minister signed Decision no. 134/2006/QĐ-TTg to establish this university. Academic programs Undergraduate programs *Computer Sciences * Data Science *Information Systems * Computer Engineering * Electronic Commerce * Computer Networks and Communications *Software Engineering *Information Technology *Information Security Graduate programs: *Computer Sciences *Information Systems *Information Security *Information Technology Research ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public University
A public university or public college is a university or college that is in owned by the state or receives significant public funds through a national or subnational government, as opposed to a private university. Whether a national university is considered public varies from one country (or region) to another, largely depending on the specific education landscape. Africa Egypt In Egypt, Al-Azhar University was founded in 970 AD as a madrasa; it formally became a public university in 1961 and is one of the oldest institutions of higher education in the world. In the 20th century, Egypt opened many other public universities with government-subsidized tuition fees, including Cairo University in 1908, Alexandria University in 1912, Assiut University in 1928, Ain Shams University in 1957, Helwan University in 1959, Beni-Suef University in 1963, Zagazig University in 1974, Benha University in 1976, and Suez Canal University in 1989. Kenya In Kenya, the Ministry of Ed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Technology
Information technology (IT) is the use of computers to create, process, store, retrieve, and exchange all kinds of data . and information. IT forms part of information and communications technology (ICT). An information technology system (IT system) is generally an information system, a communications system, or, more specifically speaking, a computer system — including all hardware, software, and peripheral equipment — operated by a limited group of IT users. Although humans have been storing, retrieving, manipulating, and communicating information since the earliest writing systems were developed, the term ''information technology'' in its modern sense first appeared in a 1958 article published in the ''Harvard Business Review''; authors Harold J. Leavitt and Thomas L. Whisler commented that "the new technology does not yet have a single established name. We shall call it information technology (IT)." Their definition consists of three categories: techniques for pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IoT & Robotics
The Internet of things (IoT) describes physical objects (or groups of such objects) with sensors, processing ability, software and other technologies that connect and exchange data with other devices and systems over the Internet or other communications networks. Internet of things has been considered a misnomer because devices do not need to be connected to the public internet, they only need to be connected to a network and be individually addressable. The field has evolved due to the convergence of multiple technologies, including ubiquitous computing, commodity sensors, increasingly powerful embedded systems, as well as machine learning.Hu, J.; Niu, H.; Carrasco, J.; Lennox, B.; Arvin, F.,Fault-tolerant cooperative navigation of networked UAV swarms for forest fire monitoring Aerospace Science and Technology, 2022. Traditional fields of embedded systems, wireless sensor networks, control systems, automation (including home and building automation), independently and co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Embedded & VLSI Design
Embedded or embedding (alternatively imbedded or imbedding) may refer to: Science * Embedding, in mathematics, one instance of some mathematical object contained within another instance ** Graph embedding * Embedded generation, a distributed generation of energy, also known as decentralized generation * Self-embedding, in psychology, an activity in which one pushes items into one's own flesh in order to feel pain * Embedding, in biology, a part of sample preparation for microscopes Computing * Embedded system, a special-purpose system in which the computer is completely encapsulated by the device it controls * Embedding, installing media into a text document to form a compound document ** , a HyperText Markup Language (HTML) element that inserts a non-standard object into the HTML document * Web embed, an element of a host web page that is substantially independent of the host page * Font embedding, inclusion of font files inside an electronic document * Word embedding, a t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Network
A cellular network or mobile network is a communication network where the link to and from end nodes is wireless. The network is distributed over land areas called "cells", each served by at least one fixed-location transceiver (typically three cell sites or base transceiver stations). These base stations provide the cell with the network coverage which can be used for transmission of voice, data, and other types of content. A cell typically uses a different set of frequencies from neighboring cells, to avoid interference and provide guaranteed service quality within each cell. When joined together, these cells provide radio coverage over a wide geographic area. This enables numerous portable transceivers (e.g., mobile phones, tablets and laptops equipped with mobile broadband modems, pagers, etc.) to communicate with each other and with fixed transceivers and telephones anywhere in the network, via base stations, even if some of the transceivers are moving through more than ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multimedia Processing
Multimedia is a form of communication that uses a combination of different content forms such as text, audio, images, animations, or video into a single interactive presentation, in contrast to traditional mass media, such as printed material or audio recordings, which features little to no interaction between users. Popular examples of multimedia include video podcasts, audio slideshows and animated videos. Multimedia also contains the principles and application of effective interactive communication such as the building blocks of software, hardware, and other technologies. Multimedia can be recorded for playback on computers, laptops, smartphones, and other electronic devices, either on demand or in real time (streaming). In the early years of multimedia, the term "rich media" was synonymous with interactive multimedia. Over time, hypermedia extensions brought multimedia to the World Wide Web. Terminology The term ''multimedia'' wa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Security
Network security consists of the policies, policies, processes and practices adopted to prevent, detect and monitor unauthorized access, Abuse, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs: conducting transactions and communications among businesses, Government agency, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: it secures the network, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Network Protocols
A computer is a machine that can be programmed to carry out sequences of arithmetic or logical operations ( computation) automatically. Modern digital electronic computers can perform generic sets of operations known as programs. These programs enable computers to perform a wide range of tasks. A computer system is a nominally complete computer that includes the hardware, operating system (main software), and peripheral equipment needed and used for full operation. This term may also refer to a group of computers that are linked and function together, such as a computer network or computer cluster. A broad range of industrial and consumer products use computers as control systems. Simple special-purpose devices like microwave ovens and remote controls are included, as are factory devices like industrial robots and computer-aided design, as well as general-purpose devices like personal computers and mobile devices like smartphones. Computers power the Internet, which l ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
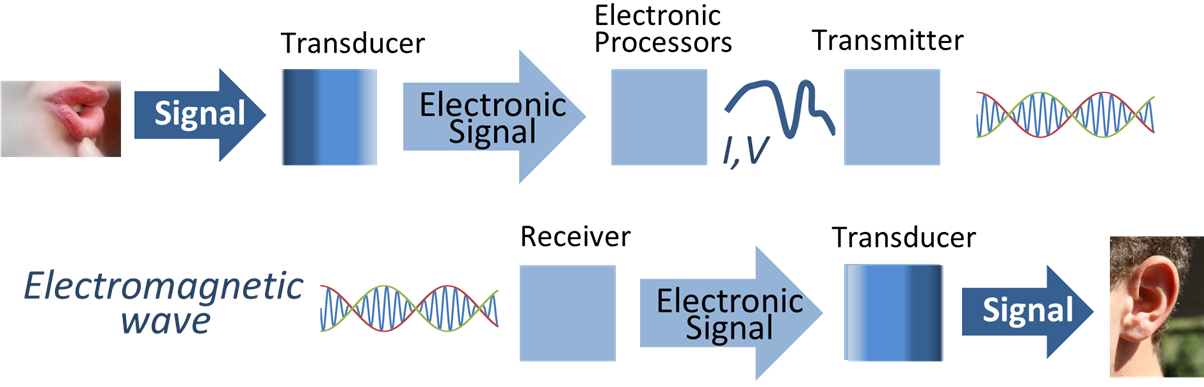
Signal Processing
Signal processing is an electrical engineering subfield that focuses on analyzing, modifying and synthesizing ''signals'', such as audio signal processing, sound, image processing, images, and scientific measurements. Signal processing techniques are used to optimize transmissions, Data storage, digital storage efficiency, correcting distorted signals, subjective video quality and to also detect or pinpoint components of interest in a measured signal. History According to Alan V. Oppenheim and Ronald W. Schafer, the principles of signal processing can be found in the classical numerical analysis techniques of the 17th century. They further state that the digital refinement of these techniques can be found in the digital control systems of the 1940s and 1950s. In 1948, Claude Shannon wrote the influential paper "A Mathematical Theory of Communication" which was published in the Bell System Technical Journal. The paper laid the groundwork for later development of information c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Knowledge Engineering
Knowledge engineering (KE) refers to all technical, scientific and social aspects involved in building, maintaining and using knowledge-based systems. Background Expert systems One of the first examples of an expert system was MYCIN, an application to perform medical diagnosis. In the MYCIN example, the domain experts were medical doctors and the knowledge represented was their expertise in diagnosis. Expert systems were first developed in artificial intelligence laboratories as an attempt to understand complex human decision making. Based on positive results from these initial prototypes, the technology was adopted by the US business community (and later worldwide) in the 1980s. The Stanford heuristic programming projects led by Edward Feigenbaum was one of the leaders in defining and developing the first expert systems. History In the earliest days of expert systems there was little or no formal process for the creation of the software. Researchers just sat down with dom ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Security
Information security, sometimes shortened to InfoSec, is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized/inappropriate access to data, or the unlawful use, disclosure, disruption, deletion, corruption, modification, inspection, recording, or devaluation of information. It also involves actions intended to reduce the adverse impacts of such incidents. Protected information may take any form, e.g. electronic or physical, tangible (e.g. paperwork) or intangible (e.g. knowledge). Information security's primary focus is the balanced protection of the confidentiality, integrity, and availability of data (also known as the CIA triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process that involves: * identifying inform ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Engineering
Software engineering is a systematic engineering approach to software development. A software engineer is a person who applies the principles of software engineering to design, develop, maintain, test, and evaluate computer software. The term '' programmer'' is sometimes used as a synonym, but may also lack connotations of engineering education or skills. Engineering techniques are used to inform the software development process which involves the definition, implementation, assessment, measurement, management, change, and improvement of the software life cycle process itself. It heavily uses software configuration management which is about systematically controlling changes to the configuration, and maintaining the integrity and traceability of the configuration and code throughout the system life cycle. Modern processes use software versioning. History Beginning in the 1960s, software engineering was seen as its own type of engineering. Additionally, the development of soft ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |


.jpg)