Shadow Table on:
[Wikipedia]
[Google]
[Amazon]
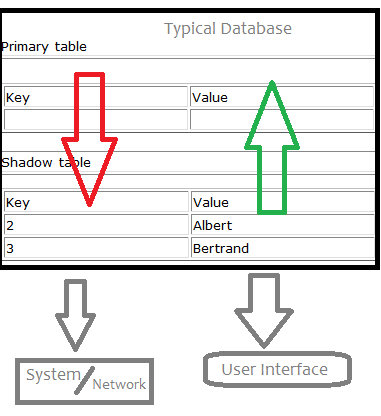 Shadow tables are
Shadow tables are
After 50 days, with this backup system, there would be 50 copies of the same table, # With shadow tables, one could create an empty "shadow table" of that table and use a program that inserts a copy of a row into the shadow table every time that row gets deleted from the primary table.
After 50 days using the shadow table system in the worst-case scenario, there would be one copy of the primary table, assuming every row in the primary table got deleted.
Virtualization: Architectural Considerations And Other Evaluation Criteria
Object-oriented programming
 Shadow tables are
Shadow tables are objects
Object may refer to:
General meanings
* Object (philosophy), a thing, being, or concept
** Object (abstract), an object which does not exist at any particular time or place
** Physical object, an identifiable collection of matter
* Goal, an ai ...
in computer science
Computer science is the study of computation, information, and automation. Computer science spans Theoretical computer science, theoretical disciplines (such as algorithms, theory of computation, and information theory) to Applied science, ...
used to improve the way machines, networks and programs handle information. More specifically, a shadow table is an object that is read and written by a processor and contains data similar to (in the same format as) its primary table, which is the table it's "shadowing". Shadow tables usually contain data that is relevant to the operation and maintenance of its primary table, but not within the subset of data required for the primary table to exist. Shadow tables are related to the data type "trails" in data storage systems. Trails are very similar to shadow tables but instead of storing identically formatted information that is different (like shadow tables), they store a history of modifications and functions operated on a table.
History
Shadow tables, as an abstract concept, have been used since the beginning of modern computing. However, widespread usage of the specific phrase "shadow table" began whenrelational database management system
A relational database (RDB) is a database based on the relational model of data, as proposed by E. F. Codd in 1970.
A Relational Database Management System (RDBMS) is a type of database management system that stores data in a structured for ...
s (RDBMS) became widely used in the 1970s.
The initial usage of relational DBMs for commercial purposes lead to the term "shadow tables" becoming widespread. A relational DBM uses related data fields (columns) to correlate information between tables. For example, two tables, transaction_user and transaction_amount, would both contain the column "key", and keys between tables would match, making it easy to find both the user and the amount of a specific transaction if the key is known. This relational technology allowed people to correlate information stored in a primary table and its shadow.
Applications
Since shadow tables are such an abstract concept, their applications remain in the realm of computer science. Although their usage may not be specifically declared as "shadow table(s)", the concept remains the same. Shadow tables are usually used in order to improve the performance, capacity, and ability of an existing computer/network system. In most applications, shadow tables are usually a carbon copy of their primary tables' structure, but with unique data.Theoretical application
Since shadow tables are a specific type of object in computer science, the applications vary greatly, because their application depends on what data is stored in the shadow table and how that data is used. The following is a list of general, abstract applications for shadow tables that span all real-world applications. * Storage - The storage of a data entry in a shadow table that would have normally been deleted or modified. * Encapsulation - The placement of data within a shadow table in order to separate a set of data from another. *Modularity
Modularity is the degree to which a system's components may be separated and recombined, often with the benefit of flexibility and variety in use. The concept of modularity is used primarily to reduce complexity by breaking a system into varying ...
- The placement of data within a shadow table to make modification and handling of the data easier.
Engineering Applications
When shadow tables are used to solve current problems in today's computer/network systems, usually a combination of more than one of the aforementioned theoretical/abstract applications of shadow tables are used. The following list is a very tiny subset of all real-world applications of shadow tables and is only shown to give an example of common applications of shadow tables.Database management systems
Database management system
In computing, a database is an organized collection of data or a type of data store based on the use of a database management system (DBMS), the software that interacts with end users, applications, and the database itself to capture and an ...
s (DBMS) are software that handle the maintenance, security, and manipulation of data tables. Well known and widely used examples of DBMS' are SQL Server, MySQL
MySQL () is an Open-source software, open-source relational database management system (RDBMS). Its name is a combination of "My", the name of co-founder Michael Widenius's daughter My, and "SQL", the acronym for Structured Query Language. A rel ...
, Oracle and PostgreSQL
PostgreSQL ( ) also known as Postgres, is a free and open-source software, free and open-source relational database management system (RDBMS) emphasizing extensibility and SQL compliance. PostgreSQL features transaction processing, transactions ...
. Each of these DBMS' create a virtual "environment" in which tables of data are held and can be read and written to via a specific type of programming language known as a query language
A query language, also known as data query language or database query language (DQL), is a computer language used to make queries in databases and information systems. In database systems, query languages rely on strict theory to retrieve informa ...
. Query languages specialize in the simple modification or retrieval of large and specific amounts of data. Most modern DBMS' specifically support SQL
Structured Query Language (SQL) (pronounced ''S-Q-L''; or alternatively as "sequel")
is a domain-specific language used to manage data, especially in a relational database management system (RDBMS). It is particularly useful in handling s ...
(a specific type of query language). Using SQL, one can easily create tables that share the same structure as already existing tables. SQL can also get data written to these new tables, creating a shadow table. Shadow tables are often used with DBMS' to improve efficiency by preventing redundant operations being performed by the DBM. Shadow tables are also easy to implement in most modern DBMS' because they do not affect the original data, so the way the databases and applications accessing them work together is not affected, unless desired.
For example, shadow tables could be used in an efficient backup system that supports large data tables that rarely change.
# Without shadow tables, one could create a program that simply saves a version of that table every day.After 50 days, with this backup system, there would be 50 copies of the same table, # With shadow tables, one could create an empty "shadow table" of that table and use a program that inserts a copy of a row into the shadow table every time that row gets deleted from the primary table.
After 50 days using the shadow table system in the worst-case scenario, there would be one copy of the primary table, assuming every row in the primary table got deleted.
Interfacing
Interfacing
Interfacing is a textile used on the unseen or "wrong" side of fabrics to make an area of a garment more rigid.
Interfacings can be used to:
*stiffen or add body to fabric, such as the interfacing used in shirt collars and cuffs
*strengthen ...
is the process of using "layers" to simplify the communications between technologies and between people and technologies. One example of layered interfacing is the buttons and menus used by home computer operating systems. These graphical objects exist as a link to the underlying "buttons" of the operating system
An operating system (OS) is system software that manages computer hardware and software resources, and provides common daemon (computing), services for computer programs.
Time-sharing operating systems scheduler (computing), schedule tasks for ...
. The command console is one level below these graphical objects as it gives you an even closer link to the underlying functions of the operating system.
Shadow tables are often used as layers between the end-user and the database. For example, if a user logs into his/her bank account and requests a history of all his/her past transactions, the database usually stores all transactions for all users in one huge table and distinguishes the parties involved in each transaction in one specific column of that table. At this point the server has two options:
# The database can send the whole transactions table.
# The database can send a shadow table that only contains the transactions involving the user that requested his/her transaction history.
The second option is usually more favorable because it saves bandwidth and processing power on the user's end. It also keeps others' transaction data secure.
Operating system virtualization
Operating system virtualization is the process of simulating the operation of a computer within another computer. This technique is useful for someone who wants to run more than one type of operating system on his/her PC concurrently.Shadow page tables
x86 virtualization is the use of hardware-assisted virtualization capabilities on an x86/x86-64 CPU.
In the late 1990s x86 virtualization was achieved by complex software techniques, necessary to compensate for the processor's lack of hardware-as ...
are often used in simulating more than one operating system on a single set of memory and processor. A page table
A page table is a data structure used by a virtual memory system in a computer to store mappings between virtual addresses and physical addresses. Virtual addresses are used by the program executed by the accessing process, while physical addr ...
is used by an operating system to map the virtual memory
In computing, virtual memory, or virtual storage, is a memory management technique that provides an "idealized abstraction of the storage resources that are actually available on a given machine" which "creates the illusion to users of a ver ...
, the actual memory used by programs and the operating system to store information, to its location on the physical memory
Computer data storage or digital data storage is a technology consisting of computer components and recording media that are used to retain digital data. It is a core function and fundamental component of computers.
The central processin ...
, the hardware-specific memory stored in bytes on the RAM (Random Access Memory). A shadow page table is a pseudo-page table within a computer's main page table which allows a system to run more than one kind of operating system concurrently.
References
{{ReflistExternal links
Virtualization: Architectural Considerations And Other Evaluation Criteria
Object-oriented programming