|
European Association For Biometrics
The European Association for Biometrics (EAB) is a non-profit organization in the field of biometrics with its headquarters in Bussum (Netherlands). The Association promotes the development of biometrics and its use in Europe, in general in accordance with the law, with the principles of ethics, stimulating the development of technology, increasing security and business. Aims The purpose of the activity is to promote the development of proper and meaningful use of biometrics from the point of view of interest of the inhabitants of European, industrial, academic, organizational and educational backgrounds. History The association was founded on November 17, 2011 in Darmstadt at the Fraunhofer Institute for Computer Graphics Research. It was developed as part of the Biometric European Stakeholders Network (BEST Network) project, funded by the European Commission under the 7th Framework Program for the Scientific Conference. The EAB Statute was based on the CAST, e.V. There were ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bussum
Bussum () is a commuter town and former municipality in the Gooi region in the south east of the province of North Holland in the Netherlands near Hilversum. Since 2016, Bussum has been part of the new municipality of Gooise Meren. Bussum had a population of 33,595 in 2019 and covered an area of . History For a long time Bussum was not more than a hamlet situated amongst the heathlands of the Gooi and was first mentioned in 1306. In this time, Bussum was a large heathland with many small farms, sheep pens and forests as is shown on old maps. Since Bussum is situated near the fortified town Naarden it was governed by Naarden from 1369 onward. In 1470 Bussum was inhabited by about 250 people, which made it the smallest village in the Gooi. Bussum became independent from Naarden in 1817, yet it was not until the arrival of a railway line in 1874 that Bussum began to flourish. Two train stations were built in the town, that still exist today: Naarden-Bussum and Bussum Zuid (Dutch l ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
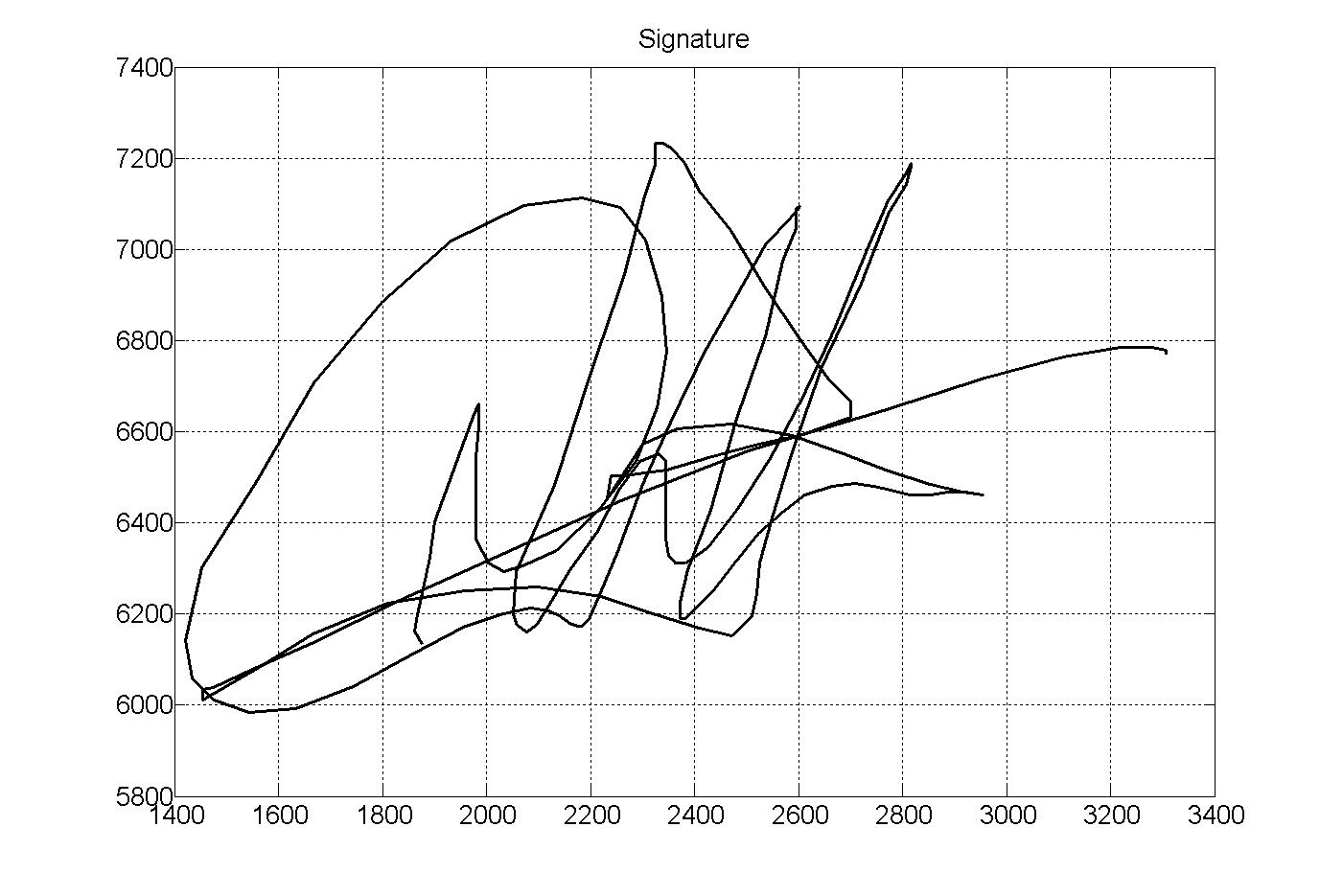
Handwritten Biometric Recognition
Handwritten biometric recognition is the process of identifying the author of a given text from the handwriting style. Handwritten biometric recognition belongs to behavioural biometric systems because it is based on something that the user has learned to do. Static and dynamic recognition Handwritten biometrics can be split into two main categories: Static: In this mode, users writes on paper, digitize it through an optical scanner or a camera, and the biometric system recognizes the text analyzing its shape. This group is also known as "off-line". Dynamic: In this mode, users writes in a digitizing tablet, which acquires the text in real time. Another possibility is the acquisition by means of stylus-operated PDAs. Dynamic recognition is also known as "on-line".Dynamic information usually consists of the following information: * spatial coordinate x(t) * spatial coordinate y(t) * pressure p(t) * azimuth az(t) * inclination in(t) Better accuracies are achieved by means of d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Surveillance
Surveillance is the monitoring of behavior, many activities, or information for the purpose of information gathering, influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information like Internet traffic. It can also include simple technical methods, such as Human intelligence (intelligence gathering), human intelligence gathering and postal interception. Surveillance is used by citizens for protecting their neighborhoods. And by governments for intelligence gathering - including espionage, prevention of crime, the protection of a process, person, group or object, or the investigation of crime. It is also used by criminal organizations to plan and commit crimes, and by businesses to Industrial espionage, gather intelligence on criminals, their competitors, suppliers or customers. Religious organisations charged with detecting he ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Information Technology Organizations Based In Europe
Information is an abstract concept that refers to that which has the power to inform. At the most fundamental level information pertains to the interpretation of that which may be sensed. Any natural process that is not completely random, and any observable pattern in any medium can be said to convey some amount of information. Whereas digital signals and other data use discrete signs to convey information, other phenomena and artifacts such as analog signals, poems, pictures, music or other sounds, and currents convey information in a more continuous form. Information is not knowledge itself, but the meaning that may be derived from a representation through interpretation. Information is often processed iteratively: Data available at one step are processed into information to be interpreted and processed at the next step. For example, in written text each symbol or letter conveys information relevant to the word it is part of, each word conveys information relevant ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Voice Analysis
Voice analysis is the study of speech sounds for purposes other than linguistic content, such as in speech recognition. Such studies include mostly medical analysis of the voice ( phoniatrics), but also speaker identification. More controversially, some believe that the truthfulness or emotional state of speakers can be determined using voice stress analysis or layered voice analysis. Analysis methods Voice problems that require voice analysis most commonly originate from the vocal folds or the laryngeal musculature that controls them, since the folds are subject to collision forces with each vibratory cycle and to drying from the air being forced through the small gap between them, and the laryngeal musculature is intensely active during speech or singing and is subject to tiring. However, dynamic analysis of the vocal folds and their movement is physically difficult. The location of the vocal folds effectively prohibits direct, invasive measurement of movement. Less invasive i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Vein Matching
Vein matching, also called vascular technology, is a technique of biometric identification through the analysis of the patterns of blood vessels visible from the surface of the skin. Though used by the Federal Bureau of Investigation and the Central Intelligence Agency, this method of identification is still in development and has not yet been universally adopted by crime labs as it is not considered as reliable as more established techniques, such as fingerprinting. However, it can be used in conjunction with existing forensic data in support of a conclusion. While other types of biometric scanners are more widely employed in security systems, vascular scanners are growing in popularity. Fingerprint scanners are more frequently used, but they generally do not provide enough data points for critical verification decisions. Since fingerprint scanners require direct contact of the finger with the scanner, dry or abraded skin can interfere with the reliability of the system. Skin d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Speaker Recognition
Speaker recognition is the identification of a person from characteristics of voices. It is used to answer the question "Who is speaking?" The term voice recognition can refer to ''speaker recognition'' or speech recognition. Speaker verification (also called speaker authentication) contrasts with identification, and ''speaker recognition'' differs from '' speaker diarisation'' (recognizing when the same speaker is speaking). Recognizing the speaker can simplify the task of translating speech in systems that have been trained on specific voices or it can be used to authenticate or verify the identity of a speaker as part of a security process. Speaker recognition has a history dating back some four decades as of 2019 and uses the acoustic features of speech that have been found to differ between individuals. These acoustic patterns reflect both anatomy and learned behavioral patterns. Verification versus identification There are two major applications of speaker recognition techn ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Smart City
A smart city is a technologically modern urban area that uses different types of electronic methods and sensors to collect specific data. Information gained from that data is used to manage assets, resources and services efficiently; in return, that data is used to improve operations across the city. This includes data collected from citizens, devices, buildings and assets that is processed and analyzed to monitor and manage traffic and transportation systems, power plants, utilities, water supply networks, waste, Criminal investigations, information systems, schools, libraries, hospitals, and other community services. Smart cities are defined as smart both in the ways in which their governments harness technology as well as in how they monitor, analyze, plan, and govern the city. In smart cities, the sharing of data is not limited to the city itself but also includes businesses, citizens and other third parties that can benefit from various uses of that data. Sharing data from ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Signature Recognition
Signature recognition is an example of behavioral biometrics that identifies a person based on their handwriting. It can be operated in two different ways: Static: In this mode, users write their signature on paper, and after the writing is complete, it is digitized through an optical scanner or a camera to turn the signature image into bits. The biometric system then recognizes the signature analyzing its shape. This group is also known as "off-line". Dynamic: In this mode, users write their signature in a digitizing tablet, which acquires the signature in real time. Another possibility is the acquisition by means of stylus-operated PDAs. Some systems also operate on smart-phones or tablets with a capacitive screen, where users can sign using a finger or an appropriate pen. Dynamic recognition is also known as "on-line". Dynamic information usually consists of the following information: * spatial coordinate x(t) * spatial coordinate y(t) * pressure p(t) * azimuth az(t) * inclinat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Retinal Scan
A retinal scan is a biometric technique that uses unique patterns on a person's retina blood vessels. It is not to be confused with other ocular-based technologies: iris recognition, commonly called an "iris scan", and eye vein verification that uses scleral veins. Introduction The human retina is a thin tissue made up of neural cells that is located in the posterior portion of the eye. Because of the complex structure of the capillaries that supply the retina with blood, each person's retina is unique, making retinal scans an emerging authentication method. The network of blood vessels in the retina is not entirely genetically determined and thus even identical twins do not share a similar pattern. Although retinal patterns may be altered in cases of diabetes, glaucoma or retinal degenerative disorders, the retina typically remains unchanged from birth until death. Due to its unique and unchanging nature, the retina appears to be the most precise and reliable biometric, aside ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Private Biometrics
Private biometrics is a form of encrypted biometrics, also called privacy-preserving biometric authentication methods, in which the biometric payload is a one-way, homomorphically encrypted feature vector that is 0.05% the size of the original biometric template and can be searched with full accuracy, speed and privacy. The feature vector's homomorphic encryption allows search and match to be conducted in polynomial time on an encrypted dataset and the search result is returned as an encrypted match. One or more computing devices may use an encrypted feature vector to verify an individual person (1:1 verify) or identify an individual in a datastore (1:many identify) without storing, sending or receiving plaintext biometric data within or between computing devices or any other entity. The purpose of private biometrics is to allow a person to be identified or authenticated while guaranteeing individual privacy and fundamental human rights by only operating on biometric data in t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multiple Biometric Grand Challenge
300px Multiple Biometric Grand Challenge (MBGC) is a biometric project. Its primary goal is to improve performance of face and iris recognition technology on both still and video imagery with a series of challenge problems and evaluation. Background Over the last decade, numerous government and industry organizations have moved or are moving toward deploying automated biometric technologies to provide increased security for their systems and facilities. Six U.S. Government organizations recently sponsored the Face Recognition Grand Challenge (FRGC), Face Recognition Vendor Test (FRVT) 2006 and the Iris Challenge Evaluation (ICE) 2006. Results from the FRGC and FRVT 2006 documented two orders of magnitude improvement in the performance of face recognition under full-frontal, controlled conditions over the last 14 years. For the first time, ICE 2006 provided an independent assessment of multiple iris recognition algorithms on the same data set. However, further advances in these te ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |