|
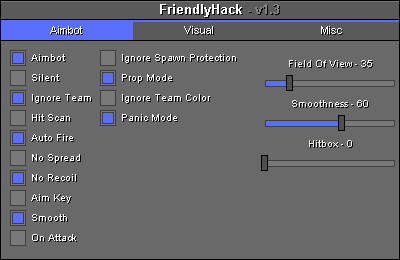
Hardcoded Screenshot
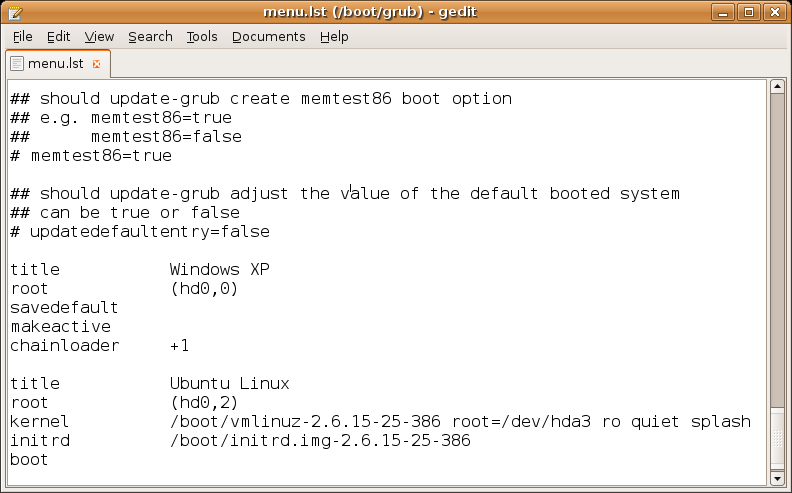
Hard coding (also hard-coding or hardcoding) is the software development practice of embedding data directly into the source code of a program or other executable object, as opposed to obtaining the data from external sources or generating it at runtime. Hard-coded data typically can only be modified by editing the source code and Compiling, recompiling the executable, although it can be changed in Volatile memory, memory or on disk using a debugger or hex editor. Data that are hard-coded is best for unchanging pieces of information, such as physical constant, physical constants, Version number, version numbers and static text elements. Softcoding, Softcoded data, on the other hand, encode arbitrary information through user input, text files, INI files, HTTP server responses, configuration files, preprocessor macros, external constants, databases, command-line arguments, and are determined at runtime. Overview Hard coding requires the program's source code to be changed any time ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Source Code
In computing, source code, or simply code, is any collection of code, with or without comments, written using a human-readable programming language, usually as plain text. The source code of a program is specially designed to facilitate the work of computer programmers, who specify the actions to be performed by a computer mostly by writing source code. The source code is often transformed by an assembler or compiler into binary machine code that can be executed by the computer. The machine code is then available for execution at a later time. Most application software is distributed in a form that includes only executable files. If the source code were included it would be useful to a user, programmer or a system administrator, any of whom might wish to study or modify the program. Alternatively, depending on the technology being used, source code may be interpreted and executed directly. Definitions Richard Stallman's definition, formulated in his 1989 seminal li ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Macro (computer Science)
In computer programming, a macro (short for "macro instruction"; ) is a rule or pattern that specifies how a certain input should be mapped to a replacement output. Applying a macro to an input is known as macro expansion. The input and output may be a sequence of lexical tokens or characters, or a syntax tree. Character macros are supported in software applications to make it easy to invoke common command sequences. Token and tree macros are supported in some programming languages to enable code reuse or to extend the language, sometimes for domain-specific languages. Macros are used to make a sequence of computing instructions available to the programmer as a single program statement, making the programming task less tedious and less error-prone. (Thus, they are called "macros" because a "big" block of code can be expanded from a "small" sequence of characters.) Macros often allow positional or keyword parameters that dictate what the conditional assembler program generates ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
End-user License Agreement
An end-user license agreement or EULA () is a legal contract between a software supplier and a customer or end-user, generally made available to the customer via a retailer acting as an intermediary. A EULA specifies in detail the rights and restrictions which apply to the use of the software. Form contracts for digital services (such as terms of service and privacy policies) were traditionally presented on paper (see shrink-wrap agreement) but are now often presented digitally via browsewrap or clickwrap formats. As the user may not see the agreement until after they have already purchased or engaged with the software, these documents may be contracts of adhesion. Software companies often make special agreements with large businesses and government entitles that include support contracts and specially drafted warranties. Many EULAs assert extensive liability limitations. Most commonly, an EULA will attempt to hold harmless the software licensor in the event that the software cau ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti-cheat
Cheating in online games is the subversion of the rules or mechanics of online video games to gain an unfair advantage over other players, generally with the use of third-party software. What constitutes cheating is dependent on the game in question, its rules, and consensus opinion as to whether a particular activity is considered to be cheating. Cheating is present in most multiplayer online games, but it is difficult to measure. Various methods of cheating in online games can take the form of software assistance, such as scripts and bots, and various forms of unsporting play taking advantage of exploits within the game. The Internet and darknets can provide players with the methodology necessary to cheat in online games, with software often available for purchase. As methods of cheating have advanced, video game publishers have similarly increased methods of anti-cheating, but are still limited in their effectiveness. Punishments for cheaters also have various forms, wi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Binary Code
A binary code represents text, computer processor instructions, or any other data using a two-symbol system. The two-symbol system used is often "0" and "1" from the binary number system. The binary code assigns a pattern of binary digits, also known as bits, to each character, instruction, etc. For example, a binary string of eight bits (which is also called a byte) can represent any of 256 possible values and can, therefore, represent a wide variety of different items. In computing and telecommunications, binary codes are used for various methods of encoding data, such as character strings, into bit strings. Those methods may use fixed-width or variable-width strings. In a fixed-width binary code, each letter, digit, or other character is represented by a bit string of the same length; that bit string, interpreted as a binary number, is usually displayed in code tables in octal, decimal or hexadecimal notation. There are many character sets and many character encodings for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software
Software is a set of computer programs and associated documentation and data. This is in contrast to hardware, from which the system is built and which actually performs the work. At the lowest programming level, executable code consists of machine language instructions supported by an individual processor—typically a central processing unit (CPU) or a graphics processing unit (GPU). Machine language consists of groups of binary values signifying processor instructions that change the state of the computer from its preceding state. For example, an instruction may change the value stored in a particular storage location in the computer—an effect that is not directly observable to the user. An instruction may also invoke one of many input or output operations, for example displaying some text on a computer screen; causing state changes which should be visible to the user. The processor executes the instructions in the order they are provided, unless it is instructed ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reverse-engineering
Reverse engineering (also known as backwards engineering or back engineering) is a process or method through which one attempts to understand through deductive reasoning how a previously made device, process, system, or piece of software accomplishes a task with very little (if any) insight into exactly how it does so. It is essentially the process of opening up or dissecting a system to see how it works, in order to duplicate or enhance it. Depending on the system under consideration and the technologies employed, the knowledge gained during reverse engineering can help with repurposing obsolete objects, doing security analysis, or learning how something works. Although the process is specific to the object on which it is being performed, all reverse engineering processes consist of three basic steps: Information extraction, Modeling, and Review. Information extraction refers to the practice of gathering all relevant information for performing the operation. Modeling refers to th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Decompiler
A decompiler is a computer program that translates an executable file to a high-level source file which can be recompiled successfully. It does therefore the opposite of a typical compiler, which translates a high-level language to a low-level language. Decompilers are usually unable to perfectly reconstruct the original source code, thus frequently will produce obfuscated code. Nonetheless, decompilers remain an important tool in the reverse engineering of computer software. Introduction The term ''decompiler'' is most commonly applied to a program which translates executable programs (the output from a compiler) into source code in a (relatively) high level language which, when compiled, will produce an executable whose behavior is the same as the original executable program. By comparison, a disassembler translates an executable program into assembly language (and an assembler could be used for assembling it back into an executable program). Decompilation is the act of using a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FLOSS
Free and open-source software (FOSS) is a term used to refer to groups of software consisting of both free software and open-source software where anyone is freely licensed to use, copy, study, and change the software in any way, and the source code is openly shared so that people are encouraged to voluntarily improve the design of the software. This is in contrast to proprietary software, where the software is under restrictive copyright licensing and the source code is usually hidden from the users. FOSS maintains the software user's civil liberty rights (see the Four Essential Freedoms, below). Other benefits of using FOSS can include decreased software costs, increased security and stability (especially in regard to malware), protecting privacy, education, and giving users more control over their own hardware. Free and open-source operating systems such as Linux and descendants of BSD are widely utilized today, powering millions of servers, desktops, smartphones (e.g., A ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backdoor (computing)
A backdoor is a typically covert method of bypassing normal authentication or encryption in a computer, product, embedded device (e.g. a home router), or its embodiment (e.g. part of a cryptosystem, algorithm, chipset, or even a "homunculus computer" —a tiny computer-within-a-computer such as that found in Intel's Intel Active Management Technology, AMT technology). Backdoors are most often used for securing remote access to a computer, or obtaining access to plaintext in cryptographic systems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information within autoschediastic networks. A backdoor may take the form of a hidden part of a program, a separate program (e.g. Back Orifice may subvert the system through a rootkit), code in the hardware backdoor, firmware of the hardware, or parts of an operating system such as Microsoft Windows, Windows. Trojan horse (computing), Trojan horses can be u ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Configuration File
In computing, configuration files (commonly known simply as config files) are computer file, files used to configure the Parameter (computer programming), parameters and Initialization (programming), initial settings for some computer programs. They are used for user application software, applications, Server (computing), server processes and operating system settings. Some applications provide tools to create, modify, and verify the syntax of their configuration files; these sometimes have graphical interfaces. For other programs, system administrators may be expected to create and modify files by hand using a text editor, which is possible because many are human-editable plain text files. For server processes and operating-system settings, there is often no standard tool, but operating systems may provide their own graphical interfaces such as YaST or debconf. Some computer programs only read their configuration files at Booting, startup. Others periodically check the configur ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Server (computing)
In computing, a server is a piece of computer hardware or software (computer program) that provides functionality for other programs or devices, called " clients". This architecture is called the client–server model. Servers can provide various functionalities, often called "services", such as sharing data or resources among multiple clients, or performing computation for a client. A single server can serve multiple clients, and a single client can use multiple servers. A client process may run on the same device or may connect over a network to a server on a different device. Typical servers are database servers, file servers, mail servers, print servers, web servers, game servers, and application servers. Client–server systems are usually most frequently implemented by (and often identified with) the request–response model: a client sends a request to the server, which performs some action and sends a response back to the client, typically with a result or acknowledg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |