|
Clampi
Clampi (also known as Ligats, llomo, or Rscan) is a strain of computer malware which infects Windows computers. More specifically, as a man-in-the-browser banking trojan designed to transmit financial and personal information from a compromised computer to a third party for potential financial gain as well as report on computer configuration, communicate with a central server, and act as downloader for other malware. Clampi was first observed in 2007 affecting computers running the Microsoft Windows operating system. Clampi monitored over 4000 website URLs, effectively keylogging credentials and user information for not only bank and credit card websites, but also reported on utilities, market research firms, online casinos, and career websites. At its peak in the fall of 2009, a computer security professional stated that it was one of the largest and most professional thieving operations on the Internet, likely run by a Russian or eastern European syndicate. False-positive repo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Man-in-the-browser
Man-in-the-browser (MITB, MitB, MIB, MiB), a form of Internet threat related to man-in-the-middle (MITM), is a proxy Trojan horse that infects a web browser by taking advantage of vulnerabilities in browser security to modify web pages, modify transaction content or insert additional transactions, all in a covert fashion invisible to both the user and host web application. A MitB attack will be successful irrespective of whether security mechanisms such as SSL/ PKI and/or two- or three-factor authentication solutions are in place. A MitB attack may be countered by using out-of-band transaction verification, although SMS verification can be defeated by man-in-the-mobile (MitMo) malware infection on the mobile phone. Trojans may be detected and removed by antivirus software; this approach scored a 23% success rate against Zeus in 2009 and still low rates in a 2011 report. The 2011 report concluded that additional measures on top of antivirus software were needed. A related, s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware
Malware (a portmanteau for ''malicious software'') is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. By contrast, software that causes harm due to some deficiency is typically described as a software bug. Malware poses serious problems to individuals and businesses on the Internet. According to Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 669,947,865 in 2017, which is twice as many malware variants as in 2016. Cybercrime, which includes malware attacks as well as other crimes committed by computer, was predicted to cost the world economy $6 trillion USD in 2021, and is increasing at a rate of 15% per year. Many types of malware exist, including computer viruses, worms, Trojan ho ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Firewall (computing)
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet. History The term '' firewall'' originally referred to a wall intended to confine a fire within a line of adjacent buildings. Later uses refer to similar structures, such as the metal sheet separating the engine compartment of a vehicle or aircraft from the passenger compartment. The term was applied in the late 1980s to network technology that emerged when the Internet was fairly new in terms of its global use and connectivity. The predecessors to firewalls for network security were routers used in the late 1980s. Because they already segregated networks, routers could apply filtering to packets crossing them. Before it was used in real-life computing, the term appeared in the 1983 computer-hacking movie ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Operation Tovar
Operation Tovar is an international collaborative operation carried out by law enforcement agencies from multiple countries against the Gameover ZeuS botnet, which is believed by the investigators to have been used in bank fraud and the distribution of the CryptoLocker ransomware. Participants include the U.S. Department of Justice, Europol, the FBI and the U.K. National Crime Agency, South African Police Service, together with a number of security companies and academic researchers, including Dell SecureWorks, Deloitte Cyber Risk Services, Microsoft Corporation, Abuse.ch, Afilias, F-Secure, Level 3 Communications, McAfee, Neustar, Shadowserver, Anubisnetworks, Symantec, Heimdal Security, Sophos and Trend Micro, and academic researchers from Carnegie Mellon University, the Georgia Institute of Technology, VU University Amsterdam and Saarland University. Other law enforcement organizations involved include the Australian Federal Police; the National Police of the Netherland ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Gameover ZeuS
GameOverZeus is a peer-to-peer botnet based on components from the earlier ZeuS trojan. The malware was created by Russian hacker Evgeniy Mikhailovich Bogachev. It is believed to have been spread through use of the Cutwail botnet. Unlike its predecessor the ZeuS trojan, Gameover ZeuS uses an encrypted peer-to-peer communication system to communicate between its nodes and its command and control servers, greatly reducing its vulnerability to law enforcement operations. The algorithm used appears to be modeled on the Kademlia P2P protocol. Scammers control and monitor Gameover ZeuS via command and control (C&C) servers. The virus establishes the connection to the server as soon as its malicious executable installs on the computer, at which point it can disable certain system processes, download and launch executables, or delete essential system files, making the system unusable. According to a report by Symantec, Gameover ZeuS has largely been used for banking fraud and distributi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Conficker
Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in November 2008. It uses flaws in Windows OS software and dictionary attacks on administrator passwords to propagate while forming a botnet, and has been unusually difficult to counter because of its combined use of many advanced malware techniques. The Conficker worm infected millions of computers including government, business and home computers in over 190 countries, making it the largest known computer worm infection since the 2003 Welchia. Despite its wide propagation, the worm did not do much damage, perhaps because its authors – believed to have been Ukrainian citizens – did not dare use it because of the attention it drew. Four men were arrested, and one pled guilty and was sentenced to four years in prison. Prevalence Estimates of the number of infected computers were difficult because the virus changed its propagatio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Botnet
A botnet is a group of Internet-connected devices, each of which runs one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. The owner can control the botnet using command and control (C&C) software. The word "botnet" is a portmanteau of the words "robot" and " network". The term is usually used with a negative or malicious connotation. Overview A botnet is a logical collection of Internet-connected devices, such as computers, smartphones or Internet of things (IoT) devices whose security have been breached and control ceded to a third party. Each compromised device, known as a "bot," is created when a device is penetrated by software from a ''malware'' (malicious software) distribution. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Appliance
A virtual appliance is a pre-configured virtual machine image, ready to run on a hypervisor; virtual appliances are a subset of the broader class of software appliances. Installation of a software appliance on a virtual machine and packaging that into an image creates a virtual appliance. Like software appliances, virtual appliances are intended to eliminate the installation, configuration and maintenance costs associated with running complex stacks of software. A virtual appliance is not a complete virtual machine platform, but rather a software image containing a software stack designed to run on a virtual machine platform which may be a Type 1 or Type 2 hypervisor. Like a physical computer, a hypervisor is merely a platform for running an operating system environment and does not provide application software itself. Many virtual appliances provide a Web page user interface to permit their configuration. A virtual appliance is usually built to host a single application; it th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kernel (operating System)
The kernel is a computer program at the core of a computer's operating system and generally has complete control over everything in the system. It is the portion of the operating system code that is always resident in memory and facilitates interactions between hardware and software components. A full kernel controls all hardware resources (e.g. I/O, memory, cryptography) via device drivers, arbitrates conflicts between processes concerning such resources, and optimizes the utilization of common resources e.g. CPU & cache usage, file systems, and network sockets. On most systems, the kernel is one of the first programs loaded on startup (after the bootloader). It handles the rest of startup as well as memory, peripherals, and input/output (I/O) requests from software, translating them into data-processing instructions for the central processing unit. The critical code of the kernel is usually loaded into a separate area of memory, which is protected from access by application ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
System Information (Windows)
System Information (msinfo32.exe) is a system profiler included with Microsoft Windows that displays diagnostic and troubleshooting information related to the operating system, hardware and software. It has been bundled with Windows since Windows NT 4.0. It compiles technical information on the overall system, hardware resources (including memory, I/O, etc.), physical hardware components (CD-ROM, sound, network, etc.), and the Windows environment as well (drivers, environment variables, services, etc.). It can export this information in the plain text format or in files with a .nfo extension, which can be used to diagnose problems. In addition, System Information can be used to gather technical information on a remote computer on the same network. See also *Systeminfo.exe *MSConfig MSConfig (officially called System Configuration in Windows Vista, Windows 7, Windows 8 or Windows 10, or Windows 11 and Microsoft System Configuration Utility in previous operating systems) is a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
FTP Clients
The following tables compare general and technical information for a number of File Transfer Protocol (FTP) clients. Unless otherwise specified in footnotes, comparisons are based on the stable versions without any add-ons, extensions, or external programs. Free and open-source software Proprietary freeware Freeware and commercial editions Trials of commercial Commercial Operating system support The operating systems the clients can run on. (CL) Command-Line interface only – no GUI (Graphical user interface) Protocol support Information about what internet protocols the clients support. External links lead to information about support in future versions of the clients or extensions that provide such functionality. See also * File Transfer Protocol The File Transfer Protocol (FTP) is a standard communication protocol used for the transfer of computer files from a server to a client on a computer network. FTP is built on a client–server model architecture usi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
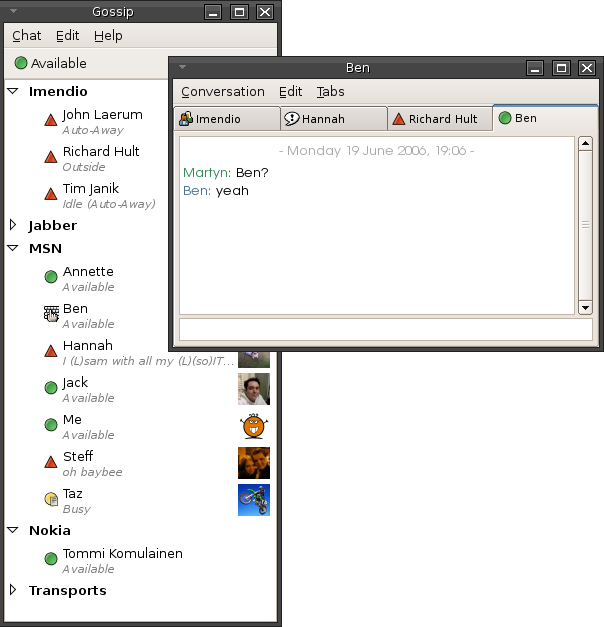
Instant Messaging
Instant messaging (IM) technology is a type of online chat allowing real-time text transmission over the Internet or another computer network. Messages are typically transmitted between two or more parties, when each user inputs text and triggers a transmission to the recipient(s), who are all connected on a common network. It differs from email in that conversations over instant messaging happen in real-time (hence "instant"). Most modern IM application (computing), applications (sometimes called "social messengers", "messaging apps" or "chat apps") use push technology and also add other features such as emojis (or graphical smileys), file transfer, chatbots, voice over IP, or Videotelephony, video chat capabilities. Instant messaging systems tend to facilitate connections between specified known users (often using a contact list also known as a "buddy list" or "friend list"), and can be standalone applications or integrated into e.g. a wider social media platform, or a website ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |