|
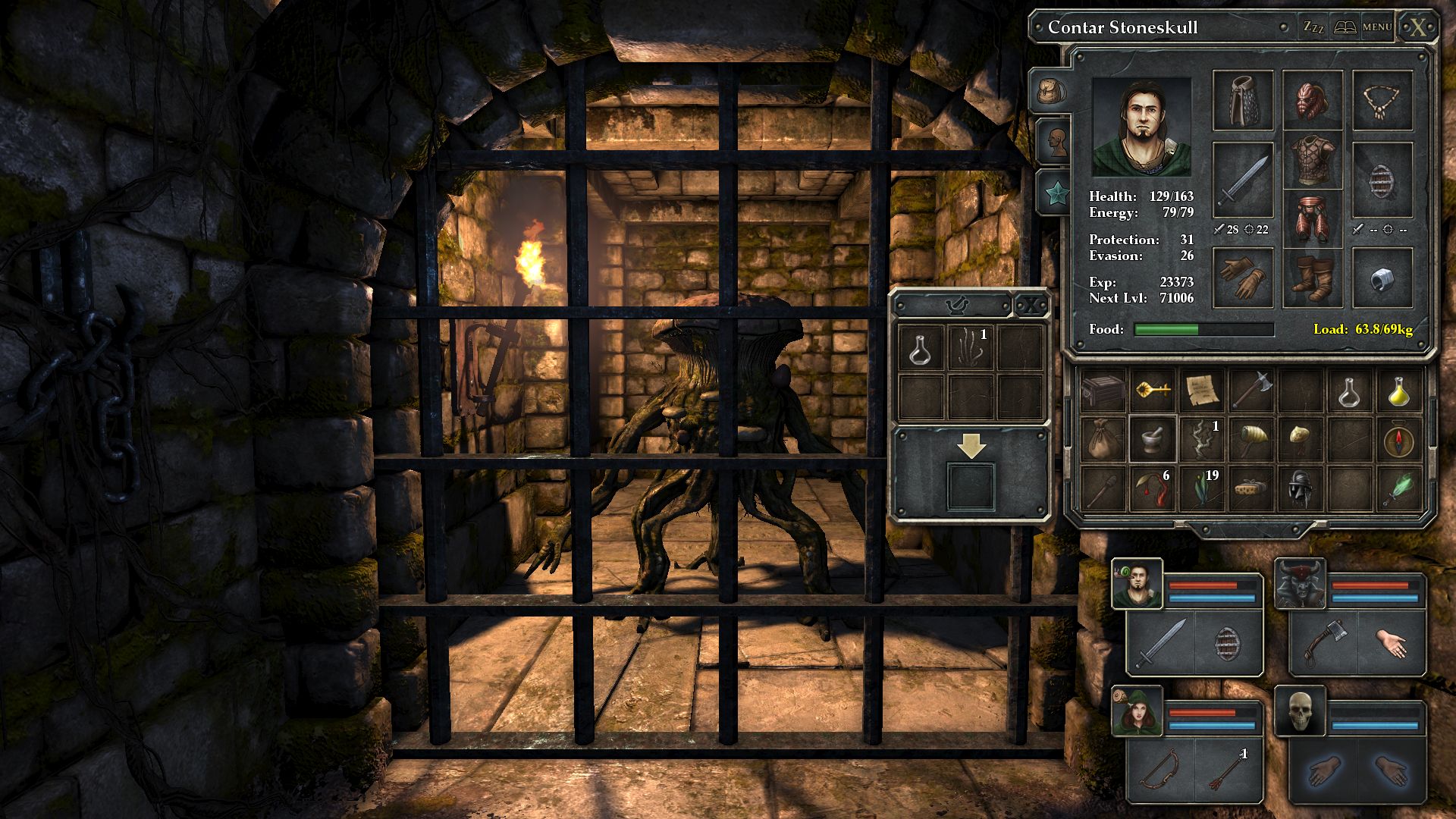
Grendel's Cave
''Grendel's Cave'' is a real-time browser-based role-playing video game and MUD from Grendel Enterprises. The basis for ''Grendel’s Cave'' was Anglo-Saxon mythology and Beowulf, and it is set in the historical medieval period. Scholars consider it an artistic depiction of Grendel and the poem, Beowulf, as well as a modern adaptation and a derivative work of the epic. Educational websites use ''Grendel's Cave'' as an Internet learning aid for medieval literature and they considered it an online Beowulf resource. Literary significance ''Grendel's Cave'' was an online Beowulf resource that goes beyond the written text by allowing players to participate in the story. Scholars consider it a modern adaptation of the original Beowulf poem. Glenco McGraw-Hill uses the site as part of their Study Guide for Beowulf. Educational websites use ''Grendel's Cave'' as an online reference for medieval literature. History Mars Software Products wrote the first version of ''Grendel's Ca ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Role-playing Video Game
A role-playing video game (commonly referred to as simply a role-playing game or RPG, as well as a computer role-playing game or CRPG) is a video game genre where the player controls the actions of a character (or several party members) immersed in some well-defined world, usually involving some form of character development by way of recording statistics. Many role-playing video games have origins in tabletop role-playing games Adams, Rollings 2003, p. 347 and use much of the same terminology, settings and game mechanics. Other major similarities with pen-and-paper games include developed story-telling and narrative elements, player character development, complexity, as well as replay value and immersion. The electronic medium removes the necessity for a gamemaster and increases combat resolution speed. RPGs have evolved from simple text-based console-window games into visually rich 3D experiences. Characteristics Role-playing video games use much of the same terminology, s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Role-playing Game (pen And Paper)
A tabletop role-playing game (typically abbreviated as TRPG or TTRPG), also known as a pen-and-paper role-playing game, is a form of role-playing game (RPG) in which the participants describe their characters' actions through speech. Participants determine the actions of their characters based on their characterization, and the actions succeed or fail according to a set formal system of rules and guidelines. Within the rules, players have the freedom to improvise; their choices shape the direction and outcome of the game. The terms ''pen-and-paper'' and ''tabletop'' are generally only used to distinguish this format of RPG from other formats, since neither pen and paper nor a table are strictly necessary. Gameplay Overview In most games, a specially designated player typically called the game master (GM) purchases or prepares a set of rules and a fictional setting in which each player acts out the role of a single character. The GM describes the game world and its inhabita ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Audio Game
An audio game is an electronic game played on a device such as a personal computer. It is similar to a video game save that there is audible and tactile feedback but not visual. Audio games originally started out as 'blind accessible'-games and were developed mostly by amateurs and blind programmers. But more and more people are showing interest in audio games, ranging from sound artists, game accessibility researchers, mobile game developers and mainstream video gamers. Most audio games run on a personal computer platform, although there are a few audio games for handhelds and video game consoles. Audio games feature the same variety of genres as video games, such as adventure games, racing games, etc. Audio game history The term "electronic game" is commonly understood as a synonym for the narrower concept of the "video game." This is understandable as both electronic games and video games have developed in parallel and the game market has always had a strong bias to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Non-player Character
A non-player character (NPC), or non-playable character, is any character in a game that is not controlled by a player. The term originated in traditional tabletop role-playing games where it applies to characters controlled by the gamemaster or referee rather than by another player. In video games, this usually means a character controlled by the computer (instead of a player) that has a predetermined set of behaviors that potentially will impact gameplay, but will not necessarily be the product of true artificial intelligence. Role-playing games In a traditional tabletop role-playing game such as ''Dungeons & Dragons'', an NPC is a character portrayed by the gamemaster (GM). While the player characters (PCs) form the narrative's protagonists, non-player characters can be thought of as the "supporting cast" or "extras" of a roleplaying narrative. Non-player characters populate the fictional world of the game, and can fill any role not occupied by a player character. Non-player ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Norse Mythology
Norse, Nordic, or Scandinavian mythology is the body of myths belonging to the North Germanic peoples, stemming from Old Norse religion and continuing after the Christianization of Scandinavia, and into the Nordic folklore of the modern period. The northernmost extension of Germanic mythology and stemming from Proto-Germanic folklore, Norse mythology consists of tales of various deities, beings, and heroes derived from numerous sources from both before and after the pagan period, including medieval manuscripts, archaeological representations, and folk tradition. The source texts mention numerous gods such as the thunder-god Thor, the raven-flanked god Odin, the goddess Freyja, and numerous other deities. Most of the surviving mythology centers on the plights of the gods and their interaction with several other beings, such as humanity and the jötnar, beings who may be friends, lovers, foes, or family members of the gods. The cosmos in Norse mythology consists of Nine Worl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Release Life Cycle
A software release life cycle is the sum of the stages of development and maturity for a piece of computer software ranging from its initial development to its eventual release, and including updated versions of the released version to help improve the software or fix software bugs still present in the software. There are several models for such a life cycle. A common method is that suggested by Microsoft, which divides software development into five phases: Pre-alpha, Alpha, Beta, Release candidate, and Stable. Pre-alpha refers to all activities performed during the software project before formal testing. The alpha phase generally begins when the software is feature complete but likely to contain several known or unknown bugs. The beta phase generally begins when the software is deemed feature complete, yet likely to contain several known or unknown bugs. Software in the production phase will generally have many more bugs in it than completed software, as well as speed/performan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Beta Version
A software release life cycle is the sum of the stages of development and maturity for a piece of computer software ranging from its initial development to its eventual release, and including updated versions of the released version to help improve the software or fix software bugs still present in the software. There are several models for such a life cycle. A common method is that suggested by Microsoft, which divides software development into five phases: Pre-alpha, Alpha, Beta, Release candidate, and Stable. Pre-alpha refers to all activities performed during the software project before formal testing. The alpha phase generally begins when the software is feature complete but likely to contain several known or unknown bugs. The beta phase generally begins when the software is deemed feature complete, yet likely to contain several known or unknown bugs. Software in the production phase will generally have many more bugs in it than completed software, as well as speed/performan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Database Server
A database server is a server which uses a database application that provides database services to other computer programs or to computers, as defined by the client–server model. Database management systems (DBMSs) frequently provide database-server functionality, and some database management systems (such as MySQL) rely exclusively on the client–server model for database access (while others, like SQLite, are meant for use as an embedded database). Users access a database server either through a " front end" running on the user's computerwhich displays requested dataor through the " back end", which runs on the server and handles tasks such as data analysis and storage. In a master-slave model, database master servers are central and primary locations of data while database slave servers are synchronized backups of the master acting as proxies. Most database applications respond to a query language. Each database understands its query language and converts each submitted ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Source Code
In computing, source code, or simply code, is any collection of code, with or without comments, written using a human-readable programming language, usually as plain text. The source code of a program is specially designed to facilitate the work of computer programmers, who specify the actions to be performed by a computer mostly by writing source code. The source code is often transformed by an assembler or compiler into binary machine code that can be executed by the computer. The machine code is then available for execution at a later time. Most application software is distributed in a form that includes only executable files. If the source code were included it would be useful to a user, programmer or a system administrator, any of whom might wish to study or modify the program. Alternatively, depending on the technology being used, source code may be interpreted and executed directly. Definitions Richard Stallman's definition, formulated in his 1989 seminal li ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cheating In Video Games
Cheating in video games involves a video game player using various methods to create an advantage beyond normal gameplay, usually in order to make the game easier. Cheats may be activated from within the game itself (a cheat code implemented by the original game developers), or created by third-party software (a game trainer or debugger) or hardware (a cheat cartridge). They can also be realized by exploiting software bugs; this may or may not be considered cheating based on whether the bug is considered common knowledge. History Cheating in video games has existed for almost their entire history. The first cheat codes were put in place for play testing purposes. Playtesters had to rigorously test the mechanics of a game and introduced cheat codes to make this process easier. An early cheat code can be found in ''Manic Miner'', where typing "6031769" (based on Matthew Smith's driving license) enables the cheat mode. Within months of '' Wizardry: Proving Grounds of the Mad Ov ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hacker (computer Security)
A security hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, information gathering, challenge, recreation, or evaluation of a system weaknesses to assist in formulating defenses against potential hackers. The subculture that has evolved around hackers is often referred to as the "computer underground". Longstanding controversy surrounds the meaning of the term "hacker." In this controversy, computer programmers reclaim the term ''hacker'', arguing that it refers simply to someone with an advanced understanding of computers and computer networks and that ''cracker'' is the more appropriate term for those who break into computers, whether computer criminals ( black hats) or computer security experts ( white hats). A 2014 article noted that "the black-hat meaning still prevails among the general public". History Birth of subcult ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
World Wide Web
The World Wide Web (WWW), commonly known as the Web, is an information system enabling documents and other web resources to be accessed over the Internet. Documents and downloadable media are made available to the network through web servers and can be accessed by programs such as web browsers. Servers and resources on the World Wide Web are identified and located through character strings called uniform resource locators (URLs). The original and still very common document type is a web page formatted in Hypertext Markup Language (HTML). This markup language supports plain text, images, embedded video and audio contents, and scripts (short programs) that implement complex user interaction. The HTML language also supports hyperlinks (embedded URLs) which provide immediate access to other web resources. Web navigation, or web surfing, is the common practice of following such hyperlinks across multiple websites. Web applications are web pages that function as application s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |