|
Convergence (SSL)
Convergence was a proposed strategy for replacing SSL certificate authorities, first put forth by Moxie Marlinspike in August 2011 while giving a talk titled "SSL and the Future of Authenticity" at the Black Hat security conference. It was demonstrated with a Firefox addon and a server-side notary daemon. In the talk, Marlinspike proposed that all of the current problems with the certificate authority (CA) system could be reduced to a single missing property, which he called "trust agility" and which Convergence aimed to provide. The strategy claimed to be agile, secure, and distributed. As of 2013, Marlinspike is focused on an IETF proposal called TACK, which is designed to be an uncontroversial first step that advocates for dynamic certificate pinning instead of full CA replacement and reduces the number of times a third party needs to be trusted. Development of Convergence was continued in a "Convergence Extra" fork until about 2014. Background Convergence was based on pre ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Browsing
Web navigation refers to the process of navigating a network of information resources in the World Wide Web, which is organized as hypertext or hypermedia. The user interface that is used to do so is called a web browser. A central theme in web design is the development of a web navigation interface that maximizes usability. A website overall navigational scheme includes several navigational pieces such as global, local, supplemental, and contextual navigation; all of these are vital aspects of the broad topic of web navigation. Hierarchical navigation systems are vital as well since it is the primary navigation system. It allows for the user to navigate within the site using levels alone, which is often seen as restricting and requires additional navigation systems to better structure the website. The global navigation of a website, as another segment of web navigation, serves as the outline and template in order to achieve an easy maneuver for the users accessing the site, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Redundancy (engineering)
In engineering, redundancy is the intentional duplication of critical components or functions of a system with the goal of increasing reliability of the system, usually in the form of a backup or fail-safe, or to improve actual system performance, such as in the case of GNSS receivers, or multi-threaded computer processing. In many safety-critical systems, such as fly-by-wire and hydraulic systems in aircraft, some parts of the control system may be triplicated, which is formally termed triple modular redundancy (TMR). An error in one component may then be out-voted by the other two. In a triply redundant system, the system has three sub components, all three of which must fail before the system fails. Since each one rarely fails, and the sub components are expected to fail independently, the probability of all three failing is calculated to be extraordinarily small; it is often outweighed by other risk factors, such as human error. Redundancy may also be known by the te ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Verifiable Data Structures
Verify or verification may refer to: General * Verification and validation, in engineering or quality management systems, is the act of reviewing, inspecting or testing, in order to establish and document that a product, service or system meets regulatory or technical standards ** Verification (spaceflight), in the space systems engineering area, covers the processes of qualification and acceptance * Verification theory, philosophical theory relating the meaning of a statement to how it is verified * Third-party verification, use of an independent organization to verify the identity of a customer * Authentication, confirming the truth of an attribute claimed by an entity, such as an identity * Forecast verification, verifying prognostic output from a numerical model * Verifiability (science), a scientific principle * Verification (audit), an auditing process Computing * Punched card verification, a data entry step performed after keypunching on a separate, keyboard-equipped ma ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Certificate Transparency
Certificate Transparency (CT) is an Internet security standard for monitoring and auditing the issuance of digital certificates. The standard creates a system of public logs that seek to eventually record all certificates issued by publicly trusted certificate authorities, allowing efficient identification of mistakenly or maliciously issued certificates. Version 2.0 of the Certificate Transparency mechanism, the latest, is described in the experimental , which obsoletes the earlier version 1.0 described in . Technical overview The certificate transparency system consists of a system of append-only certificate logs. Logs are operated by many parties, including browser vendors and certificate authorities. Certificates that support certificate transparency must include one or more ''signed certificate timestamps'' (SCTs), which is a promise from a log operator to include the certificate in their log within a ''maximum merge delay'' (MMD). At some point within the maximum merg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTTP Public Key Pinning
HTTP Public Key Pinning (HPKP) is an obsolete Internet security mechanism delivered via an HTTP header which allows HTTPS websites to resist impersonation by attackers using misissued or otherwise fraudulent digital certificates. A server uses it to deliver to the client (e.g. web browser) a set of hashes of public keys that must appear in the certificate chain of future connections to the same domain name. For example, attackers might compromise a certificate authority, and then mis-issue certificates for a web origin. To combat this risk, the HTTPS web server serves a list of “pinned” public key hashes valid for a given time; on subsequent connections, during that validity time, clients expect the server to use one or more of those public keys in its certificate chain. If it does not, an error message is shown, which cannot be (easily) bypassed by the user. The technique does not pin certificates, but public key hashes. This means that one can use the key pair to get a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Of Trust
In cryptography, a web of trust is a concept used in PGP, GnuPG, and other OpenPGP-compatible systems to establish the authenticity of the binding between a public key and its owner. Its decentralized trust model is an alternative to the centralized trust model of a public key infrastructure (PKI), which relies exclusively on a certificate authority (or a hierarchy of such). As with computer networks, there are many independent webs of trust, and any user (through their public key certificate) can be a part of, and a link between, multiple webs. The web of trust concept was first put forth by PGP creator Phil Zimmermann in 1992 in the manual for PGP version 2.0: Note the use of the word emergence in this context. The web of trust makes use of the concept of emergence. Operation of a web of trust All OpenPGP-compliant implementations include a certificate vetting scheme to assist with this; its operation has been termed a web of trust. OpenPGP certificates (which in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pretty Good Privacy
Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991. PGP and similar software follow the OpenPGP, an open standard of PGP encryption software, standard (RFC 4880) for encrypting and decrypting data. Design PGP encryption uses a serial combination of hashing, data compression, symmetric-key cryptography, and finally public-key cryptography; each step uses one of several supported algorithms. Each public key is bound to a username or an e-mail address. The first version of this system was generally known as a web of trust to contrast with the X.509 system, which uses a hierarchical approach based on certificate authority and which was added to PGP implementations later. Current v ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Monkeysphere Project
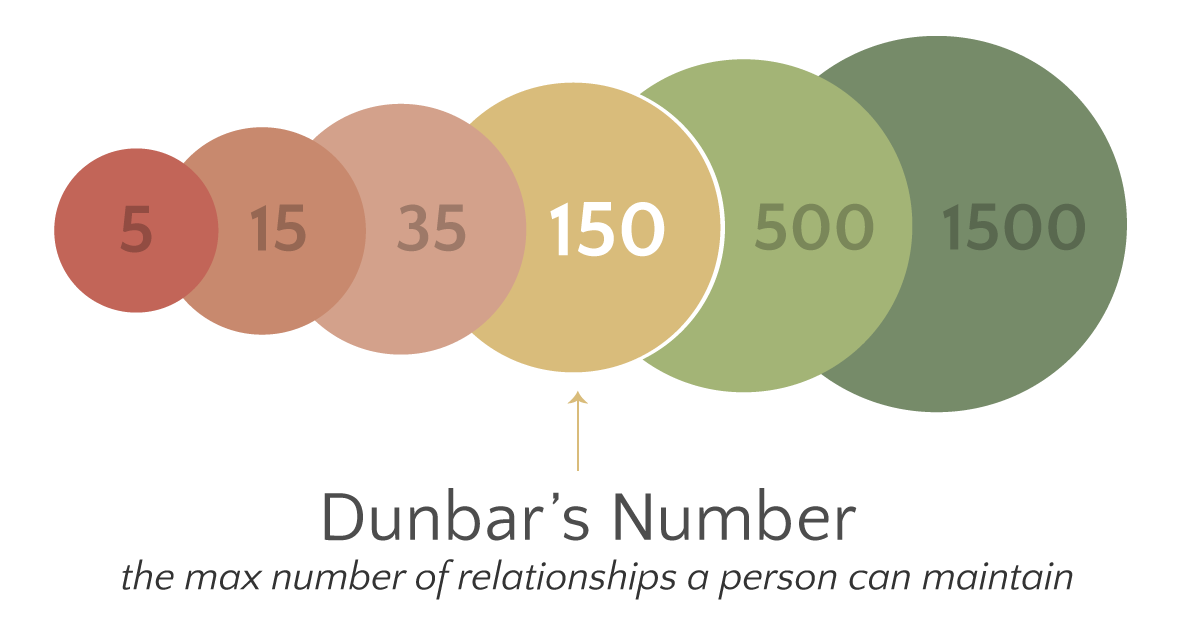
Dunbar's number is a suggested cognitive limit to the number of people with whom one can maintain stable social relationships—relationships in which an individual knows who each person is and how each person relates to every other person. This number was first proposed in the 1990s by British anthropologist Robin Dunbar, who found a correlation between primate brain size and average social group size. By using the average human brain size and extrapolating from the results of primates, he proposed that humans can comfortably maintain 150 stable relationships. There is some evidence that brain structure predicts the number of friends one has, though causality remains to be seen. Dunbar explained it informally as "the number of people you would not feel embarrassed about joining uninvited for a drink if you happened to bump into them in a bar." Dunbar theorised that "this limit is a direct function of relative neocortex size, and that this, in turn, limits group size ..the lim ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Qualys
Qualys, Inc. provides cloud security, compliance and related services and is based in Foster City, California. Qualys provides vulnerability management solutions using a "software as a service" (SaaS) model. It has added cloud-based compliance and web application security offerings. Qualys has over 10,300 customers in more than 130 countries, including a majority of the Forbes Global 100. The company has strategic partnerships with major managed services providers and consulting organizations including BT, Dell SecureWorks, Fujitsu, IBM, NTT, Symantec, Verizon, and Wipro. The company is also a founding member of the Cloud Security Alliance (CSA). History Qualys has been described as "one of the earliest software-as-a-service security vendors." Philippe Courtot first invested in the company in 1999. He became CEO and board chair in 2001. In the announcement of the second round of financing, Courtot described Qualys as addressing a "mounting need for automatic detection of ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Majority Vote
A majority, also called a simple majority or absolute majority to distinguish it from related terms, is more than half of the total.Dictionary definitions of ''majority'' aMerriam-Webster Oxford English Dictionary an Cambridge English Dictionary It is a |
Single Point Of Failure
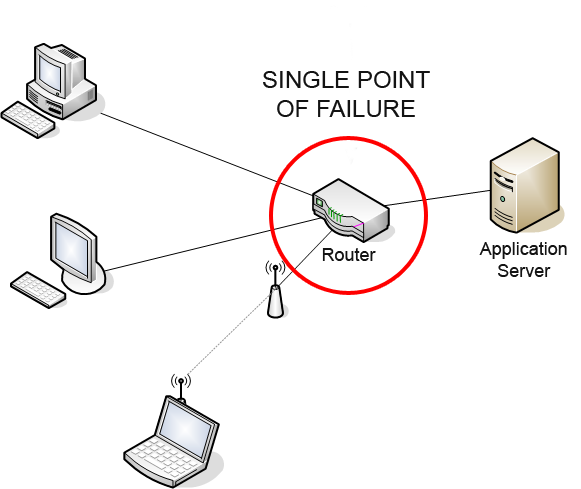
A single point of failure (SPOF) is a part of a system that, if it fails, will stop the entire system from working. SPOFs are undesirable in any system with a goal of high availability or reliability, be it a business practice, software application, or other industrial system. Overview Systems can be made robust by adding redundancy in all potential SPOFs. Redundancy can be achieved at various levels. The assessment of a potential SPOF involves identifying the critical components of a complex system that would provoke a total systems failure in case of malfunction. Highly reliable systems should not rely on any such individual component. For instance, the owner of a small tree care company may only own one woodchipper. If the chipper breaks, he may be unable to complete his current job and may have to cancel future jobs until he can obtain a replacement. The owner of the tree care company may have spare parts ready for the repair of the wood chipper, in case it fails. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Certificate Authority
In cryptography, a certificate authority or certification authority (CA) is an entity that stores, signs, and issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. A CA acts as a trusted third party—trusted both by the subject (owner) of the certificate and by the party relying upon the certificate. The format of these certificates is specified by the X.509 or EMV standard. One particularly common use for certificate authorities is to sign certificates used in HTTPS, the secure browsing protocol for the World Wide Web. Another common use is in issuing identity cards by national governments for use in electronically signing documents. Overview Trusted certificates can be used to create secure connections to a server via the Internet. A certificate ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
.jpg)