|
CRYPTO1
Crypto1 is a proprietary encryption algorithm ( stream cipher) and authentication protocol created by NXP Semiconductors for its MIFARE Classic RFID contactless smart cards launched in 1994. Such cards have been used in many notable systems, including Oyster card, CharlieCard and OV-chipkaart. By 2009, cryptographic research had reverse engineered the cipher and a variety of attacks were published that effectively broke the security. NXP responded by issueing "hardened" (but still backwards compatible) cards, the MIFARE Classic EV1. However, in 2015 a new attack rendered the cards insecure, and NXP now recommends migrating away from MIFARE Classic. Technical description Crypto1 is a stream cipher very similar in its structure to its successor, Hitag2. Crypto1 consists of * a 48-bit linear feedback shift register for the state of the cipher, * a two-layer 20-to-1 nonlinear function used to generate the keystream, and * a 16-bit LFSR which is used during the authentication ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Crypto1
Crypto1 is a proprietary encryption algorithm ( stream cipher) and authentication protocol created by NXP Semiconductors for its MIFARE Classic RFID contactless smart cards launched in 1994. Such cards have been used in many notable systems, including Oyster card, CharlieCard and OV-chipkaart. By 2009, cryptographic research had reverse engineered the cipher and a variety of attacks were published that effectively broke the security. NXP responded by issueing "hardened" (but still backwards compatible) cards, the MIFARE Classic EV1. However, in 2015 a new attack rendered the cards insecure, and NXP now recommends migrating away from MIFARE Classic. Technical description Crypto1 is a stream cipher very similar in its structure to its successor, Hitag2. Crypto1 consists of * a 48-bit linear feedback shift register for the state of the cipher, * a two-layer 20-to-1 nonlinear function used to generate the keystream, and * a 16-bit LFSR which is used during the authentication ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
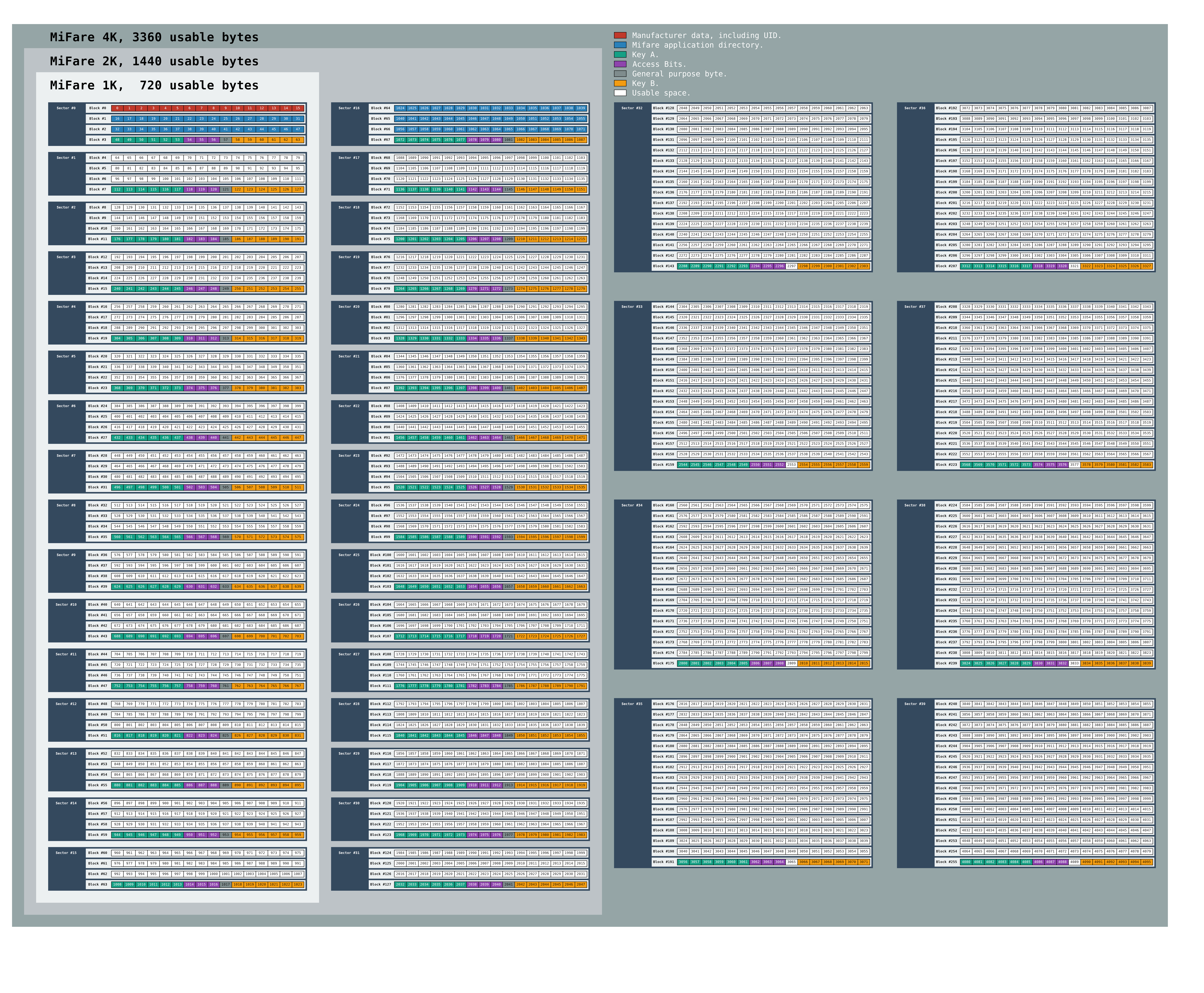
Mifare
MIFARE is the NXP Semiconductors-owned trademark of a series of integrated circuit (IC) chips used in contactless smart cards and proximity cards. The brand name covers proprietary solutions based upon various levels of the ISO/IEC 14443 Type A 13.56 MHz contactless smart card standard. It uses AES and DES/Triple-DES encryption standards, as well as an older proprietary encryption algorithm, Crypto-1. According to NXP, 10 billion of their smart card chips and over 150 million reader modules have been sold. MIFARE is owned by NXP Semiconductors, which was spun off from Philips Electronics in 2006. Variants MIFARE products are embedded in contactless and contact smart cards, smart paper tickets, wearables and phones. The MIFARE brand name (derived from the term MIKRON FARE Collection and created by the company Mikron) covers four families of contactless cards: ; MIFARE Classic: Employs a proprietary protocol compliant to parts 1–3 of ISO/IEC 14443 Type A, with an NXP ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NLFSR
A nonlinear-feedback shift register (NLFSR) is a shift register whose input bit is a non-linear function of its previous state. For an n-bit shift register ''r'' its next state is defined as: r_(b_0, b_1, b_2, \ldots, b_)=r_(b_1, b_2, \ldots, f(b_0, b_1, b_2, \ldots, b_)), where ''f'' is the non-linear feedback function. Applications Nonlinear-feedback shift registers are components in modern stream ciphers, especially in RFID and smartcard applications. NLFSRs are known to be more resistant to cryptanalytic attacks than Linear Feedback Shift Registers (LFSRs). Generating It is known how to generate an ''n''-bit NLFSR of maximal length ''2n'', generating a De Bruijn sequence, by extending a maximal-length LFSR with ''n'' stages; but the construction of other large NLFSRs with guaranteed long periods remains an open problem. Using bruteforce methods, a list of maximum-period ''n''-bit NLFSRs for n ≤ 25 has been made as well as for n=27. New methods suggest usage of evolutionar ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
LFSR
In computing, a linear-feedback shift register (LFSR) is a shift register whose input bit is a linear function of its previous state. The most commonly used linear function of single bits is exclusive-or (XOR). Thus, an LFSR is most often a shift register whose input bit is driven by the XOR of some bits of the overall shift register value. The initial value of the LFSR is called the seed, and because the operation of the register is deterministic, the stream of values produced by the register is completely determined by its current (or previous) state. Likewise, because the register has a finite number of possible states, it must eventually enter a repeating cycle. However, an LFSR with a well-chosen feedback function can produce a sequence of bits that appears random and has a very long cycle. Applications of LFSRs include generating pseudo-random numbers, pseudo-noise sequences, fast digital counters, and whitening sequences. Both hardware and software implementations o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Encryption
In cryptography, encryption is the process of encoding information. This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information. Encryption does not itself prevent interference but denies the intelligible content to a would-be interceptor. For technical reasons, an encryption scheme usually uses a pseudo-random encryption key generated by an algorithm. It is possible to decrypt the message without possessing the key but, for a well-designed encryption scheme, considerable computational resources and skills are required. An authorized recipient can easily decrypt the message with the key provided by the originator to recipients but not to unauthorized users. Historically, various forms of encryption have been used to aid in cryptography. Early encryption techniques were often used in military ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Stream Cipher
stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream). In a stream cipher, each plaintext digit is encrypted one at a time with the corresponding digit of the keystream, to give a digit of the ciphertext stream. Since encryption of each digit is dependent on the current state of the cipher, it is also known as ''state cipher''. In practice, a digit is typically a bit and the combining operation is an exclusive-or (XOR). The pseudorandom keystream is typically generated serially from a random seed value using digital shift registers. The seed value serves as the cryptographic key for decrypting the ciphertext stream. Stream ciphers represent a different approach to symmetric encryption from block ciphers. Block ciphers operate on large blocks of digits with a fixed, unvarying transformation. This distinction is not always clear-cut: in some modes of operation, a block cipher primitive is used in such a w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NXP Semiconductors
NXP Semiconductors N.V. (NXP) is a Dutch semiconductor designer and manufacturer with headquarters in Eindhoven, Netherlands. The company employs approximately 31,000 people in more than 30 countries. NXP reported revenue of $11.06 billion in 2021. Originally spun off from Philips in 2006, NXP completed its initial public offering, on August 6, 2010, with shares trading on NASDAQ under the ticker symbol ''NXPI''. On December 23, 2013, NXP Semiconductors was added to the NASDAQ 100. On March 2, 2015, it was announced that NXP would merge with Freescale Semiconductor. The merger was closed on December 7, 2015. On October 27, 2016, it was announced that Qualcomm would try to buy NXP. Because the Chinese merger authority did not approve the acquisition before the deadline set by Qualcomm, the attempt was effectively cancelled on July 26, 2018. Description NXP provides technology solutions targeting the automotive, industrial & IoT, mobile, and communication infrastructure market ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RFID
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter. When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, back to the reader. This number can be used to track inventory goods. Passive tags are powered by energy from the RFID reader's interrogating radio waves. Active tags are powered by a battery and thus can be read at a greater range from the RFID reader, up to hundreds of meters. Unlike a barcode, the tag does not need to be within the line of sight of the reader, so it may be embedded in the tracked object. RFID is one method of automatic identification and data capture (AIDC). RFID tags are used in many industries. For example, an RFID tag attached to an automobile during production can be used to track ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Contactless Smart Card
A contactless smart card is a contactless credential whose dimensions are credit-card size. Its embedded integrated circuits can store (and sometimes process) data and communicate with a terminal via NFC. Commonplace uses include transit tickets, bank cards and passports. There are two broad categories of contactless smart cards. Memory cards contain non-volatile memory storage components, and perhaps some specific security logic. Contactless smart cards contain read-only RFID called CSN (Card Serial Number) or UID, and a re-writeable smart card microchip that can be transcribed via radio waves. Overview A contactless smart card is characterized as follows: *Dimensions are normally credit card size. The ID-1 of ISO/IEC 7810 standard defines them as 85.60 × 53.98 × 0.76 mm (3.370 × 2.125 × 0.030 in). *Contains a security system with tamper-resistant properties (e.g. a secure cryptoprocessor, secure file system, human-readable features) and is capable of providing sec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Oyster Card
The Oyster card is a payment method for public transport in London (and certain areas around it) in England, United Kingdom. A standard Oyster card is a blue credit-card-sized stored-value contactless smart card. It is promoted by Transport for London (TfL) and can be used on travel modes across London including London Buses, London Underground, the Docklands Light Railway (DLR), London Overground, Tramlink, some river boat services, and most National Rail services within the London fare zones. Since its introduction in June 2003, more than 86 million cards have been used. Oyster cards can hold period tickets; travel permits and; most commonly, credit for travel ("Pay as you go"), which must be added to the card before travel. Passengers touch it on an electronic reader when entering and leaving the transport system in order to validate it and deduct funds from the stored credit. Cards may be "topped-up" by continuous payment authority, by online purchase, at credit card t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CharlieCard
The CharlieCard is a contactless smart card used for fare payment for transportation in the Boston area. It is the primary payment method for the Massachusetts Bay Transportation Authority (MBTA) and several regional public transport systems in the U.S. state of Massachusetts. The card was introduced on December 4, 2006, to enhance the technology of the transit system and eliminate the burden of carrying and collecting tokens. It replaces the metal token, the last one of which was sold at Government Center station on December 6, 2006. It is named after a fictional character in the folk song " M.T.A.", often called "Charlie on the MTA", which concerns a man forever trapped on the Boston subway system – then known as the Metropolitan Transit Authority (MTA) – because he cannot pay the 5-cent surcharge required to leave the train. In 2022, the original CharlieCard system will be replaced during the "Automated Fare Collection 2.0" project, a system similar to the Lond ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OV-chipkaart
The OV-chipkaart (short for ''openbaar vervoer chipkaart'', meaning ''public transport chipcard'') is a contactless smart card system used for all public transport in the Netherlands. First introduced in the Rotterdam Metro in April 2005, it has subsequently been rolled out to other areas and travel modes. It fully replaced the national strippenkaart system for buses, trams, and metro trains in 2011, and the paper ticket system for rail travel in July 2014. The OV-chipkaart is available in disposable form (for occasional passengers, such as tourists) and reusable versions (for frequent travellers, either in anonymous or personalised forms). History and coverage The OV-chipkaart is a collaborative initiative of five large public transport operators in the Netherlands: the main rail operator NS, the bus operator Connexxion and the municipal transport operators of the three largest cities: GVB (Amsterdam), HTM (The Hague) and RET (Rotterdam), though all public transport operator ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |