|
Data Embassies
A data embassy is a solution traditionally implemented by nation states to ensure a country's digital continuity with particular respect to critical databases. It consists of a set of servers that store one country's data and are under that country's jurisdiction while being located in another country. Purpose Data embassies are regarded as a tool to ensure a government's digital continuity, meaning the survival of critical databases to allow the continuation of government even in a situation where governing from within the country's borders is no longer an option. Among threats that might lead to such situation are natural disasters, large-scale cyberattacks, and military invasion. In the worst-case scenario, a data embassy could enable government to provide its digital services without the national territory under its control. This makes data embassies particularly attractive to countries that have already digitalized their most crucial databases and are situated in the vici ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Continuity Of Government
Continuity of government (COG) is the principle of establishing defined procedures that allow a government to continue its essential operations in case of a catastrophic event such as nuclear war. COG was developed by the British government before and during World War II to counter threats, such as that of the ''Luftwaffe'' bombing during the Battle of Britain. The need for continuity of government plans gained new urgency with nuclear proliferation. During and after the Cold War countries developed such plans to avoid (or minimize) confusion and disorder due to a power vacuum in the aftermath of a nuclear attack. In the US, COG is no longer limited to nuclear emergencies; the Continuity of Operations Plan was activated following the September 11 attacks. By country Canada Canada built numerous nuclear bunkers across the country, nicknamed " Diefenbunkers" in a play on the last name of then-Prime Minister John Diefenbaker. In 2016, the Privy Council Office made an agreement ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Database
In computing, a database is an organized collection of data stored and accessed electronically. Small databases can be stored on a file system, while large databases are hosted on computer clusters or cloud storage. The design of databases spans formal techniques and practical considerations, including data modeling, efficient data representation and storage, query languages, security and privacy of sensitive data, and distributed computing issues, including supporting concurrent access and fault tolerance. A database management system (DBMS) is the software that interacts with end users, applications, and the database itself to capture and analyze the data. The DBMS software additionally encompasses the core facilities provided to administer the database. The sum total of the database, the DBMS and the associated applications can be referred to as a database system. Often the term "database" is also used loosely to refer to any of the DBMS, the database system or an appli ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Server (computing)
In computing, a server is a piece of computer hardware or software (computer program) that provides functionality for other programs or devices, called " clients". This architecture is called the client–server model. Servers can provide various functionalities, often called "services", such as sharing data or resources among multiple clients, or performing computation for a client. A single server can serve multiple clients, and a single client can use multiple servers. A client process may run on the same device or may connect over a network to a server on a different device. Typical servers are database servers, file servers, mail servers, print servers, web servers, game servers, and application servers. Client–server systems are usually most frequently implemented by (and often identified with) the request–response model: a client sends a request to the server, which performs some action and sends a response back to the client, typically with a result or acknowledg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
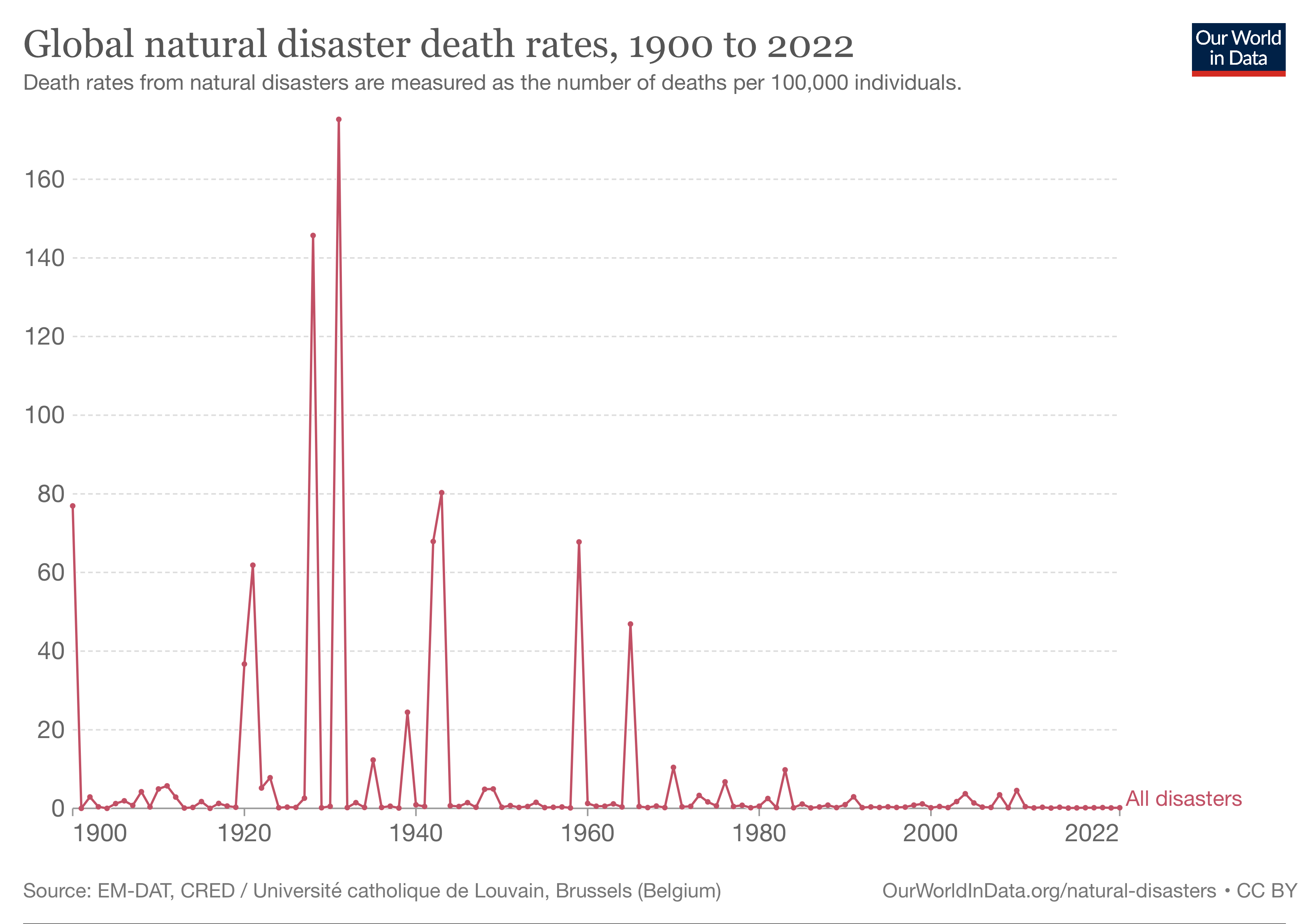
Natural Disaster
A natural disaster is "the negative impact following an actual occurrence of natural hazard in the event that it significantly harms a community". A natural disaster can cause loss of life or damage property, and typically leaves some economic damage in its wake. The severity of the damage depends on the affected population's resilience and on the infrastructure available. Examples of natural hazards include: avalanche, coastal flooding, cold wave, drought, earthquake, hail, heat wave, hurricane (tropical cyclone), ice storm, landslide, lightning, riverine flooding, strong wind, tornado, typhoon, tsunami, volcanic activity, wildfire, winter weather. In modern times, the divide between natural, man-made and man-accelerated disasters is quite difficult to draw. Human choices and activities like architecture, fire, resource management or even climate change potentially play a role in causing "natural disasters". In fact, the term "natural disaster" has been called a misnom ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyberattack
A cyberattack is any offensive maneuver that targets computer information systems, computer networks, infrastructures, or personal computer devices. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorization, potentially with malicious intent. Depending on the context, cyberattacks can be part of cyber warfare or cyberterrorism. A cyberattack can be employed by sovereign states, individuals, groups, societies or organisations and it may originate from an anonymous source. A product that facilitates a cyberattack is sometimes called a cyber weapon. Cyber attacks have increased with an alarming rate for the last few years A cyberattack may steal, alter, or destroy a specified target by hacking into a susceptible system. Cyberattacks can range from installing spyware on a personal computer to attempting to destroy the infrastructure of entire nations. Legal experts are seeking to limit the use of the ter ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Military Invasion
An invasion is a military offensive in which large numbers of combatants of one geopolitical entity aggressively enter territory owned by another such entity, generally with the objective of either: conquering; liberating or re-establishing control or authority over a territory; forcing the partition of a country; altering the established government or gaining concessions from said government; or a combination thereof. An invasion can be the cause of a war, be a part of a larger strategy to end a war, or it can constitute an entire war in itself. Due to the large scale of the operations associated with invasions, they are usually strategic in planning and execution. History Archaeological evidence indicates that invasions have been frequent occurrences since prehistory. In antiquity, before radio communications and fast transportation, the only way for a military to ensure adequate reinforcements was to move armies as one massive force. This, by its very nature, led to the st ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computing Power
In computing, computer performance is the amount of useful work accomplished by a computer system. Outside of specific contexts, computer performance is estimated in terms of accuracy, efficiency and speed of executing computer program instructions. When it comes to high computer performance, one or more of the following factors might be involved: * Short response time for a given piece of work. * High throughput (rate of processing work). * Low utilization of computing resource(s). ** Fast (or highly compact) data compression and decompression. * High availability of the computing system or application. * High bandwidth. * Short data transmission time. Technical and non-technical definitions The performance of any computer system can be evaluated in measurable, technical terms, using one or more of the metrics listed above. This way the performance can be * Compared relative to other systems or the same system before/after changes * In absolute terms, e.g. for fulfilling a cont ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Taavi Kotka
Taavi Kotka (born 21 January 1979) is an IT visionary and previously the chief information officer of the Estonian Government known for leading E-residency of Estonia, e-residency program. Between years 2005-2012, Kotka was the CEO of Nortal (then named Webmedia), one of the largest software development companies in the Baltic states. Taavi Kotka (alongside Ruth Annus, and Siim Sikkut) proposed "10 million e-residents by 2025" on idea contest by Estonian Development Fund in 2014. In April 2015, the Vice President of European Commission, Andrus Ansip, assigned Taavi Kotka to be his Special Adviser on Digital Single Market issues and e-Governance. In 2021, together with Ivo Mägi and Antti Perli, he founded the start-up company KOOS.io. In April 2022, 4 million euros were involved. The new investment round was led by the fund Taavet + Sten, among the investors were Markus Villig, Kaarel Kotkas, Triin Hertmann, Jevgeni Kabanov, etc. In addition to the Estonian funds Superangels, Un ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Jüri Ratas
Jüri Ratas (; born 2 July 1978) is an Estonian politician who was the 18th prime minister of Estonia from 2016 to 2021. He has been Leader of the Centre Party since 2016, and was the mayor of Tallinn from 2005 to 2007. Jüri Ratas' first cabinet was in office from 23 November 2016 to 29 April 2019. It formed when Social Democrats and the Union of Pro Patria and Res Publica joined the opposition's no-confidence vote against the previous cabinet and switched the liberal centre-right Reform Party with the Estonian Centre Party. Jüri Ratas' second cabinet was active from April 2019 to January 2021. It has been notable for its share of public scandals, resignations of ministers and the number of public apologies from Ratas, mostly connected to the activities of the nationalist and right-wing populist EKRE party, a coalition member. His tenure has also seen the national budget of Estonia moving to deficit after years of being in surplus. According to a national poll conducted i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Xavier Bettel
Xavier Bettel (; born 3 March 1973) is a Luxembourger lawyer and politician serving as Prime Minister of Luxembourg since 2013. He was previously a member of the Chamber of Deputies (1999–2013) and Mayor of Luxembourg City (2011–2013). Bettel is a member of the Democratic Party (DP). Following the 2013 general election, he took office as Prime Minister and succeeded Jean-Claude Juncker of the Christian Social People's Party (CSV). Bettel became the first openly gay prime minister in the world to be reelected for a second term in 2018, when his mandate was renewed. Early life Bettel was born on 3 March 1973 in Luxembourg City. His father, Claude Bettel, was a wine merchant. Bettel said he has an Orthodox Russian grandfather and a Polish-Jewish grandfather, while his parents were Catholics. His mother Aniela is a grandniece of the Russian composer Sergei Rachmaninoff. After completing his secondary school studies at Lycée Hélène Boucher in Thionville, Bettel obtained a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bahrain
Bahrain ( ; ; ar, البحرين, al-Bahrayn, locally ), officially the Kingdom of Bahrain, ' is an island country in Western Asia. It is situated on the Persian Gulf, and comprises a small archipelago made up of 50 natural islands and an additional 33 artificial islands, centered on Bahrain Island which makes up around 83 percent of the country's landmass. Bahrain is situated between Qatar and the northeastern coast of Saudi Arabia, to which it is connected by the King Fahd Causeway. According to the 2020 census, the country's population numbers 1,501,635, of which 712,362 are Bahraini nationals. Bahrain spans some , and is the third-smallest nation in Asia after the Maldives and Singapore. The capital and largest city is Manama. Bahrain is the site of the ancient Dilmun civilization.Oman: The Lost Land [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Vienna Convention On Consular Relations
en, Viennese , iso_code = AT-9 , registration_plate = W , postal_code_type = Postal code , postal_code = , timezone = CET , utc_offset = +1 , timezone_DST = CEST , utc_offset_DST = +2 , blank_name = Vehicle registration , blank_info = W , blank1_name = GDP , blank1_info = € 96.5 billion (2020) , blank2_name = GDP per capita , blank2_info = € 50,400 (2020) , blank_name_sec1 = HDI (2019) , blank_info_sec1 = 0.947 · 1st of 9 , blank3_name = Seats in the Federal Council , blank3_info = , blank_name_sec2 = GeoTLD , blank_info_sec2 = .wien , website = , footnotes = , image_blank_emblem = Wien logo.svg , blank_emblem_size = Vienna ( ; german: Wien ; bar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |




.jpg)
.jpg)
.png)