|
Hacker (other)
A hacker is a person skilled in information technology who achieves goals by non-standard means. The term has become associated in popular culture with a security hackersomeone with knowledge of bugs or exploits to break into computer systems and access data which would otherwise be inaccessible to them. In a positive connotation, though, hacking can also be utilized by legitimate figures in legal situations. For example, law enforcement agencies sometimes use hacking techniques to collect evidence on criminals and other malicious actors. This could include using anonymity tools (such as a VPN or the dark web) to mask their identities online and pose as criminals. Likewise, covert world agencies can employ hacking techniques in the legal conduct of their work. Hacking and cyber-attacks are used extra-legally and illegally by law enforcement and security agencies (conducting warrantless espionage r even sabotage">sabotage.html" ;"title="r even sabotage">r even sabotageactiviti ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Coding Da Vinci - Der Kultur-Hackathon (14123515524)
{{disambiguation ...
Coding may refer to: Computer science * Computer programming, the process of creating and maintaining the source code of computer programs * Line coding, in data storage * Source coding, compression used in data transmission * Coding theory * Channel coding, in coding theory Other uses * Coding (social sciences), an analytical process in which data are categorized for analysis * Coding strand of DNA in molecular biology * Legal coding, the process of creating summary or keyword data from a document in the legal profession * Medical coding, representation of medical diagnoses and procedures in standard code numbers * Queer coding *Coding Theory See also * Code * Entropy encoding * Transform coding Transform coding is a type of data compression for "natural" data like audio signals or photographic images. The transformation is typically lossless (perfectly reversible) on its own but is used to enable better (more targeted) quantization, whi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Hacker
A security hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, information gathering, challenge, recreation, or evaluation of a system weaknesses to assist in formulating defenses against potential hackers. The subculture that has evolved around hackers is often referred to as the "computer underground". Longstanding controversy surrounds the meaning of the term "hacker." In this controversy, computer programmers reclaim the term ''hacker'', arguing that it refers simply to someone with an advanced understanding of computers and computer networks and that ''cracker'' is the more appropriate term for those who break into computers, whether computer criminals ( black hats) or computer security experts ( white hats). A 2014 article noted that "the black-hat meaning still prevails among the general public". History Birth of subcult ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Phreaker
Phreaking is a slang term coined to describe the activity of a culture of people who study, experiment with, or explore telecommunication systems, such as equipment and systems connected to public telephone networks. The term ''phreak'' is a sensational spelling of the word ''freak'' with the ''ph-'' from ''phone'', and may also refer to the use of various audio frequencies to manipulate a phone system. ''Phreak'', ''phreaker'', or ''phone phreak'' are names used for and by individuals who participate in phreaking. The term first referred to groups who had reverse engineered the system of tones used to route long-distance calls. By re-creating these tones, phreaks could switch calls from the phone handset, allowing free calls to be made around the world. To ease the creation of these tones, electronic tone generators known as blue boxes became a staple of the phreaker community. This community included future Apple Inc. cofounders Steve Jobs and Steve Wozniak. The blue box er ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Tech (newspaper)
''The Tech'', first published on November 16, 1881, is the campus newspaper at the Massachusetts Institute of Technology in Cambridge, Massachusetts. Editions are published on Thursdays throughout the academic year and about once a month over the summer. ''The Tech'' established an early presence on the World Wide Web, and continues to publish online in tandem with the print edition.Kristina Grifantini"The Tech, Then and Now" ''MIT Technology Review'', June 23, 2008. Organization ''The Tech'' is a completely student-managed, and largely student-written publication, officially recognized as a student activity by the administration of the Massachusetts Institute of Technology. The newspaper is largely self-supporting financially, deriving most of its income from advertising. The publication has an advisory board composed primarily of ex-staffers who are alumni of MIT. Print edition Printed copies are distributed throughout the MIT campus on the morning of publication. Since Febr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fred Shapiro
Fred Richard Shapiro is an American academic and writer working as the editor of ''The Yale Book of Quotations'', ''The Oxford Dictionary of American Legal Quotations'', and several other books. Education Shapiro earned a Bachelor of Science degree from the Massachusetts Institute of Technology, a Master of Library Science from the Catholic University of America, and a Juris Doctor from Harvard Law School. Career Shapiro has published numerous articles on language, law, and information science, including "The Politically Correct United States Supreme Court and the Motherfucking Texas Court of Appeals: Using Legal Databases to Trace the Origins of Words and Quotations" and "Who Wrote the Serenity Prayer". He is an associate librarian and lecturer in legal research at Yale Law School. His work in identifying sources of recent sayings is seen in ''The Dictionary of Modern Proverbs''.Doyle, Charles Clay, Wolfgang Mieder Wolfgang Mieder (born 17 February 1944) is a retired profes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rolling Stone
''Rolling Stone'' is an American monthly magazine that focuses on music, politics, and popular culture. It was founded in San Francisco, San Francisco, California, in 1967 by Jann Wenner, and the music critic Ralph J. Gleason. It was first known for its coverage of rock music and political reporting by Hunter S. Thompson. In the 1990s, the magazine broadened and shifted its focus to a younger readership interested in youth-oriented television shows, film actors, and popular music. It has since returned to its traditional mix of content, including music, entertainment, and politics. The first magazine was released in 1967 and featured John Lennon on the cover and was published every two weeks. It is known for provocative photography and its cover photos, featuring musicians, politicians, athletes, and actors. In addition to its print version in the United States, it publishes content through Rollingstone.com and numerous international editions. Penske Media Corporation is the c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Stewart Brand
Stewart Brand (born December 14, 1938) is an American writer, best known as editor of the ''Whole Earth Catalog''. He founded a number of organizations, including The WELL, the Global Business Network, and the Long Now Foundation. He is the author of several books, most recently '' Whole Earth Discipline: An Ecopragmatist Manifesto''. Life Brand was born in Rockford, Illinois, and attended Phillips Exeter Academy in New Hampshire. He studied biology at Stanford University, graduating in 1960. As a soldier in the U.S. Army, he was a parachutist and taught infantry skills; he later expressed the view that his experience in the military had fostered his competence in organizing. A civilian again in 1962, he studied design at San Francisco Art Institute, photography at San Francisco State College, and participated in a legitimate scientific study of then-legal LSD, in Menlo Park, California. In 1966, he married mathematician Lois Jennings, an Ottawa Native American.Brand 20 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Alan Kay
Alan Curtis Kay (born May 17, 1940) published by the Association for Computing Machinery 2012 is an American computer scientist best known for his pioneering work on object-oriented programming and windowing graphical user interface (GUI) design. At Xerox PARC he led the design and development of the first modern windowed computer desktop interface. There he also led the development of the influential object-oriented programming language Smalltalk, both personally designing most of the early versions of the language and coining the term "object-oriented." He has been elected a Fellow of the American Academy of Arts and Sciences, the National Academy of Engineering, and the Royal Society of Arts. He received the Turing award in 2003. Kay is also a former professional jazz guitarist, composer, and theatrical designer. He also is an amateur classical pipe organist. Early life and work In an interview on education in America with the Davis Group Ltd., Kay said: Ori ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Geek
The word ''geek'' is a slang term originally used to describe Eccentricity (behavior), eccentric or non-mainstream people; in current use, the word typically connotes an expert or enthusiast obsessed with a hobby or intellectual pursuit. In the past, it had a generally pejorative meaning of a "peculiar person, especially one who is perceived to be overly intellectual, unfashionable, boring, or socially awkward". In the 21st century, it was reappropriation, reclaimed and used by many people, especially members of some fandoms, as a positive term. Some use the term self-referentially without malice or as a source of pride, often referring simply to "someone who is interested in a subject (usually intellectual or complex) for its own sake". The term ''geek'' is often used in association with the terms ''nerd and wikt:dweeb, dweeb.'' Etymology The word comes from English dialect ''geek'' or ''geck'' (meaning a "fool" or "freak"; from Middle Low German ''Geck''). ''Geck'' is a st ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Jargon File
The Jargon File is a glossary and usage dictionary of slang used by computer programmers. The original Jargon File was a collection of terms from technical cultures such as the MIT AI Lab, the Stanford AI Lab (SAIL) and others of the old ARPANET AI/ LISP/PDP-10 communities, including Bolt, Beranek and Newman, Carnegie Mellon University, and Worcester Polytechnic Institute. It was published in paperback form in 1983 as ''The Hacker's Dictionary'' (edited by Guy Steele), revised in 1991 as ''The New Hacker's Dictionary'' (ed. Eric S. Raymond; third edition published 1996). The concept of the file began with the Tech Model Railroad Club (TMRC) that came out of early TX-0 and PDP-1 hackers in the 1950s, where the term hacker emerged and the ethic, philosophies and some of the nomenclature emerged. 1975 to 1983 The Jargon File (referred to here as "Jargon-1" or "the File") was made by Raphael Finkel at Stanford in 1975. From that time until the plug was finally pulled on the SAIL ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
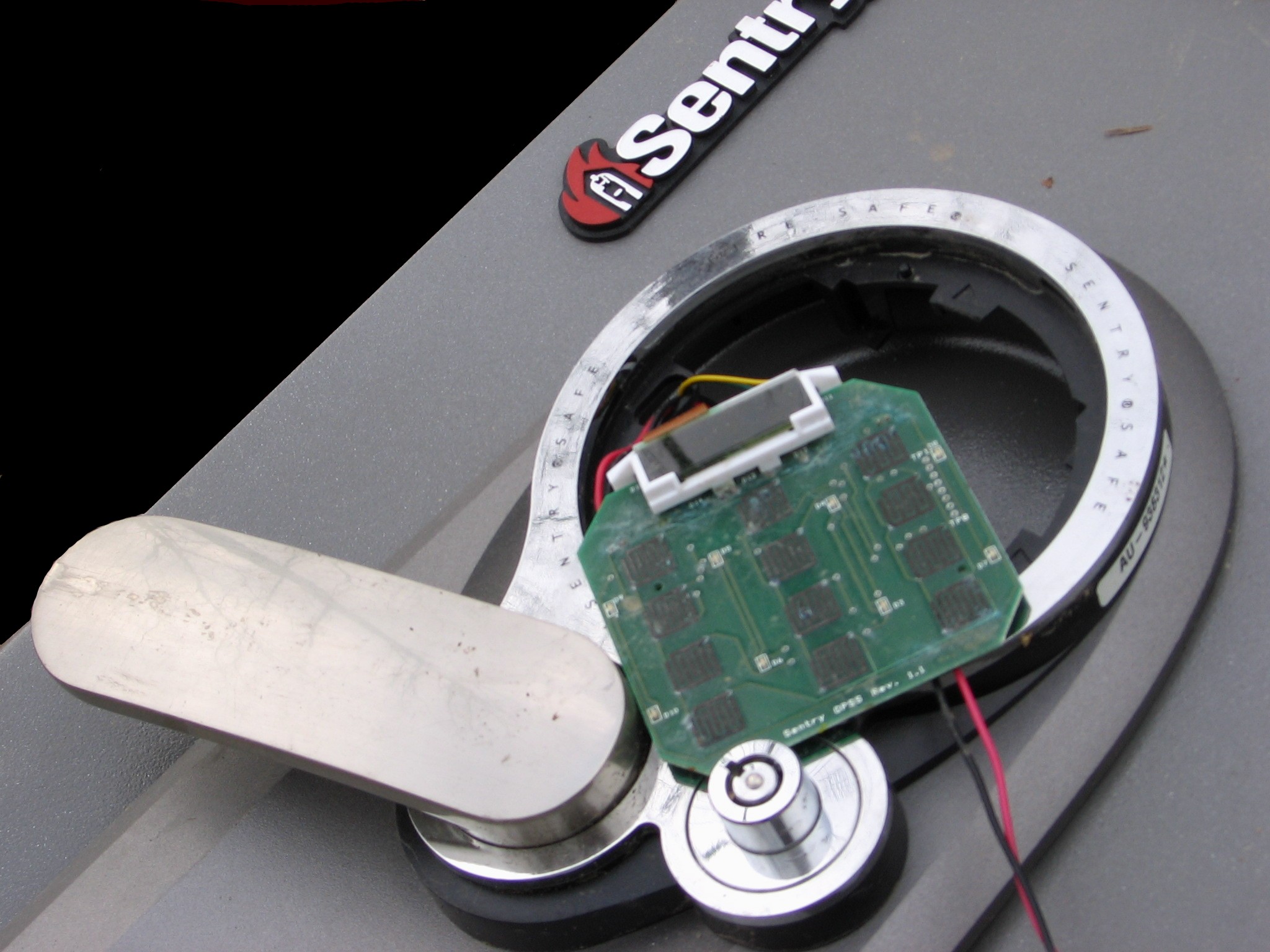
Safecracker
Safe-cracking is the process of opening a safe without either the combination or the key. Physical methods Different procedures may be used to crack a safe, depending on its construction. Different procedures are required to open different safes, so safe-crackers need to be aware of the differences. Lock manipulation Lock manipulation is a damage-free combination recovery method and a well known surreptitious bypass technique. Manipulation only requires fingers, eyes, and proper technique, though it is a skill that takes years to develop. While manipulation of combination locks is usually performed on Group 2 locks, many Group 1 locks are susceptible to manipulation. It involves the manipulation of the lock in order to obtain the combination one number at a time. Manipulation procedures can vary, but they all rely on exploiting the presence of mechanical imperfections in the lock, unlocking the safe and recovering its combination, which can then be reused to open the safe lock ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Script Kiddie
A script kiddie, skiddie, kiddie, or skid is an unskilled individual who uses scripts or programs developed by others, primarily for malicious purposes. Characteristics In a Carnegie Mellon report prepared for the U.K. Department of Defense in 2000, script kiddies are defined as The more immature but unfortunately often just as dangerous exploiter of security lapses on the Internet. The typical script kiddy uses existing and frequently well known and easy-to-find techniques and programs or scripts to search for and exploit weaknesses in other computers on the Internet—often randomly and with little regard or perhaps even understanding of the potentially harmful consequences. Script kiddies have at their disposal a large number of effective, easily downloadable programs capable of breaching computers and networks. Script kiddies vandalize websites both for the thrill of it and to increase their reputation among their peers. Some more malicious script kiddies have used virus to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)



.jpg)