|
Attack (computing)
A cyberattack (or cyber attack) occurs when there is an unauthorized action against computer infrastructure that compromises the confidentiality, integrity, or availability of its content. The rising dependence on increasingly complex and interconnected computer systems in most domains of life is the main factor that causes vulnerability to cyberattacks, since virtually all computer systems have bugs that can be exploited by attackers. Although it is impossible or impractical to create a perfectly secure system, there are many defense mechanisms that can make a system more difficult to attack, making information security a field of rapidly increasing importance in the world today. Perpetrators of a cyberattack can be criminals, hacktivists, or states. They attempt to find weaknesses in a system, exploit them and create malware to carry out their goals, and deliver it to the targeted system. Once installed, the malware can have a variety of effects depending on its purpose. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CIA Triad
Information security is the practice of protecting information by mitigating information risks. It is part of information risk management. It typically involves preventing or reducing the probability of unauthorized or inappropriate access to data or the unlawful use, disclosure, disruption, deletion, corruption, modification, inspection, recording, or devaluation of information. It also involves actions intended to reduce the adverse impacts of such incidents. Protected information may take any form, e.g., electronic or physical, tangible (e.g., paperwork), or intangible (e.g., knowledge). Information security's primary focus is the balanced protection of data confidentiality, integrity, and availability (also known as the 'CIA' triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a structured risk management process. To standardize this discipline, academics and professionals col ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
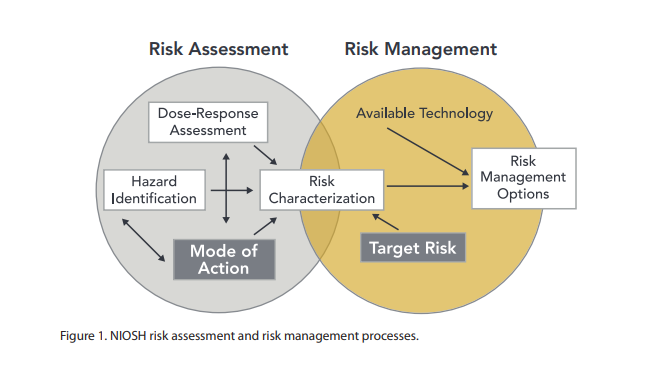
Risk Assessment
Risk assessment is a process for identifying hazards, potential (future) events which may negatively impact on individuals, assets, and/or the environment because of those hazards, their likelihood and consequences, and actions which can mitigate these effects. The output from such a process may also be called a risk assessment. Hazard analysis forms the first stage of a risk assessment process. Judgments "on the tolerability of the risk on the basis of a risk analysis" (i.e. risk evaluation) also form part of the process. The results of a risk assessment process may be expressed in a quantitative or qualitative fashion. Risk assessment forms a key part of a broader risk management strategy to help reduce any potential risk-related consequences. Categories Individual risk assessment Risk assessments can be undertaken in individual cases, including in patient and physician interactions. In the narrow sense chemical risk assessment is the assessment of a health risk in response ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Open Source Intelligence
Open source intelligence (OSINT) is the collection and analysis of data gathered from open sources (overt sources and publicly available information) to produce actionable intelligence. OSINT is primarily used in national security, law enforcement, and business intelligence functions and is of value to analysts who use non-sensitive intelligence in answering classified, unclassified, or proprietary intelligence requirements across the previous intelligence disciplines. Categories OSINT sources can be divided up into six different categories of information flow: *Media: print newspapers, magazines, radio, and television from across and between countries. *Internet: online publications, blogs, discussion groups, citizen media (i.e. – cell phone videos, and user created content), YouTube, and other social media websites (i.e. – Facebook, Twitter, , etc.). This source also outpaces a variety of other sources due to its timeliness and ease of access. *Public government da ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyber Kill Chain
The cyber kill chain is the process by which perpetrators carry out cyberattacks. Lockheed Martin adapted the concept of the '' kill chain'' from a military setting to information security, using it as a method for modeling intrusions on a computer network. The cyber kill chain model has seen some adoption in the information security community. However, acceptance is not universal, with critics pointing to what they believe are fundamental flaws in the model. Attack phases and countermeasures Computer scientists at Lockheed-Martin corporation described a new "intrusion kill chain" framework or model to defend computer networks in 2011. They wrote that attacks may occur in phases and can be disrupted through controls established at each phase. Since then, the "cyber kill chain" has been adopted by data security organizations to define phases of cyberattacks. A cyber kill chain reveals the phases of a cyberattack: from early reconnaissance to the goal of data exfiltration. The k ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cyberattack Chain
A cyberattack (or cyber attack) occurs when there is an unauthorized action against computer infrastructure that compromises the confidentiality, integrity, or availability of its content. The rising dependence on increasingly complex and interconnected computer systems in most domains of life is the main factor that causes vulnerability to cyberattacks, since virtually all computer systems have bugs that can be exploited by attackers. Although it is impossible or impractical to create a perfectly secure system, there are many defense mechanisms that can make a system more difficult to attack, making information security a field of rapidly increasing importance in the world today. Perpetrators of a cyberattack can be criminals, hacktivists, or states. They attempt to find weaknesses in a system, exploit them and create malware to carry out their goals, and deliver it to the targeted system. Once installed, the malware can have a variety of effects depending on its purpose. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intrusion Kill Chain - V2
In geology, an igneous intrusion (or intrusive body or simply intrusion) is a body of intrusive igneous rock that forms by crystallization of magma slowly cooling below the surface of the Earth. Intrusions have a wide variety of forms and compositions, illustrated by examples like the Palisades Sill of New York and New Jersey; the Henry Mountains of Utah; the Bushveld Igneous Complex of South Africa; Shiprock in New Mexico; the Ardnamurchan intrusion in Scotland; and the Sierra Nevada Batholith of California. Because the solid country rock into which magma intrudes is an excellent insulator, cooling of the magma is extremely slow, and intrusive igneous rock is coarse-grained ( phaneritic). Intrusive igneous rocks are classified separately from extrusive igneous rocks, generally on the basis of their mineral content. The relative amounts of quartz, alkali feldspar, plagioclase, and feldspathoid is particularly important in classifying intrusive igneous rocks. Intrusion ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Air Gap (networking)
An air gap, air wall, air gapping or disconnected network is a network security measure employed on one or more computers to ensure that a secure computer network is physically isolated from unsecured networks, such as the public Internet or an unsecured local area network. It means a computer or network has no network interface controllers connected to other networks, with a physical or conceptual air gap, analogous to the air gap used in plumbing to maintain water quality. Use in classified settings An ''air-gapped'' computer or network is one that has no network interfaces, either wired or wireless, connected to outside networks. Many computers, even when they are not plugged into a wired network, have a wireless network interface controller (WiFi) and are connected to nearby wireless networks to access the Internet and update software. This represents a security vulnerability, so air-gapped computers have their wireless interface controller either permanently disabled ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Attack Surface
The attack surface of a software environment is the sum of the different points (for " attack vectors") where an unauthorized user (the "attacker") can try to enter data to, extract data, control a device or critical software in an environment. Keeping the attack surface as small as possible is a basic security measure. Elements of an attack surface Worldwide digital change has accelerated the size, scope, and composition of an organization's attack surface. The size of an attack surface may fluctuate over time, adding and subtracting assets and digital systems (e.g. websites, hosts, cloud and mobile apps, etc.). Attack surface sizes can change rapidly as well. Digital assets eschew the physical requirements of traditional network devices, servers, data centers, and on-premise networks. This leads to attack surfaces changing rapidly, based on the organization's needs and the availability of digital services to accomplish it. Attack surface scope also varies from organization ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Antivirus Software
Antivirus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware. Antivirus software was originally developed to detect and remove computer viruses, hence the name. However, with the proliferation of other malware, antivirus software started to protect against other computer threats. Some products also include protection from malicious URLs, spam, and phishing. History 1971–1980 period (pre-antivirus days) The first known computer virus appeared in 1971 and was dubbed the " Creeper virus". This computer virus infected Digital Equipment Corporation's ( DEC) PDP-10 mainframe computers running the TENEX operating system.From the first email to the first YouTube video: a d ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zero-day Vulnerability
A zero-day (also known as a 0-day) is a vulnerability or security hole in a computer system unknown to its developers or anyone capable of mitigating it. Until the vulnerability is remedied, threat actors can exploit it in a zero-day exploit, or zero-day attack. The term "zero-day" originally referred to the number of days since a new piece of software was released to the public, so "zero-day software" was obtained by hacking into a developer's computer before release. Eventually the term was applied to the vulnerabilities that allowed this hacking, and to the number of days that the vendor has had to fix them. Vendors who discover the vulnerability may create patches or advise workarounds to mitigate it – though users need to deploy that mitigation to eliminate the vulnerability in their systems. Zero-day attacks are severe threats. Definition Despite developers' goal of delivering a product that works entirely as intended, virtually all software and hardware contain bugs. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Business Continuity Planning
Business continuity may be defined as "the capability of an organization to continue the delivery of products or services at pre-defined acceptable levels following a disruptive incident", and business continuity planning (or business continuity and resiliency planning) is the process of creating systems of prevention and recovery to deal with potential threats to a company. In addition to prevention, the goal is to enable ongoing operations before and during execution of disaster recovery. Business continuity is the intended outcome of proper execution of both business continuity planning and disaster recovery. Several business continuity standards have been published by various standards bodies to assist in checklisting ongoing planning tasks. Business continuity requires a top-down approach to identify an organisation's minimum requirements to ensure its viability as an entity. An organization's resistance to failure is "the ability ... to withstand changes in its environmen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Zero Trust
Zero trust architecture (ZTA) or perimeterless security is a design and implementation strategy of IT systems. The principle is that users and devices should not be trusted by default, even if they are connected to a privileged network such as a corporate LAN and even if they were previously verified. ZTA is implemented by establishing identity verification, validating device compliance prior to granting access, and ensuring least privilege access to only explicitly-authorized resources. Most modern corporate networks consist of many interconnected zones, cloud services and infrastructure, connections to remote and mobile environments, and connections to non-conventional IT, such as IoT devices. The traditional approach by trusting users and devices within a notional "corporate perimeter" or via a VPN connection is commonly not sufficient in the complex environment of a corporate network. The zero trust approach advocates mutual authentication, including checking the ident ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |