|
Artificial Intelligence For IT Operations
Artificial Intelligence for IT Operations (AIOps) is a term coined by Gartner in 2016 as an industry category for machine learning analytics technology that enhances IT operations analytics. AIOps is the acronym of "Artificial Intelligence Operations". Such operation tasks include automation, performance monitoring and event correlations among others. There are two main aspects of an AIOps platform: machine learning and big data. In order to collect observational data and engagement data that can be found inside a big data platform and requires a shift away from sectionally segregated IT data, a holistic machine learning and analytics strategy is implemented against the combined IT data. The goal is to enable IT transformation, receive continuous insights which provide continuous fixes and improvements via automation. This is why AIOps can be viewed as CI/CD for core IT functions. Given the inherent nature of IT operations, which is closely tied to cloud deployment and the man ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IT Operations Analytics
In the fields of information technology (IT) and systems management, IT operations analytics (ITOA) is an approach or method to retrieve, analyze, and report data for IT operations. ITOA may apply big data analytics to large datasets to produce business insights. In 2014, Gartner predicted its use might increase revenue or reduce costs. By 2017, it predicted that 15% of enterprises will use IT operations analytics technologies. Definition IT operations analytics (ITOA) (also known as advanced operational analytics, or IT data analytics) technologies are primarily used to discover complex patterns in high volumes of often "noisy" IT system availability and performance data. Forrester Research defined IT analytics as "The use of mathematical algorithms and other innovations to extract meaningful information from the sea of raw data collected by management and monitoring technologies." Note, ITOA is different than AIOps, which focuses on applying artificial intelligence and machine lea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Augmented Reality
Augmented reality (AR) is an interactive experience that combines the real world and computer-generated content. The content can span multiple sensory modalities, including visual, auditory, haptic, somatosensory and olfactory. AR can be defined as a system that incorporates three basic features: a combination of real and virtual worlds, real-time interaction, and accurate 3D registration of virtual and real objects. The overlaid sensory information can be constructive (i.e. additive to the natural environment), or destructive (i.e. masking of the natural environment). This experience is seamlessly interwoven with the physical world such that it is perceived as an immersive aspect of the real environment. In this way, augmented reality alters one's ongoing perception of a real-world environment, whereas virtual reality completely replaces the user's real-world environment with a simulated one. Augmented reality is largely synonymous with mixed reality. There is also overlap ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
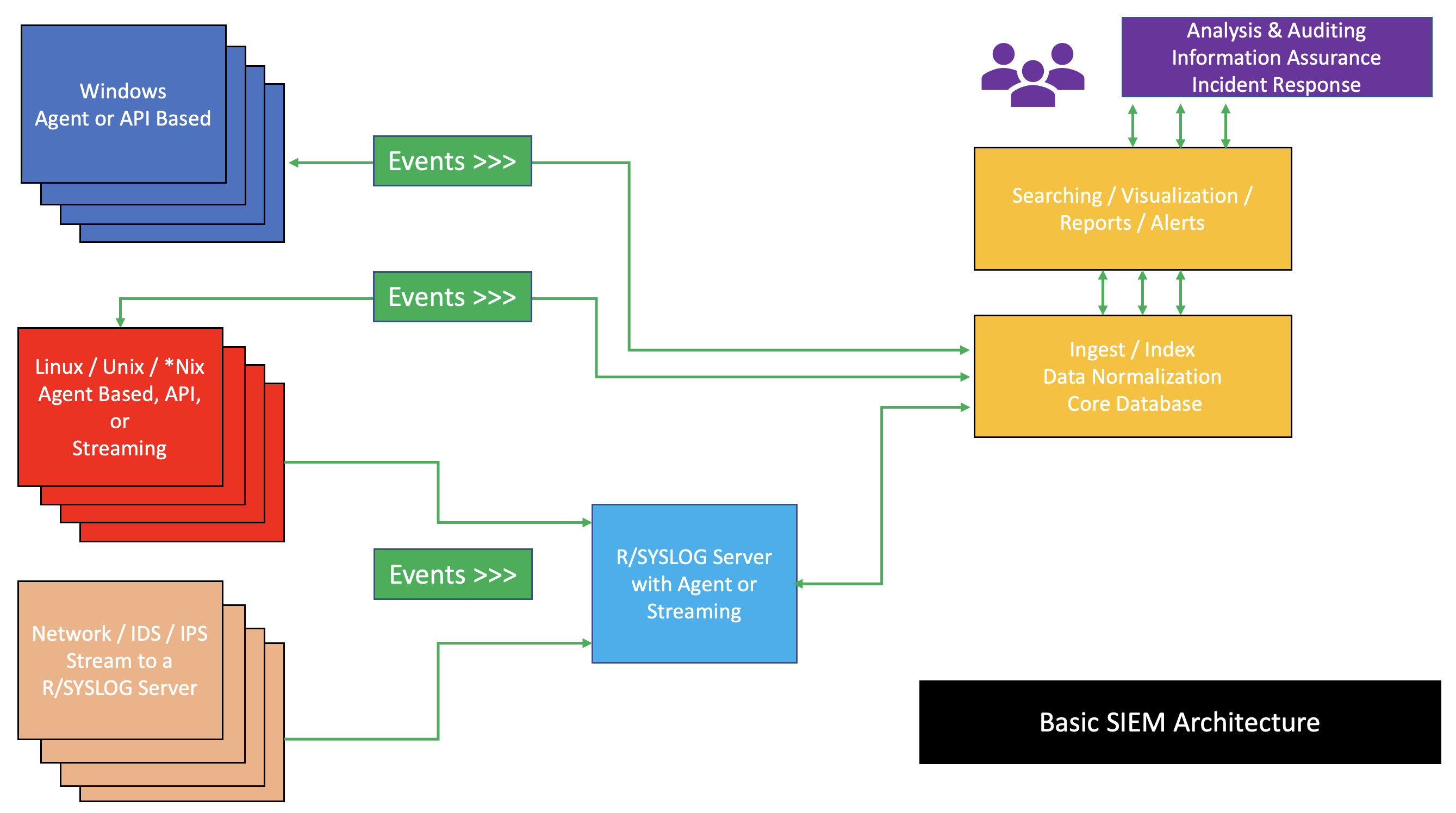
Security Information And Event Management
Security information and event management (SIEM) is a field within the field of computer security, where software products and services combine security information management (SIM) and security event management (SEM). They provide real-time analysis of security alerts generated by applications and network hardware. Vendors sell SIEM as software, as appliances, or as managed services; these products are also used to log security data and generate reports for compliance purposes. The term and the initialism SIEM was coined by Mark Nicolett and Amrit Williams of Gartner in 2005. History Monitoring system logs has grown more prevalent as complex cyber-attacks force compliance and regulatory mechanisms to mandate logging security controls within a Risk Management Framework. Logging levels of a system started with the primary function of troubleshooting system errors or debugging code compiled and run. As operating systems and networks have increased in complexity, so has the event ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Customer Support
Customer support is a range of services to assist customers in making cost effective and correct use of a product. It includes assistance in planning, installation, training, troubleshooting, maintenance, upgrading, and disposal of a product. Regarding technology products such as mobile phones, televisions, computers, software products or other electronic or mechanical goods, it is termed technical support. Phone and Emails are the primary means to offer web-based assistance for your customers when matters do not require an immediate answer. Low-cost, non-intrusive and anywhere-anytime access are some of the advantages of email-based communications. Trouble Ticketing System and CRM Applications help keep track of a series of follow-up correspondence with a particular customer. Services offered via email response management is claims processing, polling/media analysis, subscription services, troubleshooting, complaint registrations etc. Being a successful Customer Support agent ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data Center Management
Data center management is the collection of tasks performed by those responsible for managing ongoing operation of a data center This includes ''Business service management'' and planning for the future. Historically, ''data center management'' was seen as something performed by employees, with the help of tools collectively called Data Center Infrastructure Management (DCIM) tools. Both for in-house operation and outsourcing, Service-level agreements must be managed to ensure data-availability. Competition Data center management is a growing major topic for a growing list of large companies who both compete and cooperate, including: Dell, Google, HP, IBM, Intel and Yahoo. Hardware/software vendors who are willing to live with coopetition are working on projects such as "The Distributed Management Task Force" (DMTF) with a goal of learning to "more effectively manage mixed Linux, Windows and cloud environments." With the ''DMTF'' a decade old, the list of companies is growing, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Incident Management
An incident is an event that could lead to loss of, or disruption to, an organization's operations, services or functions. Incident management (IcM) is a term describing the activities of an organization to identify, analyze, and correct hazards to prevent a future re-occurrence. These incidents within a structured organization are normally dealt with by either an incident response team (IRT), an incident management team (IMT), or Incident Command System (ICS). Without effective incident management, an incident can disrupt business operations, information security, IT systems, employees, customers, or other vital business functions. Description An incident is an event that could lead to the loss of, or disruption to, an organization's operations, services or functions. Incident management (IcM) is a term describing the activities of an organization to identify, analyze, and correct hazards to prevent a future re-occurrence. If not managed, an incident can escalate into an emerg ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anomaly Detection
In data analysis, anomaly detection (also referred to as outlier detection and sometimes as novelty detection) is generally understood to be the identification of rare items, events or observations which deviate significantly from the majority of the data and do not conform to a well defined notion of normal behaviour. Such examples may arouse suspicions of being generated by a different mechanism, or appear inconsistent with the remainder of that set of data. Anomaly detection finds application in many domains including cyber security, medicine, machine vision, statistics, neuroscience, law enforcement and financial fraud to name only a few. Anomalies were initially searched for clear rejection or omission from the data to aid statistical analysis, for example to compute the mean or standard deviation. They were also removed to better predictions from models such as linear regression, and more recently their removal aids the performance of machine learning algorithms. However, ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
System Configuration
A system configuration (SC) in systems engineering defines the computers, processes, and devices that compose the system and its boundary. More generally, the system configuration is the specific definition of the elements that define and/or prescribe what a system is composed of. Alternatively, the term "system configuration" can be used to relate to a ''model'' (declarative) for abstract generalized systems. In this sense, the usage of the configuration information is not tailored to any specific usage, but stands alone as a data set. A properly-configured system avoids resource-conflict problems, and makes it easier to upgrade a system with new equipment..... Sample configuration The following is a basic SC XML System Configuration: ''Description'': This provides information about a single "site" (MyHouse) and specifies that there is one host with ''user-setup'' and ''mysql-db'' components. The host must have an account on it for a user named ''mysql'', with appropriate parame ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Business Intelligence
Business intelligence (BI) comprises the strategies and technologies used by enterprises for the data analysis and management of business information. Common functions of business intelligence technologies include reporting, online analytical processing, analytics, dashboard development, data mining, process mining, complex event processing, business performance management, benchmarking, text mining, predictive analytics, and prescriptive analytics. BI tools can handle large amounts of structured and sometimes unstructured data to help identify, develop, and otherwise create new strategic business opportunities. They aim to allow for the easy interpretation of these big data. Identifying new opportunities and implementing an effective strategy based on insights can provide businesses with a competitive market advantage and long-term stability, and help them take strategic decisions. Business intelligence can be used by enterprises to support a wide range of business decisi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Streaming Data
Streaming data is data that is continuously generated by different sources. Such data should be processed incrementally using stream processing techniques without having access to all of the data. In addition, it should be considered that concept drift may happen in the data which means that the properties of the stream may change over time. It is usually used in the context of big data in which it is generated by many different sources at high speed. Data streaming can also be explained as a technology used to deliver content to devices over the internet, and it allows users to access the content immediately, rather than having to wait for it to be downloaded. Big data is forcing many organizations to focus on storage costs, which brings interest to data lakes and data streams. A data lake refers to the storage of a large amount of unstructured and semi data, and is useful due to the increase of big data as it can be stored in such a way that firms can dive into the data lake and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Natural Language Generation
Natural language generation (NLG) is a software process that produces natural language output. In one of the most widely-cited survey of NLG methods, NLG is characterized as "the subfield of artificial intelligence and computational linguistics that is concerned with the construction of computer systems than can produce understandable texts in English or other human languages from some underlying non-linguistic representation of information". While it is widely agreed that the output of any NLG process is text, there is some disagreement on whether the inputs of an NLG system need to be non-linguistic. Common applications of NLG methods include the production of various reports, for example weather and patient reports; image captions; and chatbots. Automated NLG can be compared to the process humans use when they turn ideas into writing or speech. Psycholinguists prefer the term language production for this process, which can also be described in mathematical terms, or modeled in ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Internet Of Things
The Internet of things (IoT) describes physical objects (or groups of such objects) with sensors, processing ability, software and other technologies that connect and exchange data with other devices and systems over the Internet or other communications networks. Internet of things has been considered a misnomer because devices do not need to be connected to the public internet, they only need to be connected to a network and be individually addressable. The field has evolved due to the convergence of multiple technologies, including ubiquitous computing, commodity sensors, increasingly powerful embedded systems, as well as machine learning.Hu, J.; Niu, H.; Carrasco, J.; Lennox, B.; Arvin, F.,Fault-tolerant cooperative navigation of networked UAV swarms for forest fire monitoring Aerospace Science and Technology, 2022. Traditional fields of embedded systems, wireless sensor networks, control systems, automation (including Home automation, home and building automation), indepen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |



.jpg)