|
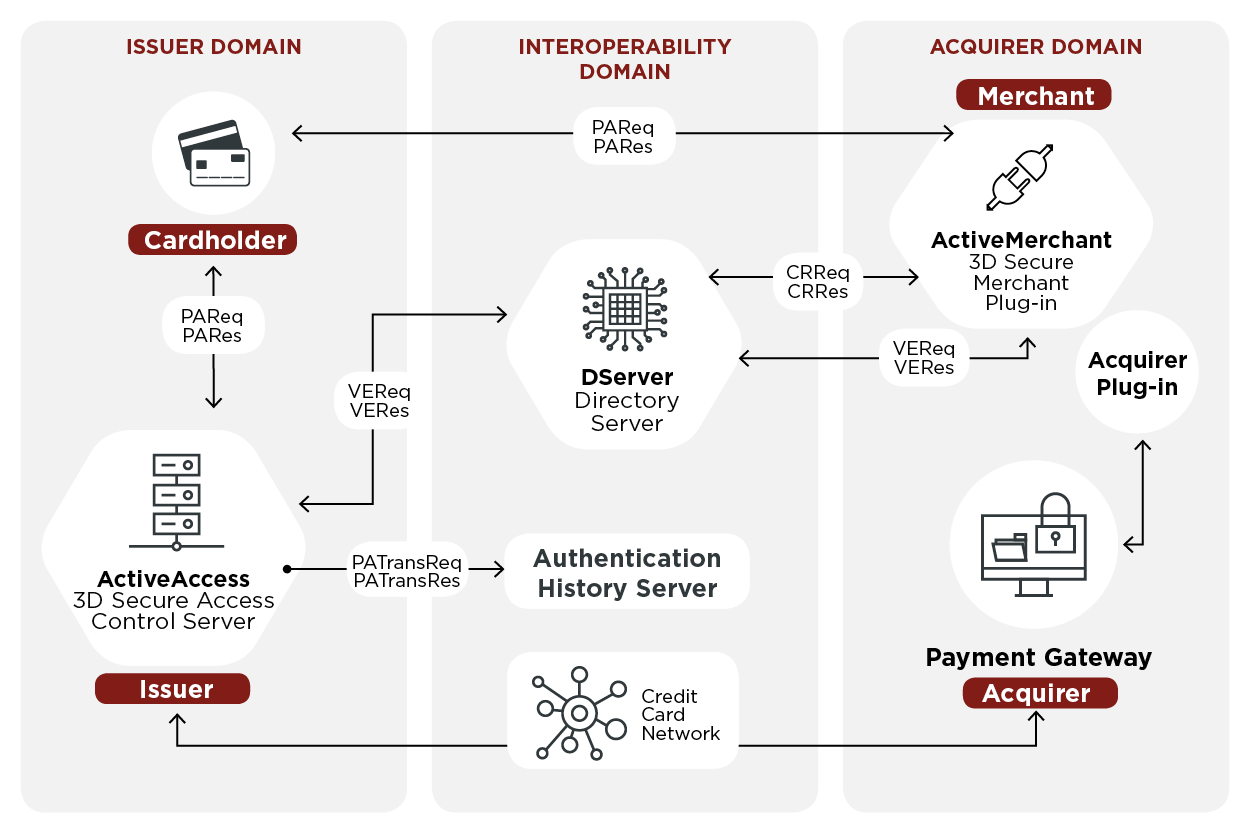
3D Secure
3-D Secure is a protocol designed to be an additional security layer for online credit and debit card transactions. The name refers to the "three domains" which interact using the protocol: the merchant/acquirer domain, the issuer domain, and the interoperability domain. Originally developed in the autumn of 1999 by Celo Communications AB (later Gemplus, Gemalto and now Thales Group) for Visa Inc. in a project named "p42" ("p" from Pole vault as the project was a big challenge and "42" as the answer from the book ''The Hitchhiker's Guide to the Galaxy''). A new updated version was developed by Gemplus between 2000-2001. In 2001 Arcot Systems (now CA Technologies) and Visa Inc. with the intention of improving the security of Internet payments, and offered to customers under the Verified by Visa brand (later rebranded as Visa Secure). Services based on the protocol have also been adopted by Mastercard as SecureCode, by Discover as ProtectBuy, by JCB International as J/Secure, and ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Credit Card
A credit card is a payment card issued to users (cardholders) to enable the cardholder to pay a merchant for goods and services based on the cardholder's accrued debt (i.e., promise to the card issuer to pay them for the amounts plus the other agreed charges). The card issuer (usually a bank or credit union) creates a revolving account and grants a line of credit to the cardholder, from which the cardholder can borrow money for payment to a merchant or as a cash advance. There are two credit card groups: consumer credit cards and business credit cards. Most cards are plastic, but some are metal cards (stainless steel, gold, palladium, titanium), and a few gemstone-encrusted metal cards. A regular credit card is different from a charge card, which requires the balance to be repaid in full each month or at the end of each statement cycle. In contrast, credit cards allow the consumers to build a continuing balance of debt, subject to interest being charged. A credit car ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Text Messaging
Text messaging, or texting, is the act of composing and sending electronic messages, typically consisting of alphabetic and numeric characters, between two or more users of mobile devices, desktops/laptops, or another type of compatible computer. Text messages may be sent over a cellular network, or may also be sent via an Internet connection. The term originally referred to messages sent using the Short Message Service (SMS). It has grown beyond alphanumeric text to include multimedia messages using the Multimedia Messaging Service (MMS) containing digital images, videos, and sound content, as well as ideograms known as emoji ( happy faces, sad faces, and other icons), and instant messenger applications (usually the term is used when on mobile devices). Text messages are used for personal, family, business and social purposes. Governmental and non-governmental organizations use text messaging for communication between colleagues. In the 2010s, the sending of short informal mes ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Strong Customer Authentication
Strong customer authentication (SCA) is a requirement of the EU Revised Directive on Payment Services (PSD2) on payment service providers within the European Economic Area. The requirement ensures that electronic payments are performed with multi-factor authentication, to increase the security of electronic payments. Physical card transactions already commonly have what could be termed strong customer authentication in the EU (Chip and PIN), but this has not generally been true for Internet transactions across the EU prior to the implementation of the requirement, and many contactless card payments do not use a second authentication factor. The SCA requirement came into force on 14 September 2019. However, with the approval of the European Banking Authority, several EEA countries have announced that their implementation will be temporarily delayed or phased, with a final deadline set for 31 December 2020. Requirement Article 97(1) of the directive requires that payment service ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Puerto Rico Department Of Consumer Affairs
The Puerto Rico Department of Consumer Affairs (PRDCA) or (DACO in Spanish)— is the executive department of the government of Puerto Rico responsible of defending and protecting consumers in the U.S. Commonwealth. The Department is headed by a Cabinet-level Secretary, appointed by the Governor and subject to the advice and consent of the Senate.Notice of public hearings amendments to regulation No. 45 for the control of prices of fuel sales in Puerto Rico " Puerto Rico Department of Consumer Affairs. Retrieved on August 23, 2010. History The Department was created by Law 5 of April 23, 1973http://www.gobierno.pr/GPRPortal/StandAlone/AgencyInformation.aspx?Fil ...[...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Puerto Rico
Puerto Rico (; abbreviated PR; tnq, Boriken, ''Borinquen''), officially the Commonwealth of Puerto Rico ( es, link=yes, Estado Libre Asociado de Puerto Rico, lit=Free Associated State of Puerto Rico), is a Caribbean island and Unincorporated territories of the United States, unincorporated territory of the United States. It is located in the northeast Caribbean Sea, approximately southeast of Miami, Florida, between the Dominican Republic and the United States Virgin Islands, U.S. Virgin Islands, and includes the eponymous main island and several smaller islands, such as Isla de Mona, Mona, Culebra, Puerto Rico, Culebra, and Vieques, Puerto Rico, Vieques. It has roughly 3.2 million residents, and its Capital city, capital and Municipalities of Puerto Rico, most populous city is San Juan, Puerto Rico, San Juan. Spanish language, Spanish and English language, English are the official languages of the executive branch of government, though Spanish predominates. Puerto Rico ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Unincorporated Territories Of The United States
Territories of the United States are sub-national administrative divisions overseen by the federal government of the United States. The various American territories differ from the U.S. states and tribal reservations as they are not sovereign entities. In contrast, each state has a sovereignty separate from that of the federal government and each federally recognized Native American tribe possesses limited tribal sovereignty as a "dependent sovereign nation". Territories are classified by incorporation and whether they have an "organized" government through an organic act passed by the Congress. American territories are under American sovereignty and, consequently, may be treated as part of the United States ''proper'' in some ways and not others (i.e., territories belong to, but are not considered to be a part of, the United States). Unincorporated territories in particular are not considered to be integral parts of the United States, and the Constitution of the United St ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Man-in-the-middle Attack
In cryptography and computer security, a man-in-the-middle, monster-in-the-middle, machine-in-the-middle, monkey-in-the-middle, meddler-in-the-middle, manipulator-in-the-middle (MITM), person-in-the-middle (PITM) or adversary-in-the-middle (AiTM) attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that they are directly communicating with each other, as the attacker has inserted themselves between the two parties. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker wit ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Question
A security question is form of shared secret used as an authenticator. It is commonly used by banks, cable companies and wireless providers as an extra security layer. History Financial institutions have used questions to authenticate customers since at least the early 20th century. In a 1906 speech at a meeting of a section of the American Bankers Association, Baltimore banker William M. Hayden described his institution's use of security questions as a supplement to customer signature records. He described the signature cards used in opening new accounts, which had spaces for the customer's birthplace, "residence," mother's maiden name, occupation and age. Hayden noted that some of these items were often left blank and that the "residence" information was used primarily to contact the customer, but the mother's maiden name was useful as a "strong test of identity." Although he observed that it was rare for someone outside the customer's family to try to withdraw money from a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
HTML Element
An HTML element is a type of HTML (HyperText Markup Language) document component, one of several types of HTML nodes (there are also text nodes, comment nodes and others). The first used version of HTML was written by Tim Berners-Lee in 1993 and there have since been many versions of HTML. The most commonly used version is HTML 4.01, which became official standard in December 1999. An HTML document is composed of a tree of simple HTML nodes, such as text nodes, and HTML elements, which add semantics and formatting to parts of document (e.g., make text bold, organize it into paragraphs, lists and tables, or embed hyperlinks and images). Each element can have HTML attributes specified. Elements can also have content, including other elements and text. Concepts Elements vs. tags As is generally understood, the position of an element is indicated as spanning from a start tag and is terminated by an end tag. This is the case for many, but not all, elements within an HTML docume ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Chip Authentication Program
250px, A Gemalto EZIO CAP device with Barclays PINsentry styling The Chip Authentication Program (CAP) is a MasterCard initiative and technical specification for using EMV banking smartcards for authenticating users and transactions in online and telephone banking. It was also adopted by Visa as Dynamic Passcode Authentication (DPA). The CAP specification defines a handheld device (''CAP reader'') with a smartcard slot, a numeric keypad, and a display capable of displaying at least 12 characters (e.g., a starburst display). Banking customers who have been issued a CAP reader by their bank can insert their Chip and PIN (EMV) card into the CAP reader in order to participate in one of several supported authentication protocols. CAP is a form of two-factor authentication as both a smartcard and a valid PIN must be present for a transaction to succeed. Banks hope that the system will reduce the risk of unsuspecting customers entering their details into fraudulent websites after reading s ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Token
A security token is a peripheral device used to gain access to an electronically restricted resource. The token is used in addition to or in place of a password. It acts like an electronic key to access something. Examples of security tokens include wireless keycards used to open locked doors, or in the case of a customer trying to access their bank account online, bank-provided tokens can prove that the customer is who they claim to be. Some security tokens may store cryptographic keys that may be used to generate a digital signature, or biometric data, such as fingerprint details. Some may also store passwords. Some designs incorporate tamper resistant packaging, while others may include small keypads to allow entry of a PIN or a simple button to start a generating routine with some display capability to show a generated key number. Connected tokens utilize a variety of interfaces including USB, near-field communication (NFC), radio-frequency identification (RFID), or Bluetoo ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Card Reader
A card reader is a data input device that reads data from a card-shaped storage medium. The first were punched card readers, which read the paper or cardboard punched cards that were used during the first several decades of the computer industry to store information and programs for computer systems. Modern card readers are electronic devices that can read plastic cards embedded with either a barcode, magnetic strip, computer chip or another storage medium. A memory card reader is a device used for communication with a smart card or a memory card. A magnetic card reader is a device used to read magnetic stripe cards, such as credit cards. A business card reader is a device used to scan and electronically save printed business cards. Smart card readers A smart card reader is an electronic device that reads smart cards and can be found in the following form: * Keyboards with a built-in card reader * External devices and internal drive bay card reader devices for personal com ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |