|
Freenom
.tk is the Internet country code top-level domain (Country code top-level domain, ccTLD) for Tokelau, a territory of New Zealand in the Australasia, South Pacific. It can be registered on the company Freenom. Overview Tokelau allows any individual to register domain names. Users and small businesses may register any number of domain names free of charge (with some restrictions). In addition to the name itself, users can opt to forward their web traffic using HTML frames and their email traffic, with a maximum of 250 addresses per user log in, or use full Domain Name System, DNS, either via their own or third-party servers, or by using Dot TK's servers. There are content restrictions for free domains, banning sites containing sexual content, drug use, hate speech, firearms, and spam or copyright infringement. Dot TK requires free domains to have a regular traffic of visitors, and if a domain's redirect target does not work (even temporarily) the domain is taken offline. If a domain ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Country Code Top-level Domain
A country code top-level domain (ccTLD) is an Internet top-level domain generally used or reserved for a country, sovereign state, or dependent territory identified with a country code. All ASCII ccTLD identifiers are two letters long, and all two-letter top-level domains are ccTLDs. In 2018, the Internet Assigned Numbers Authority (IANA) began implementing internationalized country code top-level domains, consisting of language-native characters when displayed in an end-user application. Creation and delegation of ccTLDs is described in RFC 1591, corresponding to ISO 3166-1 alpha-2 country codes. While gTLDs have to obey international regulations, ccTLDs are subjected to requirements that are determined by each country’s domain name regulation corporation. With over 150 million domain name registrations today or as of 2022, ccTLDs make up about 40% of the total domain name industry. Country code extension applications began in 1985. The registered country code extensions in t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Country Code Top-level Domains
A country code top-level domain (ccTLD) is an Internet top-level domain generally used or reserved for a country, sovereign state, or dependent territory identified with a country code. All ASCII ccTLD identifiers are two letters long, and all two-letter top-level domains are ccTLDs. In 2018, the Internet Assigned Numbers Authority (IANA) began implementing internationalized country code top-level domains, consisting of language-native characters when displayed in an end-user application. Creation and delegation of ccTLDs is described in RFC 1591, corresponding to ISO 3166-1 alpha-2 country codes. While gTLDs have to obey international regulations, ccTLDs are subjected to requirements that are determined by each country’s domain name regulation corporation. With over 150 million domain name registrations today or as of 2022, ccTLDs make up about 40% of the total domain name industry. Country code extension applications began in 1985. The registered country code extensions in th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Blog
A blog (a truncation of "weblog") is a discussion or informational website published on the World Wide Web consisting of discrete, often informal diary-style text entries (posts). Posts are typically displayed in reverse chronological order so that the most recent post appears first, at the top of the web page. Until 2009, blogs were usually the work of a single individual, occasionally of a small group, and often covered a single subject or topic. In the 2010s, "multi-author blogs" (MABs) emerged, featuring the writing of multiple authors and sometimes professionally edited. MABs from newspapers, other media outlets, universities, think tanks, advocacy groups, and similar institutions account for an increasing quantity of blog traffic. The rise of Twitter and other "microblogging" systems helps integrate MABs and single-author blogs into the news media. ''Blog'' can also be used as a verb, meaning ''to maintain or add content to a blog''. The emergence and growth of blogs i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
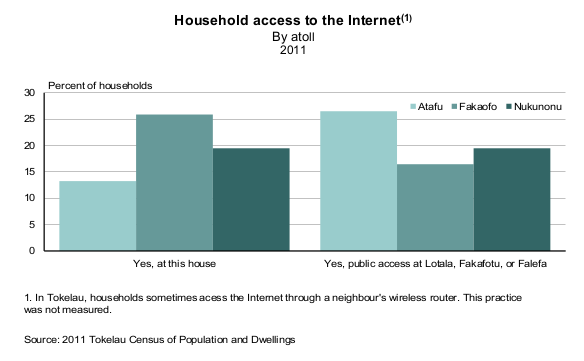
Internet In Tokelau
Internet in Tokelau is provided by Teletok, the government-owned"Bebo transforms remote Pacific youth" Stuff, 5 November 2007. communications corporation, and Taloha Inc., a private company formed by the Dutch Joost Zuurbier. Fakaoko villages, 2003. History In the year 2000,Interview: Dot TK Registry CEO, Joost ZuurbierPCMag, 10 May 2007 Joost Zuurbier realised that as Tokelau held an |
ZDNet
ZDNET is a business technology news website owned and operated by Red Ventures. The brand was founded on April 1, 1991, as a general interest technology portal from Ziff Davis and evolved into an enterprise IT-focused online publication. History Beginnings: 1991 to 1995 ZDNET began as a subscription-based digital service called "ZiffNet" that offered computing information to users of CompuServe. It featured computer industry forums, events, features and searchable archives. Initially, ZiffNet was intended to serve as a common place to find content from all Ziff-Davis print publications. As such, ZiffNet was an expansion on an earlier online service called PCMagNet for readers of PC Magazine. Launched in 1988, PCMagNet in turn was the evolution of Ziff Davis' first electronic publishing venture, a bulletin board, which launched in 1985. On June 20, 1995, Ziff-Davis announced the consolidation of its online information services under a single name, ''ZD Net''. The service had ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti Phishing Working Group
The Anti-Phishing Working Group (APWG) is an international consortium that attempts to eliminate fraud and identity theft caused by phishing and related incidents It brings together businesses affected by phishing attacks: security products and service companies, law enforcement agencies, government agencies, trade associations, regional international treaty organizations, and communications companies. Founded in 2003 by David Jevans, the APWG has more than 3200 members from more than 1700 companies and agencies worldwide. Members include leading security companies such as Kaspersky Lab, BitDefender, NortonLifeLock, Symantec, McAfee, VeriSign, IronKey, and Internet Identity. Financial industry members include the ING Group, VISA (credit card), VISA, MasterCard, and the American Bankers Association. See also *Scareware *PhishTank References External linksAPWG official website Spamming Technology consortia {{org-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Age
''The Age'' is a daily newspaper in Melbourne, Australia, that has been published since 1854. Owned and published by Nine Entertainment, ''The Age'' primarily serves Victoria (Australia), Victoria, but copies also sell in Tasmania, the Australian Capital Territory and border regions of South Australia and southern New South Wales. It is delivered both in print and digital formats. The newspaper shares some articles with its sister newspaper ''The Sydney Morning Herald''. ''The Age'' is considered a newspaper of record for Australia, and has variously been known for its investigative reporting, with its journalists having won dozens of Walkley Awards, Australia's most prestigious journalism prize. , ''The Age'' had a monthly readership of 5.321 million. History Foundation ''The Age'' was founded by three Melbourne businessmen: brothers John and Henry Cooke (who had arrived from New Zealand in the 1840s) and Walter Powell. The first edition appeared on 17 October 1854. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Spam (electronic)
Spamming is the use of messaging systems to send multiple unsolicited messages (spam) to large numbers of recipients for the purpose of commercial advertising, for the purpose of non-commercial proselytizing, for any prohibited purpose (especially the fraudulent purpose of phishing), or simply repeatedly sending the same message to the same user. While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging spam, Internet forum spam, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam. It is named after Spam, a luncheon meat, by way of a Monty Python sketch about a restaurant that has Spam in almost every dish in which Vikings annoyingly sing "Spam" repeatedly. Spamming remains economically viable because advertisers have no ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Phishing
Phishing is a type of social engineering where an attacker sends a fraudulent (e.g., spoofed, fake, or otherwise deceptive) message designed to trick a person into revealing sensitive information to the attacker or to deploy malicious software on the victim's infrastructure like ransomware. Phishing attacks have become increasingly sophisticated and often transparently mirror the site being targeted, allowing the attacker to observe everything while the victim is navigating the site, and transverse any additional security boundaries with the victim. As of 2020, phishing is by far the most common attack performed by cybercriminals, the FBI's Internet Crime Complaint Centre recording over twice as many incidents of phishing than any other type of computer crime. The first recorded use of the term "phishing" was in the cracking toolkit AOHell created by Koceilah Rekouche in 1995; however, it is possible that the term was used before this in a print edition of the hacker magazin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Scam
A confidence trick is an attempt to defraud a person or group after first gaining their trust. Confidence tricks exploit victims using their credulity, naïveté, compassion, vanity, confidence, irresponsibility, and greed. Researchers have defined confidence tricks as "a distinctive species of fraudulent conduct ..intending to further voluntary exchanges that are not mutually beneficial", as they "benefit con operators ('con men') at the expense of their victims (the 'marks')". Terminology Synonyms include con, confidence game, confidence scheme, ripoff, scam, and stratagem. The perpetrator of a confidence trick (or "con trick") is often referred to as a confidence (or "con") man, con-artist, or a "grifter". The shell game dates back at least to Ancient Greece. Samuel Thompson (1821–1856) was the original "confidence man". Thompson was a clumsy swindler who asked his victims to express confidence in him by giving him money or their watch rather than gaining their confidenc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Traffic
Web traffic is the data sent and received by visitors to a website. Since the mid-1990s, web traffic has been the largest portion of Internet traffic. Sites monitor the incoming and outgoing traffic to see which parts or pages of their site are popular and if there are any apparent trends, such as one specific page being viewed mostly by people in a particular country. There are many ways to monitor this traffic, and the gathered data is used to help structure sites, highlight security problems or indicate a potential lack of bandwidth. Not all web traffic is welcomed. Some companies offer advertising schemes that, in return for increased web traffic (visitors), pay for screen space on the site. Sites also often aim to increase their web traffic through inclusion on search engines and through search engine optimization. Analysis Web analytics is the measurement of the behavior of visitors to a website. In a commercial context, it especially refers to the measurement of which ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
McAfee
McAfee Corp. ( ), formerly known as McAfee Associates, Inc. from 1987 to 1997 and 2004 to 2014, Network Associates Inc. from 1997 to 2004, and Intel Security Group from 2014 to 2017, is an American global computer security software company headquartered in San Jose, California. The company was purchased by Intel in February 2011, and became part of the Intel Security division. In 2017, Intel had a strategic deal with TPG Capital and converted Intel Security into a joint venture between both companies called McAfee. Thoma Bravo took a minority stake in the new company, and Intel retained a 49% stake. The owners took McAfee public on the NASDAQ in 2020, and in 2022 an investor group led by Advent International Corporation took it private again. History 1987–1999 The company was founded in 1987 as McAfee Associates, named for its founder John McAfee, who resigned from the company in 1994. McAfee was incorporated in the state of Delaware in 1992. In 1993, McAfee stepped do ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |


.jpg)


