Linux.Encoder.1 on:
[Wikipedia]
[Google]
[Amazon]
Linux.Encoder (also known as ELF/Filecoder.A and Trojan.Linux.Ransom.A) is considered to be the first
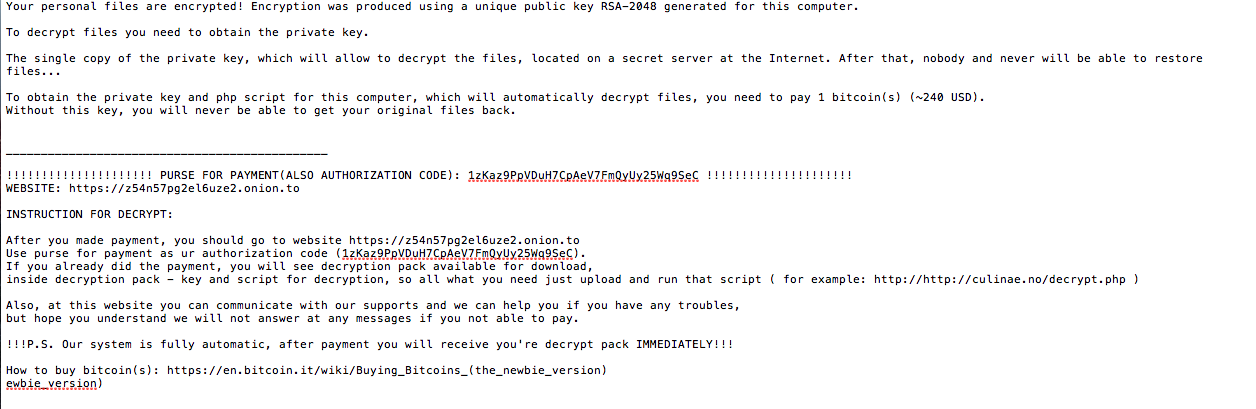 The program will then generate a file called "readme_for_decryption.txt" in every folder. This file contains the Bitcoin address generated specifically for the ransom and the website to download the decrypting tool hosted on a .
The program will then generate a file called "readme_for_decryption.txt" in every folder. This file contains the Bitcoin address generated specifically for the ransom and the website to download the decrypting tool hosted on a .
ransomware
Ransomware is a type of malware from cryptovirology that threatens to publish the victim's personal data or permanently block access to it unless a ransom is paid off. While some simple ransomware may lock the system without damaging any files, m ...
Trojan
Trojan or Trojans may refer to:
* Of or from the ancient city of Troy
* Trojan language, the language of the historical Trojans
Arts and entertainment Music
* ''Les Troyens'' ('The Trojans'), an opera by Berlioz, premiered part 1863, part 189 ...
targeting computers running Linux
Linux ( or ) is a family of open-source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically packaged as a Linux distribution, which i ...
. There are additional variants of this Trojan that target other Unix and Unix-like systems. Discovered on November 5, 2015, by Dr. Web
Dr.Web is a software suite developed by Russian anti-malware company Doctor Web. First released in 1992, it became the first anti-virus service in Russia.
The company also offers anti-spam solutions and is used by Yandex to scan e-mail attachment ...
, this malware affected at least tens of Linux users.
Linux.Encoder.1 is remotely executed on the victim's computer by using a flaw in Magento
Magento is an open-source e-commerce platform written in PHP. It uses multiple other PHP frameworks such as Laminas (formerly known as Zend Framework) and Symfony. Magento source code is distributed under Open Software License (OSL) v3.0. Mage ...
, a popular Content management system
A content management system (CMS) is computer software used to manage the creation and modification of digital content ( content management).''Managing Enterprise Content: A Unified Content Strategy''. Ann Rockley, Pamela Kostur, Steve Manning. New ...
app. When activated, the malware encrypts certain types of files stored on mounted local and network drives using AES
AES may refer to:
Businesses and organizations Companies
* AES Corporation, an American electricity company
* AES Data, former owner of Daisy Systems Holland
* AES Eletropaulo, a former Brazilian electricity company
* AES Andes, formerly AES Gener ...
and RSA
RSA may refer to:
Organizations Academia and education
* Rabbinical Seminary of America, a yeshiva in New York City
*Regional Science Association International (formerly the Regional Science Association), a US-based learned society
*Renaissance S ...
Public-key cryptography
Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a public key and a corresponding private key. Key pairs are generated with cryptographic a ...
, with the private key stored only on the malware's control servers. The malware then store a file called "readme_to_decrypt.txt" in every directory, containing a message, which offers to decrypt the data if a payment (through Bitcoin
Bitcoin ( abbreviation: BTC; sign: ₿) is a decentralized digital currency that can be transferred on the peer-to-peer bitcoin network. Bitcoin transactions are verified by network nodes through cryptography and recorded in a public di ...
) is made. Compared to other ransomware such as CryptoLocker
The CryptoLocker ransomware attack was a cyberattack using the ''CryptoLocker'' ransomware that occurred from 5 September 2013 to late May 2014. The attack utilized a trojan that targeted computers running Microsoft Windows, and was believed t ...
, the malware does not state a deadline to pay and the ransom does not increase over time.
Discovery
On November 5, 2015,Dr. Web
Dr.Web is a software suite developed by Russian anti-malware company Doctor Web. First released in 1992, it became the first anti-virus service in Russia.
The company also offers anti-spam solutions and is used by Yandex to scan e-mail attachment ...
, a Russian anti-malware company added to its virus database Linux.Encoder.1. The company then published the malware description the day after. This ransomware is written in C using the PolarSSL
Mbed TLS (previously PolarSSL) is an implementation of the TLS and SSL protocols and the respective cryptographic algorithms and support code required. It is distributed under the Apache License version 2.0. Stated on the website is that Mbed ...
library.
Operation
Propagation
According toBitdefender
Bitdefender is a Romanian cybersecurity technology company headquartered in Bucharest, Romania, with offices in the United States, Europe, Australia and the Middle East.
The company was founded in 2001 by the current CEO and main shareholder ...
Labs, the most common infection vector is through a flaw in Magento
Magento is an open-source e-commerce platform written in PHP. It uses multiple other PHP frameworks such as Laminas (formerly known as Zend Framework) and Symfony. Magento source code is distributed under Open Software License (OSL) v3.0. Mage ...
, a shopping cart software. CheckPoint
Checkpoint may refer to:
Places
* Border checkpoint, a place on the land border between two states where travellers and/or goods are inspected
* Security checkpoint, erected and enforced within contiguous areas under military or paramilitary co ...
, reported this vulnerability in April 2015. After this report, Magento issued a fix. However, a lot of small e-commerce sites did not apply this critical update. Linux host might also be attacked using other exploits.
File encryption
Encrypted files
When run as root, the program loads two files into memory containing the attackers' demands: * ./readme.crypto * ./index.crypto After this the ransomware receives the public RSA key. The malware will then start as a daemon and delete all its original files. The trojan will encrypt files with the extensions : ".php", ".html", ".tar", ".gz", ".sql", ".js", ".css", ".txt" ".pdf", ".tgz", ".war", ".jar", ".java", ".class", ".ruby", ".rar" ".zip", ".db", ".7z", ".doc", ".pdf", ".xls", ".properties", ".xml" ".jpg", ".jpeg", ".png", ".gif", ".mov", ".avi", ".wmv", ".mp3" ".mp4", ".wma", ".aac", ".wav", ".pem", ".pub", ".docx", ".apk" ".exe", ".dll", ".tpl", ".psd", ".asp", ".phtml", ".aspx", ".csv". The malicious program encrypts files with the aforementioned extensions in the following directories: * /home * /root * /var/lib/mysql * /var/www * /etc/nginx * /etc/apache2 * /var/log After this, the malware will encrypt all the files from directories with a name starting by: * public_html * www * webapp * backup * .git * .svn The program will not encrypt files in the following directories * / * /root/ * .ssh * /usr/bin * /bin * /etc/ssh The program will then generate a file called "readme_for_decryption.txt" in every folder. This file contains the Bitcoin address generated specifically for the ransom and the website to download the decrypting tool hosted on a .
The program will then generate a file called "readme_for_decryption.txt" in every folder. This file contains the Bitcoin address generated specifically for the ransom and the website to download the decrypting tool hosted on a .onion
An onion (''Allium cepa'' L., from Latin ''cepa'' meaning "onion"), also known as the bulb onion or common onion, is a vegetable that is the most widely cultivated species of the genus ''Allium''. The shallot is a botanical variety of the oni ...
website.
Encryption method
Like other ransomware, Linux.Encoder.1 use mixed-encryption algorithms to encrypt data. It starts by generating an AES key on the victim's device and encrypts all of the previous files usingAES
AES may refer to:
Businesses and organizations Companies
* AES Corporation, an American electricity company
* AES Data, former owner of Daisy Systems Holland
* AES Eletropaulo, a former Brazilian electricity company
* AES Andes, formerly AES Gener ...
- CBC-128. Then the RSA
RSA may refer to:
Organizations Academia and education
* Rabbinical Seminary of America, a yeshiva in New York City
*Regional Science Association International (formerly the Regional Science Association), a US-based learned society
*Renaissance S ...
-encrypted AES key is prepended to the beginning of every encrypted file, with the original file permissions and the IV used by the AES algorithm. All the encrypted files have ".encrypted" added at the end of their file name.
The program use the libc rand()
A pseudorandom number generator (PRNG), also known as a deterministic random bit generator (DRBG), is an algorithm for generating a sequence of numbers whose properties approximate the properties of sequences of random numbers. The PRNG-generate ...
function with the timestamp at the moment of encryption as seed to generate the IV and the keys.
Decryption
When the payment to the cybercriminal is made, the victim can download a PHP script to their computer. This script will use the RSA private key to recover the symmetric AES key and decrypt all the files with the ".encrypted" extension. Along with the file decryption, the decryption tool will also delete every "readme_for_decryption.txt" file on the hard drive.Recovering files
Because of the use of thetimestamp
A timestamp is a sequence of characters or encoded information identifying when a certain event occurred, usually giving date and time of day, sometimes accurate to a small fraction of a second. Timestamps do not have to be based on some absolut ...
as a seed
A seed is an embryonic plant enclosed in a protective outer covering, along with a food reserve. The formation of the seed is a part of the process of reproduction in seed plants, the spermatophytes, including the gymnosperm and angiosper ...
for creating the keys
Key or The Key may refer to:
Common meanings
* Key (cryptography), a piece of information that controls the operation of a cryptography algorithm
* Key (lock), device used to control access to places or facilities restricted by a lock
* Key (ma ...
and the IV for encryption, decryption of files encrypted by the ransomware is trivial given that the original timestamp information is kept intact. Researchers at Bitdefender Labs have found and exploited this weakness to recover the files without having to pay the criminals.
On other Unix systems
* Linux.Encoder.1 has been recompiled on Mac, called KeRanger. * There is a version that infectsFreeBSD
FreeBSD is a free and open-source Unix-like operating system descended from the Berkeley Software Distribution (BSD), which was based on Research Unix. The first version of FreeBSD was released in 1993. In 2005, FreeBSD was the most popular ...
.
References
{{portal, Linux