|
Event Correlation
Event correlation is a technique for making sense of a large number of events and pinpointing the few events that are really important in that mass of information. This is accomplished by looking for and analyzing relationships between events. History Event correlation has been used in various fields for many years: * since the 1970s, telecommunications and industrial process control; * since the 1980s, network management and systems management; * since the 1990s, IT service management, publish-subscribe systems (pub/sub), Complex Event Processing (CEP) and Security Information and Event Management (SIEM); * since the early 2000s, Distributed Event-Based Systems and Business Activity Monitoring (BAM). Examples and application domains Integrated management is traditionally subdivided into various fields: * layer by layer: network management, system management, service management, etc. * by management function: performance management, security management, etc. Event correlation ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telecommunications
Telecommunication is the transmission of information by various types of technologies over wire, radio, optical, or other electromagnetic systems. It has its origin in the desire of humans for communication over a distance greater than that feasible with the human voice, but with a similar scale of expediency; thus, slow systems (such as postal mail) are excluded from the field. The transmission media in telecommunication have evolved through numerous stages of technology, from beacons and other visual signals (such as smoke signals, semaphore telegraphs, signal flags, and optical heliographs), to electrical cable and electromagnetic radiation, including light. Such transmission paths are often divided into communication channels, which afford the advantages of multiplexing multiple concurrent communication sessions. ''Telecommunication'' is often used in its plural form. Other examples of pre-modern long-distance communication included audio messages, such as coded drumb ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intrusion Detection System
An intrusion detection system (IDS; also intrusion prevention system or IPS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms. IDS types range in scope from single computers to large networks. The most common classifications are network intrusion detection systems (NIDS) and host-based intrusion detection systems (HIDS). A system that monitors important operating system files is an example of an HIDS, while a system that analyzes incoming network traffic is an example of an NIDS. It is also possible to classify IDS by detection approach. The most well-known variants are signature-based detection (recogni ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Event Condition Action
Event condition action (ECA) is a short-cut for referring to the structure of active rules in event driven architecture and active database systems. Such a rule traditionally consisted of three parts: *The ''event'' part specifies the signal that triggers the invocation of the rule *The ''condition'' part is a logical test that, if satisfied or evaluates to true, causes the action to be carried out *The ''action'' part consists of updates or invocations on the local data This structure was used by the early research in active databases which started to use the term ECA. Current state of the art ECA rule engines use many variations on rule structure. Also other features not considered by the early research is introduced, such as strategies for event selection into the event part. In a memory-based rule engine, the condition could be some tests on local data and actions could be updates to object attributes. In a database system, the condition could simply be a query to the database, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Complex Event Processing
Event processing is a method of tracking and analyzing (processing) streams of information (data) about things that happen (events), and deriving a conclusion from them. Complex event processing, or CEP, consists of a set of concepts and techniques developed in the early 1990s for processing real-time events and extracting information from event streams as they arrive. The goal of complex event processing is to identify meaningful events (such as opportunities or threats) in real-time situations and respond to them as quickly as possible. These events may be happening across the various layers of an organization as sales leads, orders or customer service calls. Or, they may be news items, text messages, social media posts, stock market feeds, traffic reports, weather reports, or other kinds of data. An event may also be defined as a "change of state," when a measurement exceeds a predefined threshold of time, temperature, or other value. Analysts have suggested that CEP will give ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Causal Reasoning
Causal reasoning is the process of identifying causality: the relationship between a cause and its Result, effect. The study of causality extends from ancient philosophy to contemporary neuropsychology; assumptions about the nature of causality may be shown to be functions of a previous event preceding a later one. The first known Protoscience, protoscientific study of cause and effect occurred in Physics (Aristotle), Aristotle's ''Physics''. Causal inference is an example of causal reasoning. Understanding cause and effect Causal relationships may be understood as a transfer of force. If A causes B, then A must transmit a force (or causal power) to B which results in the effect. Causal relationships suggest change over time; cause and effect are temporally related, and the cause precedes the outcome. Causality may also be inferred in the absence of a force, a less-typical definition. A cause can be removal (or stopping), like removing a support from a structure and causing a c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Business Activity Monitoring
Business activity monitoring (BAM) is software that aids the monitoring of business activities which are implemented in computer systems. The term was originally coined by analysts at Gartner, Inc. and refers to the aggregation, analysis, and presentation of real-time information about activities inside organizations, customers, and partners. A business activity can either be a business process that is orchestrated by a business process management (BPM) software, or that of a series of activities spanning across multiple systems and applications. BAM is intended to provide a summary of business activities to operations managers and upper management. Description Business activity monitoring provides real-time information about the status and results of various operations, processes, and transactions. The main benefits of BAM are to enable an enterprise to make better informed business decisions, quickly address problem areas, and re-position organizations to take full advantage of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ITIL
The Information Technology Infrastructure Library (ITIL) is a set of detailed practices for IT activities such as IT service management (ITSM) and IT asset management (ITAM) that focus on aligning IT services with the needs of business. ITIL describes processes, procedures, tasks, and checklists which are neither organization-specific nor technology-specific, but can be applied by an organization toward strategy, delivering value, and maintaining a minimum level of competency. It allows the organization to establish a baseline from which it can plan, implement, and measure. It is used to demonstrate compliance and to measure improvement. There is no formal independent third party compliance assessment available for ITIL compliance in an organization. Certification in ITIL is only available to individuals. Since 2013, ITIL has been owned by AXELOS, a joint venture between Capita and the UK Cabinet Office. History Responding to growing dependence on IT, the UK Government's Ce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
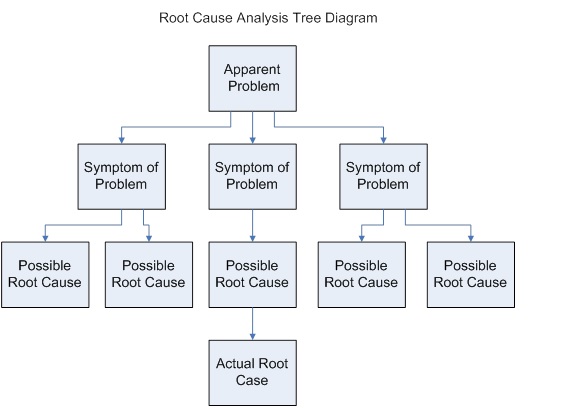
Root Cause Analysis
In science Science is a systematic endeavor that builds and organizes knowledge in the form of testable explanations and predictions about the universe. Science may be as old as the human species, and some of the earliest archeological evidence for ... and engineering, root cause analysis (RCA) is a method of problem solving used for identifying the root causes of faults or problems. It is widely used in IT operations, manufacturing, telecommunications, Process control, industrial process control, accident analysis (e.g., in aviation, rail transport, or nuclear plants), medicine (for medical diagnosis), healthcare industry (e.g., for epidemiology), etc. Root cause analysis is a form of deductive inference since it requires an understanding of the underlying causal mechanisms of the potential root causes and the problem. RCA can be decomposed into four steps: * Identify and describe the problem clearly * Establish a timeline from the normal situation until the problem ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Analytics
Analytics is the systematic computational analysis of data or statistics. It is used for the discovery, interpretation, and communication of meaningful patterns in data. It also entails applying data patterns toward effective decision-making. It can be valuable in areas rich with recorded information; analytics relies on the simultaneous application of statistics, computer programming, and operations research to quantify performance. Organizations may apply analytics to business data to describe, predict, and improve business performance. Specifically, areas within analytics include descriptive analytics, diagnostic analytics, predictive analytics, prescriptive analytics, and cognitive analytics. Analytics may apply to a variety of fields such as marketing, management, finance, online systems, information security, and software services. Since analytics can require extensive computation (see big data), the algorithms and software used for analytics harness the most current methods ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Service Desk (ITSM)
Information technology service management (ITSM) is the activities that are performed by an organization to design, build, deliver, operate and control information technology (IT) services offered to customers. Differing from more technology-oriented IT management approaches like network management and IT systems management, IT service management is characterized by adopting a process approach towards management, focusing on customer needs and IT services for customers rather than IT systems, and stressing continual improvement. The CIO WaterCoolers' annual ITSM report states that business uses ITSM "mostly in support of customer experience (35%) and service quality (48%)." Context As a discipline, ITSM has ties and common interests with other IT and general management approaches, information security management and software engineering. Consequently, IT service management frameworks have been influenced by other standards and adopted concepts from them, e.g. CMMI, ISO 9000 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trouble Ticket System
An issue tracking system (also ITS, trouble ticket system, support ticket, request management or incident ticket system) is a computer software package that manages and maintains lists of issues. Issue tracking systems are generally used in collaborative settings, especially in large or distributed collaborations, but can also be employed by individuals as part of a time management or personal productivity regimen. These systems often encompass resource allocation, time accounting, priority management, and oversight workflow in addition to implementing a centralized issue registry. Background In the institutional setting, issue tracking systems are commonly used in an organization's customer support call center to create, update, and resolve reported customer issues, or even issues reported by that organization's other employees. A support ticket should include vital information for the account involved and the issue encountered. An issue tracking system often also contains ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IT Infrastructure
Information technology infrastructure is defined broadly as a set of information technology (IT) components that are the foundation of an IT service; typically physical components (computer and networking hardware and facilities), but also various software and network components. According to the ITIL Foundation Course Glossary, IT Infrastructure can also be termed as “All of the hardware, software, networks, facilities, etc., that are required to develop, test, deliver, monitor, control or support IT services. The term IT infrastructure includes all of the Information Technology but not the associated People, Processes and documentation.” Overview In IT Infrastructure, the above technological components contribute to and drive business functions. Leaders and managers within the IT field are responsible for ensuring that both the physical hardware and software networks and resources are working optimally. IT infrastructure can be looked at as the foundation of an organizatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |