|
Data Management
Data management comprises all disciplines related to handling data as a valuable resource. Concept The concept of data management arose in the 1980s as technology moved from sequential processing (first punched cards, then magnetic tape) to random access storage. Since it was now possible to store a discrete fact and quickly access it using random access disk technology, those suggesting that data management was more important than business process management used arguments such as "a customer's home address is stored in 75 (or some other large number) places in our computer systems." However, during this period, random access processing was not competitively fast, so those suggesting "process management" was more important than "data management" used batch processing time as their primary argument. As application software evolved into real-time, interactive usage, it became obvious that both management processes were important. If the data was not well defined, the data wou ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
List Of Academic Disciplines
An academic discipline or field of study is a branch of knowledge, taught and researched as part of higher education. A scholar's discipline is commonly defined by the university faculties and learned societies to which they belong and the academic journals in which they publish research. Disciplines vary between well-established ones that exist in almost all universities and have well-defined rosters of journals and conferences, and nascent ones supported by only a few universities and publications. A discipline may have branches, and these are often called sub-disciplines. The following outline is provided as an overview of and topical guide to academic disciplines. In each case an entry at the highest level of the hierarchy (e.g., Humanities) is a group of broadly similar disciplines; an entry at the next highest level (e.g., Music) is a discipline having some degree of autonomy and being the basic identity felt by its scholars; and lower levels of the hierarchy are sub-d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Database Administration
Database administration is the function of managing and maintaining database management systems (DBMS) software. Mainstream DBMS software such as Oracle, IBM Db2 and Microsoft SQL Server need ongoing management. As such, corporations that use DBMS software often hire specialized information technology personnel called database administrators or DBAs. Responsibilities * Installation, configuration and upgrading of Database server software and related products. * Evaluate Database features and Database related products. * Establish and maintain sound backup and recovery policies and procedures. * Take care of the Database design and implementation. * Implement and maintain database security (create and maintain users and roles, assign privileges). * Database tuning and performance monitoring. * Application tuning and performance monitoring. * Setup and maintain documentation and standards. * Plan growth and changes (capacity planning). * Work as part of a team and provi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
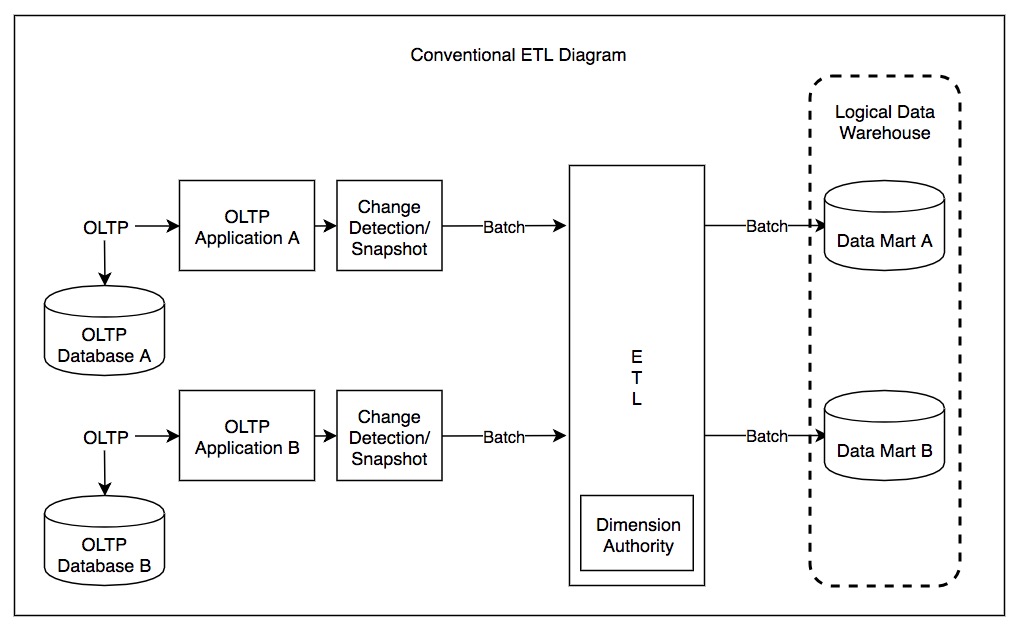
Extract, Transform, Load
In computing, extract, transform, load (ETL) is a three-phase process where data is extracted, transformed (cleaned, sanitized, scrubbed) and loaded into an output data container. The data can be collated from one or more sources and it can also be outputted to one or more destinations. ETL processing is typically executed using software applications but it can also be done manually by system operators. ETL software typically automates the entire process and can be run manually or on reoccurring schedules either as single jobs or aggregated into a batch of jobs. A properly designed ETL system extracts data from source systems and enforces data type and data validity standards and ensures it conforms structurally to the requirements of the output. Some ETL systems can also deliver data in a presentation-ready format so that application developers can build applications and end users can make decisions. The ETL process became a popular concept in the 1970s and is often used in d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Integration
Data integration involves combining data residing in different sources and providing users with a unified view of them. This process becomes significant in a variety of situations, which include both commercial (such as when two similar companies need to merge their databases) and scientific (combining research results from different bioinformatics repositories, for example) domains. Data integration appears with increasing frequency as the volume (that is, big data) and the need to share existing data explodes. It has become the focus of extensive theoretical work, and numerous open problems remain unsolved. Data integration encourages collaboration between internal as well as external users. The data being integrated must be received from a heterogeneous database system and transformed to a single coherent data store that provides synchronous data across a network of files for clients. A common use of data integration is in data mining when analyzing and extracting informati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Reference Data
Reference data is data used to classify or categorize other data. Typically, they are static or slowly changing over time. Examples of reference data include: * Units of measurement * Country codes * Corporate codes * Fixed conversion rates e.g., weight, temperature, and length * Calendar structure and constraints Reference data sets are sometimes alternatively referred to as a "controlled vocabulary" or "lookup" data. Reference data differs from master data. While both provide context for business transactions, reference data is concerned with classification and categorisation, while master data is concerned with business entities. A further difference between reference data and master data is that a change to the reference data values may require an associated change in business process to support the change, while a change in master data will always be managed as part of existing business processes. For example, adding a new customer or sales product is part of the standard ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Master Data Management
Master data management (MDM) is a technology-enabled discipline in which business and information technology work together to ensure the uniformity, accuracy, stewardship, semantic consistency and accountability of the enterprise's official shared master data assets. Drivers for master data management Organisations, or groups of organisations, may establish the need for master data management when they hold more than one copy of data about a business entity. Holding more than one copy of this master data inherently means that there is an inefficiency in maintaining a "single version of the truth" across all copies. Unless people, processes and technology are in place to ensure that the data values are kept aligned across all copies, it is almost inevitable that different versions of information about a business entity will be held. This causes inefficiencies in operational data use, and hinders the ability of organisations to report and analyze. At a basic level, master data ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Integration
Data integration involves combining data residing in different sources and providing users with a unified view of them. This process becomes significant in a variety of situations, which include both commercial (such as when two similar companies need to merge their databases) and scientific (combining research results from different bioinformatics repositories, for example) domains. Data integration appears with increasing frequency as the volume (that is, big data) and the need to share existing data explodes. It has become the focus of extensive theoretical work, and numerous open problems remain unsolved. Data integration encourages collaboration between internal as well as external users. The data being integrated must be received from a heterogeneous database system and transformed to a single coherent data store that provides synchronous data across a network of files for clients. A common use of data integration is in data mining when analyzing and extracting informati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Privacy
Information privacy is the relationship between the collection and dissemination of data, technology, the public expectation of privacy, contextual information norms, and the legal and political issues surrounding them. It is also known as data privacy or data protection. Data privacy is challenging since attempts to use data while protecting an individual's privacy preferences and personally identifiable information. The fields of computer security, data security, and information security all design and use software, hardware, and human resources to address this issue. Authorities Laws Authorities by country Information types Various types of personal information often come under privacy concerns. Cable television This describes the ability to control what information one reveals about oneself over cable television, and who can access that information. For example, third parties can track IP TV programs someone has watched at any given time. "The addition of any informati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Erasure
Data erasure (sometimes referred to as data clearing, data wiping, or data destruction) is a software-based method of overwriting the data that aims to completely destroy all electronic data residing on a hard disk drive or other digital media by using zeros and ones to overwrite data onto all sectors of the device in an irreversible process. By overwriting the data on the storage device, the data is rendered irrecoverable and achieves data sanitization. Ideally, software designed for data erasure should: #Allow for selection of a specific standard, based on unique needs, and #Verify the overwriting method has been successful and removed data across the entire device. Permanent data erasure goes beyond basic file deletion commands, which only remove direct pointers to the data disk sectors and make the data recovery possible with common software tools. Unlike degaussing and physical destruction, which render the storage media unusable, data erasure removes all information wh ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Access
Data access is a generic term referring to a process which has both an IT-specific meaning and other connotations involving access rights in a broader legal and/or political sense. In the former it typically refers to software and activities related to storing, retrieving, or acting on data housed in a database or other repository. Details Two fundamental types of data access exist: # sequential access (as in magnetic tape, for example) # random access (as in indexed media) Data access crucially involves authorization to access different data repositories. Data access can help distinguish the abilities of administrators and users. For example, administrators may have the ability to remove, edit and add data, while general users may not even have "read" rights if they lack access to particular information. Historically, each repository (including each different database, file system, etc.), might require the use of different methods and languages, and many of these repositorie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Security
Data security means protecting digital data, such as those in a database, from destructive forces and from the unwanted actions of unauthorized users, such as a cyberattack or a data breach. Technologies Disk encryption Disk encryption refers to encryption technology that encrypts data on a hard disk drive. Disk encryption typically takes form in either software (see disk encryption software) or hardware (see disk encryption hardware). Disk encryption is often referred to as on-the-fly encryption (OTFE) or transparent encryption. Software versus hardware-based mechanisms for protecting data Software-based security solutions encrypt the data to protect it from theft. However, a malicious program or a hacker could corrupt the data to make it unrecoverable, making the system unusable. Hardware-based security solutions prevent read and write access to data, which provides very strong protection against tampering and unauthorized access. Hardware-based security or assiste ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Subsetting
In research communities (for example, earth sciences, astronomy, business, and government), subsetting is the process of retrieving just the parts (a subset) of large files which are of interest for a specific purpose. This occurs usually in a client—server setting, where the extraction of the parts of interest occurs on the server before the data is sent to the client over a network. The main purpose of subsetting is to save bandwidth on the network and storage space on the client computer. Subsetting may be favorable for the following reasons: * restrict or divide the time range * select cross sections of data * select particular kinds of time series In mathematics, a time series is a series of data points indexed (or listed or graphed) in time order. Most commonly, a time series is a sequence taken at successive equally spaced points in time. Thus it is a sequence of discrete-time data. Exa ... * exclude particular observations Subsetting within programs You can subset wi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)