|
Concatenated Error Correction Code
In coding theory, concatenated codes form a class of error-correcting codes that are derived by combining an inner code and an outer code. They were conceived in 1966 by Dave Forney as a solution to the problem of finding a code that has both exponentially decreasing error probability with increasing block length and polynomial-time decoding complexity. Concatenated codes became widely used in space communications in the 1970s. Background The field of channel coding is concerned with sending a stream of data at the highest possible rate over a given communications channel, and then decoding the original data reliably at the receiver, using encoding and decoding algorithms that are feasible to implement in a given technology. Shannon's channel coding theorem shows that over many common channels there exist channel coding schemes that are able to transmit data reliably at all rates R less than a certain threshold C, called the channel capacity of the given channel. In fact, the p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Coding Theory
Coding theory is the study of the properties of codes and their respective fitness for specific applications. Codes are used for data compression, cryptography, error detection and correction, data transmission and computer data storage, data storage. Codes are studied by various scientific disciplines—such as information theory, electrical engineering, mathematics, linguistics, and computer science—for the purpose of designing efficient and reliable data transmission methods. This typically involves the removal of redundancy and the correction or detection of errors in the transmitted data. There are four types of coding: # Data compression (or ''source coding'') # Error detection and correction, Error control (or ''channel coding'') # Cryptography, Cryptographic coding # Line code, Line coding Data compression attempts to remove unwanted redundancy from the data from a source in order to transmit it more efficiently. For example, DEFLATE data compression makes files small ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Decoding Concatenated Codes
Decoding or decode may refer to: is the process of converting code into plain text or any format that is useful for subsequent processes. Science and technology * Decoding, the reverse of encoding * Parsing, in computer science * Digital-to-analog converter, "decoding" of a digital signal * Phonics, decoding in communication theory * Decode (Oracle) Other uses * deCODE genetics, a biopharmaceutical company based in Iceland * "Decode" (song), a 2008 song by Paramore * ”Decode”, a song by Sabrina Carpenter from the album Emails I Can't Send * Decoding (semiotics), the interpreting of a message communicated to a receiver See also * Code (other) * Decoder (other) * Decoding methods, methods in communication theory for decoding codewords sent over a noisy channel * Codec, a coder-decoder * Recode (other) * Video decoder A video decoder is an electronic circuit, often contained within a single integrated circuit chip, that converts base-band analog vid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
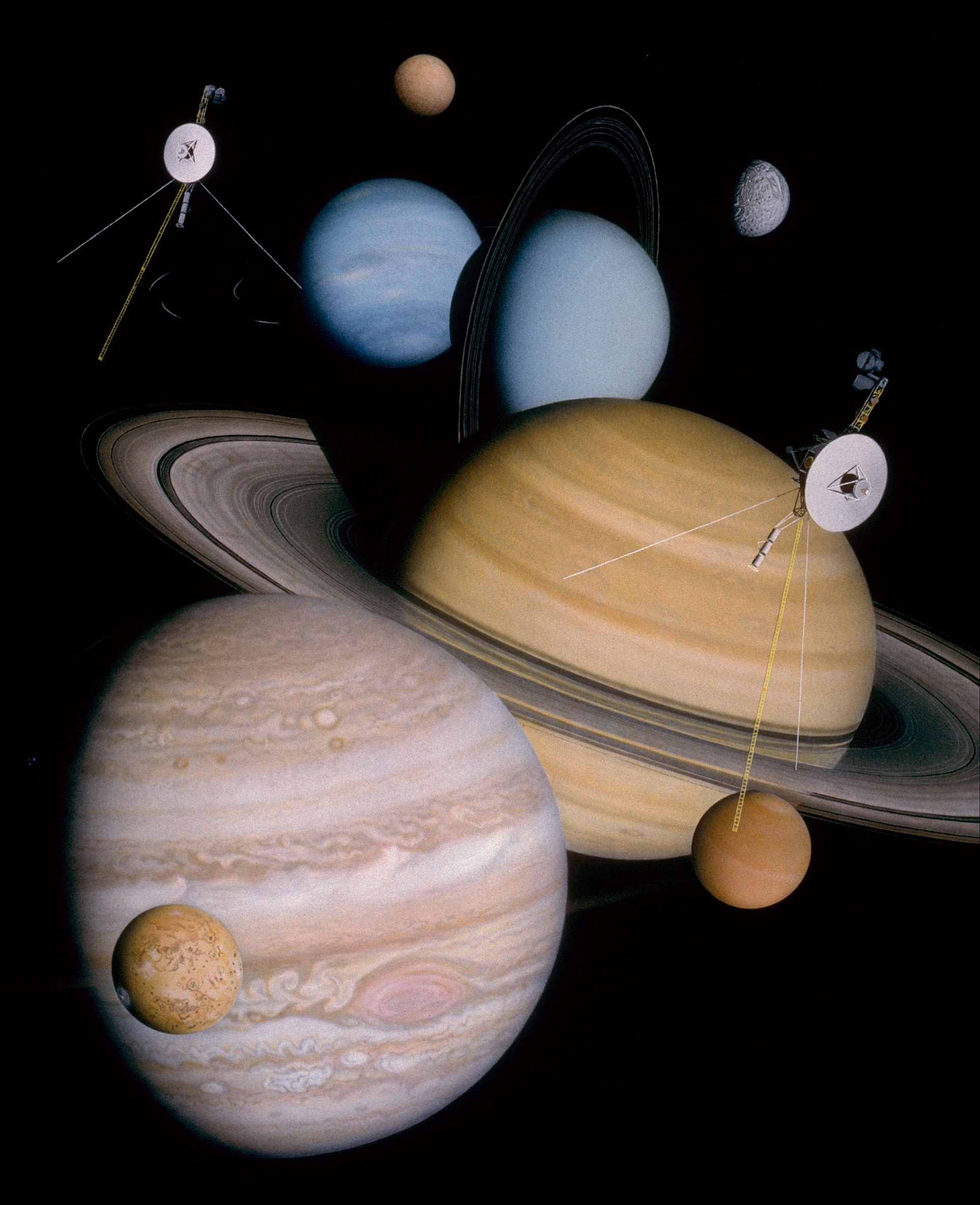
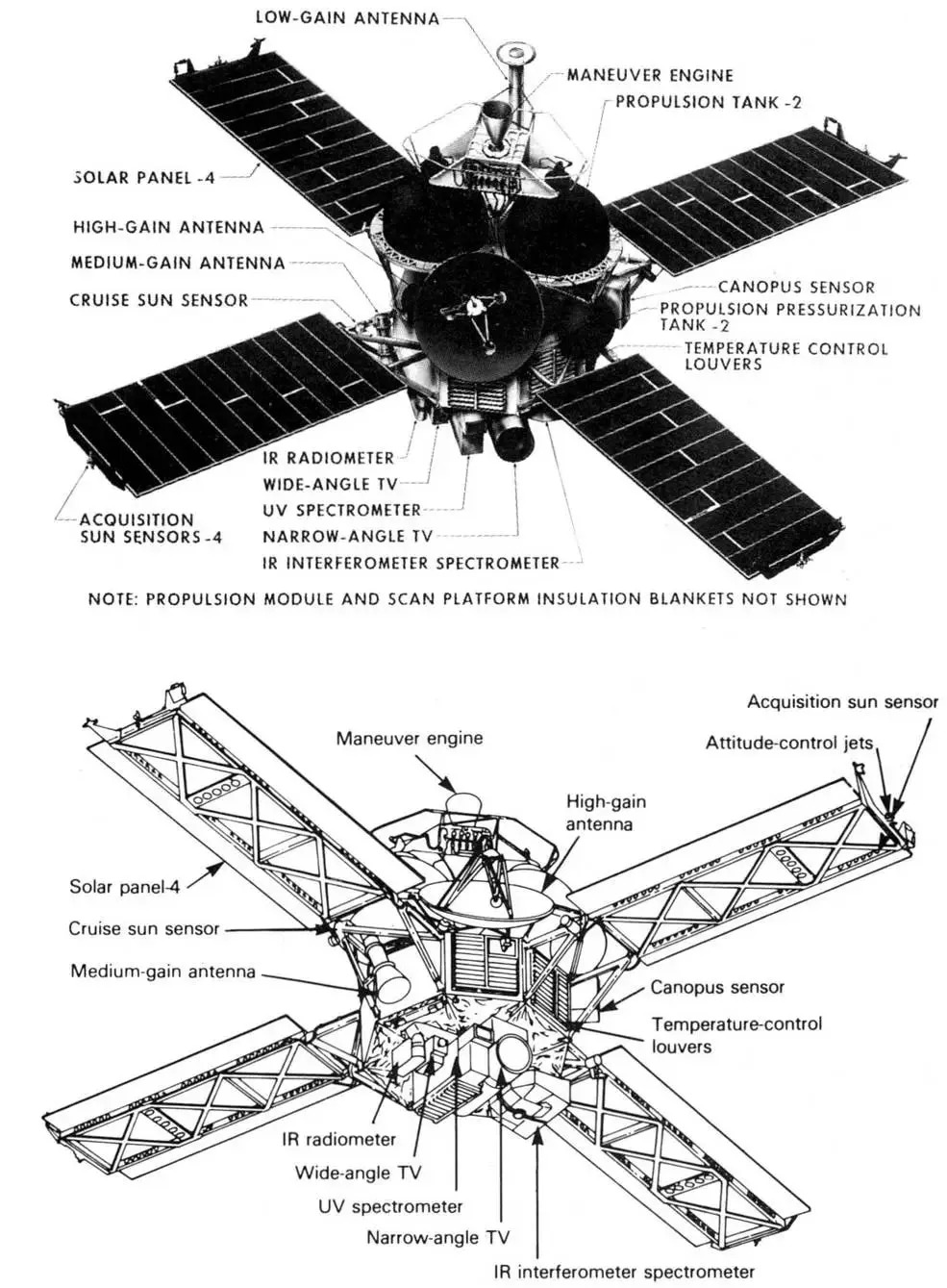
Voyager Program
The Voyager program is an American scientific program that employs two interstellar probes, ''Voyager 1'' and ''Voyager 2''. They were launched in 1977 to take advantage of a favorable planetary alignment to explore the two gas giants Jupiter and Saturn and potentially also the ice giants, Uranus and Neptune—to Flyby (spaceflight), fly near them while collecting data for transmission back to Earth. After ''Voyager 1'' successfully completed its flyby of Saturn and its moon Titan (moon), Titan, it was decided to send ''Voyager 2'' on flybys of Uranus and Neptune. After the planetary flybys were complete, decisions were made to keep the probes in operation to explore Outer space, interstellar space and the outer regions of the Solar System. On 25 August 2012, data from ''Voyager 1'' indicated that it had entered interstellar space. On 5 November 2019, data from ''Voyager 2'' indicated that it also had entered interstellar space. On 4 November 2019, scientists reported that on ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Deep Space Network
The NASA Deep Space Network (DSN) is a worldwide Telecommunications network, network of spacecraft communication ground segment facilities, located in the United States (California), Spain (Madrid), and Australia (Canberra), that supports NASA's interplanetary spaceflight, interplanetary spacecraft missions. It also performs radio astronomy, radio and radar astronomy observations for the exploration of the Solar System and the universe, and supports selected Earth-orbiting missions. DSN is part of the NASA Jet Propulsion Laboratory (JPL). General information DSN currently consists of three deep-space communications facilities located such that a distant spacecraft is always in view of at least one station. They are: * the Goldstone Deep Space Communications Complex () about north of Barstow, California, Barstow, California. For details of Goldstone's contribution to the early days of space probe tracking, see Project Space Track (1957-1961), Project Space Track; * the Mad ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mariner 8
Mariner-H (Mariner Mars '71), also commonly known as Mariner 8, was (along with Mariner 9) part of the Mariner Mars '71 project. It was intended to go into Mars orbit and return images and data, but a launch vehicle failure prevented Mariner 8 from achieving Earth orbit and the spacecraft reentered into the Atlantic Ocean shortly after launch. Mission Mariner 8 was launched on an Atlas-Centaur SLV-3C booster (AC-24). The main Centaur engine was ignited 265 seconds after launch, but the upper stage began to oscillate in pitch and tumbled out of control. The Centaur stage shut down 365 seconds after launch due to starvation caused by the tumbling. The Centaur and spacecraft payload separated and re-entered the Earth's atmosphere approximately downrange and fell into the Atlantic Ocean about north of Puerto Rico. A guidance system failure was suspected as the culprit, but JPL navigation chief Bill O'Neil dismissed the idea that the entire guidance system had failed. He argued ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Soft-decision Decoding
In information theory, a soft-decision decoder is a kind of decoding method – a class of algorithm used to decode data that has been encoded with an error correcting code. Whereas a hard-decision decoder operates on data that take on a fixed set of possible values (typically 0 or 1 in a binary code), the inputs to a soft-decision decoder may take on a whole range of values in-between. This extra information indicates the reliability of each input data point, and is used to form better estimates of the original data. Therefore, a soft-decision decoder will typically perform better in the presence of corrupted data than its hard-decision counterpart. Soft-decision decoders are often used in Viterbi decoders and turbo code decoders. See also * Forward error correction In computing, telecommunication, information theory, and coding theory, forward error correction (FEC) or channel coding is a technique used for controlling errors in data transmission over unreliable or no ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Erasure Code
In coding theory, an erasure code is a forward error correction (FEC) code under the assumption of bit erasures (rather than bit errors), which transforms a message of ''k'' symbols into a longer message (code word) with ''n'' symbols such that the original message can be recovered from a subset of the ''n'' symbols. The fraction ''r'' = ''k''/''n'' is called the code rate. The fraction ''k’/k'', where ''k’'' denotes the number of symbols required for recovery, is called reception efficiency. The recovery algorithm expects that it is known which of the ''n'' symbols are lost. History Erasure coding was invented by Irving Reed and Gustave Solomon in 1960. There are many different erasure coding schemes. The most popular erasure codes are Reed-Solomon coding, Low-density parity-check code (LDPC codes), and Turbo codes. As of 2023, modern data storage systems can be designed to tolerate the complete failure of a few disks without data loss, using one of 3 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Generalized Minimum Distance Decoding
In coding theory, generalized minimum-distance (GMD) decoding provides an efficient algorithm for decoding concatenated codes, which is based on using an errors-and- erasures decoder for the outer code. A naive decoding algorithm for concatenated codes can not be an optimal way of decoding because it does not take into account the information that maximum likelihood decoding (MLD) gives. In other words, in the naive algorithm, inner received codewords are treated the same regardless of the difference between their hamming distances. Intuitively, the outer decoder should place higher confidence in symbols whose inner encodings are close to the received word. David Forney in 1966 devised a better algorithm called generalized minimum distance (GMD) decoding which makes use of those information better. This method is achieved by measuring confidence of each received codeword, and erasing symbols whose confidence is below a desired value. And GMD decoding algorithm was one of the firs ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Minimum Distance Decoding
In coding theory, decoding is the process of translating received messages into codewords of a given code. There have been many common methods of mapping messages to codewords. These are often used to recover messages sent over a noisy channel, such as a binary symmetric channel. Notation C \subset \mathbb_2^n is considered a binary code with the length n; x,y shall be elements of \mathbb_2^n; and d(x,y) is the distance between those elements. Ideal observer decoding One may be given the message x \in \mathbb_2^n, then ideal observer decoding generates the codeword y \in C. The process results in this solution: :\mathbb(y \mbox \mid x \mbox) For example, a person can choose the codeword y that is most likely to be received as the message x after transmission. Decoding conventions Each codeword does not have an expected possibility: there may be more than one codeword with an equal likelihood of mutating into the received message. In such a case, the sender and receiver(s) must ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Decoding Methods
In coding theory, decoding is the process of translating received messages into Code word (communication), codewords of a given code. There have been many common methods of mapping messages to codewords. These are often used to recover messages sent over a noisy channel, such as a binary symmetric channel. Notation C \subset \mathbb_2^n is considered a binary code with the length n; x,y shall be elements of \mathbb_2^n; and d(x,y) is the distance between those elements. Ideal observer decoding One may be given the message x \in \mathbb_2^n, then ideal observer decoding generates the codeword y \in C. The process results in this solution: :\mathbb(y \mbox \mid x \mbox) For example, a person can choose the codeword y that is most likely to be received as the message x after transmission. Decoding conventions Each codeword does not have an expected possibility: there may be more than one codeword with an equal likelihood of mutating into the received message. In such a case, the s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Exponential Time
In theoretical computer science, the time complexity is the computational complexity that describes the amount of computer time it takes to run an algorithm. Time complexity is commonly estimated by counting the number of elementary operations performed by the algorithm, supposing that each elementary operation takes a fixed amount of time to perform. Thus, the amount of time taken and the number of elementary operations performed by the algorithm are taken to be related by a constant factor. Since an algorithm's running time may vary among different inputs of the same size, one commonly considers the worst-case time complexity, which is the maximum amount of time required for inputs of a given size. Less common, and usually specified explicitly, is the average-case complexity, which is the average of the time taken on inputs of a given size (this makes sense because there are only a finite number of possible inputs of a given size). In both cases, the time complexity is genera ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Generator Matrix
In coding theory, a generator matrix is a matrix whose rows form a basis for a linear code. The codewords are all of the linear combinations of the rows of this matrix, that is, the linear code is the row space of its generator matrix. Terminology If G is a matrix, it generates the codewords of a linear code ''C'' by : w=sG where w is a codeword of the linear code ''C'', and s is any input vector. Both w and s are assumed to be row vectors. A generator matrix for a linear , k, dq-code has format k \times n, where ''n'' is the length of a codeword, ''k'' is the number of information bits (the dimension of ''C'' as a vector subspace), ''d'' is the minimum distance of the code, and ''q'' is size of the finite field, that is, the number of symbols in the alphabet (thus, ''q'' = 2 indicates a binary code, etc.). The number of redundant bits is denoted by r = n - k. The ''standard'' form for a generator matrix is, : G = \begin I_k , P \end, where I_k is the k \times k identity m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |