|
Bigram
A bigram or digram is a sequence of two adjacent elements from a string of tokens, which are typically letters, syllables, or words. A bigram is an ''n''-gram for ''n''=2. The frequency distribution of every bigram in a string is commonly used for simple statistical analysis of text in many applications, including in computational linguistics, cryptography, and speech recognition. ''Gappy bigrams'' or ''skipping bigrams'' are word pairs which allow gaps (perhaps avoiding connecting words, or allowing some simulation of dependencies, as in a dependency grammar). Applications Bigrams, along with other n-grams, are used in most successful language models for speech recognition. Bigram frequency attacks can be used in cryptography to solve cryptograms. See frequency analysis. Bigram frequency is one approach to statistical language identification. Some activities in logology or recreational linguistics involve bigrams. These include attempts to find English words beginning wi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Frequency Analysis (cryptanalysis)
In cryptanalysis, frequency analysis (also known as counting letters) is the study of the letter frequencies, frequency of letters or groups of letters in a ciphertext. The method is used as an aid to breaking classical ciphers. Frequency analysis is based on the fact that, in any given stretch of written language, certain letters and combinations of letters occur with varying frequencies. Moreover, there is a characteristic distribution of letters that is roughly the same for almost all samples of that language. For instance, given a section of English language, , , and are the most common, while , , and are rare. Likewise, , , , and are the most common pairs of letters (termed ''bigrams'' or ''digraphs''), and , , , and are the most common repeats. The nonsense phrase "ETAOIN SHRDLU" represents the 12 most frequent letters in typical English language text. In some ciphers, such properties of the natural language plaintext are preserved in the ciphertext, and these patte ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Digraph (orthography)
A digraph () or digram is a pair of character (symbol), characters used in the orthography of a language to write either a single phoneme (distinct sound), or a sequence of phonemes that does not correspond to the normal values of the two characters combined. Some digraphs represent phonemes that cannot be represented with a single character in the writing system of a language, like in Spanish ''chico'' and ''ocho''. Other digraphs represent phonemes that can also be represented by single characters. A digraph that shares its pronunciation with a single character may be a relic from an earlier period of the language when the digraph had a different pronunciation, or may represent a distinction that is made only in certain dialects, like the English . Some such digraphs are used for purely etymology, etymological reasons, like in French. In some orthographies, digraphs (and occasionally trigraph (orthography), trigraphs) are considered individual letter (alphabet), letters, w ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
String (computer Science)
In computer programming, a string is traditionally a sequence of character (computing), characters, either as a literal (computer programming), literal constant or as some kind of Variable (computer science), variable. The latter may allow its elements to be Immutable object, mutated and the length changed, or it may be fixed (after creation). A string is often implemented as an array data structure of bytes (or word (computer architecture), words) that stores a sequence of elements, typically characters, using some character encoding. More general, ''string'' may also denote a sequence (or List (abstract data type), list) of data other than just characters. Depending on the programming language and precise data type used, a variable (programming), variable declared to be a string may either cause storage in memory to be statically allocated for a predetermined maximum length or employ dynamic allocation to allow it to hold a variable number of elements. When a string appears lit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Formal Languages
In logic, mathematics, computer science, and linguistics, a formal language is a set of string (computer science), strings whose symbols are taken from a set called "#Definition, alphabet". The alphabet of a formal language consists of symbols that concatenate into strings (also called "words"). Words that belong to a particular formal language are sometimes called Formal language#Definition, ''well-formed words''. A formal language is often defined by means of a formal grammar such as a regular grammar or context-free grammar. In computer science, formal languages are used, among others, as the basis for defining the grammar of programming languages and formalized versions of subsets of natural languages, in which the words of the language represent concepts that are associated with meanings or semantics. In computational complexity theory, decision problems are typically defined as formal languages, and complexity classes are defined as the sets of the formal languages that ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Letter Frequency
Letter frequency is the number of times letters of the alphabet appear on average in written language. Letter frequency analysis dates back to the Arab mathematician Al-Kindi (c. AD 801–873), who formally developed the method to break ciphers. Letter frequency analysis gained importance in Europe with the development of movable type in AD 1450, wherein one must estimate the amount of type required for each letterform. Linguists use letter frequency analysis as a rudimentary technique for language identification, where it is particularly effective as an indication of whether an unknown writing system is alphabetic, syllabic, or ideographic. The use of letter frequencies and frequency analysis plays a fundamental role in cryptograms and several word puzzle games, including hangman, ''Scrabble'', '' Wordle'' and the television game show '' Wheel of Fortune''. One of the earliest descriptions in classical literature of applying the knowledge of English letter frequency to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Dice-Sørensen Coefficient
The Dice-Sørensen coefficient (see below for other names) is a statistic used to gauge the similarity of two samples. It was independently developed by the botanists Lee Raymond Dice and Thorvald Sørensen, who published in 1945 and 1948 respectively. Name The index is known by several other names, especially Sørensen–Dice index, Sørensen index and Dice's coefficient. Other variations include the "similarity coefficient" or "index", such as Dice similarity coefficient (DSC). Common alternate spellings for Sørensen are ''Sorenson'', ''Soerenson'' and ''Sörenson'', and all three can also be seen with the ''–sen'' ending (the Danish letter ø is phonetically equivalent to the German/Swedish ö, which can be written as oe in ASCII). Other names include: * F1 score * Czekanowski's binary (non-quantitative) index * Measure of genetic similarity * Zijdenbos similarity index, referring to a 1994 paper of Zijdenbos et al. Formula Sørensen's original formula was intended to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Logology (linguistics)
Logology (or ludolinguistics) is the field of recreational linguistics, an activity that encompasses a wide variety of word games and wordplay. The term is analogous to the term "recreational mathematics". Overview Some of the topics studied in logology are lipograms, acrostics, palindromes, tautonyms, isograms, pangrams, bigrams, trigrams, tetragrams, transdeletion pyramids, and pangrammatic windows. The term ''logology'' was adopted by Dmitri Borgmann to refer to recreational linguistics. Notable logologists * Dmitri Borgmann * A. Ross Eckler, Jr. * Willard R. Espy * Jeremiah Farrell *Martin Gardner * Mike Keith *Douglas Hofstadter *Lila Maria de Coninck See also *Constrained writing Constrained writing is a literary technique in which the writer is bound by some condition that forbids certain things or imposes a pattern. Constraints are very common in poetry, which often requires the writer to use a particular verse form. D ... * List of forms of word play * Oulip ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Language Detection
In natural language processing, language identification or language guessing is the problem of determining which natural language given content is in. Computational approaches to this problem view it as a special case of text categorization, solved with various statistical methods. Overview There are several statistical approaches to language identification using different techniques to classify the data. One technique is to compare the compressibility of the text to the compressibility of texts in a set of known languages. This approach is known as mutual information based distance measure. The same technique can also be used to empirically construct family trees of languages which closely correspond to the trees constructed using historical methods. Mutual information based distance measure is essentially equivalent to more conventional model-based methods and is not generally considered to be either novel or better than simpler techniques. Another technique, as described ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cryptograms
A cryptogram is a type of puzzle that consists of a short piece of encryption, encrypted text. Generally the cipher used to encrypt the text is simple enough that the cryptogram can be solved by hand. Substitution ciphers where each letter is replaced by a different letter, number, or symbol are frequently used. To solve the puzzle, one must recover the original lettering. Though once used in more serious applications, they are now mainly printed for entertainment in newspapers and magazines. Other types of classical ciphers are sometimes used to create cryptograms. An example is the book cipher, where a book or article is used to encrypt a message. History The ciphers used in cryptograms were created not for entertainment purposes, but for real encryption of military or privacy, personal secrets. The first use of the cryptogram for entertainment purposes occurred during the Middle Ages by monks who had spare time for intellectual games. A manuscript found at Bamberg states t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Token (parser)
Lexical tokenization is conversion of a text into (semantically or syntactically) meaningful ''lexical tokens'' belonging to categories defined by a "lexer" program. In case of a natural language, those categories include nouns, verbs, adjectives, punctuations etc. In case of a programming language, the categories include identifiers, operators, grouping symbols, data types and language keywords. Lexical tokenization is related to the type of tokenization used in large language models (LLMs) but with two differences. First, lexical tokenization is usually based on a lexical grammar, whereas LLM tokenizers are usually probability-based. Second, LLM tokenizers perform a second step that converts the tokens into numerical values. Rule-based programs A rule-based program, performing lexical tokenization, is called ''tokenizer'', or ''scanner'', although ''scanner'' is also a term for the first stage of a lexer. A lexer forms the first phase of a compiler frontend in processing. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Language Model
A language model is a model of the human brain's ability to produce natural language. Language models are useful for a variety of tasks, including speech recognition, machine translation,Andreas, Jacob, Andreas Vlachos, and Stephen Clark (2013)"Semantic parsing as machine translation". Proceedings of the 51st Annual Meeting of the Association for Computational Linguistics (Volume 2: Short Papers). natural language generation (generating more human-like text), optical character recognition, route optimization, handwriting recognition, grammar induction, and information retrieval. Large language models (LLMs), currently their most advanced form, are predominantly based on transformers trained on larger datasets (frequently using words scraped from the public internet). They have superseded recurrent neural network-based models, which had previously superseded the purely statistical models, such as word ''n''-gram language model. History Noam Chomsky did pioneering work on lan ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
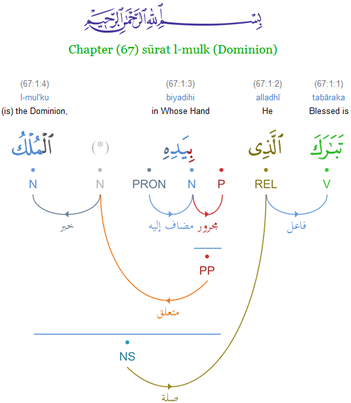
Dependency Grammar
Dependency grammar (DG) is a class of modern Grammar, grammatical theories that are all based on the dependency relation (as opposed to the ''constituency relation'' of Phrase structure grammar, phrase structure) and that can be traced back primarily to the work of Lucien Tesnière. Dependency is the notion that linguistic units, e.g. words, are connected to each other by directed links. The (finite) verb is taken to be the structural center of clause structure. All other syntactic units (words) are either directly or indirectly connected to the verb in terms of the directed links, which are called ''dependencies''. Dependency grammar differs from phrase structure grammar in that while it can identify phrases it tends to overlook phrasal nodes. A dependency structure is determined by the relation between a word (a Head (linguistics), head) and its dependents. Dependency structures are flatter than phrase structures in part because they lack a finite verb, finite verb phrase constit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |