|
Executable UML
Executable UML (xtUML or xUML) is both a software development method and a highly abstract software language. It was described for the first time in 2002 in the book "Executable UML: A Foundation for Model-Driven Architecture". The language "combines a subset of the UML (Unified Modeling Language) graphical notation with executable semantics and timing rules." The Executable UML method is the successor to the Shlaer–Mellor method. Executable UML models "can be run, tested, debugged, and measured for performance.", and can be compiled into a less abstract programming language to target a specific implementation. Executable UML supports model-driven architecture (MDA) through specification of platform-independent models, and the compilation of the platform-independent models into platform-specific models. Overview Executable UML is a higher level of abstraction than third-generation programming languages. This allows developers to develop at the level of abstraction of th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
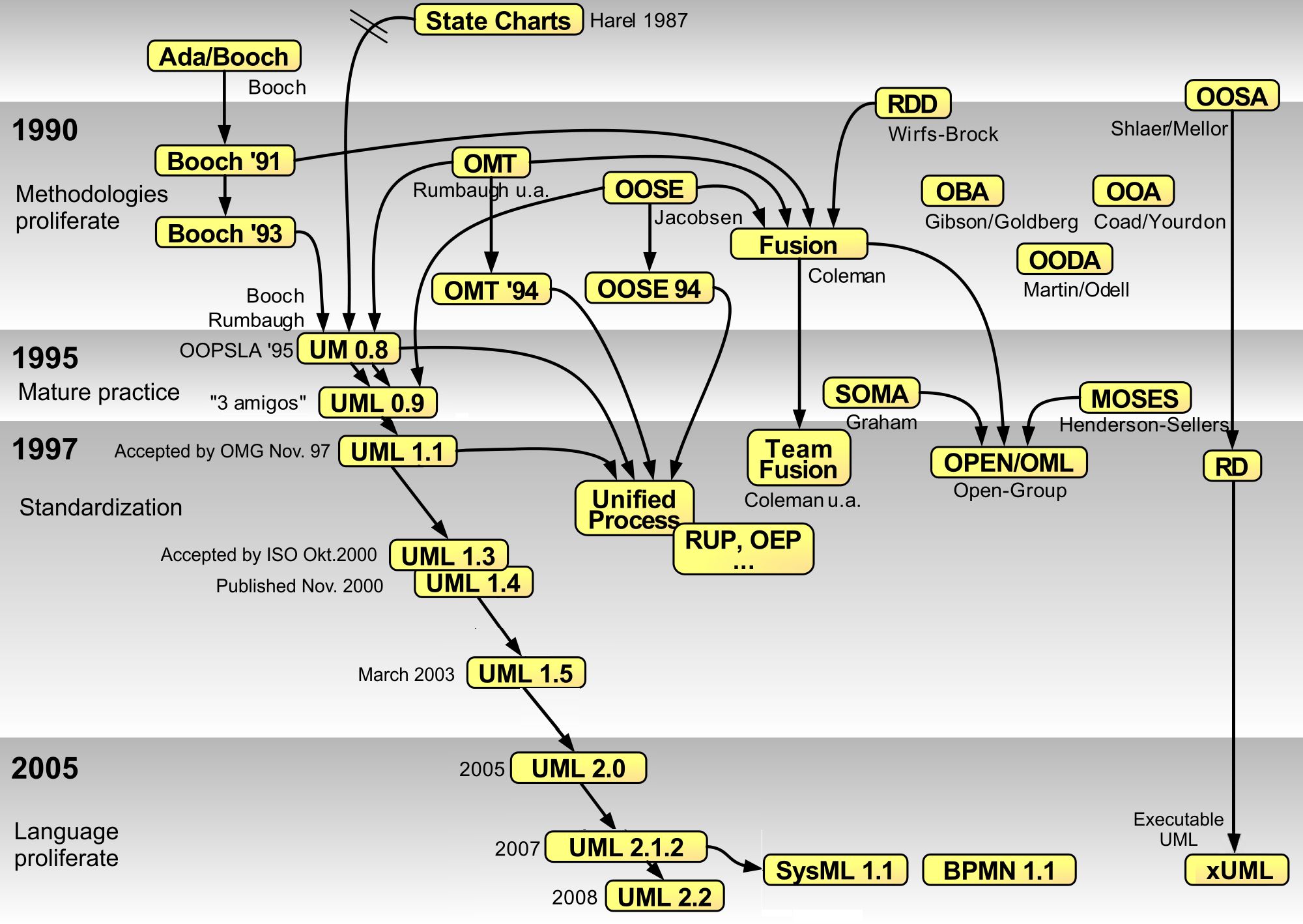
Unified Modeling Language
The Unified Modeling Language (UML) is a general-purpose visual modeling language that is intended to provide a standard way to visualize the design of a system. UML provides a standard notation for many types of diagrams which can be roughly divided into three main groups: behavior diagrams, interaction diagrams, and structure diagrams. The creation of UML was originally motivated by the desire to standardize the disparate notational systems and approaches to software design. It was developed at Rational Software in 1994–1995, with further development led by them through 1996. In 1997, UML was adopted as a standard by the Object Management Group (OMG) and has been managed by this organization ever since. In 2005, UML was also published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) as the ISO/IEC 19501 standard. Since then the standard has been periodically revised to cover the latest revision of UML. In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Action (UML)
In the Unified Modeling Language, an action is a named element that is the fundamental unit of executable functionality. Actions take a set of inputs, which may be empty, and convert them to a set of outputs, which in turn may also be empty. The execution of an action represents some transformation or processing in the modeled system. An action execution represents the run-time behavior of executing an action within a specific behavior execution. All action executions will be executions of specific kinds of actions because action is an abstract class. When the action executes, and what its actual inputs are, is determined by the concrete action and the behaviors in which it is used. An action is the specification of an executable statement and is the fundamental unit of processing or behavior in an activity node that represents some transformation in the modeled system. An action forms an abstraction of a computational procedure which is an atomic execution and therefore comp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Logging
A data logger (also datalogger or data recorder) is an electronic device that records data over time or about location either with a built-in instrument or sensor or via external instruments and sensors. Increasingly, but not entirely, they are based on a digital processor (or computer), and called digital data loggers (DDL). They generally are small, battery-powered, portable, and equipped with a microprocessor, internal memory for data storage, and sensors. Some data loggers interface with a personal computer and use software to activate the data logger and view and analyze the collected data, while others have a local interface device (keypad, LCD) and can be used as a stand-alone device. Data loggers vary from general-purpose devices for various measurement applications to very specific devices for measuring in one environment or application type only. While it is common for general-purpose types to be programmable, many remain static machines with only a limited number o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data (computing)
''In computer science, data (treated as singular, plural, or as a mass noun) is any sequence of one or more symbols; datum is a single symbol of data. Data requires interpretation to become information. Digital data is data that is represented using the binary number system of ones (1) and zeros (0), instead of analog representation. In modern (post-1960) computer systems, all data is digital.'' Data exists in three states: data at rest, data in transit and data in use. Data within a computer, in most cases, moves as parallel data. Data moving to or from a computer, in most cases, moves as serial data. Data sourced from an analog device, such as a temperature sensor, may be converted to digital using an analog-to-digital converter. Data representing quantities, characters, or symbols on which operations are performed by a computer are stored and recorded on magnetic, optical, electronic, or mechanical recording media, and transmitted in the form of digital elec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In Cryptography law, cryptography, encryption (more specifically, Code, encoding) is the process of transforming information in a way that, ideally, only authorized parties can decode. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption Key (cryptography), key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Authentication
Authentication (from ''authentikos'', "real, genuine", from αὐθέντης ''authentes'', "author") is the act of proving an Logical assertion, assertion, such as the Digital identity, identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. Authentication is relevant to multiple fields. In art, antiques, and anthropology, a common problem is verifying that a given artifact was produced by a certain person, or in a certain place (i.e. to assert that it is not counterfeit), or in a given period of history (e.g. by determining the age via carbon dating). In computer science, verifying a user's identity is often required to allow access to confidential data or systems. It might involve validating personal identity documents. In art, antiques and anthropology Authentication can be considered to be of three types: The ''first'' type of authentication is accep ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security (also cybersecurity, digital security, or information technology (IT) security) is a subdiscipline within the field of information security. It consists of the protection of computer software, systems and computer network, networks from Threat (security), threats that can lead to unauthorized information disclosure, theft or damage to computer hardware, hardware, software, or Data (computing), data, as well as from the disruption or misdirection of the Service (economics), services they provide. The significance of the field stems from the expanded reliance on computer systems, the Internet, and wireless network standards. Its importance is further amplified by the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity has emerged as one of the most significant new challenges facing the contemporary world, due to both the complexity of information systems and the societi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Business Logic
In computer software, business logic or domain logic is the part of the program that encodes the real-world business rules that determine how data can be created, stored, and changed. It is contrasted with the remainder of the software that might be concerned with lower-level details of managing a database or displaying the user interface, system infrastructure, or generally connecting various parts of the program. Details and example Business logic: * Prescribes how business objects interact with one another * Enforces the routes and the methods by which business objects are accessed and updated Business rules: * Model real-life business objects (such as accounts, loans, itineraries, and inventories) Business logic comprises: * Workflows that are the ordered tasks of passing documents or data from one participant (a person or a software system) to another. Business logic should be distinguished from business rules. Business logic is the portion of an enterprise system which ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Concern (computer Science)
In computer science, a concern is a particular set of information that has an effect on the code of a computer program. A concern can be as general as the details of database interaction or as specific as performing a primitive calculation, depending on the level of conversation between developers and the program being discussed. IBM uses the term ''concern space'' to describe the sectioning of conceptual information. Overview Usually the code can be separated into logical sections, each addressing separate concerns, and so it hides the need for a given section to know particular information addressed by a different section. This leads to a modular program. Edsger W. Dijkstra coined the term "separation of concerns" to describe the mentality behind this modularization, which allows the programmer to reduce the complexity of the system being designed. Two different concerns that intermingle in the same section of code are called " highly coupled". Sometimes the chosen module divis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Finite-state Machine
A finite-state machine (FSM) or finite-state automaton (FSA, plural: ''automata''), finite automaton, or simply a state machine, is a mathematical model of computation. It is an abstract machine that can be in exactly one of a finite number of ''State (computer science), states'' at any given time. The FSM can change from one state to another in response to some Input (computer science), inputs; the change from one state to another is called a ''transition''. An FSM is defined by a list of its states, its initial state, and the inputs that trigger each transition. Finite-state machines are of two types—Deterministic finite automaton, deterministic finite-state machines and Nondeterministic finite automaton, non-deterministic finite-state machines. For any non-deterministic finite-state machine, an equivalent deterministic one can be constructed. The behavior of state machines can be observed in many devices in modern society that perform a predetermined sequence of actions d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Association (object-oriented Programming)
In object-oriented programming, association defines a relationship between classes of objects that allows one object instance to cause another to perform an action on its behalf. This relationship is structural, because it specifies that objects of one kind are connected to objects of another and does not represent behaviour. In generic terms, the causation is usually called "sending a message", "invoking a method" or "calling a member function" to the controlled object. Concrete implementation usually requires the requesting object to invoke a ''method'' or ''member function'' using a reference or pointer to the memory location of the controlled object. The objects that are related via the association are considered to act in a role A role (also rôle or social role) is a set of connected behaviors, rights, obligations, beliefs, and norms as conceptualized by people in a social situation. It is an expected or free or continuously changing behavior and may have a given i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Class (computer Programming)
In object-oriented programming, a class defines the shared aspects of objects created from the class. The capabilities of a class differ between programming languages, but generally the shared aspects consist of state ( variables) and behavior ( methods) that are each either associated with a particular object or with all objects of that class. Object state can differ between each instance of the class whereas the class state is shared by all of them. The object methods include access to the object state (via an implicit or explicit parameter that references the object) whereas class methods do not. If the language supports inheritance, a class can be defined based on another class with all of its state and behavior plus additional state and behavior that further specializes the class. The specialized class is a ''sub-class'', and the class it is based on is its ''superclass''. Attributes Object lifecycle As an instance of a class, an object is constructed from a class via '' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |