|
Fax Server
A fax server is a system installed in a local area network (LAN) server that allows computer users whose computers are attached to the LAN to send and receive fax messages. Alternatively the term ''fax server'' is sometimes used to describe a program that enables a computer to send and receive fax messages, set of software running on a server computer which is equipped with one or more fax-capable modems (or dedicated fax boards) attached to telephone lines or, more recently, software modem emulators which use T.38 ("Fax over IP") technology to transmit the signal over an IP network. Its function is to accept documents from users, convert them into faxes, and transmit them, as well as to receive fax calls and either store the incoming documents or pass them on to users. Users may communicate with the server in several ways, through either a local network or the Internet. In a big organization with heavy fax traffic, the computer hosting the fax server may be dedicated to that func ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Local Area Network
A local area network (LAN) is a computer network that interconnects computers within a limited area such as a residence, school, laboratory, university campus or office building. By contrast, a wide area network (WAN) not only covers a larger geographic distance, but also generally involves leased telecommunication circuits. Ethernet and Wi-Fi are the two most common technologies in use for local area networks. Historical network technologies include ARCNET, Token Ring and AppleTalk. History The increasing demand and usage of computers in universities and research labs in the late 1960s generated the need to provide high-speed interconnections between computer systems. A 1970 report from the Lawrence Radiation Laboratory detailing the growth of their "Octopus" network gave a good indication of the situation. A number of experimental and early commercial LAN technologies were developed in the 1970s. Cambridge Ring was developed at Cambridge University starting in 1974. Ethe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Logging (computer Security)
In computer security, logging in (or logging on, signing in, or signing on) is the process by which an individual gains access to a computer system by identifying and authenticating themselves. The user credentials are typically some form of username and a matching password, and these credentials themselves are sometimes referred to as ''a'' login (or logon, sign-in, sign-on).Oxford Dictionaries definition of ''login''. detail and definition of ''login'' and ''logging in''. In practice, modern secure systems often require a second factor such as |
Unified Messaging
Unified messaging (or UM) is a business term for the integration of different electronic messaging and communications media (e-mail, SMS, fax, voicemail, video messaging, etc.) technologies into a single interface, accessible from a variety of different devices. While traditional communications systems delivered messages into several different types of stores such as voicemail systems, e-mail servers, and stand-alone fax machines, with Unified Messaging all types of messages are stored in one system. Voicemail messages, for example, can be delivered directly into the user's inbox and played either through a headset or the computer's speaker. This simplifies the user's experience (only one place to check for messages) and can offer new options for workflow such as appending notes or documents to forwarded voicemails. Unified messaging is increasingly accepted in the corporate environment, where it's generally seen as an improvement to business productivity. Unified messaging for pr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Fax
Internet fax, e-fax, or online fax is the use of the internet and internet protocols to send a fax (facsimile), rather than using a standard telephone connection and a fax machine. A distinguishing feature of Internet fax, compared to other Internet communications such as email, is the ability to exchange fax messages with traditional telephone-based fax machines. Purpose Fax has no technical advantage over other means of sending information over the Internet, using technologies such as email, scanner, and graphics file formats; however, it is extremely simple to use: put the documents to be faxed in a hopper, dial a phone number, and press a button. Fax continues to be used over the telephone network at locations without computer and Internet facilities; and sometimes a fax of a document with a person's handwritten signature is a requirement for legal reasons. Faxes can be sent from electronic devices, often referred to as online faxing which allows faxes to be sent and received ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Product Bundling
In marketing, product bundling is offering several products or services for sale as one combined product or service package. It is a common feature in many imperfectly competitive product and service markets. Industries engaged in the practice include telecommunications services, financial services, health care, information, and consumer electronics. A software bundle might include a word processor, spreadsheet, and presentation program into a single office suite. The cable television industry often bundles many TV and movie channels into a single tier or package. The fast food industry combines separate food items into a "meal deal" or "value meal". A bundle of products may be called a package deal, in recorded music or video games, a compilation or box set, or in publishing, an anthology. Most firms are multi-product or multi-service companies faced with the decision whether to sell products or services separately at individual prices or whether combinations of products sh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Paperless Office
A paperless office (or paper-free office) is a work environment in which the use of paper is eliminated or greatly reduced. This is done by converting documents and other papers into digital form, a process known as digitization. Proponents claim that "going paperless" can save money, boost productivity, save space, make documentation and information sharing easier, keep personal information more secure, and help the environment. The concept can be extended to communications outside the office as well. Definition The paperless world was a publicist's slogan, intended to describe the office of the future. It was facilitated by the popularization of video display computer terminals like the 1964 IBM 2260. An early prediction of the paperless office was made in a 1975 ''Business Week'' article. The idea was that office automation would make paper redundant for routine tasks such as record-keeping and bookkeeping, and it came to prominence with the introduction of the personal compu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
White List
A whitelist, allowlist, or passlist is a mechanism which explicitly allows some identified entities to access a particular privilege, service, mobility, or recognition i.e. it is a list of things allowed when everything is denied by default. It is the opposite of a blacklist, which is a list of things denied when everything is allowed by default. Email whitelists Spam filters often include the ability to "whitelist" certain sender IP addresses, email addresses or domain names to protect their email from being rejected or sent to a junk mail folder. These can be manually maintained by the user or system administrator - but can also refer to externally maintained whitelist services. Non-commercial whitelists Non-commercial whitelists are operated by various non-profit organisations, ISPs, and others interested in blocking spam. Rather than paying fees, the sender must pass a series of tests; for example, their email server must not be an open relay and have a static IP address. The ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
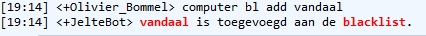
Blacklist
Blacklisting is the action of a group or authority compiling a blacklist (or black list) of people, countries or other entities to be avoided or distrusted as being deemed unacceptable to those making the list. If someone is on a blacklist, they are seen by a government or other organization as being one of a number of people who cannot be trusted or who is considered to have done something wrong. As a verb, blacklist can mean to put an individual or entity on such a list. Origins of the term The English dramatist Philip Massinger used the phrase "black list" in his 1639 tragedy ''The Unnatural Combat''. After the restoration of the English monarchy brought Charles II of England to the throne in 1660, a list of regicides named those to be punished for the execution of his father. The state papers of Charles II say "If any innocent soul be found in this black list, let him not be offended at me, but consider whether some mistaken principle or interest may not have misled ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Junk Fax
Junk faxes are a form of telemarketing where unsolicited advertisements are sent via fax transmission. Junk faxes are the faxed equivalent of spam or junk mail. Proponents of this advertising medium often use the terms ''broadcast fax'' or ''fax advertising'' to avoid the negative connotation of the term ''junk fax''. Junk faxes are generally considered to be a nuisance since they waste toner, ink and paper in fax machines. History Junk faxing came into widespread use in the late 1980s as a result of the development and proliferation of relatively inexpensive desktop fax machines which resulted in rapid growth in the number of fax machines in the U.S. The invention of the computer-based fax board in 1985 by Dr. Hank Magnuski, provided an efficient platform for reaching those fax machines with minimal cost and effort. The fax machines of this period typically used expensive thermal paper and a common complaint about junk faxes was that they consumed that expensive paper without pe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disaster Recovery
Disaster recovery is the process of maintaining or reestablishing vital infrastructure and systems following a natural or human-induced disaster, such as a storm or battle.It employs policies, tools, and procedures. Disaster recovery focuses on the information technology (IT) or technology systems supporting critical business functions as opposed to business continuity. This involves keeping all essential aspects of a business functioning despite significant disruptive events; it can therefore be considered a subset of business continuity. Disaster recovery assumes that the primary site is not immediately recoverable and restores data and services to a secondary site. IT service continuity IT Service Continuity (ITSC) is a subset of business continuity planning (BCP) that focuses on Recovery Point Objective (RPO) and Recovery Time Objective (RTO). It encompasses IT disaster recovery planning and wider IT resilience planning. It also incorporates IT infrastructure and services rela ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Center
A data center (American English) or data centre (British English)See spelling differences. is a building, a dedicated space within a building, or a group of buildings used to house computer systems and associated components, such as telecommunications and storage systems. Since IT operations are crucial for business continuity, it generally includes redundant or backup components and infrastructure for power supply, data communication connections, environmental controls (e.g., air conditioning, fire suppression), and various security devices. A large data center is an industrial-scale operation using as much electricity as a small town. History Data centers have their roots in the huge computer rooms of the 1940s, typified by ENIAC, one of the earliest examples of a data center.Old large computer rooms that housed machines like the U.S. Army's ENIAC, which were developed pre-1960 (1945), were now referred to as "data centers". Early computer systems, complex to operate and ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telecommunications Data Retention
Data retention defines the policies of persistent data and records management for meeting legal and business data archival requirements. Although sometimes interchangeable, it is not to be confused with the Data Protection Act 1998. The different data retention policies weigh legal and privacy concerns against economics and need-to-know concerns to determine the retention time, archival rules, data formats, and the permissible means of storage, access, and encryption. In the field of telecommunications, data retention generally refers to the storage of call detail records (CDRs) of telephony and internet traffic and transaction data ( IPDRs) by governments and commercial organisations. In the case of government data retention, the data that is stored is usually of telephone calls made and received, emails sent and received, and websites visited. Location data is also collected. The primary objective in government data retention is traffic analysis and mass surveillance. By analy ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |