|
Contributory Liability
Contributory copyright infringement is a way of imposing secondary liability for infringement of a copyright. It is a means by which a person may be held liable for copyright infringement even though he or she did not directly engage in the infringing activity. In the United States, the Copyright Act does not itself impose liability for contributory infringement expressly. It is one of the two forms of secondary liability apart from vicarious liability. Contributory infringement is understood to be a form of infringement in which a person is not directly violating a copyright but, induces or authorises another person to directly infringe the copyright. This doctrine is a development of general tort law and is an extension of the principle in tort law that in addition to the tortfeasor, anyone who contributed to the tort should also be held liable. Requirements The requirements for fulfilling the threshold of contributory infringement and imposing liability for copyright infringem ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secondary Liability
Secondary liability, or indirect infringement, arises when a party materially contributes to, facilitates, induces, or is otherwise responsible for directly infringing acts carried out by another party. The US has statutorily codified secondary liability rules for trademarks and patents, but for matters relating to copyright, this has solely been a product of case law developments. In other words, courts, rather than Congress, have been the primary developers of theories and policies concerning secondary liability. Early case law Secondary liability in copyright has come about with case-by-case decisions. In other words, there has not been any real or consolidated theory. Furthermore, patent and copyright cases have tended to cross-cite each other. Examples of this are cases such as ''Kalem Co. v. Harper Brothers''''Kalem Co. v. Harper Brothers''222 U.S. 55(1911). (the producer of the movie Ben Hur (1907 film) didn't himself infringe, but was responsible for making and commercially ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Betamax Case
''Sony Corp. of America v. Universal City Studios, Inc.'', 464 U.S. 417 (1984), also known as the “Betamax case”, is a decision by the Supreme Court of the United States which ruled that the making of individual copies of complete television shows for purposes of time shifting does not constitute copyright infringement, but is fair use.. The Court also ruled that the manufacturers of home video recording devices, such as Betamax or other VCRs (referred to as VTRs in the case), cannot be liable for contributory infringement. The case was a boon to the home video market, as it created a legal safe haven for the technology. The broader legal consequence of the Supreme Court's decision was its establishment of a general test for determining whether a device with copying or recording capabilities ran afoul of copyright law. This test has created some interpretative challenges to courts in applying the case to more recent file sharing technologies available for use on home computer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Willful Blindness
Willful blindness is a term used in law to describe a situation in which a person seeks to avoid civil or criminal liability for a wrongful act by intentionally keeping themselves unaware of facts that would render them liable or implicated. In ''United States v. Jewell'', the court held that proof of willful ignorance satisfied the requirement of knowledge as to criminal possession and importation of drugs.''Criminal Law – Cases and Materials'', 7th ed. 2012, Wolters Kluwer Law & Business; John Kaplan, Robert Weisberg, Guyora Binder, /ref> Although the term was originally—and still is—used in legal contexts, the phrase "willful ignorance" has come to mean any situation in which people intentionally turn their attention away from an ethical problem that is believed to be important by those using the phrase (for instance, because the problem is too disturbing for people to want it dominating their thoughts, or from the knowledge that solving the problem would require exten ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Preliminary Injunction
An injunction is a legal and equitable remedy in the form of a special court order that compels a party to do or refrain from specific acts. ("The court of appeals ... has exclusive jurisdiction to enjoin, set aside, suspend (in whole or in part), or to determine the validity of...."); ("Limit on injunctive relief'); ''Jennings v. Rodriguez'', 583 U.S. ___, ___138 S.Ct. 830 851 (2018); '' Wheaton College v. Burwell''134 S.Ct. 2806 2810-11 (2014) ("Under our precedents, an injunction is appropriate only if (1) it is necessary or appropriate in aid of our jurisdiction, and (2) the legal rights at issue are indisputably clear.") (internal quotation marks and brackets omitted); '' Lux v. Rodrigues''561 U.S. 1306 1308 (2010); ''Correctional Services Corp. v. Malesko''534 U.S. 61 74 (2001) (stating that "injunctive relief has long been recognized as the proper means for preventing entities from acting unconstitutionally."); '' Nken v. Holder''556 U.S. 418(2009); see also ''Alli v. Dec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in military ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
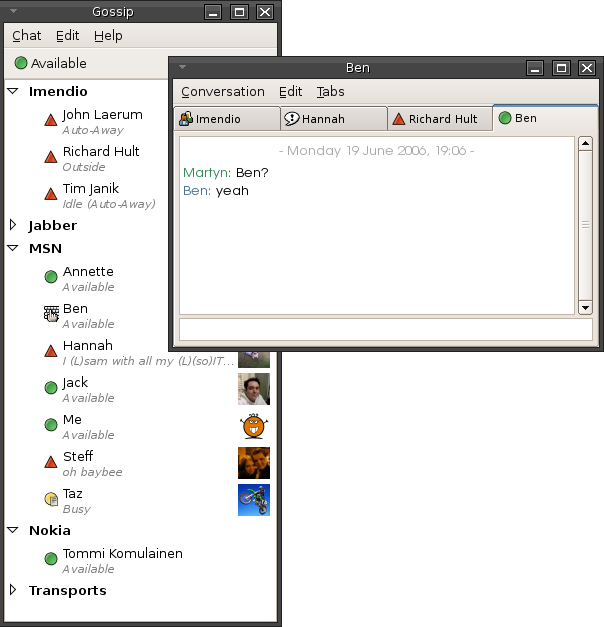
Instant Messaging
Instant messaging (IM) technology is a type of online chat allowing real-time text transmission over the Internet or another computer network. Messages are typically transmitted between two or more parties, when each user inputs text and triggers a transmission to the recipient(s), who are all connected on a common network. It differs from email in that conversations over instant messaging happen in real-time (hence "instant"). Most modern IM application (computing), applications (sometimes called "social messengers", "messaging apps" or "chat apps") use push technology and also add other features such as emojis (or graphical smileys), file transfer, chatbots, voice over IP, or Videotelephony, video chat capabilities. Instant messaging systems tend to facilitate connections between specified known users (often using a contact list also known as a "buddy list" or "friend list"), and can be standalone applications or integrated into e.g. a wider social media platform, or a website ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
In Re Aimster Copyright Litigation
''In re Aimster Copyright Litigation'', 334 F.3d 643 ( 7th Cir. 2003), was a case in which the United States Court of Appeals for the Seventh Circuit addressed copyright infringement claims brought against Aimster, concluding that a preliminary injunction against the file-sharing service was appropriate because the copyright owners were likely to prevail on their claims of contributory infringement, and that the services could have non-infringing users was insufficient reason to reverse the district court's decision. The appellate court also noted that the defendant could have limited the quantity of the infringements if it had eliminated an encryption system feature, and if it had monitored the use of its systems. This made it so that the defense did not fall within the safe harbor of 17 U.S.C. § 512(i). and could not be used as an excuse to not know about the infringement. In addition, the court decided that the harm done to the plaintiff was irreparable and outweighed any harm ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Music Sharing
File sharing is the practice of distributing or providing access to digital media, such as computer programs, multimedia (audio, images and video), documents or electronic books. Common methods of storage, transmission and dispersion include removable media, centralized servers on computer networks, Internet-based hyperlinked documents, and the use of distributed peer-to-peer networking. File sharing technologies, such as BitTorrent, are integral to modern media piracy, as well as the sharing of scientific data and other free content. History Files were first exchanged on removable media. Computers were able to access remote files using filesystem mounting, bulletin board systems (1978), Usenet (1979), and FTP servers (1970's). Internet Relay Chat (1988) and Hotline (1997) enabled users to communicate remotely through chat and to exchange files. The mp3 encoding, which was standardized in 1991 and substantially reduced the size of audio files, grew to widespread use in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Morpheus (software)
Morpheus was a file sharing and searching peer-to-peer client for Microsoft Windows, developed and distributed by the company StreamCast, that originally used the OpenNap protocol, but later supported many different peer-to-peer protocols. On April 22, 2008, distributor StreamCast Networks filed for Chapter 7 bankruptcy after a long legal battle with music companies; all of their employees were laid off and the official download at www.morpheus.com stopped being available, though for a small period the website remained online. As of October 29, 2008, the official Morpheus website is offline, including all other websites owned by StreamCast Networks, specifically MusicCity.com, Streamcastnetworks.com and NeoNetwork.com. Availability Users of the Morpheus community have set up a website (at GnutellaForums.com) where the Morpheus software can still be downloaded. At that site, there is a support forum and support chat room setup from the site and within the client. Presence of ad ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Grokster
Grokster Ltd. was a privately owned software company based in Nevis, West Indies that created the Grokster peer-to-peer file-sharing client in 2001 that used the FastTrack protocol. Grokster Ltd. was rendered extinct in late 2005 by the United States Supreme Court's decision in '' MGM Studios, Inc. v. Grokster, Ltd.'' The court ruled against Grokster's peer-to-peer file sharing program for computers running the Microsoft Windows operating system, effectively forcing the company to cease operations. The product was similar in look and feel to Kazaa, marketed by Sharman Networks, and Morpheus, which was distributed by StreamCast. Grokster, along with Morpheus and Kazaa, are considered second-generation peer-to-peer file sharing programs. Unlike their predecessor Napster, these file sharing programs allowed users to trade files directly between one another, without these transactions passing through a centralized server. Because Napster maintained this fraction of control over t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Aimster
Madster (initially called Aimster) was a peer-to-peer file sharing service. It was released in Napster's wake in August 2000 shut down in December 2002 as a result of a lawsuit by the Recording Industry Association of America. Origin According to John Deep, a professor at Rensselaer Polytechnic Institute, the Madster software was originally inspired by his daughter's use of instant messaging software. His idea was to combine instant messaging with file sharing. John Deep's daughter Aimee had an interest in providing privacy to her online friends; instant messaging was lacking when it came to privacy protection. Features The Madster service was initially called Aimster, but it was later renamed to Madster due to concerns that the Aimster name infringed AOL's AIM (AOL Instant Messenger) trademark. The Madster software allowed users to share files via instant messaging services. In particular, users could share files specifically with users who were included on a " buddy list" with ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Napster
Napster was a peer-to-peer file sharing application. It originally launched on June 1, 1999, with an emphasis on digital audio file distribution. Audio songs shared on the service were typically encoded in the MP3 format. It was founded by Shawn Fanning, Sean Parker, and Hugo Sáez Contreras. As the software became popular, the company ran into legal difficulties over copyright infringement. It ceased operations in 2001 after losing a wave of lawsuits and filed for bankruptcy in June 2002. Later, more decentralized projects followed Napster's P2P file-sharing example, such as Gnutella, Freenet, FastTrack, and Soulseek. Some services and software, like AudioGalaxy, LimeWire, Scour, Kazaa / Grokster, Madster, and eDonkey2000, were also brought down or changed due to copyright issues. Napster's assets were eventually acquired by Roxio, and it re-emerged as an online music store. Best Buy later purchased the service and merged it with its Rhapsody service on December 1, 2011, r ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |