|
Event Correlation
Event correlation is a technique for making sense of a large number of events and pinpointing the few events that are really important in that mass of information. This is accomplished by looking for and analyzing relationships between events. History Event correlation has been used in various fields for many years: * since the 1970s, telecommunications and Industrial process, industrial process control; * since the 1980s, network management and systems management; * since the 1990s, IT service management, Publish–subscribe pattern, publish-subscribe systems (pub/sub), Complex Event Processing (CEP) and Security Information and Event Management (SIEM); * since the early 2000s, Distributed Event-Based Systems and Business Activity Monitoring (BAM). Examples and application domains Integrated management is traditionally subdivided into various fields: * layer by layer: network management, system management, Service Level Management, service management, etc. * by management functio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telecommunications
Telecommunication, often used in its plural form or abbreviated as telecom, is the transmission of information over a distance using electronic means, typically through cables, radio waves, or other communication technologies. These means of transmission may be divided into communication channels for multiplexing, allowing for a single medium to transmit several concurrent Session (computer science), communication sessions. Long-distance technologies invented during the 20th and 21st centuries generally use electric power, and include the electrical telegraph, telegraph, telephone, television, and radio. Early telecommunication networks used metal wires as the medium for transmitting signals. These networks were used for telegraphy and telephony for many decades. In the first decade of the 20th century, a revolution in wireless communication began with breakthroughs including those made in radio communications by Guglielmo Marconi, who won the 1909 Nobel Prize in Physics. Othe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intrusion Detection System
An intrusion detection system (IDS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically either reported to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources and uses alarm filtering techniques to distinguish malicious activity from false alarms. IDS types range in scope from single computers to large networks. The most common classifications are network intrusion detection systems (NIDS) and host-based intrusion detection systems (HIDS). A system that monitors important operating system files is an example of an HIDS, while a system that analyzes incoming network traffic is an example of an NIDS. It is also possible to classify IDS by detection approach. The most well-known variants are signature-based detection (recognizing bad patterns, such as exploitatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Event Condition Action
Event condition action (ECA) is a short-cut for referring to the structure of active rules in event-driven architecture and active database systems. Such a rule traditionally consisted of three parts: *The ''event'' part specifies the signal that triggers the invocation of the rule *The ''condition'' part is a logical test that, if satisfied or evaluates to true, causes the action to be carried out *The ''action'' part consists of updates or invocations on the local data This structure was used by the early research in active databases which started to use the term ECA. Current state of the art ECA rule engines use many variations on rule structure. Also other features not considered by the early research is introduced, such as strategies for event selection into the event part. In a memory-based rule engine, the condition could be some tests on local data and actions could be updates to object attributes. In a database system, the condition could simply be a query to the database ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Complex Event Processing
Event processing is a method of tracking and analyzing (processing) streams of information (data) about things that happen (events), and deriving a conclusion from them. Complex event processing (CEP) consists of a set of concepts and techniques developed in the early 1990s for processing real-time events and extracting information from event streams as they arrive. The goal of complex event processing is to identify meaningful events (such as opportunities or threats) in real-time situations and respond to them as quickly as possible. These events may be happening across the various layers of an organization as sales leads, orders or customer service calls. Or, they may be news items, text messages, social media posts, business processes (such as supply chain), traffic reports, weather reports, or other kinds of data. An event may also be defined as a "change of state," when a measurement exceeds a predefined threshold of time, temperature, or other value. Analysts have suggest ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Causal Reasoning
Causality is an influence by which one event, process, state, or object (''a'' ''cause'') contributes to the production of another event, process, state, or object (an ''effect'') where the cause is at least partly responsible for the effect, and the effect is at least partly dependent on the cause. The cause of something may also be described as the reason for the event or process. In general, a process can have multiple causes,Compare: which are also said to be ''causal factors'' for it, and all lie in its past. An effect can in turn be a cause of, or causal factor for, many other effects, which all lie in its future. Some writers have held that causality is metaphysically prior to notions of time and space. Causality is an abstraction that indicates how the world progresses. As such it is a basic concept; it is more apt to be an explanation of other concepts of progression than something to be explained by other more fundamental concepts. The concept is like those of ag ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Business Activity Monitoring
Business activity monitoring (BAM) is a category of software intended for use in monitoring and tracking business activities. BAM is a term introduced by Gartner, Inc., referring to the collection, analysis, and presentation of real-time information about activities within organizations, including those involving customers and partners. BAM tracks individual business processes and sequences of activities across multiple systems and applications and provides information about them in real time. Description BAM software is used to monitor the status and outcomes of operations, processes, and transactions. BAM systems typically display data on computer dashboards, but they differ from business intelligence (BI) dashboards. In BAM systems, events are processed in real time or near real time and displayed immediately, whereas BI dashboards typically update at scheduled intervals by querying databases. Related fields * Business service management * Business intelligence * Business ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ITIL
ITIL (previously and also known as Information Technology Infrastructure Library) is a framework with a set of practices (previously processes) for IT activities such as IT service management (ITSM) and IT asset management (ITAM) that focus on aligning IT services with the needs of the business. ITIL describes best practices, including processes, procedures, tasks, and checklists which are neither organization-specific nor technology-specific. It is designed to allow organizations to establish a baseline and can be used to demonstrate compliance and to measure improvements. There is no formal independent third-party compliance assessment available to demonstrate ITIL compliance in an organization. Certification in ITIL is only available to individuals and not organizations. Since 2021, the ITIL trademark has been owned by PeopleCert. History Responding to growing dependence on IT, the UK Government's Central Computer and Telecommunications Agency (CCTA) in the 1980s develo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
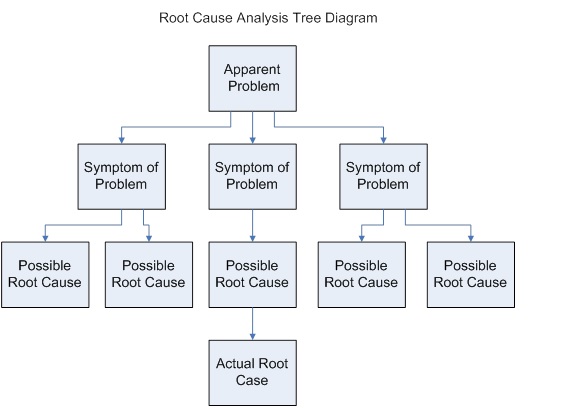
Root Cause Analysis
In science and engineering, root cause analysis (RCA) is a method of problem solving used for identifying the root causes of faults or problems. It is widely used in IT operations, manufacturing, telecommunications, industrial process control, accident analysis (e.g., in aviation, rail transport, or nuclear plants), medical diagnosis, the healthcare industry (e.g., for epidemiology), etc. Root cause analysis is a form of inductive inference (first create a theory, or ''root'', based on empirical evidence, or ''causes'') and deductive inference (test the theory, i.e., the underlying causal mechanisms, with empirical data). RCA can be decomposed into four steps: # Identify and describe the problem clearly # Establish a timeline from the normal situation until the problem occurrence # Distinguish between the root cause and other causal factors (e.g., via event correlation) # Establish a causal graph between the root cause and the problem. RCA generally serves as input to a r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Analytics
Analytics is the systematic computational analysis of data or statistics. It is used for the discovery, interpretation, and communication of meaningful patterns in data, which also falls under and directly relates to the umbrella term, data science. Analytics also entails applying data patterns toward effective decision-making. It can be valuable in areas rich with recorded information; analytics relies on the simultaneous application of statistics, computer programming, and operations research to quantify performance. Organizations may apply analytics to business data to describe, predict, and improve business performance. Specifically, areas within analytics include descriptive analytics, diagnostic analytics, predictive analytics, prescriptive analytics, and cognitive analytics. Analytics may apply to a variety of fields such as marketing, management, finance, online systems, information security, and software services. Since analytics can require extensive computation (s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Service Desk (ITSM)
Information technology service management (ITSM) are the activities performed by an organization to design, build, deliver, operate and control IT services offered to customers. Differing from more technology-oriented IT management approaches like network management and IT systems management, IT service management is characterized by adopting a process approach towards management, focusing on customer needs and IT services for customers rather than IT systems, and stressing continual improvement. The CIO WaterCooler's 2017 ITSM report states that business uses ITSM "mostly in support of customer experience (35%) and service quality (48%)." Process Execution of ITSM processes in an organization, especially those processes that are more workflow-driven, can benefit significantly from being supported with specialized software tools. Service desk A service desk is a primary IT function within the discipline of IT service management (ITSM) as defined by ITIL. It is intend ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Trouble Ticket System
An issue tracking system (also ITS, trouble ticket system, support ticket, request management or incident ticket system) is a computer software package that manages and maintains lists of issues. Issue tracking systems are generally used in collaborative settings, especially in large or distributed collaborations, but can also be employed by individuals as part of a time management or personal productivity regimen. These systems often encompass resource allocation, time accounting, priority management, and oversight workflow in addition to implementing a centralized issue registry. Background In the institutional setting, issue tracking systems are commonly used in an organization's customer support call center to create, update, and resolve reported customer issues, or even issues reported by that organization's other employees. A support ticket should include vital information for the account involved and the issue encountered. An issue tracking system often also contains a kn ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IT Infrastructure
Information technology infrastructure is defined broadly as a set of information technology (IT) components that are the foundation of an IT service; typically physical components (Computer hardware, computer and networking hardware and facilities), but also various software and Computer network, network components. According to the ITIL Foundation Course Glossary, IT Infrastructure can also be termed as “All of the hardware, software, networks, facilities, etc., that are required to develop, test, deliver, monitor, control or support IT services. The term IT infrastructure includes all of the Information Technology but not the associated People, Processes and documentation.” Overview In IT Infrastructure, the above technological components contribute to and drive business functions. Leaders and managers within the IT field are responsible for ensuring that both the physical hardware and software networks and resources are working optimally. IT infrastructure can be looked at ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |