|
Computer Surveillance In The Workplace
Computer surveillance in the workplace is the use of computers to monitor activity in a workplace. Computer monitoring is a method of collecting performance data which employers obtain through digitalised employee monitoring. Computer surveillance may nowadays be used alongside traditional security applications, such as closed-circuit television. Computer usage monitoring Depending upon the technology and methods used, monitoring applications may track all activity or may target specific activities of employees on a company-owned computer or terminal. They may monitor various devices installed on the computer (e.g., web cameras and microphones). This includes not only recordings from these devices but also remote broadcasting of live feed from webcams and microphones. Tools used for monitoring employee computer usage incorporate: *Screen monitoring records video or static images detailing the contents, or screen capture, of the entire video display or the content of the screen ac ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Workplace
A workplace is a location where someone Work (human activity), works, for their employer or themselves, a place of employment. Such a place can range from a Small office/home office, home office to a large office building or factory. For Industrial society, industrialized societies, the workplace is one of the most important social spaces other than the home, constituting "a central concept for several entities: the worker and [their] family, the employing organization, the customers of the organization, and the society as a whole". The development of new communication technologies has led to the development of the virtual workplace and remote work. Workplace issues * Sexual harassment: Unwelcome sexual advances or conduct of a sexual nature which unreasonably interferes with the performance of a person's job or creates an intimidating, hostile, or offensive work environment. * Kiss up kick down * Toxic workplace * Workplace aggression: A specific type of aggression that occurs ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
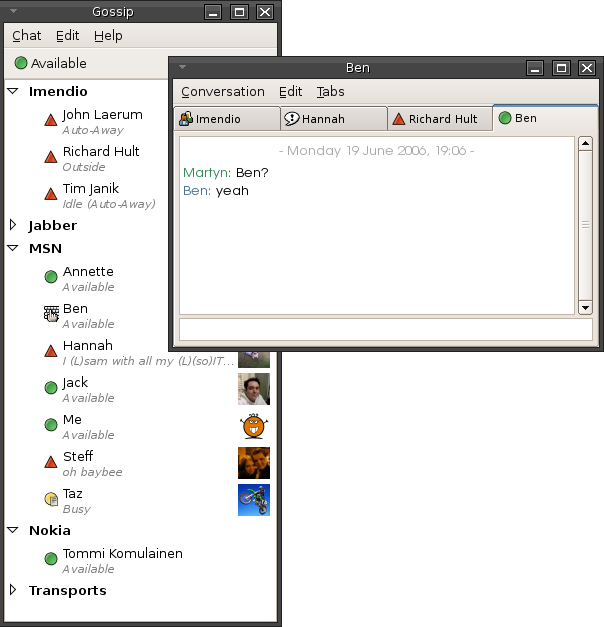
Instant Message
Instant messaging (IM) technology is a type of online chat allowing real-time text transmission over the Internet or another computer network. Messages are typically transmitted between two or more parties, when each user inputs text and triggers a transmission to the recipient(s), who are all connected on a common network. It differs from email in that conversations over instant messaging happen in real-time (hence "instant"). Most modern IM applications (sometimes called "social messengers", "messaging apps" or "chat apps") use push technology and also add other features such as emojis (or graphical smileys), file transfer, chatbots, voice over IP, or video chat capabilities. Instant messaging systems tend to facilitate connections between specified known users (often using a contact list also known as a "buddy list" or "friend list"), and can be standalone applications or integrated into e.g. a wider social media platform, or a website where it can for instance be used for co ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Labor Union
A trade union (labor union in American English), often simply referred to as a union, is an organization of workers intent on "maintaining or improving the conditions of their employment", ch. I such as attaining better wages and benefits (such as holiday, health care, and retirement), improving working conditions, improving safety standards, establishing complaint procedures, developing rules governing status of employees (rules governing promotions, just-cause conditions for termination) and protecting the integrity of their trade through the increased bargaining power wielded by solidarity among workers. Trade unions typically fund their head office and legal team functions through regularly imposed fees called ''union dues''. The delegate staff of the trade union representation in the workforce are usually made up of workplace volunteers who are often appointed by members in democratic elections. The trade union, through an elected leadership and bargaining committee, b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
E-mail
Electronic mail (email or e-mail) is a method of exchanging messages ("mail") between people using electronic devices. Email was thus conceived as the electronic ( digital) version of, or counterpart to, mail, at a time when "mail" meant only physical mail (hence '' e- + mail''). Email later became a ubiquitous (very widely used) communication medium, to the point that in current use, an email address is often treated as a basic and necessary part of many processes in business, commerce, government, education, entertainment, and other spheres of daily life in most countries. ''Email'' is the medium, and each message sent therewith is also called an ''email.'' The term is a mass noun. Email operates across computer networks, primarily the Internet, and also local area networks. Today's email systems are based on a store-and-forward model. Email servers accept, forward, deliver, and store messages. Neither the users nor their computers are required to be online simult ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Email Privacy
Email privacy is a broad topic dealing with issues of unauthorized access to, and inspection of, electronic mail, or unauthorized tracking when a user reads an email. This unauthorized access can happen while an email is in transit, as well as when it is stored on email servers or on a user's computer, or when the user reads the message. In countries with a constitutional guarantee of the secrecy of correspondence, whether email can be equated with letterstherefore having legal protection from all forms of eavesdroppingis disputed because of the very nature of email. In 2022 a lookback at an 1890 law review article about personal privacy (the "right to be left alone”) noted how "digital technology has been allowed to invade our lives" both by personal choice and behavior, and also by various forms of ongoing monitoring. An email has to go through potentially untrustworthy intermediate computers (email servers, ISPs) before reaching its destination, and there is no way to ver ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
American Management Association
The American Management Association (AMA) is an American non-profit educational membership organization for the promotion of management, based in New York City. Besides its headquarters there, it has local head offices throughout the world. It offers its members a wide range of training programs, seminars, conferences, studies, and publications, which cover topics as diverse as industrial or commercial management, communication, finance and accounting, human resources management, leadership, international management, marketing and sales. As a corporate training and consulting group, it provides a variety of educational and management development services to businesses, government agencies, and individuals. History Origins The origins of the American Management Association dates back to the beginning of the 20th century, when the training of industrial workers became a concern for large American companies. In 1913, 35 of the most important professional schools, led by the New ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Secure Sockets Layer
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible. The TLS protocol aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of certificates, between two or more communicating computer applications. It runs in the presentation layer and is itself composed of two layers: the TLS record and the TLS handshake protocols. The closely related Datagram Transport Layer Security (DTLS) is a communications protocol providing security to datagram-based applications. In technical writing you often you will see references to (D)TLS when it applies to both versions. TLS is a proposed Internet Engineering Task Force (IETF) standard, first defined in 1999, and the cu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible. The TLS protocol aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of certificates, between two or more communicating computer applications. It runs in the presentation layer and is itself composed of two layers: the TLS record and the TLS handshake protocols. The closely related Datagram Transport Layer Security (DTLS) is a communications protocol providing security to datagram-based applications. In technical writing you often you will see references to (D)TLS when it applies to both versions. TLS is a proposed Internet Engineering Task Force (IETF) standard, first defined in 1999, and the c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Traffic
Internet traffic is the flow of data within the entire Internet, or in certain network links of its constituent networks. Common traffic measurements are total volume, in units of multiples of the byte, or as transmission rates in bytes per certain time units. As the topology of the Internet is not hierarchical, no single point of measurement is possible for total Internet traffic. Traffic data may be obtained from the Tier 1 network providers' peering points for indications of volume and growth. However, Such data excludes traffic that remains within a single service provider's network and traffic that crosses private peering points. As of December 2022 India and China controls almost half(48%) of the Internet traffic where as once a majority but now North America, Europe’s share got reduced to a quarter of the traffic of global internet. Traffic sources File sharing constitutes a fraction of Internet traffic. The prevalent technology for file sharing is the BitTorrent pro ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Access
Web most often refers to: * Spider web, a silken structure created by the animal * World Wide Web or the Web, an Internet-based hypertext system Web, WEB, or the Web may also refer to: Computing * WEB, a literate programming system created by Donald Knuth * GNOME Web, a Web browser * Web.com, a web-design company * Webs (web hosting), a Web hosting and website building service Engineering * Web (manufacturing), continuous sheets of material passed over rollers ** Web, a roll of paper in offset printing * Web, the vertical element of an I-beam or a rail profile * Web, the interior beams of a truss Films * ''Web'' (2013 film), a documentary * ''Webs'' (film), a 2003 science-fiction movie * ''The Web'' (film), a 1947 film noir * Charlotte's Web (2006 film) Literature * ''Web'' (comics), a MLJ comicbook character (created 1942) * ''Web'' (novel), by John Wyndham (1979) * The Web (series), a science fiction series (1997–1999) * World English Bible, a public-domain Bible t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Traffic
Network traffic or data traffic is the amount of data moving across a network at a given point of time. Network data in computer networks is mostly encapsulated in network packets, which provide the load in the network. Network traffic is the main component for network traffic measurement, network traffic control and simulation. * Network traffic control - managing, prioritizing, controlling or reducing the network traffic * Network traffic measurement - measuring the amount and type of traffic on a particular network * Network traffic simulation - to measure the efficiency of a communications network * Traffic generation model - is a stochastic model of the traffic flows or data sources in a communication computer network. Proper analysis of network traffic provides the organization with the network security as a benefit - unusual amount of traffic in a network is a possible sign of an attack. Network traffic reports provide valuable insights into preventing such attacks. Traffic ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet
The Internet (or internet) is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a '' network of networks'' that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the inter-linked hypertext documents and applications of the World Wide Web (WWW), electronic mail, telephony, and file sharing. The origins of the Internet date back to the development of packet switching and research commissioned by the United States Department of Defense in the 1960s to enable time-sharing of computers. The primary precursor network, the ARPANET, initially served as a backbone for interconnection of regional academic and military networks in the 1970s to enable resource shari ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |


.jpg)
