Segment Protection on:
[Wikipedia]
[Google]
[Amazon]
Segment protection is a type of backup technique that can be used in most networks. It can be implemented as a dedicated backup or as a shared backup protection. Overlapping segments and non-overlapping segments are allowed; each providing different advantages.





 #Working path - is the chosen route from source to destination.
#Segment protection path - is the working path where the broken segment is using the protected path.
#Primary segment - is a segment of the working path.
#Protected segment - is the backup path of one segment.
#End-to-end protection - is the protection of one segment where is source and destination are also the end points of the backup protection.
Saradhi, C.V.; Murthy, C.S.R.; , "Segmented protection paths in WDM mesh networks," High Performance Switching and Routing, 2003, HPSR. Workshop on , vol., no., pp. 311- 316, 24–27 June 2003
doi: 10.1109/HPSR.2003.1226724
#Working path - is the chosen route from source to destination.
#Segment protection path - is the working path where the broken segment is using the protected path.
#Primary segment - is a segment of the working path.
#Protected segment - is the backup path of one segment.
#End-to-end protection - is the protection of one segment where is source and destination are also the end points of the backup protection.
Saradhi, C.V.; Murthy, C.S.R.; , "Segmented protection paths in WDM mesh networks," High Performance Switching and Routing, 2003, HPSR. Workshop on , vol., no., pp. 311- 316, 24–27 June 2003
doi: 10.1109/HPSR.2003.1226724
see more
*Iterative Two-Step-Approach
see more
Technique
Terms






 #Working path - is the chosen route from source to destination.
#Segment protection path - is the working path where the broken segment is using the protected path.
#Primary segment - is a segment of the working path.
#Protected segment - is the backup path of one segment.
#End-to-end protection - is the protection of one segment where is source and destination are also the end points of the backup protection.
Saradhi, C.V.; Murthy, C.S.R.; , "Segmented protection paths in WDM mesh networks," High Performance Switching and Routing, 2003, HPSR. Workshop on , vol., no., pp. 311- 316, 24–27 June 2003
doi: 10.1109/HPSR.2003.1226724
#Working path - is the chosen route from source to destination.
#Segment protection path - is the working path where the broken segment is using the protected path.
#Primary segment - is a segment of the working path.
#Protected segment - is the backup path of one segment.
#End-to-end protection - is the protection of one segment where is source and destination are also the end points of the backup protection.
Saradhi, C.V.; Murthy, C.S.R.; , "Segmented protection paths in WDM mesh networks," High Performance Switching and Routing, 2003, HPSR. Workshop on , vol., no., pp. 311- 316, 24–27 June 2003
doi: 10.1109/HPSR.2003.1226724
Examples
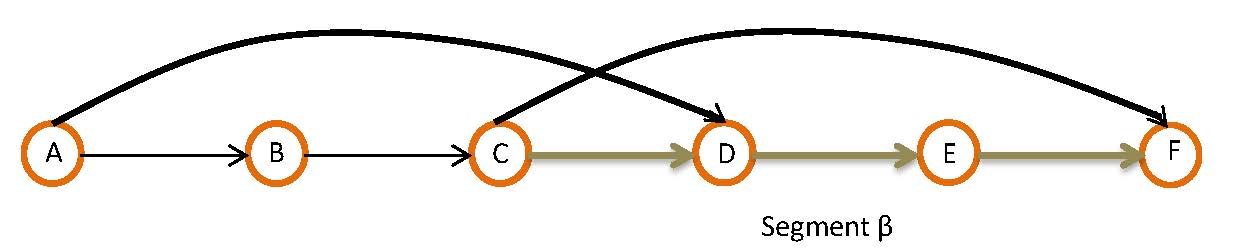
In "Working path" animation on the right it can be seen that for a chosen route the primary path becomes the working path. This example illustrates that the source (node A) is routed to B,then C,D,E, and lastly the destination (node F). We can see that segment protection has been implemented. Segment consists of nodes A, B, C, and D while segment consists of nodes C, D, E, and F. Lets assume that link B-C failed. Nodes B and C know that the link between them is down so they signal to their neighboring nodes that a link is down and to move to a backup path. Node A sends its traffic over to node D directly. Node D then sends the traffic over its route to E then finally destination F. ''Note'': in this case the segment protection path for segment does not contain any intermediate nodes; this is usually not the case, but the example would follow respectively.Overlapping vs. non-overlapping
Overlapping and non-overlapping segment protection have one main difference but provide different protections at different costs.Kantarci, B.; Mouftah, H.T.; Oktug, S.; , "Availability analysis and Connection provisioning in overlapping shared segment protection for optical networks," Computer and Information Sciences, 2008. ISCIS '08. 23rd International Symposium on , vol., no., pp.1-6, 27-29 Oct. 2008 doi: 10.1109/ISCIS.2008.4717963 The diagrams to the right, "overlapping protection" and "non-overlapping protection" illustrate the difference between the two. The overlapping scheme makes sure that there is at least one link that is protected by two segments, while the non-overlapping scheme begins a segment protection at the same node as the previous ended. Node protection is the main advantage of the overlapping scheme over the non-overlapping scheme. Node protection that is provided allows a path to be provisioned if a node goes ''offline.'' In the diagram, "Overlapped link", we can see that link C-D has protection from segment and segment . This type of protection allows node C to fail and for the backup of segment to be used. The path would then be node A to D to E to F. This would work the same if node D failed. The corresponding path to that failure would be node A to B to C to F. Non-overlapping segment protection does not provide node protection at every node. This scheme is only able to recover from a node failure that is not at the segment end node. In the diagram, "Non-overlapping protection", if node D fails a path cannot be provisioned from node A, the source, to node F, the Destination. Non-overlapping segment protection is a more cost efficient solution because only the end node of every segment requires to have extra ports. In the long term it is more cost efficient to implement overlapping segment protection because the a provisioned circuit's availability would be much higher.Backup variations
Dedicated segment protection and shared segment protection are both available for use. Shared segment protection allows a more efficient network to be deployed. Both of these schemes can be implemented on an overlapping and a non-overlapping network topology. The "working path" diagram illustrates the dedicated-overlapping segment protection. "Shared segment protection", on the right, illustrated a shared-non-overlapping segment protection. Working paths, A and B, both have segment protection. The first segment protection path consists of, node A to B to C to D and the second consists of, node D to E to F. In this example we can see that if part of working path A, node D to F, would fail that node D would use its shred segment protection for that segment. The new path for working path A would be, A to D to E to F. Of course, if a second failure occurred on the same segment before the first failure is fixed a recovery would not be possible. Shared segment protection provides a higher efficiency. Although the networks provided here as examples are simple the benefits of sharing are noticeable. In the previous example we can see that a new backup segment protection is not necessary for each working path. When this scheme is scaled to a large network a substantial cost improvement can be seen.Implementation
This protection scheme can be implemented in most mesh networks. Of course, the larger the network the more possibilities are available. Determining the working path is found by the routing algorithm. We are not limited to any one particular algorithm, but we must make modifications to allow for segments to be created with a protection path for each segment. Another important parameter is the number of hops or distance that each segment should have to have an optimal network. Although there is no secret number that would work for any network, there have been studies which show their experiment results.Tewari, R.; Ramamurthy, B.; , "Optimal segment size for fixed-sized segment protection in wavelength-routed optical networks," Advanced Networks and Telecommunication Systems (ANTS), 2009 IEEE 3rd International Symposium on , vol., no., pp.1-3, 14-16 Dec. 2009 doi: 10.1109/ANTS.2009.5409857Algorithms
Generalized Segment Protection "The algorithm works as follows: K working paths are selected based on a predetermined criterion (shortest path
In graph theory, the shortest path problem is the problem of finding a path between two vertices (or nodes) in a graph such that the sum of the weights of its constituent edges is minimized.
The problem of finding the shortest path between t ...
, minimum unavailability, shortest hop count, etc.). Upon selecting the K-paths, for each working path, the links along the working path are reversed. The cost of every link that has at least one spare channel is degraded by a negligible coefficient ε. Each link that originates out of the working path but ends on the working path is modified so that its end point is moved to the previous node on the working path. Finally a path from source to destination is selected. Upon obtaining the path, the modified links are restored, and the connection is provisioned with
the corresponding backup segments"C. Ou, S. Rai, and B. Mukherjee, “Extension of segment protection
for bandwidth efficiency and differentiated quality of protection in optical/mpls networks,”Optical Switching and Networking, vol. 1, pp.19–33, January 2005.Tornatore. M, Carcagni. Matteo, Mukherjee. Biswanath Ou. Canhui, and Pattavina. Achille, “Efficient shared-segment protection exploiting the knowledge of connection holding time,” in Global Telecommunications Conference (GLOBECOM). IEEE, 2006, pp. 1–5.
External papers
*Cascaded Diverse RoutingPin-Han Ho; Mouftah, H.T.; , "Allocation of protection domains in dynamic WDM mesh networks," Network Protocols, 2002. Proceedings. 10th IEEE International Conference on , vol., no., pp. 188- 189, 12-15 Nov. 2002 doi: 10.1109/ICNP.2002.1181400see more
*Iterative Two-Step-Approach
see more
See also
*Link protection Link protection is designed to safeguard networks from failure. Failures in high-speed networks have always been a concern of utmost importance. A single fiber cut can lead to heavy losses of traffic and protection-switching techniques have been us ...
*Path Protection
Path protection in telecommunications is an end-to-end protection scheme used in connection oriented circuits in different network architectures to protect against inevitable failures on service providers’ network that might affect the servi ...
*P-cycle protection
The p-Cycle protection scheme is a technique to protect a mesh network from a failure of a link, with the benefits of ring like recovery speed and mesh-like capacity efficiency, similar to that of a shared backup path protection (SBPP). p-Cycle pr ...
*Optical Mesh Networks
An optical mesh network is a type of optical telecommunications network employing wired fiber-optic communication or wireless free-space optical communication in a mesh network architecture.
Most optical mesh networks use fiber-optic commun ...
*Shortest Path Problem
In graph theory, the shortest path problem is the problem of finding a path between two vertices (or nodes) in a graph such that the sum of the weights of its constituent edges is minimized.
The problem of finding the shortest path between t ...
*K shortest path routing
The ''k'' shortest path routing problem is a generalization of the shortest path routing problem in a given network. It asks not only about a shortest path but also about next ''k−1'' shortest paths (which may be longer than the shortest path) ...
*Dijkstra's algorithm
Dijkstra's algorithm ( ) is an algorithm for finding the shortest paths between nodes in a graph, which may represent, for example, road networks. It was conceived by computer scientist Edsger W. Dijkstra in 1956 and published three years ...
References
{{Reflist Network architecture