|
Enterprise Information Security Architecture
Enterprise information security architecture (ZBI) is a part of enterprise architecture focusing on information security throughout the enterprise. The name implies a difference that may not exist between small/medium-sized businesses and larger organizations. Overview Enterprise information security architecture is becoming a common practice within financial institutions around the globe. The primary purpose of creating an enterprise information security architecture is to ensure that business strategy and IT security are aligned. Enterprise information security architecture topics Enterprise information security architecture was first formally positioned by Gartner in their whitepaper called “''Incorporating Security into the Enterprise Architecture Process''”. High-level security architecture framework Enterprise information security architecture frameworks are only a subset of enterprise architecture frameworks. If we had to simplify the conceptual abstraction o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IEEE
The Institute of Electrical and Electronics Engineers (IEEE) is a 501(c)(3) professional association for electronic engineering and electrical engineering (and associated disciplines) with its corporate office in New York City and its operations center in Piscataway, New Jersey. The mission of the IEEE is ''advancing technology for the benefit of humanity''. The IEEE was formed from the amalgamation of the American Institute of Electrical Engineers and the Institute of Radio Engineers in 1963. Due to its expansion of scope into so many related fields, it is simply referred to by the letters I-E-E-E (pronounced I-triple-E), except on legal business documents. , it is the world's largest association of technical professionals with more than 423,000 members in over 160 countries around the world. Its objectives are the educational and technical advancement of electrical and electronic engineering, telecommunications, computer engineering and similar disciplines. History Origin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Assurance
Information assurance (IA) is the practice of assuring information and managing risks related to the use, processing, storage, and transmission of information. Information assurance includes protection of the integrity, availability, authenticity, non-repudiation and confidentiality of user data. IA encompasses not only digital protections but also physical techniques. These protections apply to data in transit, both physical and electronic forms, as well as data at rest . IA is best thought of as a superset of information security (i.e. umbrella term), and as the business outcome of information risk management. Overview Information assurance (IA) is the process of processing, storing, and transmitting the right information to the right people at the right time. IA relates to the business level and strategic risk management of information and related systems, rather than the creation and application of security controls. IA is used to benefit business through the use of information ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Security
Information security, sometimes shortened to InfoSec, is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized/inappropriate access to data, or the unlawful use, disclosure, disruption, deletion, corruption, modification, inspection, recording, or devaluation of information. It also involves actions intended to reduce the adverse impacts of such incidents. Protected information may take any form, e.g. electronic or physical, tangible (e.g. paperwork) or intangible (e.g. knowledge). Information security's primary focus is the balanced protection of the confidentiality, integrity, and availability of data (also known as the CIA triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process that involves: * identifying inform ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Enterprise Architecture Planning
Enterprise architecture planning (EAP) in enterprise architecture is the planning process of defining architectures for the use of information in support of the business and the plan for implementing those architectures.The Chief Information Officers Council (1999). Federal Enterprise Architecture Framework Version 1.1'' September 1999. Overview One of the earlier professional practitioners in the field of system architecture Steven H. Spewak in 1992 defined Enterprise Architecture Planning (EAP) as "the process of defining architectures for the use of information in support of the business and the plan for implementing those architectures." Steven Spewak and S. C. Hill (1992) ''Enterprise Architecture Planning: Developing a Blueprint for Data, Applications, and Technology''. Boston, QED Pub. Group. p. 1 Spewak’s approach to EAP is similar to that taken by DOE in that the business mission is the primary driver. That is followed by the data required to satisfy the mission, fol ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zachman Framework
The Zachman Framework is an enterprise ontology and is a fundamental structure for enterprise architecture which provides a formal and structured way of viewing and defining an enterprise. The ontology is a two dimensional classification schema that reflects the intersection between two historical classifications. The first are primitive interrogatives: What, How, When, Who, Where, and Why. The second is derived from the philosophical concept of reification, the transformation of an abstract idea into an instantiation. The Zachman Framework reification transformations are: identification, definition, representation, specification, configuration and instantiation. The Zachman Framework is not a methodology in that it does not imply any specific method or process for collecting, managing, or using the information that it describes; rather, it is an ontology whereby a schema for organizing architectural artifacts (in other words, design documents, specifications, and models) is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
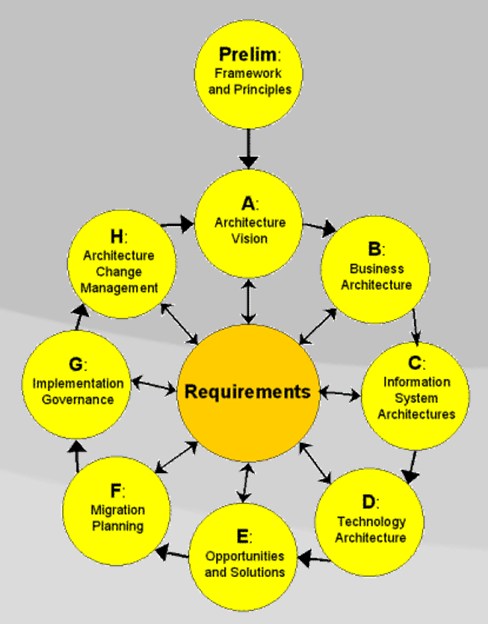
TOGAF
The Open Group Architecture Framework (TOGAF) is the most used framework for enterprise architecture as of 2020 that provides an approach for designing, planning, implementing, and governing an enterprise information technology architecture. TOGAF is a high-level approach to design. It is typically modeled at four levels: Business, Application, Data, and Technology. It relies heavily on modularization, standardization, and already existing, proven technologies and products. TOGAF was developed starting 1995 by The Open Group, based on United States Department of Defense's TAFIM and Capgemini's Integrated Architecture Framework (IAF). As of 2016, The Open Group claims that TOGAF is employed by 80% of Global 50 companies and 60% of Fortune 500 companies. Overview An architecture framework is a set of tools which can be used for developing a broad range of different architectures. It should: * describe a method for defining an information system in terms of a set of building bl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Service-Oriented Modeling
Service-oriented modeling is the discipline of modeling business and software systems, for the purpose of designing and specifying service-oriented business systems within a variety of architectural styles and paradigms, such as application architecture, service-oriented architecture, microservices, and cloud computing. Any service-oriented modeling method typically includes a modeling language that can be employed by both the "problem domain organization" (the business), and "solution domain organization" (the information technology department), whose unique perspectives typically influence the service development life-cycle strategy and the projects implemented using that strategy. Service-oriented modeling typically strives to create models that provide a comprehensive view of the analysis, design, and architecture of all software entities in an organization, which can be understood by individuals with diverse levels of business and technical understanding. Service-oriented ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MODAF
The British Ministry of Defence Architecture Framework (MODAF) was an enterprise architecture framework, architecture framework which defined a standardised way of conducting enterprise architecture, originally developed by the British Ministry of Defence, UK Ministry of Defence. It has since been replaced with the NATO Architecture Framework. Initially the purpose of MODAF was to provide rigour and structure to support the definition and integration of MOD equipment capability, particularly in support of network-enabled capability (NEC). The MOD additionally used MODAF to underpin the use of the enterprise architecture approach to the capture of the information about the business to identify the processes and resources required to deliver the vision expressed in the strategy. Overview MODAF was an internationally recognised enterprise architecture framework developed by the Ministry of Defence (United Kingdom), MOD to support Defence planning and change management activitie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Institute For Enterprise Architecture Developments
Jaap Schekkerman (born 1953) is a Dutch computer scientist and founder of the Institute For Enterprise Architecture Developments (IFEAD) in the Netherlands. He is particularly known for his 2003 book ''How to Survive in the Jungle of Enterprise Architecture'' in which he compared 14 Enterprise Architecture Frameworks. Biography Schekkerman received a degree in clinical chemistry from the Bakhuis Roozeboom Instituut in Beverwijk in 1973, and his Engineer's degree in electronic engineering from the HTS Amsterdam in 1979. Further on he received a certificates in information technology from AMBI in 1984, and a certificates in business economics from the Open University in the Netherlands in 1988.Jaap Schekkerman biography at ''enterprise-architecture.info''. Accessed 7 July 2013 Schekkerm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |