|
DirectAccess
DirectAccess, also known as Unified Remote Access, is a VPN technology that provides intranet connectivity to client computers when they are connected to the Internet. Unlike many traditional VPN connections, which must be initiated and terminated by explicit user action, DirectAccess connections are designed to connect automatically as soon as the computer connects to the Internet. DirectAccess was introduced in Windows Server 2008 R2, providing this service to Windows 7 and Windows 8 "Enterprise" edition clients. In 2010, Microsoft Forefront Unified Access Gateway (UAG) was released, which simplifies the deployment of DirectAccess for Windows 2008 R2, and includes additional components that make it easier to integrate without the need to deploy IPv6 on the network, and with a dedicated user interface for the configuration and monitoring. Some requirements and limitations that were part of the design of DirectAccess with Windows Server 2008 R2 and UAG have been changed (see require ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Microsoft Forefront Unified Access Gateway
Microsoft Forefront Unified Access Gateway (UAG) is a discontinued software suite that provides secure remote access to corporate networks for remote employees and business partners. Its services include reverse proxy, virtual private network (VPN), DirectAccess and Remote Desktop Services. UAG was released in 2010, and is the successor for Microsoft Intelligent Application Gateway (IAG) which was released in 2007. UAG is part of the Microsoft Forefront offering. Microsoft discontinued the product in 2014, although the Web Application Proxy feature of Windows Server 2012 R2 and later offers some of its functionalities. History Unified Access Gateway was originally developed by a startup company named ''Whale Communications'' in Rosh HaAyin, Israel. Whale's initial product, e-Gap, was designed to create physical separation between networks of disparate trust levels. It consisted of an appliance housing a 512k memory chip that toggled connections between two servers via a SCSI ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IP-HTTPS
IP over HTTPS ("IP-HTTPS", "MS-IPHTTPS") is a Microsoft network tunneling protocol. The IP-HTTPS protocol transports IPv6 packets across non-IPv6 networks. It does a similar job as the earlier 6to4 or Teredo tunneling mechanisms. Microsoft preference when deciding between transition protocols Microsoft used to discourage IP-HTTPS use because it was slow. For Windows Server 2012 Windows Server 2012, codenamed "Windows Server 8", is the sixth version of the Windows Server operating system by Microsoft, as part of the Windows NT family of operating systems. It is the server version of Windows based on Windows 8 and succ ..., Microsoft changed the internal workings of the protocol, and IP-HTTPS is now the "preferred IPv6 transition technology" for their "DirectAccess" VPN technology. References External links ">S-IPHTTPS">Official Microsoft open standards document [MS-IPHTTPS/nowiki> {{compu-network-stub Network protocols IPv6 transition technologies ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Teredo Tunneling
In computer networking, Teredo is a transition technology that gives full IPv6 connectivity for IPv6-capable hosts that are on the IPv4 Internet but have no native connection to an IPv6 network. Unlike similar protocols such as 6to4, it can perform its function even from behind network address translation (NAT) devices such as home routers. Teredo operates using a platform independent tunneling protocol that provides IPv6 (Internet Protocol version 6) connectivity by encapsulating IPv6 datagram packets within IPv4 User Datagram Protocol (UDP) packets. Teredo routes these datagrams on the IPv4 Internet and through NAT devices. Teredo nodes elsewhere on the IPv6 network (called Teredo relays) receive the packets, un-encapsulate them, and pass them on. Teredo is a temporary measure. In the long term, all IPv6 hosts should use native IPv6 connectivity. Teredo should be disabled when native IPv6 connectivity becomes available. Christian Huitema developed Teredo at Microsoft, and t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows Server 2008 R2
Windows Server 2008 R2 is the fifth version of the Windows Server operating system produced by Microsoft and released as part of the Windows NT family of operating systems. It was released to manufacturing on July 22, 2009, and became generally available on October 22, 2009, shortly after the completion of Windows 7. It is the successor to Windows Server 2008, which is derived from the Windows Vista codebase, released the previous year, and was succeeded by the Windows 8-based Windows Server 2012. Enhancements in Windows Server 2008 R2 include new functionality for Active Directory, new virtualization and management features, version 7.5 of the Internet Information Services web server and support for up to 256 logical processors. It is built on the same kernel used with the client-oriented Windows 7, and is the first server operating system released by Microsoft to exclusively support 64-bit processors, a move which was followed by the consumer-oriented Windows 11 in 2021. Windo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Windows 7
Windows 7 is a major release of the Windows NT operating system developed by Microsoft. It was released to manufacturing on July 22, 2009, and became generally available on October 22, 2009. It is the successor to Windows Vista, released nearly three years earlier. It remained an operating system for use on personal computers, including home and business desktops, laptops, tablet PCs and media center PCs, and itself was replaced in November 2012 by Windows 8, the name spanning more than three years of the product. Until April 9, 2013, Windows 7 original release included updates and technical support, after which installation of Service Pack 1 was required for users to receive support and updates. Windows 7's server counterpart, Windows Server 2008 R2, was released at the same time. The last supported version of Windows based on this operating system was released on July 1, 2011, entitled Windows Embedded POSReady 7. Extended support ended on January 14, 2020, over ten ye ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
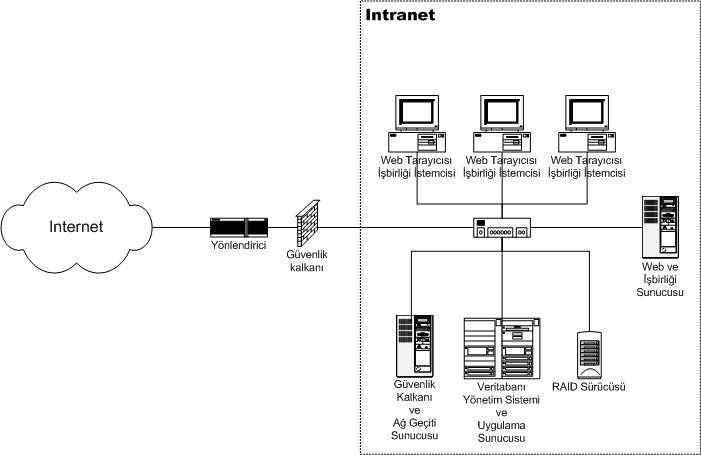
Intranet
An intranet is a computer network for sharing information, easier communication, collaboration tools, operational systems, and other computing services within an organization, usually to the exclusion of access by outsiders. The term is used in contrast to public networks, such as the Internet, but uses the same technology based on the Internet protocol suite. An organization-wide intranet can constitute an important focal point of internal communication and collaboration, and provide a single starting point to access internal and external resources. In its simplest form, an intranet is established with the technologies for local area networks (LANs) and wide area networks (WANs). Many modern intranets have Web search engine, search engines, user profiles, blogs, mobile apps with notifications, and events planning within their infrastructure. An intranet is sometimes contrasted to an extranet. While an intranet is generally restricted to employees of the organization, extranets m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Protocols
A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any kind of variation of a physical quantity. The protocol defines the rules, syntax, semantics and synchronization of communication and possible error recovery methods. Protocols may be implemented by hardware, software, or a combination of both. Communicating systems use well-defined formats for exchanging various messages. Each message has an exact meaning intended to elicit a response from a range of possible responses pre-determined for that particular situation. The specified behavior is typically independent of how it is to be implemented. Communication protocols have to be agreed upon by the parties involved. To reach an agreement, a protocol may be developed into a technical standard. A programming language describes the same for computations, so there is a close analogy between protocols and programming languages: ''protocols are to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Access Protection
Network Access Protection (NAP) is a Microsoft technology for controlling network access of a computer, based on its health. With NAP, system administrators of an organization can define policies for system health requirements. Examples of system health requirements are whether the computer has the most recent operating system updates installed, whether the computer has the latest version of the anti-virus software signature, or whether the computer has a host-based firewall installed and enabled. Computers with a NAP client will have their health status evaluated upon establishing a network connection. NAP can restrict or deny network access to the computers that are not in compliance with the defined health requirements. NAP was deprecated in Windows Server 2012 R2 and removed from Windows Server 2016. Overview Network Access Protection Client Agent makes it possible for clients that support NAP to evaluate software updates for their statement of health. NAP clients are comp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Public Key Infrastructure
A public key infrastructure (PKI) is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email. It is required for activities where simple passwords are an inadequate authentication method and more rigorous proof is required to confirm the identity of the parties involved in the communication and to validate the information being transferred. In cryptography, a PKI is an arrangement that ''binds'' public keys with respective identities of entities (like people and organizations). The binding is established through a process of registration and issuance of certificates at and by a certificate authority (CA). Depending on the assurance level of the binding, this may be carried out by an aut ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain Name System
The Domain Name System (DNS) is a hierarchical and distributed naming system for computers, services, and other resources in the Internet or other Internet Protocol (IP) networks. It associates various information with domain names assigned to each of the associated entities. Most prominently, it translates readily memorized domain names to the numerical IP addresses needed for locating and identifying computer services and devices with the underlying network protocols. The Domain Name System has been an essential component of the functionality of the Internet since 1985. The Domain Name System delegates the responsibility of assigning domain names and mapping those names to Internet resources by designating authoritative name servers for each domain. Network administrators may delegate authority over sub-domains of their allocated name space to other name servers. This mechanism provides distributed and fault-tolerant service and was designed to avoid a single large ce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Domain Controller
A domain controller (DC) is a server computer that responds to security authentication requests within a computer network domain. It is a network server that is responsible for allowing host access to domain resources. It authenticates users, stores user account information and enforces security policy for a domain. It is most commonly implemented in Microsoft Windows environments (see Domain controller (Windows)), where it is the centerpiece of the Windows Active Directory service. However, non-Windows domain controllers can be established via identity management software such as Samba and Red Hat FreeIPA. Software The software and operating system used to run a domain controller usually consists of several key components shared across platforms. This includes the operating system (usually Windows Server or Linux), an LDAP service (Red Hat Directory Server, etc.), a network time service ( ntpd, chrony, etc.), and a computer network authentication protocol (usually Ker ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NAT64
NAT64 is an IPv6 transition mechanism that facilitates communication between IPv6 and IPv4 hosts by using a form of network address translation (NAT). The NAT64 gateway is a translator between IPv4 and IPv6 protocols, for which function it needs at least one IPv4 address and an IPv6 network segment comprising a 32-bit address space. The "well-known prefix" reserved for this service is . An IPv6 client embeds the IPv4 address it wishes to communicate with using the host part of the IPv6 network segment, resulting in an ''IPv4-embedded IPv6 addresses'' (hence the 32-bit address space in the IPv6 network segment), and sends packets to the resulting address. The NAT64 gateway creates a mapping between the IPv6 and the IPv4 addresses, which may be manually configured or determined automatically. Principle of operation A simple NAT64 installation may consist of a gateway with two interfaces connected to an IPv4 network and an IPv6 network, respectively. Traffic from the IPv6 networ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |