|
Geom Cube
GEOM is the main storage framework for the FreeBSD operating system. It is available in FreeBSD 5.0 and later releases, and provides a standardized way to access storage layers. GEOM is modular and allows for ''geom modules'' to connect to the framework. For example, the geom_mirror module provides RAID1 or mirroring functionality to the system. A number of modules are provided as part of FreeBSD and others have been developed independently and are distributed via (e.g.) GitHub. GEOM was developed for the FreeBSD Project by Poul-Henning Kamp and NAI Labs, the Security Research Division of Network Associates, Inc. under DARPA/SPAWAR contract N66001-01-C-8035 ("CBOSS"), as part of the DARPA CHATS research program. The name symbolizes its impact on disk geometry. Stacked design Because of geom's modular design, modules can be 'stacked' together to form a chain of geom layers. For example, on top of the geom_mirror module an encryption module can be added, such as geom_eli to prov ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Framework
In computer programming, a software framework is a software abstraction that provides generic functionality which developers can extend with custom code to create applications. It establishes a standard foundation for building and deploying software, offering reusable components and design patterns that handle common programming tasks within a larger software platform or environment. Unlike libraries where developers call functions as needed, frameworks implement inversion of control by dictating program structure and calling user code at specific points, while also providing default behaviors, structured extensibility mechanisms, and maintaining a fixed core that accepts extensions without direct modification. Frameworks also differ from regular applications that can be modified (like web browsers through extensions, video games through mods), in that frameworks are intentionally incomplete scaffolding meant to be extended through well-defined extension points and followin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RAID5
In computer storage, the standard RAID levels comprise a basic set of RAID ("redundant array of independent disks" or "redundant array of inexpensive disks") configurations that employ the techniques of striping, mirroring, or parity to create large reliable data stores from multiple general-purpose computer hard disk drives (HDDs). The most common types are RAID 0 (striping), RAID 1 (mirroring) and its variants, RAID 5 (distributed parity), and RAID 6 (dual parity). Multiple RAID levels can also be combined or '' nested'', for instance RAID 10 (striping of mirrors) or RAID 01 (mirroring stripe sets). RAID levels and their associated data formats are standardized by the Storage Networking Industry Association (SNIA) in the Common RAID Disk Drive Format (DDF) standard. The numerical values only serve as identifiers and do not signify performance, reliability, generation, hierarchy, or any other metric. While most RAID levels can provide good protection ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Shared Secret
In cryptography, a shared secret is a piece of data, known only to the parties involved, in a secure communication. This usually refers to the key of a symmetric cryptosystem. The shared secret can be a PIN code, a password, a passphrase, a big number, or an array of randomly chosen bytes. The shared secret is either shared beforehand between the communicating parties, in which case it can also be called a pre-shared key, or it is created at the start of the communication session by using a key-agreement protocol, for instance using public-key cryptography such as Diffie–Hellman or using symmetric-key cryptography such as Kerberos. The shared secret can be used for authentication (for instance when logging in to a remote system) using methods such as challenge–response or it can be fed to a key derivation function to produce one or more keys to use for encryption and/or MACing of messages. To make unique session and message keys the shared secret is usually comb ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GBDE
GBDE, standing for GEOM Based Disk Encryption, is a block device-layer disk encryption system written for FreeBSD, initially introduced in version 5.0. It is based on the GEOM disk framework. GBDE was designed and implemented by Poul-Henning Kamp and Network Associates Inc. (now known as McAfee). Design decisions Unlike most disk encryption software, GBDE does not attempt to defeat watermarking attacks through the use of disk encryption-specific modes of operation (see disk encryption theory), but instead generates a random key each time a sector is written. Unlike some alternatives, such as CBC with sector-specific initialization vectors, this approach does not reveal any information to the attacker even if they have access to snapshots of the disk image from different points in time, since encryption keys are never re-used. The one time sector key is encrypted using a pseudorandom key. This pseudorandom key is derived from the sector number and a static 2048-bit maste ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RIPEMD160
RIPEMD (RIPE Message Digest) is a family of cryptographic hash functions developed in 1992 (the original RIPEMD) and 1996 (other variants). There are five functions in the family: RIPEMD, RIPEMD-128, RIPEMD-160, RIPEMD-256, and RIPEMD-320, of which RIPEMD-160 is the most common. The original RIPEMD, as well as RIPEMD-128, is not considered secure because 128-bit result is too small and also (for the original RIPEMD) because of design weaknesses. The 256- and 320-bit versions of RIPEMD provide the same level of security as RIPEMD-128 and RIPEMD-160, respectively; they are designed for applications where the security level is sufficient but longer hash result is necessary. While RIPEMD functions are less popular than SHA-1 and SHA-2, they are used, among others, in Bitcoin and other cryptocurrencies based on Bitcoin. History The original RIPEMD function was designed in the framework of the EU project RIPE ( RACE Integrity Primitives Evaluation) in 1992. Its design was based ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SHA512
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published in 2001. They are built using the Merkle–Damgård construction, from a one-way compression function itself built using the Davies–Meyer structure from a specialized block cipher. SHA-2 includes significant changes from its predecessor, SHA-1. The SHA-2 family consists of six hash functions with digests (hash values) that are 224, 256, 384 or 512 bits: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256. SHA-256 and SHA-512 are hash functions whose digests are eight 32-bit and 64-bit words, respectively. They use different shift amounts and additive constants, but their structures are otherwise virtually identical, differing only in the number of rounds. SHA-224 and SHA-384 are truncated versions of SHA-256 and SHA-512 respectively, computed with different initial values. SHA-512/224 and SHA-512/256 are also truncate ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
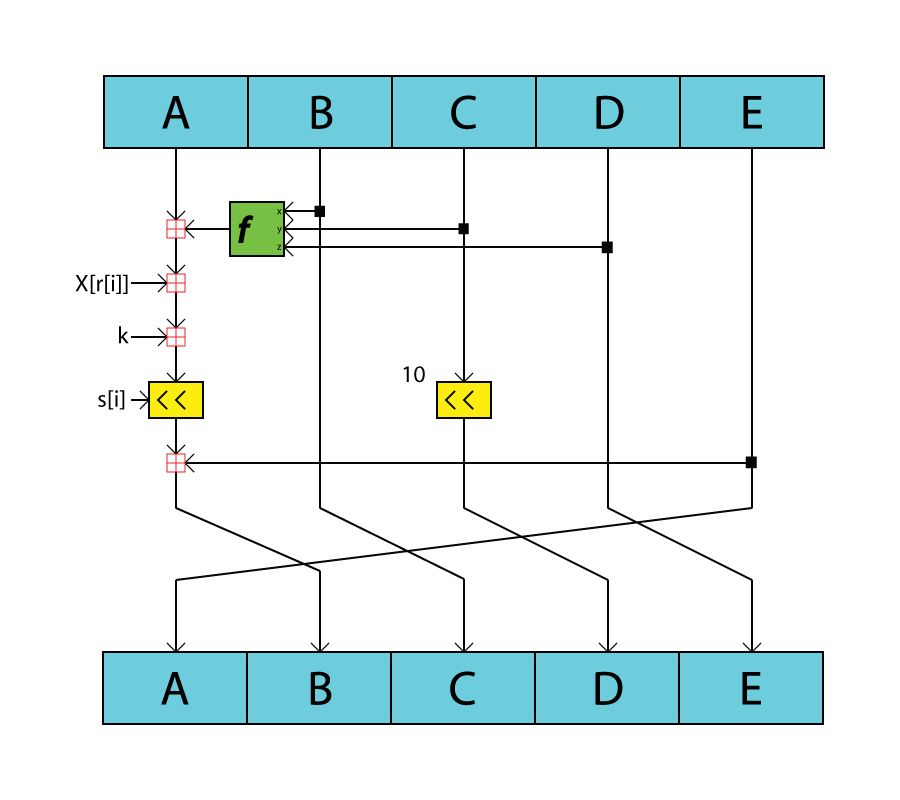
SHA1
In cryptography, SHA-1 (Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160- bit (20-byte) hash value known as a message digest – typically rendered as 40 hexadecimal digits. It was designed by the United States National Security Agency, and is a U.S. Federal Information Processing Standard. The algorithm has been cryptographically broken but is still widely used. Since 2005, SHA-1 has not been considered secure against well-funded opponents; as of 2010 many organizations have recommended its replacement. NIST formally deprecated use of SHA-1 in 2011 and disallowed its use for digital signatures in 2013, and declared that it should be phased out by 2030. , chosen-prefix attacks against SHA-1 are practical. As such, it is recommended to remove SHA-1 from products as soon as possible and instead use SHA-2 or SHA-3. Replacing SHA-1 is urgent where it is used for digital signatures. All major web browser vendors ceased acceptance of SHA-1 SSL ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Camellia (cipher)
In cryptography, Camellia is a symmetric key block cipher with a block size of 128 bits and key sizes of 128, 192 and 256 bits. It was jointly developed by Mitsubishi Electric and NTT of Japan. The cipher has been approved for use by the ISO/IEC, the European Union's NESSIE project and the Japanese CRYPTREC project. The cipher has security levels and processing abilities comparable to the Advanced Encryption Standard. The cipher was designed to be suitable for both software and hardware implementations, from low-cost smart cards to high-speed network systems. It is part of the Transport Layer Security (TLS) cryptographic protocol designed to provide communications security over a computer network such as the Internet. The cipher was named for the flower '' Camellia japonica'', which is known for being long-lived as well as because the cipher was developed in Japan. Design Camellia is a Feistel cipher with either 18 rounds (when using 128-bit keys) or 24 rounds (when usin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Triple DES
In cryptography, Triple DES (3DES or TDES), officially the Triple Data Encryption Algorithm (TDEA or Triple DEA), is a symmetric-key block cipher, which applies the DES cipher algorithm three times to each data block. The 56-bit key of the Data Encryption Standard (DES) is no longer considered adequate in the face of modern cryptanalytic techniques and supercomputing power; Triple DES increases the effective security to 112 bits. A CVE released in 2016, CVE-2016-2183', disclosed a major security vulnerability in the DES and 3DES encryption algorithms. This CVE, combined with the inadequate key size of 3DES, led to NIST deprecating 3DES in 2019 and disallowing all uses (except processing already encrypted data) by the end of 2023. It has been replaced with the more secure, more robust AES. While US government and industry standards abbreviate the algorithm's name as TDES (Triple DES) and TDEA (Triple Data Encryption Algorithm), RFC 1851 referred to it as 3DES from the tim ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blowfish (cipher)
Blowfish is a Symmetric-key algorithm, symmetric-key block cipher, designed in 1993 by Bruce Schneier and included in many cipher suites and encryption products. Blowfish provides a good encryption rate in software, and no effective cryptanalysis of it has been found to date for smaller files. It is recommended Blowfish should not be used to encrypt files larger than 4GB in size, Twofish should be used instead. Blowfish has a 64-bit block size and therefore it could be vulnerable to Sweet32 birthday attacks. Schneier designed Blowfish as a general-purpose algorithm, intended as an alternative to the aging Data Encryption Standard, DES and free of the problems and constraints associated with other algorithms. At the time Blowfish was released, many other designs were proprietary, encumbered by patents, or were commercial or government secrets. Schneier has stated that "Blowfish is unpatented, and will remain so in all countries. The algorithm is hereby placed in the public domai ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |