|
Alternate Instruction Set
The Alternate Instruction Set (AIS) is a second 32-bit instruction set architecture found in some x86 CPUs made by VIA Technologies. On these VIA C3 processors, the second hidden processor mode is accessed by executing the x86 instruction ALTINST (). If AIS mode has been enabled, the processor will perform a JMP EAX and begin executing AIS instructions at the address of the EAX register. Using AIS allows native access to the Centaur Technology-designed RISC core inside the processor. Instruction format The manufacturer describes the Alternate Instruction Set as "an extended set of integer, MMX, floating-point, and 3DNow! instructions along with additional registers and some more powerful instruction forms". Every AIS instruction is prefixed with the 3-byte sequence 0x8D8400 followed by the 32-bit instruction; this prefix form for the AIS instructions makes them appear to be x86 Load Effective Address (LEA) instructions. In 2018 researcher Christoper Domas reported that the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Instruction Set Architecture
In computer science, an instruction set architecture (ISA), also called computer architecture, is an abstract model of a computer. A device that executes instructions described by that ISA, such as a central processing unit (CPU), is called an ''implementation''. In general, an ISA defines the supported instructions, data types, registers, the hardware support for managing main memory, fundamental features (such as the memory consistency, addressing modes, virtual memory), and the input/output model of a family of implementations of the ISA. An ISA specifies the behavior of machine code running on implementations of that ISA in a fashion that does not depend on the characteristics of that implementation, providing binary compatibility between implementations. This enables multiple implementations of an ISA that differ in characteristics such as performance, physical size, and monetary cost (among other things), but that are capable of running the same machine code, so that ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Privilege Escalation
Privilege escalation is the act of exploiting a bug, a design flaw, or a configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user. The result is that an application with more privileges than intended by the application developer or system administrator can perform unauthorized actions. Background Most computer systems are designed for use with multiple user accounts, each of which has abilities known as privileges. Common privileges include viewing and editing files or modifying system files. Privilege escalation means users receive privileges they are not entitled to. These privileges can be used to delete files, view private information, or install unwanted programs such as viruses. It usually occurs when a system has a bug that allows security to be bypassed or, alternatively, has flawed design assumptions about how it will be used. Privilege escalation occurs in two ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
X86 Instructions
The x86 instruction set refers to the set of instructions that x86-compatible microprocessors support. The instructions are usually part of an executable program, often stored as a computer file and executed on the processor. The x86 instruction set has been extended several times, introducing wider registers and datatypes as well as new functionality. x86 integer instructions Below is the full 8086/8088 instruction set of Intel (81 instructions total). Most if not all of these instructions are available in 32-bit mode; they just operate on 32-bit registers (eax, ebx, etc.) and values instead of their 16-bit (ax, bx, etc.) counterparts. The updated instruction set is also grouped according to architecture (i386, i486, i686) and more generally is referred to as (32-bit) x86 and (64-bit) x86-64 (also known as AMD64). Original 8086/8088 instructions Added in specific Intel processors Added with 80186/ 80188 Added with 80286 Added with 80386 Compared to e ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data General Eclipse MV/8000
The Eclipse MV/8000 was the first in a family of 32-bit minicomputers produced by Data General during the 1980s. Codenamed ''Eagle'' during development, its architecture was a new 32-bit design backward compatible with the previous 16-bit Eclipse series. The development of the computer and the people who worked on it were the subject of Tracy Kidder's book ''The Soul of a New Machine''. The MV/8000 was succeeded by the MV/6000, MV/8000-II, MV/2000, MV/2500, MV/4000, MV/10000, MV15000, MV/20000, MV/30000 and MV/40000. Later models such as the MV/40000 were SMP systems with hot-swappable components. The Eclipse MV was a 32-bit CISC architecture with a 4 GB address space. The 4 GB address space was divided into eight rings of 512 MB each with a privilege mechanism mapped onto the rings. The outermost ring, ring-7, was the least privileged. The inner-most ring, ring-0, was the most privileged. The AOS/VS operating system supported the notion of lightweight "tasks" as ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Data General
Data General Corporation was one of the first minicomputer firms of the late 1960s. Three of the four founders were former employees of Digital Equipment Corporation (DEC). Their first product, 1969's Data General Nova, was a 16-bit minicomputer intended to both outperform and cost less than the equivalent from DEC, the 12-bit PDP-8. A basic Nova system cost or less than a similar PDP-8 while running faster, offering easy expandability, being significantly smaller, and proving more reliable in the field. Combined with Data General RDOS (DG/RDOS) and programming languages like Data General Business Basic, Novas provided a multi-user platform far ahead of many contemporary systems. A series of updated Nova machines were released through the early 1970s that kept the Nova line at the front of the 16-bit mini world. The Nova was followed by the Eclipse series which offered much larger memory capacity while still being able to run Nova code without modification. The Eclipse launch wa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tracy Kidder
John Tracy Kidder (born November 12, 1945) is an American writer of nonfiction books. He received the Pulitzer Prize for his ''The Soul of a New Machine'' (1981), about the creation of a new computer at Data General Corporation. He has received praise and awards for other works, including his biography of Paul Farmer, a physician and anthropologist, titled ''Mountains Beyond Mountains'' (2003). Kidder is considered a literary journalist because of the strong story line and personal voice in his writing. He has cited as his writing influences John McPhee, A. J. Liebling, and George Orwell. In a 1984 interview he said, "McPhee has been my model. He's the most elegant of all the journalists writing today, I think." Kidder wrote in a 1994 essay, "In fiction, believability may have nothing to do with reality or even plausibility. It has everything to do with those things in nonfiction. I think that the nonfiction writer's fundamental job is to make what is true believable." E ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
The Soul Of A New Machine
''The Soul of a New Machine'' is a non-fiction book written by Tracy Kidder and published in 1981. It chronicles the experiences of a computer engineering team racing to design a next-generation computer at a blistering pace under tremendous pressure. The machine was launched in 1980 as the Data General Eclipse MV/8000. The book, whose author was described by the ''New York Times'' as having "elevated it to a high level of narrative art" is "about real people working on a real computer for a real company," and it won the 1982 National Book Award for Nonfiction"National Book Awards – 1982" . Retrieved February 21, 2012. This ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
DEF CON
DEF CON (also written as DEFCON, Defcon or DC) is a hacker convention held annually in Las Vegas, Nevada. The first DEF CON took place in June 1993 and today many attendees at DEF CON include computer security professionals, journalists, lawyers, federal government employees, security researchers, students, and hackers with a general interest in software, computer architecture, hardware modification, conference badges, and anything else that can be "hacked". The event consists of several tracks of speakers about computer- and hacking-related subjects, as well as cyber-security challenges and competitions (known as hacking wargames). Contests held during the event are extremely varied, and can range from creating the longest Wi-Fi connection to finding the most effective way to cool a beer in the Nevada heat. Other contests, past and present, include lockpicking, robotics-related contests, art, slogan, coffee wars, scavenger hunt and Capture the Flag. Capture the Flag (CTF) is p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Intel 8080
The Intel 8080 (''"eighty-eighty"'') is the second 8-bit microprocessor designed and manufactured by Intel. It first appeared in April 1974 and is an extended and enhanced variant of the earlier 8008 design, although without binary compatibility.'' Electronic News'' was a weekly trade newspaper. The same advertisement appeared in the May 2, 1974 issue of ''Electronics'' magazine. The initial specified clock rate or frequency limit was 2 MHz, with common instructions using 4, 5, 7, 10, or 11 cycles. As a result, the processor is able to execute several hundred thousand instructions per second. Two faster variants, the 8080A-1 (sometimes referred to as the 8080B) and 8080A-2, became available later with clock frequency limits of 3.125 MHz and 2.63 MHz respectively. The 8080 needs two support chips to function in most applications: the i8224 clock generator/driver and the i8228 bus controller. It is implemented in N-type metal-oxide-semiconductor logic (NMOS) usin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NEC V20
The NEC V20 is a microprocessor that was designed and produced by NEC. It is both pin compatible and object code compatible with the Intel 8088, with an instruction set architecture (ISA) similar to that of the Intel 80188 with some extensions. The V20 was introduced in March 1984. Features The V20's die comprised 63,000 transistors; more than double the 29,000 of the 8088 CPU. The chip was designed for a clock duty cycle of 50%, compared to the 33% duty cycle used by the 8088. The V20 has two, 16-bit wide internal databuses, allowing two data transfers to occur concurrently. Differences like that meant that a V20 could typically complete more instructions in a given time than an Intel 8088 running at the same frequency. The V20 was fabricated in 2-micron CMOS technology. Early versions ran at speeds of 5, 8, and 10 MHz. In 1990, an upgrade to the fabrication process technology resulted in the V20H and V20HL, with improved performance and reduced power consumption. Lat ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
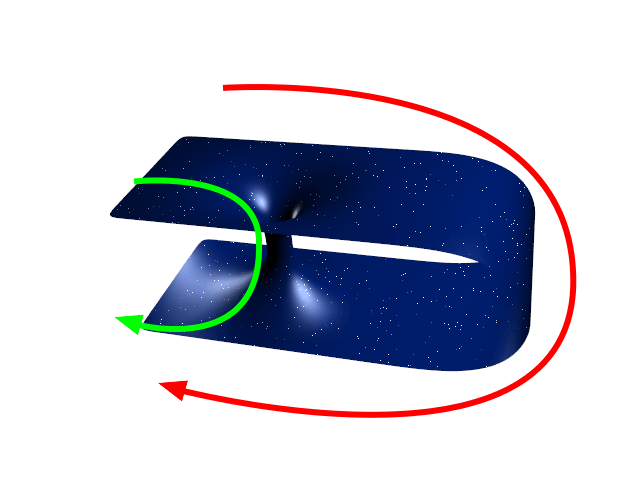
Einstein-Rosen Bridge
A wormhole ( Einstein-Rosen bridge) is a hypothetical structure connecting disparate points in spacetime, and is based on a special solution of the Einstein field equations. A wormhole can be visualized as a tunnel with two ends at separate points in spacetime (i.e., different locations, different points in time, or both). Wormholes are consistent with the general theory of relativity, but whether wormholes actually exist remains to be seen. Many scientists postulate that wormholes are merely projections of a fourth spatial dimension, analogous to how a two-dimensional (2D) being could experience only part of a three-dimensional (3D) object. Theoretically, a wormhole might connect extremely long distances such as a billion light years, or short distances such as a few meters, or different points in time, or even different universes. In 1995, Matt Visser suggested there may be many wormholes in the universe if cosmic strings with negative mass were generated in the early ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tom's Hardware
''Tom's Hardware'' is an online publication owned by Future plc and focused on technology. It was founded in 1996 by Thomas Pabst. It provides articles, news, price comparisons, videos and reviews on computer hardware and high technology. The site features coverage on CPUs, motherboards, RAM, PC cases, graphic cards, display technology, power supplies and displays, storage, smartphones, tablets, gaming, consoles, and computer peripherals. ''Tom's Hardware'' has a forum and featured blogs. History ''Tom's Hardware'' was founded in April 1996 as ''Tom's Hardware Guide'' in the United States by Thomas Pabst. It started using the domain tomshardware.com in September 1997 and was followed by several foreign language versions, including Italian, French, Finnish and Russian based on franchise agreements. While the initial testing labs were in Germany and California, much of Tom's Hardware's testing now occurs in New York and a facility in Ogden, Utah owned by its parent company. In ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |