|
Access Badge
An access badge is a credential used to gain entry to an area having automated access control entry points. Entry points may be doors, turnstiles, parking gates or other barriers. Access badges use various technologies to identify the holder of the badge to an access control system. The most common technologies are magnetic stripe, proximity, barcode, smart cards and various biometric devices. The magnetic strip ID card was invented by Forrest Parry in 1960. {{webarchive, url=https://web.archive.org/web/20111027061240/http://www.suu.edu/alumni/magazine/fall04/pdf/news.pdf , date=2011-10-27 The access badge contains a number that is read by a |
Integrated Circuit
An integrated circuit or monolithic integrated circuit (also referred to as an IC, a chip, or a microchip) is a set of electronic circuits on one small flat piece (or "chip") of semiconductor material, usually silicon. Transistor count, Large numbers of tiny MOSFETs (metal–oxide–semiconductor field-effect transistors) integrate into a small chip. This results in circuits that are orders of magnitude smaller, faster, and less expensive than those constructed of discrete electronic components. The IC's mass production capability, reliability, and building-block approach to integrated circuit design has ensured the rapid adoption of standardized ICs in place of designs using discrete transistors. ICs are now used in virtually all electronic equipment and have revolutionized the world of electronics. Computers, mobile phones and other home appliances are now inextricable parts of the structure of modern societies, made possible by the small size and low cost of ICs such as mode ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ID Card Printer
In computing, a printer is a peripheral machine which makes a persistent representation of graphics or text, usually on paper. While most output is human-readable, bar code printers are an example of an expanded use for printers. Different types of printers include 3D printers, inkjet printers, laser printers, and thermal printers. History The first computer printer designed was a mechanically driven apparatus by Charles Babbage for his difference engine in the 19th century; however, his mechanical printer design was not built until 2000. The first patented printing mechanism for applying a marking medium to a recording medium or more particularly an electrostatic inking apparatus and a method for electrostatically depositing ink on controlled areas of a receiving medium, was in 1962 by C. R. Winston, Teletype Corporation, using continuous inkjet printing. The ink was a red stamp-pad ink manufactured by Phillips Process Company of Rochester, NY under the name Clear Prin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Fortification
A fortification is a military construction or building designed for the defense of territories in warfare, and is also used to establish rule in a region during peacetime. The term is derived from Latin ''fortis'' ("strong") and ''facere'' ("to make"). From very early history to modern times, defensive walls have often been necessary for cities to survive in an ever-changing world of invasion and conquest. Some settlements in the Indus Valley civilization were the first small cities to be fortified. In ancient Greece, large stone walls had been built in Mycenaean Greece, such as the ancient site of Mycenae (famous for the huge stone blocks of its ' cyclopean' walls). A Greek '' phrourion'' was a fortified collection of buildings used as a military garrison, and is the equivalent of the Roman castellum or English fortress. These constructions mainly served the purpose of a watch tower, to guard certain roads, passes, and borders. Though smaller than a real fortress, th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Electronic Lock
An electronic lock (or electric lock) is a locking device which operates by means of electric current. Electric locks are sometimes stand-alone with an electronic control assembly mounted directly to the lock. Electric locks may be connected to an access control system, the advantages of which include: key control, where keys can be added and removed without re-keying the lock cylinder; fine access control, where time and place are factors; and transaction logging, where activity is recorded. Electronic locks can also be remotely monitored and controlled, both to lock and to unlock. Operation Electric locks use magnets, solenoids, or motors to actuate the lock by either supplying or removing power. Operating the lock can be as simple as using a switch, for example an apartment intercom door release, or as complex as a biometric based access control system. There are two basic types of locks: "preventing mechanism" or operation mechanism. Types Electromagnetic lock The m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Door Security
The term door security or door security gate may refer to any of a range of measures used to strengthen doors against door breaching, ram-raiding and lock picking, and prevent crimes such as burglary and home invasions. Door security is used in commercial and government buildings, as well as in residential settings. Some strengthened doors function as fire doors to prevent or inhibit the spread of fire. Security devices Alarms Alarms — designed to warn of burglaries. Locks * Smart locks can be used to limit door access to only people with an electronic key fob or near-field communication device, like a smartphone. These devices are popular with landlords, who can enable and disable digital access without physically mailing out keys. The locks can log the times of entry, and can trigger an alarm if they are struck during a break-in attempt. * Deadbolts — unlike common spring latches, the locking mechanism of these typically prevents the bolt from being retracted by ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Security
Computer security, cybersecurity (cyber security), or information technology security (IT security) is the protection of computer systems and networks from attack by malicious actors that may result in unauthorized information disclosure, theft of, or damage to hardware, software, or data, as well as from the disruption or misdirection of the services they provide. The field has become of significance due to the expanded reliance on computer systems, the Internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices, including smartphones, televisions, and the various devices that constitute the Internet of things (IoT). Cybersecurity is one of the most significant challenges of the contemporary world, due to both the complexity of information systems and the societies they support. Security is of especially high importance for systems that govern large-scale systems with far-reaching physical effects, such as power distribu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
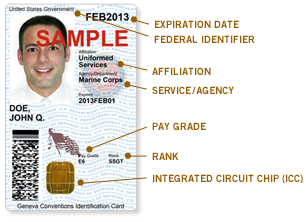
Common Access Card
The Common Access Card, also commonly referred to as the CAC is a smart card about the size of a credit card. It is the standard identification for Active Duty United States Defense personnel, to include the Selected Reserve and National Guard, United States Department of Defense (DoD) civilian employees, United States Coast Guard (USCG) civilian employees and eligible DoD and USCG contractor personnel. It is also the principal card used to enable physical access to buildings and controlled spaces, and it provides access to defense computer networks and systems. It also serves as an identification card under the Geneva Conventions (especially the Third Geneva Convention). In combination with a personal identification number, a CAC satisfies the requirement for two-factor authentication: something the user knows combined with something the user has. The CAC also satisfies the requirements for digital signature and data encryption technologies: authentication, integrity and n ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Card Printer
Card or The Card may refer to: * Various types of plastic cards: **By type ***Magnetic stripe card ***Chip card *** Digital card **By function ***Payment card ****Credit card **** Debit card ****EC-card ****Identity card ****European Health Insurance Card ****Driver's license * Playing card, a card used in games * Printed circuit board * Punched card, a piece of stiff paper that holds digital data represented by the presence or absence of holes in predefined positions. *In communications ** Postcard ** Greeting card, an illustrated piece of card stock featuring an expression of friendship or other sentiment * \operatorname, in mathematical notation, a function that returns the cardinality of a set * Card, a tool for carding, the cleaning and aligning of fibers * Sports terms ** Card (sports), the lineup of the matches in an event ** Penalty card As a proper name People with the name * Card (surname) Companies * Cards Corp, a South Korean internet company Arts and entertainment * ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Biometrics
Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance. Biometric identifiers are the distinctive, measurable characteristics used to label and describe individuals. Biometric identifiers are often categorized as physiological characteristics which are related to the shape of the body. Examples include, but are not limited to fingerprint, palm veins, face recognition, DNA, palm print, hand geometry, iris recognition, retina, odor/scent, voice, shape of ears and gait. Behavioral characteristics are related to the pattern of behavior of a person, including but not limited to mouse movement, typing rhythm, gait, signature, behavioral profiling, and credentials. Some researchers have coined the term behaviometrics to describe the latter cl ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |

.jpg)