|
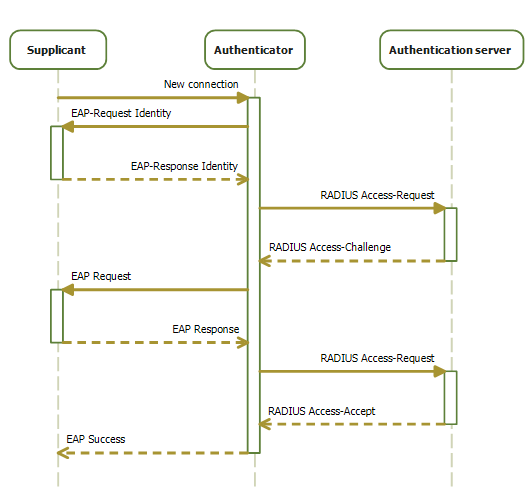
802.1x
IEEE 802.1X is an IEEE Standard for port-based Network Access Control (PNAC). It is part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a Local area network, LAN or Wireless LAN, WLAN. IEEE 802.1X defines the encapsulation of the Extensible Authentication Protocol (EAP) over wired IEEE 802 networksand over 802.11 wireless networks, which is known as "EAP over LAN" or EAPOL. EAPOL was originally specified for IEEE 802.3 Ethernet, IEEE 802.5 Token Ring, and Fiber Distributed Data Interface, FDDI (ANSI X3T9.5/X3T12 and ISO 9314) in 802.1X-2001, but was extended to suit other IEEE 802 LAN technologies such as IEEE 802.11 wireless in 802.1X-2004. The EAPOL was also modified for use with IEEE 802.1AE ("MACsec") and IEEE 802.1#802.1AR, IEEE 802.1AR (Secure Device Identity, DevID) in 802.1X-2010IEEE 802.1X-2010, page ivIEEE 802.1X-2010, § 5 to support service identification and optional point to point encryption ove ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Supplicant (computer)
In computer networking, a supplicant is an entity at one end of a point-to-point LAN segment that seeks to be authenticated by an authenticator attached to the other end of that link. The IEEE 802.1X standard uses the term "supplicant" to refer either to hardware or to software. In practice, a supplicant is a software application installed on an end-user's computer. The user invokes the supplicant and submits credentials to connect the computer to a secure network. If the authentication succeeds, the authenticator typically allows the computer to connect to the network. A supplicant, in some contexts, refers to a user or to a client in a network environment seeking to access network resources secured by the IEEE 802.1X authentication mechanism. But saying "user" or "client" over-generalizes; in reality, the interaction takes place through a personal computer, an Internet protocol (IP) phone, or similar network device. Each of these must run supplicant software that initiates or ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Extensible Authentication Protocol
Extensible Authentication Protocol (EAP) is an authentication framework frequently used in network and internet connections. It is defined in , which made obsolete, and is updated by . EAP is an authentication framework for providing the transport and usage of material and parameters generated by EAP methods. There are many methods defined by RFCs, and a number of vendor-specific methods and new proposals exist. EAP is not a wire protocol; instead it only defines the information from the interface and the formats. Each protocol that uses EAP defines a way to encapsulate by the user EAP messages within that protocol's messages. EAP is in wide use. For example, in IEEE 802.11 (WiFi) the WPA and WPA2 standards have adopted IEEE 802.1X (with various EAP types) as the canonical authentication mechanism. Methods EAP is an authentication framework, not a specific authentication mechanism. It provides some common functions and negotiation of authentication methods called EAP methods. Ther ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wireless LAN
A wireless LAN (WLAN) is a wireless computer network A wireless network is a computer network that uses wireless data connections between network nodes. Wireless networking is a method by which homes, telecommunications networks and business installations avoid the costly process of introducing c ... that links two or more devices using wireless communication to form a local area network (LAN) within a limited area such as a home, school, computer laboratory, campus, or office building. This gives users the ability to move around within the area and remain connected to the network. Through a Gateway (telecommunications), gateway, a WLAN can also provide a connection to the wider Internet. Wireless LANs based on the IEEE 802.11 standards are the most widely used computer networks in the world. These are commonly called Wi-Fi, which is a trademark belonging to the Wi-Fi Alliance. They are used for home and small office networks that link together laptop computers, printer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Network Access Control
Network access control (NAC) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host intrusion prevention, and vulnerability assessment), user or system authentication and network security enforcement. Description Network access control is a computer networking solution that uses a set of protocols to define and implement a policy that describes how to secure access to network nodes by devices when they initially attempt to access the network. NAC might integrate the automatic remediation process (fixing non-compliant nodes before allowing access) into the network systems, allowing the network infrastructure such as routers, switches and firewalls to work together with back office servers and end user computing equipment to ensure the information system is operating securely before interoperability is allowed. A basic form of NAC is the 802.1X standard. Network access control aims to do exactly what the name implies— ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IOS (Apple)
iOS (formerly iPhone OS) is a mobile operating system created and developed by Apple Inc. exclusively for its hardware. It is the operating system that powers many of the company's mobile devices, including the iPhone; the term also includes the system software for iPads predating iPadOS—which was introduced in 2019—as well as on the iPod Touch devices—which were discontinued in mid-2022. It is the world's second-most widely installed mobile operating system, after Android. It is the basis for three other operating systems made by Apple: iPadOS, tvOS, and watchOS. It is proprietary software, although some parts of it are open source under the Apple Public Source License and other licenses. Unveiled in 2007 for the first-generation iPhone, iOS has since been extended to support other Apple devices such as the iPod Touch (September 2007) and the iPad (introduced: January 2010; availability: April 2010.) , Apple's App Store contains more than 2.1 million iOS ap ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Android (operating System)
Android is a mobile operating system based on a modified version of the Linux kernel and other open-source software, designed primarily for touchscreen mobile devices such as smartphones and tablets. Android is developed by a consortium of developers known as the Open Handset Alliance and commercially sponsored by Google. It was unveiled in November 2007, with the first commercial Android device, the HTC Dream, being launched in September 2008. Most versions of Android are proprietary. The core components are taken from the Android Open Source Project (AOSP), which is free and open-source software (FOSS) primarily licensed under the Apache License. When Android is installed on devices, the ability to modify the otherwise free and open-source software is usually restricted, either by not providing the corresponding source code or by preventing reinstallation through technical measures, thus rendering the installed version proprietary. Most Android devices ship with additional ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ChromeOS
ChromeOS, sometimes stylized as chromeOS and formerly styled as Chrome OS, is a Linux-based operating system designed by Google. It is derived from the open-source ChromiumOS and uses the Google Chrome web browser as its principal user interface. Google announced the project in July 2009, initially describing it as an operating system where applications and user data would reside in the Cloud computing, cloud. ChromeOS was used primarily to run web applications. All ChromiumOS and ChromeOS versions support progressive web applications (such as Google Docs or Microsoft Office 365), as well as web browser extensions (which can resemble native applications). ChromeOS (but not ChromiumOS) from 2016 onwards can also run Android (operating system), Android applications from the Google Play Store, Play Store. Since 2018, ChromiumOS/ChromeOS version 69 onwards also support Linux applications, which are executed in a lightweight virtual machine with a Debian Linux environment. The ope ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IPod Touch
The iPod Touch (stylized as iPod touch) is a discontinued line of iOS-based mobile devices designed and marketed by Apple Inc. with a touchscreen-controlled user interface. As with other iPod models, the iPod Touch can be used as a music player and a handheld gaming device, but can also be used as a digital camera, a web browser and for messaging. It is similar in design to the iPhone, but it connects to the Internet only through Wi-Fi and does not use cellular network data, so it is not a smartphone. The iPod Touch was introduced in 2007; some 100 million iPod Touch units were sold by May 2013. The final generation of iPod Touch, released on May 28, 2019, is the seventh-generation model. iPod Touch models were sold by storage space and color; all models of the same generation typically offered identical features, performance, and operating system upgrades. An exception was the fifth generation, in which the low-end (16 GB) model was initially sold without a rea ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
802-1X
8 (eight) is the natural number following 7 and preceding 9. In mathematics 8 is: * a composite number, its proper divisors being , , and . It is twice 4 or four times 2. * a power of two, being 2 (two cubed), and is the first number of the form , being an integer greater than 1. * the first number which is neither prime nor semiprime. * the base of the octal number system, which is mostly used with computers. In octal, one digit represents three bits. In modern computers, a byte is a grouping of eight bits, also called an octet. * a Fibonacci number, being plus . The next Fibonacci number is . 8 is the only positive Fibonacci number, aside from 1, that is a perfect cube. * the only nonzero perfect power that is one less than another perfect power, by Mihăilescu's Theorem. * the order of the smallest non-abelian group all of whose subgroups are normal. * the dimension of the octonions and is the highest possible dimension of a normed division algebra. * the first number ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wpa Supplicant
wpa_supplicant is a free software implementation of an IEEE 802.11i supplicant for Linux, FreeBSD, NetBSD, QNX, AROS, Microsoft Windows, Solaris, OS/2 (including ArcaOS and eComStation) and Haiku. In addition to being a WPA3 and WPA2 supplicant, it also implements WPA and older wireless LAN security protocols. Features Features include: * WPA-PSK and WPA2-PSK ("WPA-Personal", pre-shared key) *WPA3 * WPA with EAP ("WPA-Enterprise", for example with RADIUS authentication server) * RSN: PMKSA caching, pre-authentication * IEEE 802.11r * IEEE 802.11w * Wi-Fi Protected Setup ( WPS) Included with the supplicant are a GUI and a command-line utility for interacting with the running supplicant. From either of these interfaces it is possible to review a list of currently visible networks, select one of them, provide any additional security information needed to authenticate with the network (for example, a passphrase, or username and password) and add it to the preference list ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Xsupplicant
Xsupplicant is a supplicant that allows a workstation to authenticate with a RADIUS server using 802.1X and the Extensible Authentication Protocol (EAP). It can be used for computers with wired or wireless LAN connections to complete a strong authentication before joining the network and supports the dynamic assignment of WEP keys. Overview Xsupplicant up to version 1.2.8 was designed to run on Linux clients as a command line utility. Version 1.3.X and greater are designed to run on Windows XP and are currently being ported to Linux/BSD systems, and include a robust graphical user interface, and also includes Network Access Control (NAC) functionality from Trusted Computing Group's Trusted Network Connect NAC. Xsupplicant was chosen by the OpenSea Alliance, dedicated to developing, promoting, and distributing an open source 802.1X supplicant. Xsupplicant supports the following EAP types: * EAP-MD5 * LEAP * EAP-MSCHAPv2 * EAP-OTP * EAP-PEAP (v0 and v1) * EAP-SIM * EAP-TLS * ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |


.jpg)


