() was the
signals intelligence
Signals intelligence (SIGINT) is the act and field of intelligence-gathering by interception of ''signals'', whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly u ...
agency of the
Heer (German Army), before and during
World War II
World War II or the Second World War (1 September 1939 – 2 September 1945) was a World war, global conflict between two coalitions: the Allies of World War II, Allies and the Axis powers. World War II by country, Nearly all of the wo ...
. It was the successor to the former cipher bureau known as Inspectorate 7/VI in operation between 1940 and 1942, when it was further reorganised into the Headquarters for Signal Intelligence () () between 1942 and 1944, until it was finally reorganised in October 1944 into the GdNA. The agency was also known at the OKH/Gend Na, GendNa or Inspectorate 7 or more commonly OKH/GdNA. ''Inspectorate 7/VI'' was also known as In 7 or In/7 or In 7/VI and also OKH/Chi.
Chi-Stelle
The letter ''Chi'' for the ('cipher department') is, contrary to what one might expect, not the Greek letter ''Chi'', nor anything to do with the
chi-squared test
A chi-squared test (also chi-square or test) is a Statistical hypothesis testing, statistical hypothesis test used in the analysis of contingency tables when the sample sizes are large. In simpler terms, this test is primarily used to examine w ...
, a common cryptographic test used as part of deciphering of
enciphered message, and invented by
Solomon Kullback, but simply the first three letters of the word .
Key personnel

Senior personnel
Erich Fellgiebel, was Director of the Code and Cipher section of the Defense Ministry from 1931 to 1932 and held the dual combined office of Chef HNW and Chief Signal Officer Armed Forces (Chef WNF) from 1939 until 20 July 1944. Fellgiebel was executed in July 1944 after an attempt on Hitler's life in the failed
20th July plot.
The unit was then subordinated to
Fritz Thiele
Fritz Thiele (14 April 1894 – 4 September 1944) was a member of the German resistance to Nazism, German resistance who also served as the communications chief of the German Army (1935-1945), German Army during World War II. Life
Thiele was bor ...
, who was Director of Section III of the Armed Forces Signal Communication Group,
Radio Defense Corps, or more accurately the AgWBNV, Radio Communication Group 3 (), (AgWNV/FU III) were responsible for locating, eliminating, or neutralizing all enemy agents' radio activities.
[IF-176, foreword]
Wilhelm Gimmler, () was Chief Signals Officer subordinated to Commander in Chief
OB West
''Oberbefehlshaber West'' ( German: initials ''OB West'') (German: "Commander-in-Chief n theWest") was the overall commander of the '' Westheer'', the German armed forces on the Western Front during World War II. It was directly subordinate to t ...
and Chief of the Armed Forces Signal Communications Office. Gimmler was responsible for coordinating all the cryptographic security studies undertaken by German Armed Forces and was notable for standardising wireless phraseology between different Army Groups.
Colonel
Hugo Kettler was a career Signals officer, who volunteered at the start of
World War I
World War I or the First World War (28 July 1914 – 11 November 1918), also known as the Great War, was a World war, global conflict between two coalitions: the Allies of World War I, Allies (or Entente) and the Central Powers. Fighting to ...
, entering the ''Telephone Replacement Department No. 6'' () and after undergoing continual promotion during World War I and the interwar period, was a senior signals officer at the start of
World War II
World War II or the Second World War (1 September 1939 – 2 September 1945) was a World war, global conflict between two coalitions: the Allies of World War II, Allies and the Axis powers. World War II by country, Nearly all of the wo ...
. Colonel Hugo Kettler was a Director of OKW/Chi from October 1943.
Kettler was first director of HLS Ost and who would later become Chief of
OKW/Chi in the summer of 1943. During the summer of 1942, Kettler was succeeded by Baron Colonel Rudolf Von Der Osten-Sacken, who remained its chief until July 1944, when he was implicated in the
20 July plot
The 20 July plot, sometimes referred to as Operation Valkyrie, was a failed attempt to assassinate Adolf Hitler, the chancellor and leader of Nazi Germany, and overthrow the Nazi regime on 20 July 1944. The plotters were part of the German r ...
on Hitler's life and committed suicide before he was scheduled to be hanged.
Headquarters

* Agn/Gen. der. Nachr. Aufkl – Fritz Boetzel
* Chief of Staff () – Andrea
*
Adjutant
Adjutant is a military appointment given to an Officer (armed forces), officer who assists the commanding officer with unit administration, mostly the management of “human resources” in an army unit. The term is used in French-speaking armed ...
Norawec
* Chief of Understaff () Köbe
* Group Z – Major Hüther
Fritz Boetzel, was the officer who was responsible for the German Defense Ministry's signals intelligence agency, during the important interwar period, when the service was being enlarged and professionalised, In 1939, he was posted to
Army Group Southeast () to take up the office position of Chief of Intelligence Evaluation in
Athens
Athens ( ) is the Capital city, capital and List of cities and towns in Greece, largest city of Greece. A significant coastal urban area in the Mediterranean, Athens is also the capital of the Attica (region), Attica region and is the southe ...
,
Greece
Greece, officially the Hellenic Republic, is a country in Southeast Europe. Located on the southern tip of the Balkan peninsula, it shares land borders with Albania to the northwest, North Macedonia and Bulgaria to the north, and Turkey to th ...
. In 1944, following the reorganisation of the Wehrmacht signals intelligence capability, Fritz Boetzel, now General Fritz Boetzel, who was promoted by
Albert Praun, created 12
Communications Reconnaissance Battalions (KONA regiment) in eight regiments, with each regiment assigned to a particular
Army Group
An army group is a military organization consisting of several field army, field armies, which is self-sufficient for indefinite periods. It is usually responsible for a particular geographic area. An army group is the largest field organizatio ...
. Fritz Boetzel was considered to be one of the sources for the
Lucy spy ring
The Lucy spy ring () was an anti-Nazi World War II espionage operation headquartered in Switzerland and run by Rudolf Roessler, a German refugee. Its story was only published in 1966, and very little is clear about the ring, Roessler, or the effo ...
. Boetzel knew
Hans Oster
''Generalmajor'' Hans Paul Oster (9 August 1887 – 9 April 1945) was a general in the ''Wehrmacht'' and a leading figure of the anti-Nazi German resistance from 1938 to 1943. As deputy head of the counter-espionage bureau in the ''Abwehr'' (Ge ...
and
Wilhelm Canaris
Wilhelm Franz Canaris (1 January 1887 – 9 April 1945) was a admiral (Germany), German admiral and the chief of the ''Abwehr'' (the German military intelligence, military-intelligence service) from 1935 to 1944. Initially a supporter of Ad ...
and had fit the
anti-nazi personality of
Rudolf Roessler
Rudolf Roessler (German: ''Rößler''; 22 November 1897 – 11 December 1958) was a Protestant Germany, German and a dedicated German resistance to Nazism, anti-Nazi. During the interwar period, Roessler was a lively cultural journalist, with a ...
contacts, the man who had run the spy ring.
Cryptanalysis unit command
The directors of the ''In 7/Vi'' cryptanalysis units from January 1941 to February 1945 were:
* Major Major Mang. 1941–1942
* Major Mettig. November 1941 to June 1943
* Major Lechner 1943
* Major Dr Rudolf Hentze 1944–1945
Werner Mettig was a career signals officer who joined the military in 1933, and worked up to command the
Germany Armies cryptologic centre, Inspectorate ''7/VI'' from November 1941 to June 1943. After working in the Signals Battalion on the
Eastern Front for several months, he was assigned second in command of
OKW/Chi in December 1943, and subordinated to Hugo Kettler, and held the position until April 1945. After the war he was considered such a high-value target that he was moved to England to be interrogated by TICOM.
Communication office
The following German Army officers worked with the communication office and provided the main liaison function for conveying intelligence from the central office to the field.
Unit Commander
Johannes Marquart and I/C Cryptanalysis
Leutnant
() is the lowest junior officer rank in the armed forces of Germany ( Bundeswehr), the Austrian Armed Forces, and the military of Switzerland.
History
The German noun (with the meaning "" (in English "deputy") from Middle High German «locum ...
Schlemmer were Commander of KONA 5 and were communication intelligence liaison officers for several army groups on the southern part of the
Western Front.
Unit Commander Major Lechner and I/C Cryptanalysis
Leutnant
() is the lowest junior officer rank in the armed forces of Germany ( Bundeswehr), the Austrian Armed Forces, and the military of Switzerland.
History
The German noun (with the meaning "" (in English "deputy") from Middle High German «locum ...
Herbert von Denffer were Commander of KONA 6 and were communication intelligence liaison officers for several army groups for the northern part of the
Western Front.
Colonel
Walter Kopp, was a senior communication intelligence officer for OB West, i.e. for Sig. Int. West.
Gotthard Heinrici
Gotthard Fedor August Heinrici (; 25 December 1886 – 10 December 1971) was a German general during World War II. Heinrici is considered to have been the premier defensive expert of the ''Wehrmacht''. His final command was Army Group Vistula, fo ...
was on the General Staff and Chief Signals officer for OB West.
Leo Hepp was a member of the General Staff and was Deputy Chief of Army Signal Communication. Hepp was later Chief of Staff for the Chief Signals Officer at the
Oberkommando der Wehrmacht
The (; abbreviated OKW ː kaːˈveArmed Forces High Command) was the Command (military formation), supreme military command and control Staff (military), staff of Nazi Germany during World War II, that was directly subordinated to Adolf ...
and directly subordinated to Fellgiebel and later General
Albert Praun, when Fellgiebel was killed.
Colonel Muegge was a communication intelligence officer for an army group.
Colonel
Kunibert Randewig was commander of intercept units with various army groups. Randewig was a career Signals officer, who joined the
German Army
The German Army (, 'army') is the land component of the armed forces of Federal Republic of Germany, Germany. The present-day German Army was founded in 1955 as part of the newly formed West German together with the German Navy, ''Marine'' (G ...
in 1914. During the
World War I
World War I or the First World War (28 July 1914 – 11 November 1918), also known as the Great War, was a World war, global conflict between two coalitions: the Allies of World War I, Allies (or Entente) and the Central Powers. Fighting to ...
and the interwar period, he became a veteran of monitoring Soviet wireless communications and a supporter of decentralisation of signal intelligence. He would eventually become Commander of all
KONA Signal Intelligence regiments in the west. Randewig would later work on the rocket programme.
Cryptanalytic staff
Johannes Marquart. He was a mathematician, who was also a German Army hand cryptographic systems specialist. In a later role, he was the liaison officer between the clearing centre of communications intelligence, and the Western Intelligence Branch, Army General Staff.
History
1919–1933
Little was known about the Signals Intelligence of the
German Army
The German Army (, 'army') is the land component of the armed forces of Federal Republic of Germany, Germany. The present-day German Army was founded in 1955 as part of the newly formed West German together with the German Navy, ''Marine'' (G ...
during this period. A Codes and Ciphers Section of the German
Defence Ministry () was subordinated to an Army Signal Officer, that had been maintained in skeleton form since the end of
World War I
World War I or the First World War (28 July 1914 – 11 November 1918), also known as the Great War, was a World war, global conflict between two coalitions: the Allies of World War I, Allies (or Entente) and the Central Powers. Fighting to ...
. The following people were directors of the unit:
The directors of the ciphers section also controlled the Defense Ministry's intercept network, which was used to gather ''operational intelligence'' and was divided into two branches. The first branch was the
fixed intercept network stations which were dated from 1923 to 1924 () (Feste), and at least seven stations were operating before 1933 in military districts. The second intercept branch was the motorised Intercept Companies (), created by Fellgiebel himself. Six of the stationary intercept stations were aligned specifically to the interception of foreign military traffic and the last one specifically designed for foreign diplomatic traffic. The military traffic stations were:
Stuttgart
Stuttgart (; ; Swabian German, Swabian: ; Alemannic German, Alemannic: ; Italian language, Italian: ; ) is the capital city, capital and List of cities in Baden-Württemberg by population, largest city of the States of Germany, German state of ...
,
Munich
Munich is the capital and most populous city of Bavaria, Germany. As of 30 November 2024, its population was 1,604,384, making it the third-largest city in Germany after Berlin and Hamburg. Munich is the largest city in Germany that is no ...
,
Münster
Münster (; ) is an independent city#Germany, independent city (''Kreisfreie Stadt'') in North Rhine-Westphalia, Germany. It is in the northern part of the state and is considered to be the cultural centre of the Westphalia region. It is also a ...
,
Königsberg
Königsberg (; ; ; ; ; ; , ) is the historic Germany, German and Prussian name of the city now called Kaliningrad, Russia. The city was founded in 1255 on the site of the small Old Prussians, Old Prussian settlement ''Twangste'' by the Teuton ...
,
Leignitz and
Breslau with the diplomatic traffic intercept station located at
Treuenbrietzen
Treuenbrietzen () is a town in the Potsdam-Mittelmark district of Brandenburg, Germany.
Geography
The municipality Treuenbrietzen is situated 32 km northeast of Wittenberg and includes the localities
* city of Treuenbrietzen with its agglom ...
. Each intercept station was assigned a series of intercept assignments, with the most important assignments monitored by two stations, e.g. the Soviet Union was monitored from Königsberg and Frankfurt, and so on. The assignments were established in the Assignment Plan ''H-Aufgabenplan''. Each assignment was prioritised from first to fourth, sometimes absolute, sometimes relative, e.g. Poland was assigned first for Frankfurt/Oder stations and a first or second for Königsberg. Priority could change depending if a country went to war.
1933–1939
During the 1933–1934 period, the Defense Ministry created three more intercept stations: one was at
Hersbruck
Hersbruck () is a small town in Middle Franconia, Bavaria, Germany, belonging to the district Nürnberger Land. It is best known for the late-gothic artwork of the Hersbruck altar, the "Hirtenmuseum" and the landscape of Hersbruck Switzerland.
...
, (that was later moved to
Lauf) with the other two located at
Striegau and
Chemnitz
Chemnitz (; from 1953 to 1990: Karl-Marx-Stadt (); ; ) is the third-largest city in the Germany, German States of Germany, state of Saxony after Leipzig and Dresden, and the fourth-largest city in the area of former East Germany after (East Be ...
. Using the ten intercept stations to intercept foreign military and diplomatic communications, the Defense Ministry created its own military code and cipher section, called ''Intercept Control Station'' (HLS) () in 1933/34. To run the control station, the Ministry reassigned several trained
cryptanalysts from the Ministry of the Reichswehr Codes and Cipher Section. All Army intercepts were forwarded to the HLS, but other intercept traffic types were forwarded to the Commander-In-Chief aligned agency, e.g. Foreign Air Force traffic was sent to chi-stelle, the Luftwaffe Cipher Bureau. Diplomatic intercepts were sent to both German War Ministry () and to
Foreign Office
Foreign may refer to:
Government
* Foreign policy, how a country interacts with other countries
* Ministry of Foreign Affairs, in many countries
** Foreign Office, a department of the UK government
** Foreign office and foreign minister
* United ...
civilian cipher bureau
AA/Pers Z S.
1939–1941
During the early years of World War II, substantial change occurred within the German Army signal intelligence service. The main developments were:
* The intercept service mission was narrowed to include only Army Traffic. With the formation of
OKW/Chi, the signals intelligence agency of the
Supreme Command of the Armed Forces, in 1939, OKW/Chi took over all diplomatic intercept traffic. To help facilitate message interception, the Army transferred two interception stations at Lauf and Treuenbrietzen.
* The intercept service expanded. In 1939, the Army established two new branch stations for the intercept of foreign Army communications from the east. The branch stations were created as
Graz
Graz () is the capital of the Austrian Federal states of Austria, federal state of Styria and the List of cities and towns in Austria, second-largest city in Austria, after Vienna. On 1 January 2025, Graz had a population of 306,068 (343,461 inc ...
and Tullin.
* Five new
Signal Intelligence Regiments (, ) were created. The KONA operated in the theatre as complete intercept and evaluation units, while attached to
Army Groups, (e.g.
Army Group A
Army Group A () was the name of three distinct army groups of the ''German Army (1935–1945), Heer'', the ground forces of the ''Wehrmacht'', during World War II.
The first Army Group A, previously known as "Army Group South", was active from Oct ...
). Each KONA unit was numbered from one to five. KONA units 1,2,3 were assigned to the
Eastern Front. KONA 1 was assigned to the southern front, KONA 2 to the Central front and KONA 3 to the Army Group on the Northern Front. KONA 4 was not attached to any Army Group, but was subordinated to the commander of the German Armies in the
Balkans
The Balkans ( , ), corresponding partially with the Balkan Peninsula, is a geographical area in southeastern Europe with various geographical and historical definitions. The region takes its name from the Balkan Mountains that stretch throug ...
(). KONA 5 was assigned to
Army Group B
Army Group B () was the name of four distinct German Army Group, army group commands that saw action during World War II.
The first Army Group B was created on 12 October 1939 (from the former Army Group North) and fought in the Battle of France ...
on the
Western Front.
* In 1939, to cope with the increased demand and difficulty of decryption of enemy Army traffic, a large number of mathematicians and linguists, e.g.
translators
Translation is the communication of the meaning of a source-language text by means of an equivalent target-language text. The English language draws a terminological distinction (which does not exist in every language) between ''transl ...
and
interpreters
Interpreting is translation from a spoken or signed language into another language, usually in real time to facilitate live communication. It is distinguished from the translation of a written text, which can be more deliberative and make use o ...
were drafted and assigned to various field units, or intercept stations. When intercept units moved into the field in 1939, no cryptographers were available. Colonel ()
Kunibert Randewig, was a veteran of pre-war monitoring of
Soviet Union
The Union of Soviet Socialist Republics. (USSR), commonly known as the Soviet Union, was a List of former transcontinental countries#Since 1700, transcontinental country that spanned much of Eurasia from 1922 until Dissolution of the Soviet ...
wireless traffic. As commander of all the intercept units in the west, he was tasked with seeking available personnel. Those cryptographers which were available from
Y Units around
Berlin
Berlin ( ; ) is the Capital of Germany, capital and largest city of Germany, by both area and List of cities in Germany by population, population. With 3.7 million inhabitants, it has the List of cities in the European Union by population withi ...
were reassigned with additional linguists and mathematicians recruited as necessary. As a result, when the
German offensive started in April 1940, a sufficient group of cryptanalysts personnel was available.
* The Army showed an increased interest in the security of their own key systems. This gave rise, via a concentration of personnel, to a new agency, a math referat that was created in 1939/40, Army Signal Security Agency Group IV of Inspectorate 7 (). This was subordinated to the Chief of Army Equipment and Commander of the Replacement Army () (). The unit initially had about a dozen mathematicians including Dr
Hans Pietsch, Friedrich Steinberg,
Friedrich Böhm
Friedrich Böhm (born 15 August 1885 in Harburg (Swabia) near Donauwörth, died 25 August 1965 in Munich) was a German actuarial and insurance mathematician and university lecturer. During World War II, Böhm was conscripted into Group IV of ...
, Dr
Herbert von Denffer, Hilburg, and Dr
Hans-Peter Luzius. Most of these were drawn from the statistical offices of insurance companies. Dr
Otto Buggisch had his first contact with the group at the end of 1940. The group was loose at first, as men could be detached for specific projects in security work, but over time the work gradually split into three functions. This was General Theory – Referat F under Denffer, Hand ciphers under Oblt. Lüders and machine systems with the heading, Referat 13 commanded by Wachtmeister Döring.
:The German Army Signal Intelligence service in 1939 consisted of the following parts:
:* At least 10 intercept stations for the interception of foreign traffic (, ).
:* Five Signal Intelligence Regiments (KONA) attached to Army Groups.
:* An Intercept Control Stations () for the evaluation and analysis of foreign Army traffic.
:* An Army Signal Security Agency, Inspectorate 7/IV for testing and issuing codes and ciphers for the Army.
1941–1944
Western evaluation centre
During the middle of war, the small staff of the intercept and listening stations () was found to be inadequate to cope with the large amount of traffic resulting from the pressures of the war. A central cryptanalytic agency was established in Berlin, around 1 February 1941, that was designated as Inspecktorate 7 or more simply ''In 7''. It was also commanded by the Chief of the Army Equipment and Commander of the Replacement Army (), specifically Obstlt. Hassel. The experience of 1940 illustrated the fact that huge expansion of the German Army cryptologic effort was desirable. A central evaluation agency was created at the
Zeppelin bunker near
Zossen, which was designated as Control Station for Signal Intelligence () ().
Gruppe VI of ''In 7 (In 7/VI)'' was organised by Major Mang, whose aim was to not only build staffing levels at the centre, but to provide reserves of staff that could be called upon when necessary. In order to provide sufficient staff, Mang subordinated the ''In 6/VI'' unit to Chief of the Army Equipment and Commander of the
Replacement Army
The Replacement Army () was part of the Imperial German Army during World War I and part of the Wehrmacht during World War II. It was based within Germany proper and included command and administrative units as well as training and guard troops. I ...
. In matters of policy, ''In 7/VI'' was subordinated to the Field Army only. Considered a curious form of organisation, it enabled the cryptanalytic service to recruit sufficient staff without operational interference, at the same time maintaining close support of field units. The cryptographic section would eventually become independent.
Eastern evaluation centre
During the first months of the unit, Russian cryptanalysis was conducted as part of the operational schedule of ''In 7/VI'', with Russian evaluation included as part of the cryptanalytic work done by unit LNA. Both of these units felt, incorrectly, that cryptanalysis and evaluation of Russian intercepts should be carried out close to the front lines of the field army in
East Prussia
East Prussia was a Provinces of Prussia, province of the Kingdom of Prussia from 1772 to 1829 and again from 1878 (with the Kingdom itself being part of the German Empire from 1871); following World War I it formed part of the Weimar Republic's ...
. This resulted in significant numbers of personnel being detached from the LNA and ''In 7/VI'' in late 1941, made up of cryptanalysts and evaluators skilled in Russian traffic and sent to
Loetzen to work. This group would eventually become the nucleus of the organisation:
Intercept Control Station East () () for Russian evaluation and traffic analysis. From this point on until November 1944, signal intelligence was divided into Russian cryptanalysis carried out by HLS Ost, and non-Russian signal intelligence carried out by ''OKH/Chi'' and LNA.
Expansion
In 1942, the responsibility for security testing of existing German Army cryptographic systems had been transferred from ''In 7/IV'' to ''In 7/VI''. From that time, the Army Signal Security Agency, ''In 7/IV'' had been confined to the development of new systems for the Army and for the production, printing, and distribution of current keys and systems.
In the autumn of 1943, ''OKH/Chi'' had been transferred to the newly created Department of Signals of the General Army Office and renamed Signal Intelligence, Department of Signals, General Army Office, Army High Command () (). Minor changes in internal organisation were affected, but the function and operation of the agency was not changed.
Although there was no essential change in the organisation of the field units of Germany Army Sigint Service from 1941 to 1944, additional units were put in place in the field. In 1942, the eastern
KONA units (1,2,3) were supplemented by the addition of KONA 6, which was formed to cover the
German campaign in the Caucasus.
[DF-18 p. 81] The KONA unit was not subordinated to any Army Group but was directly under HLS Ost. KONA 7 was established in February 1943 and was subordinated to the Commander-in-Chief South,
Albert Kesselring
Albert Kesselring (30 November 1885 – 16 July 1960) was a German military officer and convicted war crime, war criminal who served in the ''Luftwaffe'' during World War II. In a career which spanned both world wars, Kesselring reached the ra ...
, who controlled Army Group C, and the German forces in Italy.
The organisation of the German Army Sigint Service in 1944 consisted of the following:
* A central cryptanalytic agency for non-Russian traffic: ''In 7/VI'', later AgN/NA
* A central evaluation agency for non-Russian traffic: LNA
* A central cryptanalytic and evaluation agency for Russian traffic: HLS Ost
* Seven Signal Intelligence Regiments (KONA)
* An Army Signal Security agency for the distribution and development of Army systems: ''In 7/IV''
1944–1945
In October 1944, the various organisations of the German Army signal intelligence service was completely changed again, through the amalgamation of the three central agencies. The ''In 7/VI'' (later AgN/NA), the LNA, and HLS Ost was combined into one central cryptanalytic and evaluation agency: OKH/GDNA. This combined unit was the logical result of the retreat of HLS Ost together with the German Army, from East Prussia to
Zeppelin bunker near
Zossen where ''In 7/VI'' and LNA were situated.
The KONA signal intelligence regiments were not greatly affected by the amalgamation of the central agencies into the GdNA, although the KONA units did come under closer centralised control in matters of administration and signal intelligence policy. The main change to the Armies field organisations in 1944 were brought on by the
Allied invasion of France in June 1944. To cope with the situation,
KONA 6 was moved from the eastern front to the western, and a Senior Commander of the Signal Intelligence () () was created to coordinate and control KONA 5 and KONA 6. In late 1944 and early 1945, two additional KONA regiments were created,
KONA 8 and
KONA Nord, but it is worth noting that these KONA regiments were largely borrowed from other eastern front regiments, and were not a mark of expansion, merely a redeployment to areas under stress.
Colonel Boetzel, chief of the OKH/GdNA stated that KONA 4 was transferred to the west at the end of the war. A captured document indicated that KONA 4 had been succeeded by a signal battalion, () () 16, in February 1945 but did not mention its transfer to the west. It is probable that the KONA disintegrated and that various parts were sent to the different fronts.
The organisation of the signal intelligence service at the end of World War II consisted of the following:
* The Signal Intelligence Agency of the Army High Command (OKH/GdNA), a central cryptanalytic and evaluation agency for all traffic.
* A Senior Commander of the Signal Intelligence (Hoeh Kdr d NA) with control over the KONA stationed in the west and responsibility for all the
signals intelligence
Signals intelligence (SIGINT) is the act and field of intelligence-gathering by interception of ''signals'', whether communications between people (communications intelligence—abbreviated to COMINT) or from electronic signals not directly u ...
activities of the German Army in the west.
* Nine Signal Intelligence Regiments (KONA) which were attached to Army Groups or Commanders in the field.
Organisation of central agencies
Intercept Control Station
Intercept station operations 1939–1944

Before the war,
cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), ...
in the German Army was carried out by ''In 7'' ''Listening Position'' () (). This organisation originated in the cipher section of the German War Ministry and grew up in parallel with the cipher section of
OKW/Chi. Before the war, ''In 7'' Horchleistelle was merely a small department. It had a number of fixed intercept stations called ''Festes'', i.e. Fixed News Services () (). These were staffed by a skeleton organisation and were working to monitor the traffic of neighbouring states.
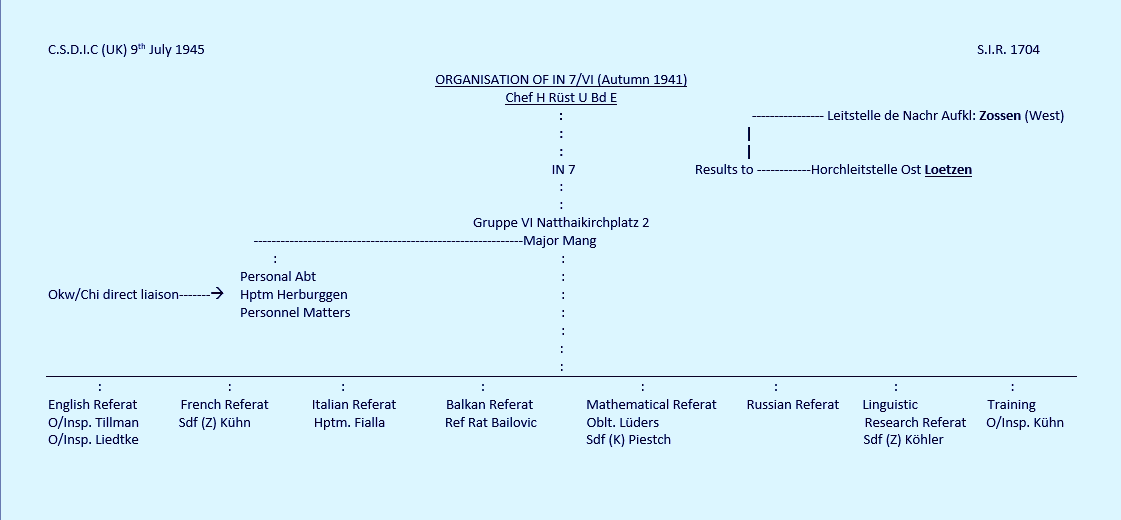
Inspectorate 7/VI organisation
In Autumn 1941, Inspectorate ''7/VI'' was divided into the following sections:
:::
Between 1941 and 1943, the following changes in ''OKH/Chi'' took place:
* The Russian Referat was sent to
Loetzen,
East Prussia
East Prussia was a Provinces of Prussia, province of the Kingdom of Prussia from 1772 to 1829 and again from 1878 (with the Kingdom itself being part of the German Empire from 1871); following World War I it formed part of the Weimar Republic's ...
.
* A Referat for cryptanalysis of USA systems was formed with the entry of the US into the war on 7 December 1941.
* A Referat for cryptanalysis of traffic of agents (foreign and internal) was added in 1943.
* The investigation of the security of the current German Army systems was transferred from ''In 7/VI'', the former Army Signal Security Agency, to the mathematical Referat of ''In 7/VI''.
* An
IBM
International Business Machines Corporation (using the trademark IBM), nicknamed Big Blue, is an American Multinational corporation, multinational technology company headquartered in Armonk, New York, and present in over 175 countries. It is ...
Referat together with its
machinery
A machine is a physical system that uses power to apply forces and control movement to perform an action. The term is commonly applied to artificial devices, such as those employing engines or motors, but also to natural biological macromolec ...
from ''In 7/IV'' was added.
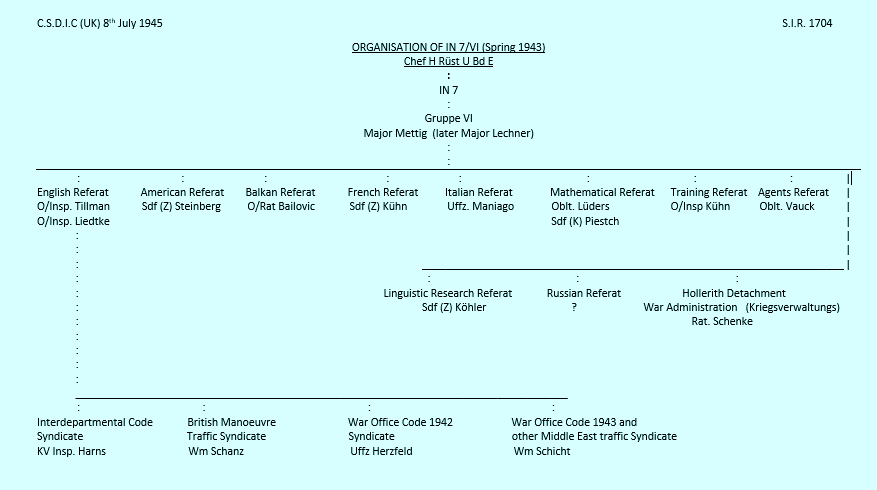
In the spring of 1943, ''OKH/Chi'' organisation was as follows:
::
The sections of ''In 7/VI'' were housed during this period in buildings near the
Bendlerstrasse in
Berlin
Berlin ( ; ) is the Capital of Germany, capital and largest city of Germany, by both area and List of cities in Germany by population, population. With 3.7 million inhabitants, it has the List of cities in the European Union by population withi ...
. The Headquarters Training Section and sections for USA, French and Agents traffic were located at Mattaekirchplatz 4; the British and Balkan sections were located at Schellingstrasse 9, with the
Hollerith machinery located at Viktoriastrasse. Location of the Mathematical section was not known. In November 1943, the first large RAF raid on Berlin destroyed a large part of the offices of the Army High Command on Bendlerstrasse in Berlin, among which were those of ''OKH/Chi''. ''In 7/VI'' was thereupon moved to
Jüterbog
Jüterbog () is a historic town in north-eastern Germany, in the Teltow-Fläming district of Brandenburg. It is on the Nuthe river at the northern slope of the Fläming hill range, about southwest of Berlin.
History
The Polabian Slavs, Slavic se ...
in Oct 1943, where it was located until its amalgamation in November 1944 into GdNA. No estimate is given of the number of people employed in ''In 7/VI''.
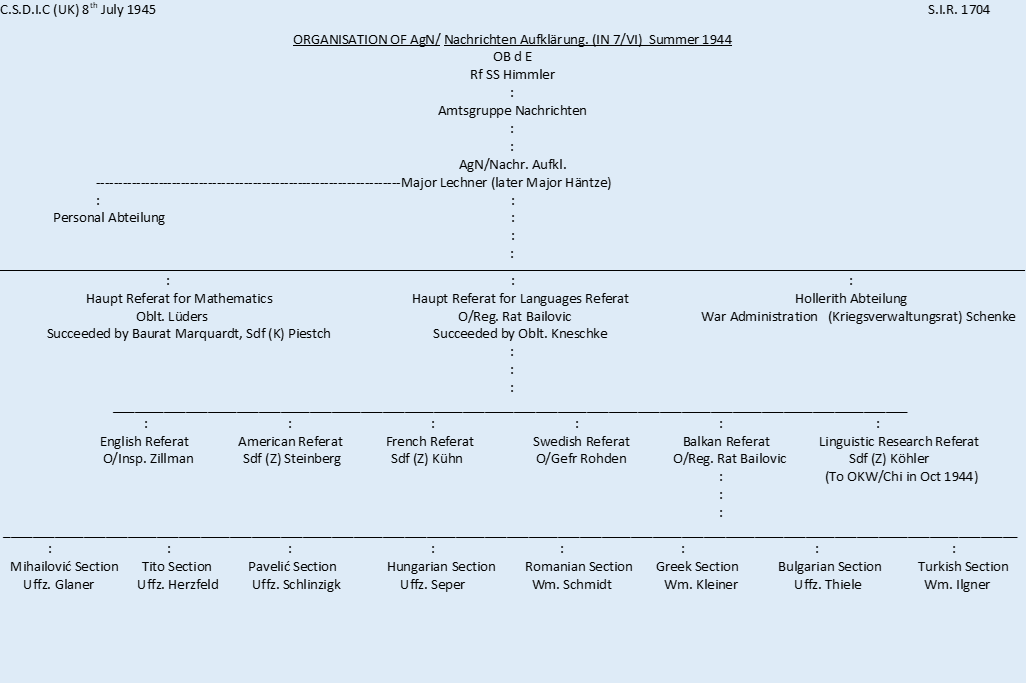
Organisation of AgN/NA
When ''In 7/VI'' was reorganised as the Signal Intelligence Section of the Department of signals of the General Army Office, of the Army High Command () (), the internal organisation was changed. The previously independent sections were organised into a main section () for mathematics, and a main section for languages. The
Hollerith section retained its autonomy.
The main section for languages, with the exception that one section was added for Swedish traffic, covered the same field as had been covered by the additional language sections of ''OKH/Chi''. The organisation of AgN/NA is as follows:
:::
Control Station For Intelligence LNA
The nature of this obscure unit was as an evaluation agency, which focused primarily on non Russian traffic. The unit which was called Control Station For Intelligence () () had sections for evaluating British, US, Italian, Balkan, Greek, Turkish, Tunisian, Near Eastern, Portuguese and Spanish traffic. Evaluation was made both of traffic and post decoded intercepts, passed to the unit from ''OKH/Chi''. This unit size of the LNA was small, and consisted of 75 military personnel.
HLS Ost
The Intercept Control Station East () () was the central cryptanalytic and evaluation centre for Russian traffic located at
Loetzen,
East Prussia
East Prussia was a Provinces of Prussia, province of the Kingdom of Prussia from 1772 to 1829 and again from 1878 (with the Kingdom itself being part of the German Empire from 1871); following World War I it formed part of the Weimar Republic's ...
from late 1941 to late 1944. The size of the unit was not known, but had the following organisation, as defined below:
::
In the winter of 1942–43, the
Baudot Reception Station was moved from
Minsk
Minsk (, ; , ) is the capital and largest city of Belarus, located on the Svislach (Berezina), Svislach and the now subterranean Nyamiha, Niamiha rivers. As the capital, Minsk has a special administrative status in Belarus and is the administra ...
to
Loetzen and subordinated to HLS Ost, Referat 4. The first director of HLS Ost was Colonel Hugo Kettler who would later become Chief of
OKW/Chi in the summer of 1943. During the summer of 1942, Kettler was succeeded by Baron Colonel Rudolf Von Der Osten-Sacken who remained its chief until July 1944 when he was implicated in the
20 July plot
The 20 July plot, sometimes referred to as Operation Valkyrie, was a failed attempt to assassinate Adolf Hitler, the chancellor and leader of Nazi Germany, and overthrow the Nazi regime on 20 July 1944. The plotters were part of the German r ...
on
Hitler's life and committed suicide.
Signal Intelligence Agency
The three agencies, ''OKH/Chi'' (lattery AgN/NA), HLS Ost and LNA were amalgamated in November 1944, into the Signal Intelligence Agency of the Army High Command () () almost intact. ''OKH/Chi'' had some personnel reassigned, and became Group IV of GdNA, which was assigned responsibility for all
cryptanalysis
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic se ...
on foreign military traffic. LNA was transferred as a unit to Group II of GDNA, except for those referats which had been dealing with wireless and news agency traffic. These section were assigned to Group I and GDNA. The various sections of HLS Ost were absorbed into the appropriate sections of GDNA as follows:
::
Organisation of GDNA

This organisation of OKH/GdNA was in effect from November 1944 to the end of the war. Approximately 700 people were employed by the unit.
*''Headquarters Unit''. The HQ unit of OKH/GDNA, was managed by () (colonel)
Fritz Boetzel, his chief of staff, (lieutenant colonel) Andrea, the Adjutant Lieutenant Moravec and staff officer Lieutenant () Koebe. As well as all staff being subordinate to the unit, the unit also controlled two intercept stations, Feste 6 and Feste 11 (
KONA Unit), who specialised in intercepting
high frequency
High frequency (HF) is the ITU designation for the band of radio waves with frequency between 3 and 30 megahertz (MHz). It is also known as the decameter band or decameter wave as its wavelengths range from one to ten decameters (ten to one ...
traffic of the
Red Army
The Workers' and Peasants' Red Army, often shortened to the Red Army, was the army and air force of the Russian Soviet Republic and, from 1922, the Soviet Union. The army was established in January 1918 by a decree of the Council of People ...
and the
NKVD
The People's Commissariat for Internal Affairs (, ), abbreviated as NKVD (; ), was the interior ministry and secret police of the Soviet Union from 1934 to 1946. The agency was formed to succeed the Joint State Political Directorate (OGPU) se ...
The officers and men of the unit supervised the intercept traffic requirements of the KONA units and their subordinate units, directly in the case of KONA 1, 2,3,7, and 8, and through the Senior Commander of Signal Intelligence () () for KONA 5 and KONA 6. In October 1944, the HQ was run by Lieutenant Colonel () Andrea, Chief of Staff was Colonel () Köbe, with Group Z being run by Major () Hüther.
:The authority of the staff was exclusively in matters of intelligence policy and did not extend direct to intercept units in the field. It could however liaise with these through the unit staff. The final responsibility for policy, issue of intercept reports and allocation of work within the groups lay with staff HQ.
*''Group () I'': This unit was directed by
Amtmann
__NOTOC__
The ''Amtmann'' or ''Ammann'' (in Switzerland) was an official in German-speaking countries of Europe and in some of the Nordic countries from the time of the Middle Ages whose office was akin to that of a bailiff
A bailiff is a ...
Bodenmüller and was responsible for two main tasks:
:* The first task was the maintenance of communications between the units of the GdNA.
::The signals officer of the group, Inspector Strahlendorf was in charge of a wireless centre and teleprinter centres of a network connecting to the outlying units of the HQ.
Teleprinter
A teleprinter (teletypewriter, teletype or TTY) is an electromechanical device that can be used to send and receive typed messages through various communications channels, in both point-to-point (telecommunications), point-to-point and point- ...
was the preferred method of communication unit the end of the war, when radio was used. In the middle of April 1945, a plan was evolved for creating wireless stations in occupied parts of Germany for intercept purposes. Comms with these stations was to be maintained by the wireless centre of the GdNA. The plan was abandoned. Personnel employed by the comms unit were almost exclusively women.
:* The second was wireless monitoring. This section was known as Radio Reception Point () and was commanded by Wm Pretterebner. This unit had four subsections:
::*Referat Ia: The broadcast monitoring East () unit monitored eastern wireless.
:::Owing to personnel shortage its efforts were restricted to monitoring the
Moscow
Moscow is the Capital city, capital and List of cities and towns in Russia by population, largest city of Russia, standing on the Moskva (river), Moskva River in Central Russia. It has a population estimated at over 13 million residents with ...
wireless. Latterly, a certain amount of Balkan monitoring was instituted particularly for
Turkey
Turkey, officially the Republic of Türkiye, is a country mainly located in Anatolia in West Asia, with a relatively small part called East Thrace in Southeast Europe. It borders the Black Sea to the north; Georgia (country), Georgia, Armen ...
and
Romania
Romania is a country located at the crossroads of Central Europe, Central, Eastern Europe, Eastern and Southeast Europe. It borders Ukraine to the north and east, Hungary to the west, Serbia to the southwest, Bulgaria to the south, Moldova to ...
::*Referat Ib: The broadcast monitoring West () of western wireless.
:::Owing also to personnel shortages this unit only monitored the BBC London Service.
::*Referat Ic: The Plain text monitoring () unit.
:::This unit was responsible for the intercept activity which concentrated on the
Reuters
Reuters ( ) is a news agency owned by Thomson Reuters. It employs around 2,500 journalists and 600 photojournalists in about 200 locations worldwide writing in 16 languages. Reuters is one of the largest news agencies in the world.
The agency ...
agency.
::*Referat Ic: An evaluation section.
:::This section was responsible for collating all information from the other three sections and consolidating it into reports. The collated reports were divided into separate parts for political, economic or military news. They were circulated within the departments of the Army High Command (OKH), sometimes with the classification TOP SECRET () (). Special news flashed on items of urgent importance were also issued.
*''Group II'': This unit which was known as End Evaluation WEST () was commanded by Major Thiel. Formally group II was known as LNA West and was located at the
Zeppelin bunker near
Zossen, and had a personnel count of around 50 people, producing radio situation reports correlating the information from KONA 5, KONA 6 and KONA 7. Captain Thiel, who was head of this group, had been with the LNA for a long time, and was thoroughly familiar with the problems of western evaluation. The evaluation sub-section was responsible for collating all information received from the three Referat in Group I and consolidating them into reports. Collated reports were issued, divided into separate parts for political, economic or military news. The reports were circulated within various departments of the OKH. Frequently, and owing to the political nature of the information, the reports were graded ''GKdos'' (Top Secret) although they were obtained merely from monitoring enemy wireless news. Special news flashes on items of urgent importance were also issued.
*''Group III'': This unit was known as End Evaluation EAST ). Captain () Gorzolla was responsible for this unit. This unit undertook evaluation of intercept traffic and cryptanalytic work emanating from the Eastern European Front, e.g.
Soviet Union
The Union of Soviet Socialist Republics. (USSR), commonly known as the Soviet Union, was a List of former transcontinental countries#Since 1700, transcontinental country that spanned much of Eurasia from 1922 until Dissolution of the Soviet ...
.
::: With the HQ of Group III, there was a special receiving office through which all messages emanating from the forward intercept units and fixed stations were passed. At the reception office, the unit originating the message was identified by the call signs used. Undecipherable messages were thence passed immediately to Group IV for deciphering and messages which were already in plain text were passed to the special evaluation sub-sections according to the nature of the traffic. In addition, deciphered messages were passed back from the Gruppe IV through the reception office for evaluation. The head office of Groupe III kept a central card index in which call signs, cipher indicator groups and contents of messages were registered.
:The department was subdivided into the following sections:
:*Referat IIIa: Traffic Sorting Office.
:*Referat IIIb: Northern Sector Evaluation.
:*Referat IIIc: Central Sector Evaluation.
:*Referat IIId: Southern Sector Evaluation.
:*Referat IIIe: People's Commissariat for Internal Affairs (
NKVD
The People's Commissariat for Internal Affairs (, ), abbreviated as NKVD (; ), was the interior ministry and secret police of the Soviet Union from 1934 to 1946. The agency was formed to succeed the Joint State Political Directorate (OGPU) se ...
) Evaluation.
:*Referat IIIf: Partisan traffic evaluation.
:*Referat IIIg: Swedish traffic evaluation.
::Sources of information for the evaluation unit were
call signs
In broadcasting and radio communications, a call sign (also known as a call name or call letters—and historically as a call signal—or abbreviated as a call) is a Identifier, unique identifier for a transmitter station. A call sign can be fo ...
,
cipher indicator groups and D/F reports. Using these it was possible to establish a detailed
order of battle
Order of battle of an armed force participating in a military operation or campaign shows the hierarchical organization, command structure, strength, disposition of personnel, and equipment of units and formations of the armed force. Various abbr ...
. Surnames were considered an exceptionally valuable source of intelligence since they were used so infrequently in Russian traffic dealing with promotion and transfer. Surnames about Major were tracked in a card index. The evaluation of NKVD traffic was equally valuable since reinforcements and movements of NKVD traffic normally indicated similar movements in the
Red Army
The Workers' and Peasants' Red Army, often shortened to the Red Army, was the army and air force of the Russian Soviet Republic and, from 1922, the Soviet Union. The army was established in January 1918 by a decree of the Council of People ...
Field Army. They also gave a good indication of lines of communication. Partisan traffic was also intercepted, for appropriate countermeasures.
*''Group IV'': Major Rudolf Hentze was responsible for all cryptanalytic work done at GdNA. It was one of the largest groups within the GdNA, having been built up from parts of the three former agencies: The defunct ''OKH/Chi'', LNA West at
Zossen and the HLS East at
Lötzen. The HLS East group, which operated in Loetzen, East Prussia, during 1942–1944, intercepted Soviet teletype transmissions. This unit was captured wholesale in May 1945 in
Rosenheim
Rosenheim () is a city in Bavaria, Germany. It is an independent city located in the centre of the Rosenheim (district), district of Rosenheim (Upper Bavaria), and is also the seat of its administration. It is located on the west bank of the Inn ...
, Germany, by the Allies, and transported by TICOM and put to work so their methods could be evaluated. The Allies then either directly copied the German equipment, or built similar models and used them to intercept the internal Soviet network traffic.
:::The unit was divided into separate Referat according to the origin of the material. Material dealt with in the Group IV, consisted of traffic which the forward intercept units had intercepted but had been unable to decipher. A certain amount of special traffic was also intercepted by the Feste attached to the GDNA.
:*Referat I: The mathematician, Dr Hans Pietsch was responsible for the unit. It was responsible for analytical research. It was the former Mathematical Section of ''OKH/Chi''. It was responsible for the security of German Army Systems.
::*Referat Ia: The subsection was headed by
Johannes Marquart, and was engaged in research on German Army hand cryptanalytic systems.
::*Referat Ib: This subsection was managed by Dr Pietsch, handling research on German Army machine systems.
:::*Subsection F:This subsection designated ''F'' for the German word for research (). This subsection was headed by
Herbert von Denffer and handled research on foreign systems.
Otto Buggisch rated Herbert von Denffer as the most capable cryptanalyst within the German Armed Forces.
:::*Subsection 7:This subsection dealt with the security of German hand systems.
:::*Subsection 13:This subsection was heading by Dr S. Döring and dealt with the security of own machinery and process of German Army machine systems.
:*Referat II: Headed by the mathematician Dr
Alfred Kneschke, it dealt with the cryptanalysis and deciphering of non-Russian traffic. It had three sub-sections:
::*Referat IIa: Cryptanalysis and decoding of British, USA and Swedish systems. This unit was managed by Dr Werner Schulze. Ludwig Falter worked as an English interpreter, mathematician and cryptanalyst on the British desk.
::*Referat IIb: Cryptanalysis and decoding of French, Spanish, Portuguese, Brazilian and Swiss systems. This unit was managed by Otto Kühn. Most of the volume of traffic from these countries was extremely small and was thus was unimportant.
::*Referat IIc: Cryptanalysis and decoding of Balkan systems. This unit was managed by
Alfred Kneschke, previously Giesler, previously Dr
Rudolf Bailovic.
:*Referat III: This subsection was managed by Lieutenant Alexis Dettman. The section was composed of the cryptanalytic sections of HLS Ost. It dealt with the Russian systems and had four sub-sections:
::*Referat IIIa: Cryptanalysis of NKVD traffic.
::*Referat IIIb: Cryptanalysis of Russian army traffic.
::*Referat IIIc: Cryptanalysis of Partisan traffic.
::*Referat IIId: Cryptanalysis of Russian systems.
:*Referat IV: This unit was the former Hollerith machinery section of ''OKH/Chi''. This section performed mainly
statistical
Statistics (from German language, German: ', "description of a State (polity), state, a country") is the discipline that concerns the collection, organization, analysis, interpretation, and presentation of data. In applying statistics to a s ...
work. Most of the members of the unit were women used to run the machinery. The section maintained its own repair shop for the machines.
:*Referat V: This unit was the training department of the GdNA where cryptographic and cryptanalytic courses were given under the direction of Inspector Kuehn, who had headed the Training section of ''OKH/Chi''. During the last months of the war, the once flourishing section dwindled to a group of 40 students every three months.
*''Group V'': This unit was commanded by
Amtmann
__NOTOC__
The ''Amtmann'' or ''Ammann'' (in Switzerland) was an official in German-speaking countries of Europe and in some of the Nordic countries from the time of the Middle Ages whose office was akin to that of a bailiff
A bailiff is a ...
Block. It had a fair wide field of activity. It had a mixed group containing three Referat all of which carried out unrelated work.
::*Referat I: This section was named () headed by Inspector Zipper, and was engaged in reconstructing Russian, British and USA
call sign
In broadcasting and radio communications, a call sign (also known as a call name or call letters—and historically as a call signal—or abbreviated as a call) is a unique identifier for a transmitter station. A call sign can be formally as ...
s and call signs systems, and deducing units therefrom. It covered various procedures of enemy wireless traffic and the allocation of
wave lengths.
::*Referat II: This section managed specifically by Amtmann Block was responsible for the exploitation of captured Russian documents and manuals of signals interest. Captured manuals were translated and descriptions of Russian equipment examined. By April 1945, the Referat II had completed an up-to-date booklet on Russian abbreviations, which was ready for publication. This book was to have been made available to all forward intercept units.
::*Referat III: This section had two tasks. The first was engaged in supplying the KONA signal intelligence regiments with the necessary intercept equipment and in maintaining a workshop to service the needs of the GdNA HQ itself.
*''Group VI'': This unit was located in
Potsdam
Potsdam () is the capital and largest city of the Germany, German States of Germany, state of Brandenburg. It is part of the Berlin/Brandenburg Metropolitan Region. Potsdam sits on the Havel, River Havel, a tributary of the Elbe, downstream of B ...
under Captain () Röder, and was responsible for intercepting and evaluating special high-grade machine systems.
:*Referat I, with three sub-sections, handled Russian Systems:
::*Sub-Section Ia: This section was responsible for interception and evaluation of Inter-Soviet State traffic, picked up on
Baudot traffic.
:::On the basis of this, the () () bulletins were compiled. These bulletins gave a detailed summary of Russian economic situation, particularly in the areas of Moscow,
Baku
Baku (, ; ) is the Capital city, capital and List of cities in Azerbaijan, largest city of Azerbaijan, as well as the largest city on the Caspian Sea and in the Caucasus region. Baku is below sea level, which makes it the List of capital ci ...
,
Rostov and included production figures and details of supply and labour conditions. About 30 copies of this report were issued. Detailed card indexes were kept, which included names and locations of factories and personalities therein.
::*Sub-Section Ib: Interception and evaluation of Russian
Baudot.
:::The unit consisted of two cryptographers who undertook research into the cipher machines employed for Baudot traffic forward of GHQ Moscow. They also assisted Referat Ic in preliminary evaluation.
::*Sub-Section Ic: Interception and evaluation of Russian Army traffic.
:::This section picked up Inter-Soviet and Red Army Baudot traffic and dealt with the preliminary evaluation of Ref Army Baudot traffic. Based on this analysis, a situation report was brought out, giving the Order of Battle, personalities, frequencies, call signs and cipher indicator groups used in the traffic. This was passed to Group III for evaluation. Referat Ib carried out joint initial evaluation.
:*Referat II had two sub-sections. Inspector Heller was responsible for this unit.
::*Sub-Section IIa: Interception of western
teleprinter
A teleprinter (teletypewriter, teletype or TTY) is an electromechanical device that can be used to send and receive typed messages through various communications channels, in both point-to-point (telecommunications), point-to-point and point- ...
and automatic
morse traffic intercepts.
::*Sub-Section IIb: Evaluation of the intercepts from section 2a.
*''Group Z'': This unit was responsible for general administrative control of all departments with OKH/GdNA. The work was divided into four types:
:*Personnel: A central card index was kept for all personnel employed with the GdNA. The unit was also responsible for all transfers, either interdepartmental or outside the unit.
:*Registry Office (). This communications unit registered all incoming and outgoing correspondence and was responsible for all courier communications between HT General GDNA and its outlying subordinate units. For local communications, the registry had its own runners, but for long distances, the courier services of the Army High Command (OKH) were used. In addition, the Registry Office duplicated some reports for the individual groups.
:*Paymaster. All of OKH/GdNA were paid by this section.
:*Drawing. This unit managed the production of situation maps and maps of WT radio networks were produced.
Mimeograph
A mimeograph machine (often abbreviated to mimeo, sometimes called a stencil duplicator or stencil machine) is a low-cost duplicating machine that works by forcing ink through a stencil onto paper. The process is called mimeography, and a co ...
and
Bookbinding
Bookbinding is the process of building a book, usually in codex format, from an ordered stack of paper sheets with one's hands and tools, or in modern publishing, by a series of automated processes. Firstly, one binds the sheets of papers alon ...
activity was also carried on here.
Signal intelligence operations
Intercept Control Station
HLS before World War II was principally engaged in intercepting traffic from
France
France, officially the French Republic, is a country located primarily in Western Europe. Overseas France, Its overseas regions and territories include French Guiana in South America, Saint Pierre and Miquelon in the Atlantic Ocean#North Atlan ...
,
Belgium
Belgium, officially the Kingdom of Belgium, is a country in Northwestern Europe. Situated in a coastal lowland region known as the Low Countries, it is bordered by the Netherlands to the north, Germany to the east, Luxembourg to the southeas ...
,
Netherlands
, Terminology of the Low Countries, informally Holland, is a country in Northwestern Europe, with Caribbean Netherlands, overseas territories in the Caribbean. It is the largest of the four constituent countries of the Kingdom of the Nether ...
,
Poland
Poland, officially the Republic of Poland, is a country in Central Europe. It extends from the Baltic Sea in the north to the Sudetes and Carpathian Mountains in the south, bordered by Lithuania and Russia to the northeast, Belarus and Ukrai ...
, and
Russia
Russia, or the Russian Federation, is a country spanning Eastern Europe and North Asia. It is the list of countries and dependencies by area, largest country in the world, and extends across Time in Russia, eleven time zones, sharing Borders ...
;
Switzerland
Switzerland, officially the Swiss Confederation, is a landlocked country located in west-central Europe. It is bordered by Italy to the south, France to the west, Germany to the north, and Austria and Liechtenstein to the east. Switzerland ...
was only casually monitored. The main successes were gained at the expense of France, Netherlands and Russia.
Russia
HLS was able during the first
Russo-Finnish War to break a number of Russian 2,3 and 4-figure codes. In addition, a copy of the Russian 5-digit code was obtained, which was handed over to the Finish General Staff (
Finnish radio intelligence). That particular code was used by the Russians in the first year of the war with Germany in 1939.
Netherlands
An exercise of the
Dutch Army was covered in 1937. Very simple techniques, principally
double transposition cipher
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure. An alternative, less common term is ''encipherment''. To encipher or encode i ...
s, were used and these could be read without much difficulty. As a result, it was possible to establish the
Order of battle
Order of battle of an armed force participating in a military operation or campaign shows the hierarchical organization, command structure, strength, disposition of personnel, and equipment of units and formations of the armed force. Various abbr ...
of the Dutch units participating in the exercise down to the
battalion
A battalion is a military unit, typically consisting of up to one thousand soldiers. A battalion is commanded by a lieutenant colonel and subdivided into several Company (military unit), companies, each typically commanded by a Major (rank), ...
level.
France
Continuous and significant successes were obtained against the French (
Deuxième Bureau) before the war. Before 1939, HLS Ost covered the French static wireless net which radiated from Paris to the static formations in France. Cipher procedures were continuously read, and provided valuable information during the international crisis of 1937, Spring and Summer 1938 and 1939.
Britain
Very little success was obtained in the reading of British ciphers before the war, principally due to the low quality of the personnel involved.
Inspectorate 7/VI operations
Static period 1939 to 1940
The signal intelligence picture provided during the early period of the war was good. The complete picture of British, French and Dutch orders of battle was available. Changes in that order could always be followed. The French, Belgium and Dutch picture was partly obtained as a result of cryptanalysis achievements, the
order of battle
Order of battle of an armed force participating in a military operation or campaign shows the hierarchical organization, command structure, strength, disposition of personnel, and equipment of units and formations of the armed force. Various abbr ...
of the
British Army
The British Army is the principal Army, land warfare force of the United Kingdom. the British Army comprises 73,847 regular full-time personnel, 4,127 Brigade of Gurkhas, Gurkhas, 25,742 Army Reserve (United Kingdom), volunteer reserve perso ...
could only be built up by the results of Direction-Finding () information, and the evaluation of call-signs and other items of the wireless traffic procedure.
=France
=
In 1939, ''OKH/Chi''
cryptanalysed the ''mobile'' cipher which had replaced the peacetime cipher of the static French wireless net with the outbreak of war. All messages of an administrative or supply nature, nevertheless, helped to fill in the tactical picture, e.g. the strength of units being created on the training ground at
Camp de Châlons at
Mourmelon-le-Grand, was estimated by statistics of water bottles and blankets. It was equally possible to deduce facts about the shortage of armour-piercing ammunition with the French infantry units. Similarly, the conversion of the 2nd and
3rd Cuirassier Regiment to
armoured division status in the area northeast of
Paris
Paris () is the Capital city, capital and List of communes in France with over 20,000 inhabitants, largest city of France. With an estimated population of 2,048,472 residents in January 2025 in an area of more than , Paris is the List of ci ...
was ascertained in December 1939. Likewise, the order of battle of the
French 6th Army on the French-Italian border was well known.
=Poland
=
According to Metting, that owing to the speedy development of the
Polish campaign
The invasion of Poland, also known as the September Campaign, Polish Campaign, and Polish Defensive War of 1939 (1 September – 6 October 1939), was a joint attack on the Republic of Poland by Nazi Germany, the Slovak Republic, and the Soviet ...
, very little cryptographic work was undertaken. The main signal intelligence information on the regrouping of the Polish forces was derived from the Polish relay wireless traffic which was believed to be carried out in
Plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
.
German offensive May–June 1940
=France
=

With the opening of the
Battle of France
The Battle of France (; 10 May – 25 June 1940), also known as the Western Campaign (), the French Campaign (, ) and the Fall of France, during the Second World War was the Nazi Germany, German invasion of the Low Countries (Belgium, Luxembour ...
in May 1940, the French began to use ciphers in increasing quantities. Germany at this point suffered an acute shortage of forward
cryptographers
This is a list of cryptographers. Cryptography is the practice and study of techniques for secure communication in the presence of third parties called adversaries.
Pre twentieth century
* Al-Khalil ibn Ahmad al-Farahidi: wrote a (now lost) book ...
and was therefore unable to undertake much work on the French forward ciphers. As a result, the forward units concentrated on the two French cipher machines, the
B-211, which was an electromechanical cipher machine, designed and built by
Boris Hagelin
Boris Caesar Wilhelm Hagelin (2 July 1892 – 7 September 1983) was a Swedish businessman and inventor of encryption machines.
Biography
Born of Swedish parents in Adshikent, Russian Empire (now Azerbaijan), Hagelin attended Lundsberg boardin ...
for use by the
French Army
The French Army, officially known as the Land Army (, , ), is the principal Army, land warfare force of France, and the largest component of the French Armed Forces; it is responsible to the Government of France, alongside the French Navy, Fren ...
and the
C-36. Progress was slow, but as the result of the research on two captured C-36 machines,
Army Group C
Army Group C () was an army group of the German Wehrmacht during World War II. In its first deployment between 1939 and 1941, its main assignment was the defense of the Franco-German border during the Phony War and the Western Campaign, after whi ...
was in a position by July 1940 to undertake satisfactory reading of the traffic. Likewise, it was impossible to break the B-211 machine in time for that information to be of any value. Nevertheless, the research undertaken during this period was to justify the results later.
=United Kingdom
=
Although similar successes were achieved against the Dutch and Belgian ciphers, Germany still failed to break into any important British procedures. The English desk cryptanalysts, consisting of six personnel from the HLS, were put to work while located in
Bad Godesberg, but in spite of a plentiful supply of intercepts, they failed to achieve any successes.
=Supplies of cryptanalysts in the west 1939 to 1940
=
When the forward intercept units moved into the field in 1939, no cryptanalysts were available. Kunibert Randewig, the commander of all units in the west, was able to procure a number of cryptanalysts from intercept stations around Berlin and filled that number out by calling in a number of mathematicians and linguists including translators and language interpreters from the statistical offices of insurance companies. As a result, when the offensive started in April 1940, the intercept stations with the army groups, contrived to have a moderate supply of cryptanalyst personnel.
Reorganisation of Inspectorate 7
The experience of 1940 showed that considerable expansion in the German Army cryptographic service was desirable. This organisation was carried out by Major Mang. His aim was not only to increase the cryptanalysis staff at the centre, but also to provide reserves of
cryptography
Cryptography, or cryptology (from "hidden, secret"; and ''graphein'', "to write", or ''-logy, -logia'', "study", respectively), is the practice and study of techniques for secure communication in the presence of Adversary (cryptography), ...
to work in certain key areas. The cryptanalysis section thereupon became independent and was reorganised as Group VI of In 7. Henceforth it was subordinated to the reserve army for personnel and administrative matters, but remained subordinated to Chef HNW of Field Army, just as Horchleitstelle was converted to Group IV. Nevertheless, this curious form of organisation paid, and enabled the cryptographic service to recruit sufficient personnel without serious interference.
In general, the object of ''OKH/Chi'' was the organisation of cryptanalysis in the field and in the rear; training of cryptographers and the investigation of the security of German
Cipher
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a procedure. An alternative, less common term is ''encipherment''. To encipher or encode i ...
s
It was also felt that in certain critical regions, an extra cryptanalytic effort should be enforced, to help in the cryptanalysis of
War Office
The War Office has referred to several British government organisations throughout history, all relating to the army. It was a department of the British Government responsible for the administration of the British Army between 1857 and 1964, at ...
cipher W, the
British Army
The British Army is the principal Army, land warfare force of the United Kingdom. the British Army comprises 73,847 regular full-time personnel, 4,127 Brigade of Gurkhas, Gurkhas, 25,742 Army Reserve (United Kingdom), volunteer reserve perso ...
's universal high-grade codebook, which carried traffic between
Whitehall
Whitehall is a road and area in the City of Westminster, Central London, England. The road forms the first part of the A roads in Zone 3 of the Great Britain numbering scheme, A3212 road from Trafalgar Square to Chelsea, London, Chelsea. It ...
, commands, armies, corps and later divisions. To this end, the Russian Referat of ''OKH/Chi'' was detached to the Horchleitstelle
Lötzen, while special cryptanalysis sections for British traffic were detached to the Horch kp in the
Middle East
The Middle East (term originally coined in English language) is a geopolitical region encompassing the Arabian Peninsula, the Levant, Turkey, Egypt, Iran, and Iraq.
The term came into widespread usage by the United Kingdom and western Eur ...
under the command of Seebaum and Commander of Signals Troops () in
Athens
Athens ( ) is the Capital city, capital and List of cities and towns in Greece, largest city of Greece. A significant coastal urban area in the Mediterranean, Athens is also the capital of the Attica (region), Attica region and is the southe ...
.
=Reorganisation of Referat
=
In 1942, the Mathematical Referat had expanded to such an extent that three sections were created out of it. Steinberg and the mathematicians who had been working with him on the
M-209 cipher machine and the
strip cipher separated to form the American Referat while two separate sections were formed, one under Lüders for the investigation of cipher security and security of own processes, and one under Dr Döring for the investigation of secret
teleprinter
A teleprinter (teletypewriter, teletype or TTY) is an electromechanical device that can be used to send and receive typed messages through various communications channels, in both point-to-point (telecommunications), point-to-point and point- ...
s.
=Work on Hollerith Referat
=
The Hollerith Referat was commanded by Baurat Schenke. The department was equipped with all kinds of German machines and also with all kinds of French
Hollerith equipment. This department proved invaluable in the investigations of unclear or difficult cipher techniques. A lot of time and manpower was saved, particularly in the sorting of traffic and the ascertaining of parallelisms and in the calculation of recurring differences. Contrast this with the
Cipher Department of the High Command of the Wehrmacht
The Cipher Department of the High Command of the Wehrmacht () (also ''Oberkommando der Wehrmacht Chiffrierabteilung'' or ''Chiffrierabteilung of the High Command of the Wehrmacht'' or ''Chiffrierabteilung of the OKW'' or ''OKW/Chi'' or ''Chi'') ...
(), the organisation that ''In 7/VI'' grew out of. The OKW/Chi cipher bureau did not have a Hollerith machinery department, hence custom mechanical aids had to be built, termed
Rapid analytic machinery that were time-consuming to build and costly, and only worked in specifically defined areas, whereas Hollerith machines were generic in nature. The exploitation of Hollerith methods was particularly favoured by Baurat Schulze, who in civilian life was an employee of Hollerith company at
Lankwitz in Berlin.
=Work on Mathematical Referat
=
Baurat Dr Hans Pietsch collected together in this section the best available mathematicians. In this section all unbroken intercept traffic from the country desks was investigated for however long it to achieve initial cryptanalysis by purely analytical methods. As soon as a technique for breaking a particular cipher was evolved, they handed back for further work to the specific country desk concerned. In some cases mathematical specialists were attached to a specific desk to work on various procedures.
A further large field of work undertaken at the Mathematical Referat was the investigation of the security of the current German cipher procedures, i.e. security own processes, and in the assessment of discoveries that were always being brought forward. The compromise of the security of a cipher usually resulted from exceeding the days safety margin for transmission, thus creating
Depth or by other breaches of standard operating instructions.
In order to provide some check on the use of German ciphers and to provide the Mathematical Referat with the necessary material, the News Reconnaissance Division/Chief of Army Equipment and Commander of the Replacement Army ( ()) was created in Berlin during November 1941. Two companies of this unit were to act as normal holding companies for ''In 7/VI'', while the third was an intercept company which worked within the field and for the Reserve Army for collecting material to use to build statistical models to determine the efficacy of German ciphers. However, at the end of February 1942, this unit was dissolved owing to personnel shortages. Thus the control of cipher security became once more the responsibility of the Field Army, a responsibility which was never fully undertaken.
As a result of the security investigation of German ciphers and the reporting of new discoveries, Pietsch's Referat naturally began to develop new cipher techniques of its own. In 1942, however, the development of these techniques was handed over to OKW/Chi. However, by the time the organisation had morphed into the OKH/GDNA, it had been specifically banned from intercepting and attacking German traffic as a security precaution.
The main investigation carried out by the Mathematical Referat was a continual enquiry into the security of the main German cipher machines:
Enigma machine
The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication. It was employed extensively by Nazi Germany during World War II, in all branches of the W ...
. The cause of this anxiety lay in the fact that it had been established before the war that
Czechoslovakia
Czechoslovakia ( ; Czech language, Czech and , ''Česko-Slovensko'') was a landlocked country in Central Europe, created in 1918, when it declared its independence from Austria-Hungary. In 1938, after the Munich Agreement, the Sudetenland beca ...
in collaboration with
France
France, officially the French Republic, is a country located primarily in Western Europe. Overseas France, Its overseas regions and territories include French Guiana in South America, Saint Pierre and Miquelon in the Atlantic Ocean#North Atlan ...
had been able to read traffic enciphered by the Enigma machine. This was named as an old model, without
plugboard
A plugboard or control panel (the term used depends on the application area) is an array of jack (connector), jacks or sockets (often called hubs) into which patch cords can be inserted to complete an electrical circuit. Control panels are som ...
and socket connections, possibly describing a
commercial Enigma K. Evidence on this subject was captured during the
occupation of Czechoslovakia during 1938. Moreover, in
Poland
Poland, officially the Republic of Poland, is a country in Central Europe. It extends from the Baltic Sea in the north to the Sudetes and Carpathian Mountains in the south, bordered by Lithuania and Russia to the northeast, Belarus and Ukrai ...
in 1939, the
plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
version of a wireless transmission () message was found; this message has been transmitted from a German cruiser in Spanish waters during the
Spanish Civil War
The Spanish Civil War () was a military conflict fought from 1936 to 1939 between the Republican faction (Spanish Civil War), Republicans and the Nationalist faction (Spanish Civil War), Nationalists. Republicans were loyal to the Left-wing p ...
, and had been transmitted using Officers Keys. An exact proof as to whether these successes were due to compromise, or to cryptanalysis, despite detailed investigation, is not known. As this instance of compromise affected the ''Stecker Enigma'', investigations were carried out thoroughly. The
Biuro Szyfrów
The Cipher Bureau ( Polish: ''Biuro Szyfrów'', ) was the interwar Polish General Staff's Second Department's unit charged with SIGINT and both cryptography (the ''use'' of ciphers and codes) and cryptanalysis (the ''study'' of ciphers and cod ...
located in the right wing of the
Saxon Palace in
Warsaw
Warsaw, officially the Capital City of Warsaw, is the capital and List of cities and towns in Poland, largest city of Poland. The metropolis stands on the Vistula, River Vistula in east-central Poland. Its population is officially estimated at ...
was searched in 1939. In subsequent years, in 1943, and 1944, General
Erich Fellgiebel ordered the re-interrogation of two captured Polish cryptanalysts to check this point. This was the so-called
Der Fall Wicher (Case Wicher). In 1943–44, the two Polish officers, who were being held in a PoW camp in Hamburg ''volunteered'' the information to Pietsch, that the Enigma was being read several years before the war, considering the fact that after so long a period, the information was no longer valuable.
Nevertheless, these investigations revealed that the safety margin of the Enigma cipher machine had to be reduced from 50,000 to 20,000 letters on a day's cipher (an experience which resulted in the daily cipher, which at the beginning of the
Russian campaign was very heavily burdened, being split up into two or three portions). As the final result of the investigations described above, the value of carrying out investigations into machine ciphers of enemy nations was recognised and the process undertaken.
=Russian Referat
=
This department had a curious history in that it was detached to Chef NNW Horchleitstelle at
Lötzen before the outbreak of hostilities with
Russia
Russia, or the Russian Federation, is a country spanning Eastern Europe and North Asia. It is the list of countries and dependencies by area, largest country in the world, and extends across Time in Russia, eleven time zones, sharing Borders ...
. Under the leadership of War Administration Inspector () Dettman, and for a time under Professor
Peter Novopashenny, this unit achieved considerable initial success until spring 1942. The
5-figure code was acquired by the Germans during the
Winter War
The Winter War was a war between the Soviet Union and Finland. It began with a Soviet invasion of Finland on 30 November 1939, three months after the outbreak of World War II, and ended three and a half months later with the Moscow Peac ...
of 1939–1940, and was still used by the Russians, two years later. An additional copy of this procedure was also captured by Germany. Through the allocation of call signs and of
indicator groups, it was possible to establish the entire Russian order of battle and the location of strategic reserves. This was additional to intelligence gained by reading the content of traffic. On 1 April 1942, the Russians introduced a new
5-figure code. The migration from the old to the new cipher was so faulty that within the first week it was possible to establish 2000 groups of the new code. Indeed, it was possible at that time to leave the decoding to the front line NAZ unit cryptanalysts, instead of at the rear at the large centralised Signal Intelligence Evaluation Centre (NAAS) unit. The Russians gradually improved their security, and by spring 1943, altered the indicator group system and split up the code, making it specific to various front sectors. As a result, it was necessary to collect all the 5-figure traffic at
Lötzen and to call in the assistance of the Hollerith Referat of ''OKH/Chi''. Only by this method was the necessary depth on a days traffic, achieved. The quantity of traffic read decreased considerably. 2,3 and 4-digit traffic was continuously decoded.
Cryptanalysis work on
partisan
Partisan(s) or The Partisan(s) may refer to:
Military
* Partisan (military), paramilitary forces engaged behind the front line
** Francs-tireurs et partisans, communist-led French anti-fascist resistance against Nazi Germany during WWII
** Ital ...
traffic was carried out by the forward Long Range Signal Intelligence Platoons in the area. Particular successes were achieved in the
Smolensk
Smolensk is a city and the administrative center of Smolensk Oblast, Russia, located on the Dnieper River, west-southwest of Moscow.
First mentioned in 863, it is one of the oldest cities in Russia. It has been a regional capital for most of ...
area with the arrival of specialist cryptanalysts and translators.
It was in the summer of 1943 when
KONA 6 with Oberleutnant Schubert in charge, was committed to anti-partisan work, that the traffic between
Moscow
Moscow is the Capital city, capital and List of cities and towns in Russia by population, largest city of Russia, standing on the Moskva (river), Moskva River in Central Russia. It has a population estimated at over 13 million residents with ...
and the partisans was successfully read.
=British Referat
=
This referat commanded by Zillman was assisted in its early days by the successes of its forward cryptographic teams. These successes, however, were restricted purely to forward techniques.
In spite of continual efforts, Oberinspektor Zillman was unable to break into the British
Typex cipher machine. Several British cipher machines were captured during the summer campaign of 1940, but for each of them, the wheels were missing.
The general successes of the British Referat ceased therefore, in the summer of 1942, after an intercept company, commanded by Oberleutnant Seebaum was captured in
North Africa
North Africa (sometimes Northern Africa) is a region encompassing the northern portion of the African continent. There is no singularly accepted scope for the region. However, it is sometimes defined as stretching from the Atlantic shores of t ...
. Despite the report to the cryptanalysis section, by a NCO who had escaped, that all cipher material had been destroyed, it had obviously proved possible for Britain to recognise, from other evidence, which British procedures had been read and which had not. In consequence the department was reinforced in order to win back the lost ground, which it was unable to do.
From summer 1942, Germany concentrated on watching military exercise traffic in Britain from
KONA 5 in
Saint-Germain-en-Laye
Saint-Germain-en-Laye () is a Communes of France, commune in the Yvelines Departments of France, department in the Île-de-France in north-central France. It is located in the western suburbs of Paris, from the Kilometre Zero, centre of Paris. ...
and the Stationary Intercept Company (''Feste'') in
Bergen
Bergen (, ) is a city and municipalities of Norway, municipality in Vestland county on the Western Norway, west coast of Norway. Bergen is the list of towns and cities in Norway, second-largest city in Norway after the capital Oslo.
By May 20 ...
. The Feste also watched Swedish traffic, but apart from unimportant police wireless there was very little army traffic to provide enough depth to break the British encryption.
As a result of watching Britain, it was still not possible to gain any assistance in winning back the ground lost in the Mediterranean traffic. It was nevertheless possible to gain some information regarding the training and order of battle for the forthcoming invasion of the continent, although the extent of this information was not known by TICOM interrogators.
Intercept station operations
Soviet cryptanalysis
Organisation of cryptanalytic effort against Soviet Union
Review of Central Office organisation
Prior to 1939, the ''Intercept Control Station''
ef 5.1had a section for handling Russian traffic, but little was known of its operation or achievements. Early successes against Russian cryptography were evidenced by
cryptanalysis
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic se ...
of 2,3, and 4-figure codes with 5-figure codes broken at the start of the war using a Russian 5-figure code book obtained from Finland, that was used in the first year of the war. When HLS was replaced in 1941 with the new agencies: ''OKH/Chi'' and HLS
ef 5.2 the Soviet evaluation section was moved to LNA and the cryptanalysis unit for the Soviet sector remained with ''Inspectorate 7/VI''. In late 1941, on a recommendation by
Kunibert Randewig, both cryptanalysis and evaluation sections were moved to
Loetzen,
East Prussia
East Prussia was a Provinces of Prussia, province of the Kingdom of Prussia from 1772 to 1829 and again from 1878 (with the Kingdom itself being part of the German Empire from 1871); following World War I it formed part of the Weimar Republic's ...
. This section formed the nucleus for the third central agency, the HLS Ost
ef 5.5 From that time, until 1944, the German Army Signals Intelligence activities were sharply divided into non-Russian, which were undertaken at ''Inspectorate 7/VI'' and into Russian activities, performed by HLS Ost and the LNA.
In October 1944, the three agencies were amalgamated together into the GdNA, into a central agency.
For a breakdown of Russian signals intelligence activities, Group II under Captain () Gorzolla and Group IV under Major Rudolf Hentze were the principal units with the GdNA which worked on Russian systems
ef 5.6.1
Review of Field Office organisation
Cryptanalytic effort against Soviet Union
Introduction

The Soviet Union state used various military cryptographic systems in order to secure its communication. Two organisations prepared and evaluated cipher procedures. This was the
NKVD
The People's Commissariat for Internal Affairs (, ), abbreviated as NKVD (; ), was the interior ministry and secret police of the Soviet Union from 1934 to 1946. The agency was formed to succeed the Joint State Political Directorate (OGPU) se ...
5th Department and the
Red Army
The Workers' and Peasants' Red Army, often shortened to the Red Army, was the army and air force of the Russian Soviet Republic and, from 1922, the Soviet Union. The army was established in January 1918 by a decree of the Council of People ...
's 8th Department of the main intelligence directorate
GRU
Gru is a fictional character and the main protagonist of the ''Despicable Me'' film series.
Gru or GRU may also refer to:
Arts and entertainment
* Gru (rapper), Serbian rapper
* Gru, an antagonist in '' The Kine Saga''
Organizations Georgia (c ...
. The soviet military used 2,3,4, and 5-digit codes enciphered with substitution methods or with additive sequences used with the most important 4 and 5 figure codes. The NKVD relied on figure codes enciphered both with substitution and addition methods. Partisan groups also used figure codes enciphered with additive sequences or transposed based on a key word. The
diplomatic service
Diplomatic service is the body of diplomats and foreign policy officers maintained by the government of a country to communicate with the governments of other countries. Diplomatic personnel obtain diplomatic immunity when they are accredited to o ...
used 4-digit codebooks enciphered with
One-time pad
The one-time pad (OTP) is an encryption technique that cannot be Cryptanalysis, cracked in cryptography. It requires the use of a single-use pre-shared key that is larger than or equal to the size of the message being sent. In this technique, ...
s tables.
2-Digit codes
The
Soviet Union
The Union of Soviet Socialist Republics. (USSR), commonly known as the Soviet Union, was a List of former transcontinental countries#Since 1700, transcontinental country that spanned much of Eurasia from 1922 until Dissolution of the Soviet ...
2-digit codes were used by the
Russian Army
The Russian Ground Forces (), also known as the Russian Army in English, are the Army, land forces of the Russian Armed Forces.
The primary responsibilities of the Russian Ground Forces are the protection of the state borders, combat on land, ...
,
Air Force
An air force in the broadest sense is the national military branch that primarily conducts aerial warfare. More specifically, it is the branch of a nation's armed services that is responsible for aerial warfare as distinct from an army aviati ...
and
NKVD
The People's Commissariat for Internal Affairs (, ), abbreviated as NKVD (; ), was the interior ministry and secret police of the Soviet Union from 1934 to 1946. The agency was formed to succeed the Joint State Political Directorate (OGPU) se ...
. In the Army, they were used by Army Groups, Armies, Corps, Divisions, and Regiments; and by small independent special units such as Combat Engineer Brigades, Motor Regiments, and artillery. In the NKVD, they were used on regimental communication close to the front, and from divisional level downwards.
Cryptanalysis of 2-digit systems was done mostly in
FAK units at the company level, but was also handled by
NAA, the
NAAS
Naas ( ; or ) is the county town of County Kildare in Republic of Ireland, Ireland. In 2022, it had a population of 26,180, making it the largest town in County Kildare (ahead of Newbridge, County Kildare, Newbridge) and the List of urban ar ...
and at HQ level of the GDNA itself.
It was clear from interrogations that 2-digit codes were not always in use, but were being constantly read. POWS of
NAA 11 stated that the last known table was PT-43, and it could not be constructed. For Lieutenant Alexis Dettman, who stated that solving PT codes was:
:''merely a form of crossword puzzle''
Dr. Wilhelm Gerlich of NAAS 1, stated that one or two men at
NAAS
Naas ( ; or ) is the county town of County Kildare in Republic of Ireland, Ireland. In 2022, it had a population of 26,180, making it the largest town in County Kildare (ahead of Newbridge, County Kildare, Newbridge) and the List of urban ar ...
1 were able to cope with decipherment of 2-digit messages, especially as the greater part of them were being solved at company level.
KONA 1 prisoners stated categorically that the Soviet Union has ceased using 2-digit codes after 1943, however other evidence would seem to have indicated that they were used up until the end of the war by the Red Army and NKVD, particularly by units in active combat, and were still being actively used, even if not appearing.
3-Digit codes
3-digit codes were used by the Red Army, the Air Force and the NKVD. They were first used in 1941–1942, initially mainly by the Air Force and later, more widely, by the Army. Traffic from Army Group down to Battalion had its own 3-digit code. The 3-digit codes were replaced by 3-digit Signal Codes in 1943, which were used by all units. For the NKVD, they were used by the
Black Sea Fleet
The Black Sea Fleet () is the Naval fleet, fleet of the Russian Navy in the Black Sea, the Sea of Azov and the Mediterranean Sea. The Black Sea Fleet, along with other Russian ground and air forces on the Crimea, Crimean Peninsula, are subordin ...
and from division downwards.
The solution of these codes was done mostly in
FAK companies, but also handled by the NAA, NAAS and the HLS Ost.
They were first noticed in February, 1941, and used increasingly from May 1941 at the beginning of the
Russian campaign (
Eastern Front (World War II)
The Eastern Front, also known as the Great Patriotic War (term), Great Patriotic War in the Soviet Union and its successor states, and the German–Soviet War in modern Germany and Ukraine, was a Theater (warfare), theatre of World War II ...
). From then until late summer 1942, the Air Force made the most use of the code and each Air Division had its own cipher. In 1942, the
48th Army, the first Army to use it, started by using a 3-digit syballic code.

Interrogations of personnel from Feste 10 and KONA 1: ''By the time of Stalingrad practically every Army engaged in the battle had its own 3-digit cipher.'' Dettman and Samsonov do not discuss any 3-digit codes as such, so it must be assumed that they considered these types of codes similar to the 2-digit PT series, and did not warrant discussion as a special sub-type.
=Technical description
=
The first 3-digit ciphers were very simple in form, consisting of several pages, ten at most, and contained alphabetically semi-hatted or completely hatted, the numbers 1 to 0 and punctuation marks. See Fig IV.

Soon afterwards the letters of the alphabet were put in their alphabetic position in the book. See Fig V.
Besides the above types of codes, syllabic codes contained few words but practically all the possible syllables which could be formed out of 2 or 3 letters. All codes of this kind which were broken were alphabetic. See Fig. VII

After some months, the strictly alphabetic nature of the books was given up and the alphabeticity only maintained within the area of a letter. The numbers were at the same time distributed at random over the page. See Fig VI. The book could have 1000 groups, but Oberleutnant Schubert stated that the average number of groups was 300–800, stating: '' in general small scope, but frequent change.'' If the codes were smaller than 1000 groups, alternatives were given either to pages or first figures of the lines. The substitutions could be constructed without any recognizable system or they could be made up from a Latin square, with the square usually lasting about one month, although with the Air Force, it sometimes lasted longer. Schubert stated that towards the end of the war, there appeared quite isolated 4 to 7-digit substitution, presumably private systems of the respective cipher departments, but appeared very seldom.
From the beginning of 1943, most 3-digit codes no longer contained single letters but used the initial letter of the words for this purpose. In order to indicate which meaning was to be used two groups were introduced:
:: 736 1) Read the initial letter
:: 737 2) Read the whole word

The 3-digit groups were read in the order of page-line. The recipher of 3-digit ciphers was as varied as in the case of 2-figure ciphers. Each figure was re-enciphered separately. This is to say, for the page numbers, a hatted order of the figures 1 to 0 was substituted. Thus Page 1 became 4, 2 became 6 and so on. Fig. VIII.
3-digit code ''R3ZC'' which was mentioned by Corporal A. Faure of
NAA 11 and was discovered as part of the Norway codes. It was a code with 10 pages of 100 positions each, 10 x 10 alphabetically arranged. One column of each page, the 8th was empty. Only the 100's and 10's figures of each group were reciphered.
The 3-figure code, it is clear from all interrogations, was mainly used by the Army, but also by the Air Forces. According to a report by Uffz. Karrenberg of Group VI, on regimental networks and for less important messages on the level of assault armies, mainly the 3-digit codes (with a 2-digit Latin square encipherment) was used. KONA 1 personnel stated that every Army Group down to Battalion had its own 3-digit code.
A good deal of
plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
was inserted into the 3-digit enciphered code as it was transmitted. Gerlich pointed out the advantages of plaintext insertion stating: ''They often gave words and names not contained in the code. 3-figure traffic was always solved when one encipherment was available'' 3-figure traffic was only slightly more secure that 2-digit code traffic and was 80% readable. It was known that Air Force codes were often current for much longer periods than those for the Army, and thus be able to find
depth. Army 3-digit codes were changed after a big operation and were in use for one week to one month. However, all 3-digit codes were readable and Lt. Col. Mettig stated that from spring 1943 to 1945, 2-digit and 3-digit traffic was read regularly, providing a large amount of tactical intelligence.
The operational 3-digit codes were discontinued in 1943 and replaced by 3-digit Signal Codes, which were different only in that they contained no letters, only words and phrases of importance, and were not alphabetic but had meanings grouped under headings such as ''attack'', ''defend'', ''enemy movements''. Each meaning had two or three, 3-figure groups allotted to it. As in the case of the former code, anything not in the codebook was sent in plaintext. It was assumed that these types of codes were also read as consistently and as fully as the 2-digit and 3-digit codes they superseded.
4-Digit codes
4-digit () codes were used by the Army, Air Force and NKVD. There were used in the Army as General Army Codes, called General Commanders Codes, and on lower operational levels by mobile formations such as Tank and Mechanised Corps, Tank Armies, and Tank Administration and Supply Units. For the NKVD, they were used on Railway and Transport Nets.
Solutions to these codes were handled at FAK, NAA and GDNA level. At FAK level, the companies usually had a 4-figure unit, as well as a 2-digit unit and 3-digit units, in a cryptanalysis department.
Lt. Schubert of KONA 6 stated under interrogation that: ''The Soviet Army keys are 3 or 4-digit systems. The basis is the same.'' The construction of 4-digit codes was the same as 3-digit codes, except the book had a possible 10,000 groups instead of 1,000. with the book length being described as either six or seven pages each with a block of consecutive numbers, or with KONA 1 personnel stating that book length being of from 5 to 100 pages long. The latter value seemed more likely. The Air Force Codes usually had about 10,000 groups and the Army 5,000 groups, and each page could have a variant page designation.
=Technical description
=
The actual construction of pages varied in 4-digit code books as much as it did in 3-digit books, in respect of alphabeticity and sequence of numbers. But the methods of enciphering the last two digits were still more varied than those used in 3-figure systems:substitutions by row, digraph substitution (in comparison to single-letter substitution in the case of 3-digit codes), combinations of these two, abbreviated figures in the substitution, and others. Uffz. Corporal Karrenberg, who was a GDNA cryptographer, and was a specialist on Russian
Baudot stated, while under interrogation, in his discussion of the ''Russian Cryptanalysis course'' given for field training, that 3-digit or 4-digit could also be reciphered on an adder. For this purpose a text chosen at random is enciphered (likewise by the code) and the code text added to or subtracted from (non carrying). There was no other indication in interrogations that this method was met in actual practice. The general method seem to have been variant page designations for the book (2-figures) and encipherment of the last 2-digits by various means, including 2-digit
Latin square
Latin ( or ) is a classical language belonging to the Italic branch of the Indo-European languages. Latin was originally spoken by the Latins in Latium (now known as Lazio), the lower Tiber area around Rome, Italy. Through the expansion o ...
.
From May 1942, the Air Force began to use 4-digit codes in many different forms, but often of the simplest construction. In the middle of 1943, many mobile formations, Tank and Mechanised Corps, Tank Armies and Administration, and Supply units also started using these 4-digit codes. They were also used by the Railway and Transport Nets.
Dettmann and Samsonov described the first ''general army and air force'' code, which was a 4-figure with 4,600 groups, enciphered by digraphic substitution. The successor codes were the names ''OKK5'' to ''OKK8'' which were General Commanders Codes that rapidly replaced one another from 1939 to 1941. OKK 5 was captured in the
Winter War
The Winter War was a war between the Soviet Union and Finland. It began with a Soviet invasion of Finland on 30 November 1939, three months after the outbreak of World War II, and ended three and a half months later with the Moscow Peac ...
, and ''OKK 6'', 7, 8 later.
Dettmann and Samsonov stated:
:''All these systems, however, recovered by cryptanalysis before their capture and were made completely and currently readable.''
Ltn. Harry Loeffler of Feste 10 stated that a:
:''General army 4-digit cipher was last observed in use in
Tajikistan
Tajikistan, officially the Republic of Tajikistan, is a landlocked country in Central Asia. Dushanbe is the capital city, capital and most populous city. Tajikistan borders Afghanistan to the Afghanistan–Tajikistan border, south, Uzbekistan to ...
(North Persia) in the winter of 1941–42. It had 50 pages, each designated by two alternative
Bigram
A bigram or digram is a sequence of two adjacent elements from a string of tokens, which are typically letters, syllables, or words. A bigram is an ''n''-gram for ''n''=2.
The frequency distribution of every bigram in a string is commonly used f ...
s and 100 lines to each page.''
There was no indication in interrogations that 4-digit codes were either less or more frequently employed. In 1944, 4-digit Signal Codes, of the same form as the 3-digit Signal Codes, appeared, and were used by army groups. and probably superseded in great part, if not wholly, the 4-digit codes discussed above.
Four-digit codes were changed less frequently than other codes but Dr Wilhelm Gerlich's of
NAAS 1 of
KONA 1 stated, the change in encipherment was not quick enough to make decipherment impossible
y Germany Certainly the 4-digit codes gave Germany cryptanalysts a certain amount of trouble, as a large amount of material was ''absolutely necessary'' and the majority of unsolved 4-digit codes and ciphers were abandoned because of an insufficient number of messages.
Captain Holetzlo, a member of
LN Regiment 353, the Luftwaffe signals regiment intercepting Russian Air Force traffic, speaking mainly about 4/F air force codes (ground/ground) stated that they were ''only 60% readable''. Corporal Heudorf of
NAA 8 of
KONA 2 stated that later 4/F traffic provided some difficulty in cryptanalysis, but an Engineer unit's in March and April 1945 was being read concurrently.
In the interrogations of KONA 1 members, the following 4/F codes were listed as solved:
* 4-digit code of VI Guards Mech. Corps of
1st Ukrainian Front
The 1st Ukrainian Front (), previously the Voronezh Front (), was a major formation of the Red Army during World War II, being equivalent to a Western army group. They took part in the capture of Berlin, the capital of Nazi Germany.
Wartime ...
from January 1945 to end of war.
* 4-digit code of 152 Tank Brigade of
60th Army of the 1st Ukrainian Front.
* 4-digit code of Tank Supply and Administration Authorities of the 1st Ukrainian Front.
* 4-digit code of the 76th Regional Air Base (Russian 76 RAB).
* 4-digit code of Supply Units of
13th Army of 1st Ukrainian Front.
* 4-digit code of
3rd Guards Tank Army
The 3rd Guards Tank Army () was a tank army established by the Soviet Union's Red Army during World War II. The 3rd Tank Army was created in 1942 and fought in the southern areas of the Soviet Union and Poland, then in Germany and Czechoslovakia ...
.
Horst Schubert stated:
:''We broke Army 3 and 4-digit re-enciphered books. These were enciphered on a conversion table. Early in the war we read most of this traffic, but by the end only 40% to 50%.''
5-Digit codes
5-digit codes were used by the Army, Air Force and NKVD. In the Army, they were used by the
People's Commissariat for Defence (), Army Groups, Armies, Corps, Divisions and Brigades. In the Air Force, they were used by Air Armies, Air Corps, Air Divisions, Regional Air Bases, Anti-Aircraft Corps and Divisions and Anti-Aircraft units. They contained strategic, tactical, personnel and supply matters, and political reports and directives.
With the exception of a short period in 1943, when KONA 1 did independent 5-digit cryptanalysis, solution of 5-digit codes was handled exclusively by the GDNA.
In discussing the achievements of the ''OKH/Chi'', Lt. Col. Mettig, stated glibly:
:''The breaking of the Russian 5-digit reciphered code...was the most outstanding cryptanalytic achievement of In 7/VI.''
The Soviet 5-digit code was broken chiefly by War Administration Inspector () Lieutenant Alexis Dettman. When rating the relative importance of cryptographic including cryptanalysis achievements contributing to total intelligence, Mettig was most impressed by the continuous breaking of the Russian 5-digit code despite the difficulties that were experienced after spring-summer 1943.
[I-128 p. 2] However Mettig could have been stressing organisational changes carried out to facilitate the breaking of codes rather than actual cryptographic achievements. Dr
Otto Buggisch, also of ''OKH/Chi'' stated that Mettig had few fundamental ideas of cryptanalysis.
Certainly other evidence exists that points conclusively and without doubt to an almost complete failure on the part of the German cryptanalysts to make any progress with the solution of the 5-digit code. Corporal () A. Althans of the KONA 1 stated that cryptanalysis of 5-digit codes was only possible with the following conditions:
* There was a number of messages, at least three, which had the same additive applied.
* The 5-digit code had been captured.
Dettmann and Samsonov
[DF-18 p. 59] stated that codes ''011-A'', ''023-A'', ''O45-A'', ''062-A'' and ''091-A'' used successively from the beginning of World War II to the end, did prove difficult from a pure cryptanalytic solution. They stated:
:''It is interesting to point out that during the course of the war all the newly appearing versions of each cipher were captured through fortunate circumstances and always so soon that the originals were almost always in the hands of the cryptanalysts at the instance of their being put into use by the Soviets.
Of course, this 'contentious capture' was an aid in solution, under such circumstances because of the
One-time pad
The one-time pad (OTP) is an encryption technique that cannot be Cryptanalysis, cracked in cryptography. It requires the use of a single-use pre-shared key that is larger than or equal to the size of the message being sent. In this technique, ...
encipherment. The ''individual'' tables offer almost complete security against breaking.''
In the reports of personnel from
NAA 11, a Captain Schmidt stated that:
:''With regard to Russian
oviettraffic, the Abteilung
attaliondid everything up to and including 4-digit. 5-digit they considered insoluble and forward these to the GdNA.''
One Corporal Karrenberg, of GdNA, while under interrogation discussed 5-letter and 5-digit codes used for operational orders, stated:
:''These were so-called Blocknot codes, which were only used once and were therefore unbreakable.''
Blocknots were random sequences of numbers contained in a book and organised by numbered rows and columns and were used as additives in reciphering and were considered as a type of
One-time pad
The one-time pad (OTP) is an encryption technique that cannot be Cryptanalysis, cracked in cryptography. It requires the use of a single-use pre-shared key that is larger than or equal to the size of the message being sent. In this technique, ...
. The GdNA mathematician
Johannes Marquart conducted research on Blocknots and was unable to determine how they were generated. Corporal Karrenberg stated flatly:
5-figure and 5-digit messages were not touched at all. In general very little work was done on decipherment of 5-group messages, although these contained the most important operation reports. They were only used to identify units and were only read if code books happened to have been captured.
In 1943,
KONA 1, for a period, undertook 5-digit
cryptanalysis
Cryptanalysis (from the Greek ''kryptós'', "hidden", and ''analýein'', "to analyze") refers to the process of analyzing information systems in order to understand hidden aspects of the systems. Cryptanalysis is used to breach cryptographic se ...
independently of GdNA, but the general practice was for all units to forward 5-digit traffic directly to Berlin to GdNA for possible cryptanalysis and evaluation. Karrenberg stated:
:''even at the GdNA HQ, very little attention was give to 5-digit messages and very little enthusiasm displayed in working on it. Only the preambles were used to identify units, from Blocknots and indicator groups.''
Finally Lt. Schubert, when questioned on possible success on 5-digit codes replied:
:''In the Finnish campaign the book was captured and the Russians used the one-time pads over again. Because of this we had considerable success. Recently the Russians used the
ne timepads correctly and only very few messages were read, these through re-encodements.''
=Technical description
=
This small measure of success was due to the fulfilment of the two conditions set forth by Althans for successful cryptanalysis.
Althans stated that successful cryptanalysis is possible only if:
* There are a number of messages, at least three, which have had the same additive applied.
* The 5-figure code was captured.
Cryptanalysis starts from the mathematical rule that the difference between two code groups remains constant if both have the same additive row applied to them. For example:
::
The most important cryptanalytic aid was therefore the catalogue of differences, a numerically arranged table of the differences between the most frequently used code groups.
Directly the code, which changed approximately semiannually, was captured, about 1000 frequently used clear groups (positionen) were written out by the Gen. d. N.A., arranged and serially numbered according to frequency, and then each subtracted from the other, non-carrying, by
Hollerith (
Herman Hollerith
Herman Hollerith (February 29, 1860 – November 17, 1929) was a German-American statistician, inventor, and businessman who developed an electromechanical tabulating machine for punched cards to assist in summarizing information and, later, in ...
) machines and entries made on the catalogue as follows:
:"41909 17-32" which means:
:
In 1943 KONA 1 for a period undertook 5-figure cryptanalysis independently of GdNA. For this purpose a difference catalogue of 200 clear groups (which equals 19900 differences) was compiled by hand. A calculation aid, in the form of a wooden frame with five paper belted wheels I to V, where one wheel represented each digit of the 5-figure group, was used. The apparatus also served as an aid in actual decoding, when a great deal of non-carrying addition or subtraction had to be done. Note: little information is available from TICOM as to how this device functioned.
The
Finnish predecessor to the
Finnish Defence Intelligence Agency, during the early period of World War II had captured and turned over to the Germans, a Russian 5-figure book which was used continually until the
Winter War
The Winter War was a war between the Soviet Union and Finland. It began with a Soviet invasion of Finland on 30 November 1939, three months after the outbreak of World War II, and ended three and a half months later with the Moscow Peac ...
. An additional copy had been captured by the Germans and though the Russians introduced a new 5-figure code on 1 April 1942, the changeover was faulty, and it was possible to establish 2000 groups of the new code within a week.
[I-79 p. 8] Indeed, it was possible at this time to leave the decoding of this procedure to the forward KONA units. The Russians gradually improved their security, however, and in the spring of 1943, altered the
indicator
Indicator may refer to:
Biology
* Environmental indicator of environmental health (pressures, conditions and responses)
* Ecological indicator of ecosystem health (ecological processes)
* Health indicator, which is used to describe the health o ...
group system and split up the code into various front sectors. As it result it was necessary to collect all the 5-figure at
Giżycko
Giżycko (former or ''Łuczany''; ) is a town in northeastern Poland with 28,597 inhabitants as of December 2021. It is situated between Lake Kisajno and Lake Niegocin in the region of Masuria, within the Warmian-Masurian Voivodeship. It is ...
(Lotzen) intercept station and to use the Hollerith department of the ''In 7/VI''. Only thus could have the necessary
depth on a day's traffic be achieved.
But it was clear that after this time, there was practically no success in 5-figure code solutions, although the Germans were able to establish the nature of the book and the type of encipherment:
:''The 5-figure code books contained about 25,000 out of a possible 100,000 groups, the pages being numbered 000 to 999 with a hundred lines on each page. The Germans never broke a book and any examples they had were captures. The books were alphabetic at first but then became "semi-hatted", i.e. all groups with the same initial letter were grouped together but not alphabetically, nor were the initial letters alphabetic with reference to one another.''
Alphabetic at first, the 5-digit codebooks later became partially alphabetic. They contained:
* Single letters
* Words
* Phrases
* Two-figure numbers
* Types of units
* Specific units of the
Red Army
The Workers' and Peasants' Red Army, often shortened to the Red Army, was the army and air force of the Russian Soviet Republic and, from 1922, the Soviet Union. The army was established in January 1918 by a decree of the Council of People ...
* Full stops and commas on every page
* Add designations of types, such as Types of Tanks, ammunition, wireless stations (W/T), transport etc.
The encipherment was effected by applying additives taken from enciphering
pads known as
Blocknots, that were a variable of sheets on which 50–100 5-figure groups appeared. The second condition for successful cryptanalytic success established by Corporal Althans was fulfilled:
Depth was established.
Address codes
Soviet Address Codes (2-digit, 3-digit, 4-digit) were used by the Army for Army Groups, Armies and Independent Corps. They were used more widely by the
Air Force
An air force in the broadest sense is the national military branch that primarily conducts aerial warfare. More specifically, it is the branch of a nation's armed services that is responsible for aerial warfare as distinct from an army aviati ...
and the Anti-Aircraft Defense.
Solution of address codes was considered somewhat ''special'' to judge the statements in KONA 1 interrogations describing cryptanalytic operations of the various units:
:
Although mention was in the KONA 1 interrogations of 2-digit address material, nothing was recorded in the interrogations on this subject except one statement in the final interrogation of NAA 11 personnel:
:''
Bigram
A bigram or digram is a sequence of two adjacent elements from a string of tokens, which are typically letters, syllables, or words. A bigram is an ''n''-gram for ''n''=2.
The frequency distribution of every bigram in a string is commonly used f ...
s and
Trigram
Trigrams are a special case of the ''n''-gram, where ''n'' is 3. They are often used in natural language processing for performing statistical analysis of texts and in cryptography for control and use of ciphers and codes. See results of analysi ...
s in Addresses. Blome knew of the two used separately, but could not recall any case of the two in conjunction. He suggested that this might accompany something he had seen, namely 3 Z code mixed with 2Z traffic.''
There was no record of extent or success of solution with regard to 2-F address codes. Likewise, there was no description of 4-F (figure, or digit, both the same) address codes nor any statement regarding the extent or success of solution.
Oberleutnant Schubert of KONA 6, stated that towards the close of hostilities, the Soviets (Russians) were using 3-F codes for addresses. He stated:
:''In this code the clear position remained unchanged for periods, but the ciphers were changed daily. These ciphers were in some way related to the call signs.''
The only description of 3-F address codes was given in the KONA 1 reports.
=Technical description
=

3-Figure (3-Digit, or 3-F) Address codes were used in conjunction with 5-Digit messages to enable wireless stations to ensure that messages arrived at their proper destination. Their construction was similar to that of the PT-39 or PT-42 codes, described above, but they contained only figures, unit designations, authorities, words such as ''for'' or ''from''. See Fig X.
Example of an address:
A code of this type was first used at the beginning of 1944 on the 1st and 2nd Ukrainian and the 1st White Russian Fronts for communications between their Army Groups and their respective Armies and independent Corps. In the summer of 1944 armies began to use similar codes with their subordinates units and latterly the use of such codes increased still further.
The solution to these codes, given a fair amount of material, was generally easy. They were often simpler than the example given in Fig. X and sometimes appeared in the form of straightforward lists with each meaning numbered consecutively of 100 pages instead of 10. See Fig XI.
The same variations in construction occur as with three-figure.
* Alphabetic with the letters of the alphabet grouped at the end of the Code.
* Each letter of the alphabet placed before the part devoted to words beginning with that letter.
* Semi-hatted, i.e. with all the words beginning with one letter grouped together but the groups in random order.
* Letters of the alphabet with alternatives.
* Syllabic Codes (with words distributed over the code).
* Letters of the alphabet with alternatives.
:* Read the initial letter.
:* Read the word.
* With the two groups directly above appearing several times, often on each page.
Codes had anything from 5 to 100 pages. The Air Force Codes usually had about 10,000 groups and the Army 5000 or fewer. According to members of KONA 1, the solution of these codes given a fair amount of material, was generally easy. Members of the
NAA 11 stated the following:
:''Addresses to personal names rather than titles were common in all Russian traffic and this suggested the use of initials. The vagueness of this answer surprised the interrogator who asked if the addresses, being enciphered on the PT table, were not read currently. The answer was that unless the same address was used frequently and some outside hint was given they were unusually unable to read the address. They supposed it used values which had special local meanings added to the table.''
Miscellaneous codes
Most of the statements given here are taken from the interrogations of members of
KONA 1. It is not the complete story, as the POW's themselves were aware:
:''The examples described are only those ciphers whose basic construction was established. There were many types of cipher which were only partially broken (solved) and whose basic form could not be established, these are not mentioned.. The number of Russian ciphers of all types that were broken was about 3000.''
=4-letter codes
=

Two forms of four-letter codes first appeared in practice traffic between Army Groups and Armies and Independent Corps of the
1st Ukrainian Front
The 1st Ukrainian Front (), previously the Voronezh Front (), was a major formation of the Red Army during World War II, being equivalent to a Western army group. They took part in the capture of Berlin, the capital of Nazi Germany.
Wartime ...
in November 1944:
* Revolving Stencil
: This consisted of a sheet of paper ruled off into 8 x 8 squares. On top was placed another sheet in which 16 holes were cut of corresponding size to the squares on the first sheet. These holes were so cut that if the sheet is turned through 90° round the centre point in the four possible positions and a letter written on the bottom sheet through each hole in each position, all 64 squares on the bottom sheet would be filled. The text of the message to be enciphered was written in the holes horizontally with the stencil in the first then in the second, third and fourth positions The cipher text was then read off horizontally and sent in four letter groups. If a message was longer that 64 letters the process was repeated as many times as necessary. The revolving stencil was changed from time to time.
* Transposition
:This cipher is a simple
transposition cipher
In cryptography, a transposition cipher (also known as a permutation cipher) is a method of encryption which scrambles the positions of characters (''transposition'') without changing the characters themselves. Transposition ciphers reorder units ...
, the key given by a ''Keyword'' and the text being written in vertically according to the key and either upwards or downwards according to accompanying instructions. The cipher text was then read off horizontally and sent in 4 or 5-letter groups. See Fig. XVI
The contents of messages sent in both the above types of cipher were usually about technical signal matters though in later stages units and positions were named.
=Word-Code
=

From the middle of 1944, a word code was used in the area of the
2nd Ukrainian Front
The 2nd Ukrainian Front () was a front of the Red Army during the Second World War.
History
On October 20, 1943, the Steppe Front was renamed the 2nd Ukrainian Front.
In mid-May 1944 Malinovsky took over the 2nd Ukrainian Front.
During t ...
. The book consisted of two halves, each designated by a word such as ''SEVER ZAPAD'' literally meaning North West. Clear groups such as numbers, units, offices, designations such as Tank, Guards, Mechanised, were grouped in two columns. Each half of the code identified was only used by the Army and contained strategic and tactical reports and the names of the units. They were small in size and contained only essential groups.
The first half of the code is used with column 1 and the second half with column 2. The order of the halves can be changed and indicated by the indicating word.
If the cleargroup consists of more than one word such as ''In the former sector '' = Dolvnost and the wanted word is ''former'', this can be indicated by saying ''the second word of '' DOLVNOST. See Fig XVII.
Example:
::
The codes identified were only used by the Army and contained strategic and tactical reports and the names of units. They were small in size and contained only essential groups. Anything that could not be enciphered was sent in
plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
or in the clear. Coordinates also appeared in messages.
=Periodic and Columnar Substitutions
=
Corporal Karrenberg stated in discussing the
German Army Cryptography Course stated: "These rarely appear in Russian cipher systems... Periodic and columnar substitutions concluded the sections on substitutions systems in the course. Not so much time was spent on them as they are rarely encountered in practice."
=Coordinate systems
=
These were very varied. Armies made up their own systems and arbitrary reference points and grids were used.
=Machine Ciphers
=
The handling of
Teleprinter
A teleprinter (teletypewriter, teletype or TTY) is an electromechanical device that can be used to send and receive typed messages through various communications channels, in both point-to-point (telecommunications), point-to-point and point- ...
traffic was processed exclusively at GdNA. Lt. Schubert, whose position at the GdNA chi-stelle was Director of Main unit East, (), stated that teleprinter traffic was worked on in the machine section, specifically Group IV, whose director was Rudolf Hentze. Lt. Schubert thought that messages in
Depth had been read, but was uncertain whether the machine had been recovered. Schubert himself never worked on cipher machines, but knew that the Soviet (Russians) had a machine, already in use at the beginning of the war, but not on military traffic.
Corporal Karrenberg spoke of the ''Bandwurm'', the so-called
Russian FISH, who defined it as Russian
Baudot letter ''strip'', that should not be confused with Soviet 5-F traffic also carried on
Baudot lines. Karrenberg believed the first traffic was intercepted in 1940 in
Warsaw
Warsaw, officially the Capital City of Warsaw, is the capital and List of cities and towns in Poland, largest city of Poland. The metropolis stands on the Vistula, River Vistula in east-central Poland. Its population is officially estimated at ...
, and as far as he believed there was no interest taken in it. The first actual knowledge of the traffic, with the same external features, e.g. chat, indicators, was in summer 1943, when the first real interest was taken in it. Dr Pietsch and Döring conducted the initial research. The German intelligence agencies did not capture any of the apparatus used, but felt that it consisted of two parts:
* A Baudot
teleprinter
A teleprinter (teletypewriter, teletype or TTY) is an electromechanical device that can be used to send and receive typed messages through various communications channels, in both point-to-point (telecommunications), point-to-point and point- ...
.
* A cipher attachment consisting of five small wheels driven by one large wheel.
Depths were frequent, but the Germans did not seem to make any attempt to reconstruct the wheel patterns. The system was used by the
Red Army
The Workers' and Peasants' Red Army, often shortened to the Red Army, was the army and air force of the Russian Soviet Republic and, from 1922, the Soviet Union. The army was established in January 1918 by a decree of the Council of People ...
and the
Air Force
An air force in the broadest sense is the national military branch that primarily conducts aerial warfare. More specifically, it is the branch of a nation's armed services that is responsible for aerial warfare as distinct from an army aviati ...
and to a lesser extent the
NKVD
The People's Commissariat for Internal Affairs (, ), abbreviated as NKVD (; ), was the interior ministry and secret police of the Soviet Union from 1934 to 1946. The agency was formed to succeed the Joint State Political Directorate (OGPU) se ...
.
Otto Buggisch of the ''In 7/VI'' later GdNA and the
OKW/Chi went into somewhat more historical detail and stated that:
* In 1943, Buggisch heard that the
Research Office of the Reich Air Ministry,
Hermann Göring
Hermann Wilhelm Göring (or Goering; ; 12 January 1893 – 15 October 1946) was a German Nazism, Nazi politician, aviator, military leader, and convicted war criminal. He was one of the most powerful figures in the Nazi Party, which gov ...
's Research Bureau, had success on a Russian teletype machine and had recreated the action. It was a machine with a very long cycle, not being prime but the product of several small cycles, like the S42. Buggisch did not know the cycles of the individual wheels or any other details. He found this out from Döring, who was undertaking research on the T52. Liaison with the
FA was considered bad anyway. Mettig was particularly opposed to the
SS. Nothing came of the FA work. Buggisch stated in interrogation that the cycle of one wheel was 37, varying from 30 to 80.
* Late in 1943, early 1944, OKH began to intercept non-morse 5-impulse traffic, named ''Hughes'' by Buggisch. Group IV worked on it, at the end of 1943, resulting in a ''Kompromise'' and a depth of eight messages with the same settings was created. The section was able to recover 1400 letters of pure key, and to determine the traffic was derived from a 5-figure code, with regular station chat enciphered at the same time on the machine. Corporal Karrenberg stated that part of the depth was created within the same long message, so that the machine had a cycle, at least in this one case of about 1450 letters. The actual number was thought to be very significant by the Germans, as it was prime, so could not be the product of smaller cycles in any way they could image. Germany postulated a tape machine like the T43, or a machine in which the motions of the wheels influenced each other, 1 and 2 affecting 3, 3 affecting 5, etc. as in the T52 (which was known to be insecure). They were not able to prove any theories they had. Germany had chronic personnel problems, and the OKH/GdNA was no exception, being short of mathematicians. Buggisch believed there would be a solution.
* After this experience, they devised
Hollerith machinery to locate depths, but in fact only found three or four more cases and none of these gave additional cycle evidence or even furnished another key.
* Buggisch thought the traffic slumped, left the unit in June 1944, and the LNA stepped in to improve the solution, to improve reception as they believed the traffic was still present, which it was not. Buggisch stated in passing that their own security idea on the subject of wheel machines of this sort was that the cycle should not be a product of small periods (as in Hagelin cipher machines), even if this was long. Mutual influence of wheels should be used to avoid this, but at the same time care must be taken that too short a period was not created in the process. This in fact had apparently been done by the Soviets, but the fact that it was not repeated suggested to him that they might have seen the weakness and corrected it.
Buggisch stressed one fact which had surprised him, that they never had information about either of these machines, from POW's or agent sources. He assumed that the one that the FA broke was not the same because of the difference of cycles.
The number of links, according to Corporal Karrenberg, varied according to the number of armies, with the maximum of eight. One end of the link was
Moscow
Moscow is the Capital city, capital and List of cities and towns in Russia by population, largest city of Russia, standing on the Moskva (river), Moskva River in Central Russia. It has a population estimated at over 13 million residents with ...
, the other mobile. After 1944, no work was done on the traffic except on the spot. No vital clues to the system were given away by the Soviets, though their security precautions were not considered effective.
=NKVD codes
=
NKVD Codes were simple mono-alphabetic
Substitution cipher
In cryptography, a substitution cipher is a method of encrypting in which units of plaintext are replaced with the ciphertext, in a defined manner, with the help of a key; the "units" may be single letters (the most common), pairs of letters, t ...
2-figure, 3-figure, 4-figure, 5-figure and 5-letter types. They were used without any apparent reason on two large networks:
* The networks of the NKVD Central Authorities, that were divided into those of Security Troops, Frontier Troops, and Railway Troops and Convoy Troops.
* The network of NKVD Formation, communication between units attached to Army Front Staffs.
4-figure and 5-figure codes were used on the front line: there was a 4-figure code, e.g. used by the military police, and a general 4-figure code used on Staff-Regiment-Battalion links.
Solution of NKVD codes was handled by the
NAAS
Naas ( ; or ) is the county town of County Kildare in Republic of Ireland, Ireland. In 2022, it had a population of 26,180, making it the largest town in County Kildare (ahead of Newbridge, County Kildare, Newbridge) and the List of urban ar ...
and the GdNA. In interrogation:
:''The traffic of the NKVD formed a special group of Russian wireless traffic. The distinction applied equally to the manner of conducting traffic and to the message themselves.''
The German Army cryptanalysts reflected this Russian ''distinction'' in their own attacks on NKVD systems, allocating the work, again in their own attacks on NKVD systems, to ''levels of operation determined by difficulty of solution''. Lt Ed. Wöllner of KONA 1, stated that:
:''NKVD traffic was always covered, but only by FAK companies. Evaluation and cryptanalysis were done by NAAS.''
On the same subject Lt. Löffler of
Feste 10 stated that
:''all NKVD signals originated in the regiments area were worked on in the NAAS, others were sent to the LNA''.
But in neither case was there specified what type of NKVD traffic was worked on, and what type was passed to higher echelons. Apparently the distinction corresponded to that observed in the case of actual army traffic. All lower-level operational codes, up to 4-figure codes, could be handled by the NAAS. The 5-figure codes were not dealt with by the
KONA, but handled by 40 to 50 men in the LNA,
ef 5.4at
Zeppelin
A Zeppelin is a type of rigid airship named after the German inventor Ferdinand von Zeppelin () who pioneered rigid airship development at the beginning of the 20th century. Zeppelin's notions were first formulated in 1874Eckener 1938, pp. 155� ...
bunker at
Zossen. Löffler thought that a good deal of success was obtained in the case of Far Eastern Traffic. An additive was used for the recipher. Dettman and Samsonov substantiated this point, in their discussion of the German army cryptanalytic effort:
:''All the five-place message material from the Army or the Airforce, as well as the NKVD messages, was submitted for the exclusive processing of the GdNA''
They also gave full descriptions of NKVD systems. There was no discrepancy between the facts in their report and the facts given by Lt. Löffler. The details of description were scattered throughout the report according to types of encipherment. They mentioned the following:
* Mono-alphabetic substitution systems common to all NKVD organisations.
* Conversion systems: substitution and additive:
::* 1936: 4-figure code: 2500 values, used in district.
::* By 1939: three 4-figure conversion systems with codebooks of up to 5000 values, enciphered by digraphic substitution or conversion table.
::* 1939: first general NKVD 4-figure code, with 10000 book positions enciphered first by single digit substitution, later by additive. At time of capitulation, three 4-figure systems (''ZERNO'', ''NEVA'', ''VIZA'', see infra) used respectively by:
:::* NKVD Troops.
:::* NKVD Border defense troops.
:::* NKVD Security troops.
::::(200 messages were read daily in all three)
:::* 5 figure Railway Troops code, which used 2500 groups with digraphic substitution encipherment. A few 3-figure small codes (read currently) existed, that used letter transposition. These were never found in NKVD traffic number series.
::* 1940: 4-figure single letter conversion encipherment (1941–1942): 4-figure, enciphered by text key, which was letters equalling numbers.
::* 1942: 4-figure enciphered by military technical manual (used by Interior troops) until end of 1944 with encipherment combining single digit conversion and Gama Tables (no description of these is given).
NKVD codes technical description
NKVD traffic was always covered, but only by
Long Range Signals companies, with evaluation and cryptanalysis done by the NAAS units.
When W/T traffic was restricted during radio silences, NKVD traffic was often the most important source for Radio Intelligence. At such times, it was more completely covered. When the Army W/T was in full swing, coverage of NKVD was correspondingly reduced. On an average day, 6–12 receivers were employed exclusively on NKVD cover.
In general the following nets were covered:
* Networks of Central Authority. The covered the Chief NKVD authority in
Moscow
Moscow is the Capital city, capital and List of cities and towns in Russia by population, largest city of Russia, standing on the Moskva (river), Moskva River in Central Russia. It has a population estimated at over 13 million residents with ...
with the Front HQ's. The NKVD W/T radio intelligence picture, gave indications of groups, or the insertion of new Fronts. E.g. the appearance of a new W/T station communication with the
1st Ukrainian Front
The 1st Ukrainian Front (), previously the Voronezh Front (), was a major formation of the Red Army during World War II, being equivalent to a Western army group. They took part in the capture of Berlin, the capital of Nazi Germany.
Wartime ...
and
2nd Ukrainian Front
The 2nd Ukrainian Front () was a front of the Red Army during the Second World War.
History
On October 20, 1943, the Steppe Front was renamed the 2nd Ukrainian Front.
In mid-May 1944 Malinovsky took over the 2nd Ukrainian Front.
During t ...
showed that the
4th Ukrainian Front had been inserted between the 1st and 2nd Fronts. In addition, the new Front HQ could be located by
Direction finding
Direction finding (DF), radio direction finding (RDF), or radiogoniometry is the use of radio waves to determine the direction to a radio source. The source may be a cooperating radio transmitter or may be an inadvertent source, a naturall ...
().
:The Central Authority Networks were subdivided into;
:* Central Authority of the Security Troops.
:* Central Authority of the Frontier Troops.
:* Central Authority of the Security Troops (Divisions and Brigades of the Back Area).
:* Central Authority of the Railway Troops.
* Networks of Formation. This covered the Front staffs with the ''Grenztruppen'' Regiments. Communication between commanders of the security troops at the
front and their regiments, was monitored. D/Fing of the Regiments revealed the approximate extent of the Front. D/F of the Chief of Security Troops with the Front HQ. Finding the High Command indicated the approximate location of the Front HQ. Besides, when a forward echelon of the Chief of Security with the Front HQ appeared, it was possible to deduce that the Front HQ would move. This, on the basis of NKVD traffic alone.
* Regiments to Battalions. Most of the messages could be read, they mentioned Army units by name, e.g.;
:* Before the attack from the NEISSE sector (1st Ukrainian Front), a 2nd Army and 3rd and 4th Field Replacement Rifle Regiments were mentioned by III Bn.of the 83rd ''Grenztruppen'' Regiment, operating in the
Görlitz
Görlitz (; ; ; ; ; Lusatian dialects, East Lusatian: , , ) is a town in the Germany, German state of Saxony. It is on the river Lusatian Neisse and is the largest town in Upper Lusatia, the second-largest town in the region of Lusatia after ...
area. The conclusion drawn was that the
2nd Polish Army had been newly brought up to the NEISSE sector.
:* Lines of advance and boundaries of battalions were mentioned. Battalion boundaries often proved to be Army boundaries.
Traffic of rear NKVD troops and of the Signals Regiment were of no interest, and were not covered by KONA 1.
A constant watch was kept on the 1st network, ''Central Authority of the Security Troops''. It consisted of the communications between the Central NKVD Authority in Moscow and the commanders of those troops in Army Groups, directing staffs North and South, the less interesting GHQ Signals Regiments. These messages were not readable.
Apart from the characteristics already noted they were also to be recognised by their use of Call-signs which were made up from a square. The Russian wireless station numbers were:
:::
The method of working was controlled () circle working. The Kreise were known by the number of the controlling station. They were:
* Kreis VIII: Station 8 with 21, 23, 23 Night Frequency on 3170/3380
kcs
* Kreis IX: Station 9 with 20,21,25,28 Night Freq. on 3850/4230 kcs.
* Kreis XI: Station 11 with 26,29,87 Night Freq. on 4580/4940 Day Freq. 7400/8670 kcs.
* Kreis XII: Station 12 with 27,84 Night Freq. on 4580/4940 kcs.
* Kreiss LXXXI: Station 81 with 20,21,22,23,24,25,28,49,50,55,57,59,60,61,63,65 Night Freq. 2850/2975 kcs. Day Freq. 4080/4480 kcs.
* Kreiss LXXXV: Station 85 with 26,27,29,51,52,53,54,56,58,62,64,80.84,87 Night Freq. 2700/3050 kcs. Day Freq. 3950/4400 kcs.
Call sign
In broadcasting and radio communications, a call sign (also known as a call name or call letters—and historically as a call signal—or abbreviated as a call) is a unique identifier for a transmitter station. A call sign can be formally as ...
s were mostly pronounceable. The Front Staff networks usually changed their call-signs daily, the Regiment networks at regular intervals of several days, in many cases of weeks. Frequencies used lay mainly between 2400 & 3600 kcs. It should be mentioned that 5-figure NKVD messages had been picked up in nets identified as belonging to the Army or the Air Force, such messages contained
SMERSH
SMERSH () was an umbrella organization for three independent counter-intelligence agencies in the Red Army formed in late 1942 or even earlier, but officially announced only on 14 April 1943. The name SMERSH was coined by Joseph Stalin. The form ...
in the
preamble. Such messages were originated by units of the
Red Army
The Workers' and Peasants' Red Army, often shortened to the Red Army, was the army and air force of the Russian Soviet Republic and, from 1922, the Soviet Union. The army was established in January 1918 by a decree of the Council of People ...
counter-intelligence units.
Lt. Schubert spoke of two 5-figure codes, the
SMERSH
SMERSH () was an umbrella organization for three independent counter-intelligence agencies in the Red Army formed in late 1942 or even earlier, but officially announced only on 14 April 1943. The name SMERSH was coined by Joseph Stalin. The form ...
organisation code, used with an individual subtractor, and the Railways Troop codes, that was a 4-figure code, enciphered with substitutions tables, the 5th digit representing the quadrant on the page in which the group appeared. Schubert was more familiar with the 4-figure NKVD codes, which were apparently more exploitable than the 5-F codes.
The Security Troops Codes were of two types. One was used forward of regiment, when a regiment was used in approximately an Army Group Sector, i.e., it is a cipher, therefore, used forward of Army Group. This particular code ran for comparatively long periods, at least 1.5 years. The code, a
Substitution cipher
In cryptography, a substitution cipher is a method of encrypting in which units of plaintext are replaced with the ciphertext, in a defined manner, with the help of a key; the "units" may be single letters (the most common), pairs of letters, t ...
, was alphabetical and contained 100 pages, with 25 or 50 groups per page, and enciphered by means of an enciphered
indicator
Indicator may refer to:
Biology
* Environmental indicator of environmental health (pressures, conditions and responses)
* Ecological indicator of ecosystem health (ecological processes)
* Health indicator, which is used to describe the health o ...
, which provided for page and position substitution, the result of which was again enciphered by a substitution table. These substitution tables were also valid for a longer time and varied with the network. The additives on the page did not change, only the substitution table.
The second type, a code used rearwards of regiment, was enciphered by a figure subtractor originally from tables (up to September 1944). The same tables could appear on different networks, and since the subtractor was used very frequently, ''it was not uncommon for 20 messages to have the same subtractor'' In October 1945, 2 subtractors were used, taken from different tables, and the indicators for the 2nd subtractor were enciphered with the first one. In spite of the potential difficulties involved in this method on encipherment, the system was solved by 15 February 1945, though mainly because of bad Russian usage of the system.
The Frontier Troops Code was exactly like the Security Code rearwards of regiment, with a different basic book, at least in traffic out of
Saint Petersburg
Saint Petersburg, formerly known as Petrograd and later Leningrad, is the List of cities and towns in Russia by population, second-largest city in Russia after Moscow. It is situated on the Neva, River Neva, at the head of the Gulf of Finland ...
(Leningrad) Lt. Schubert made a statement on the Railways and Convoy Troops code quotes above.
The 4-F NKVD codes exploited by
KONA 1 were used by front line units, i.e. regiments and battalions, mainly employed by the Soviet Military Police. From the period of 1933 to 1942, code ''R4ZC4'' Russian 4-Figure, Code 4/ was in use. It consisted of a 100-page alphabetic book each with a hundred lines. It was broken by Germany in 1940. Only one code book, known to Germany as R4ZC 1800 and to the Russians as ''KODOWA TABLICA ZERNO'' was used by the NKVD from October 1943 until the end of 1944.
NKVD R4 Z C 1800 Code

The ''R4 Z C 1800'' code, had since October 1943 had 50 pages, each consisting of 50 lines and totalling 2,500 clear groups, alphabetically arranged. Each page is shifted by means of Cipher square () and the
bigram
A bigram or digram is a sequence of two adjacent elements from a string of tokens, which are typically letters, syllables, or words. A bigram is an ''n''-gram for ''n''=2.
The frequency distribution of every bigram in a string is commonly used f ...
s (ab and cd) are then replaced by others according to a substitution table.
The recipher consists of two elements:
''Shifting by means of Chiffranten'' enciphering: Any figure, chosen from Row A (sample code in Annexe 1), will indicate on any page, in Row B below, the figure must be added to that standing beside the clear group (and subtracted when deciphering).The ''chiffrant'' consisted of the figures 0 to 9 in random order printed at the top of the page, a different order being used for each page. The third figure of the 4-figure indicator group gave the number of the chiffrant to be used, i.e., if 5 was the 3rd figure of the indicator group, the fifth figure of the ''chiffrant'' reading from left to right would be the one used for each page. This number was then added to the numbers of the lines on the page before they were reciphered by means of the bigram table, i.e. if the number was 6 then line 00 would become 06 and line 24 would become line 05.
''Substitution of bigrams'': For the first and second halves of the 4-figure group (elements ''ab'' and ''cd'') there are substitution tables, each of which contains 100 bigrams (each bigram from 01 to 50 occurs twice). There are 10 such tables (numbered for the most part from 0 to 9). Two different bigram substitution tables were used for reciphering the big ram representing the page and that representing the line. 10 such tables were in use concurrently for the recipher of both page and line. Each table was 10 x 10 so that each bigram could be reciphered in two different ways and each table was designated by one of the figures from 0 to 9. The figure designating the table used for the line was put in the second place of the indicator group and that designating the table used for the page in the fourth place. The first place was a dummy. A series of substitution tables was current for a period of from 2 to 6 months.
The reciphering is indicated by a 4-figure group (indicator) which appears at a definite position in the message and contains;
* Number of the clear-group table (indicated with two digits).
* Chiffrant.
* Number of the pagination table.
:::Example:
:::Indicator 0151
:::Chigruppe 2406
:::Decipherment (according to the tables below)
Element ab (=24) yields 20 according to the pagination table. The clear-group therefore is on page 20. Element cd yields 02 according to the clear-group table. From this the chiffrant is subtracted, in this case 1 (the number of page 20 under the fixed figure 5). Thus the clear group 2001, which represents ''Komandirowatj'' is derived.
The indicator group was inserted ''en clair'' in one of the first ten groups of the message according to instructions. The penultimate group consisted of the date and length of the message and the last group the Chi number.
R4ZC4 was used from 1933, solved in 1940 and in use until 1942. There were 100 pages each with 100 clear groups arranged alphabetically. Recipherment was by means of 31 substitution tables.
NKVD Other codes
Though the emphasis by the POW's being interrogated by TICOM was on 4-figure NKVD codes, it should be pointed out that a great variety of encipherments were worked on, though not all of them read. Corporal Karrenberg, gave the following breakdown of nets and types of codes used:
* Administration networks: usually sent 5-figure messages and less often, 4-figure and 5-letter messages.
* Frontier networks: used 4 and 5-figure codes: on regimental networks, also 2-figure systems.
*
Black Sea Fleet
The Black Sea Fleet () is the Naval fleet, fleet of the Russian Navy in the Black Sea, the Sea of Azov and the Mediterranean Sea. The Black Sea Fleet, along with other Russian ground and air forces on the Crimea, Crimean Peninsula, are subordin ...
: used 3-figure and 5-figure codes networks from divisional level downward: used 2-figure and 3-figure, plain language and figure messages with plain language.
Corporal Exeter of NAA 11 stated that he worked on 2-figure NKVD codes. Traffic of an NKVD net on the
White Sea
The White Sea (; Karelian language, Karelian and ; ) is a southern inlet of the Barents Sea located on the northwest coast of Russia. It is surrounded by Karelia to the west, the Kola Peninsula to the north, and the Kanin Peninsula to the nort ...
Front, controlled from the NKVD HQ at
Archangel
Archangels () are the second lowest rank of angel in the Catholic hierarchy of angels, based on and put forward by Pseudo-Dionysius the Areopagite in the 5th or 6th century in his book ''De Coelesti Hierarchia'' (''On the Celestial Hierarchy'') ...
was worked on with some success.
NKVD Conclusions
In general, certain elements seemed to be constant in all NKVD codes:
* Simply that NKVD messages were enciphered on the same system.
* NKVD messages were always arranged alphabetically.
* NKVD messages whether 5-letter or 4-figure or 5-figure, had the date in the penultimate group.
=Agent codes
=
Agents' Codes included codes used by agents, guerillas and scouts () All systems were used from
substitutions, double
transpositions,
grilles and subtractors to one-time pads (tape based). Solving agents' traffic was always done centrally in Berlin.
The solving of agent, guerilla and scout traffic was the responsibility of Referat IIIc of Group IV. Solving the cipher depended mainly on captured material and there was generally enough material to accomplish solutions. Some agent traffic was one-time tape and therefore unbreakable. By and large the group did not place much value on agent traffic and neglected it.
It should be pointed out that Russian agent systems were not handled exclusively by OKH/GdNA/IV/3c, but were also handled by:
* Section III of the Armed Forces Signal Communication Group,
Radio Defense Corps, or more accurately the AgWBNV, Radio Communication Group 3 (), (AgWNV/FU III) who were responsible for locating, eliminating, or neutralizing all enemy agents' radio activities.
The unit was subordinated to
Generalleutnant
() is the German-language variant of lieutenant general, used in some German speaking countries.
Austria
Generalleutnant is the second highest general officer rank in the Austrian Armed Forces (''Bundesheer''), roughly equivalent to the NATO ...
Fritz Thiele
Fritz Thiele (14 April 1894 – 4 September 1944) was a member of the German resistance to Nazism, German resistance who also served as the communications chief of the German Army (1935-1945), German Army during World War II. Life
Thiele was bor ...
. Preliminary reading, especially when the code was captured, or the system recognised, was done at WNV/FU/III. For more difficult cryptanalysis, traffic was turned over to OKH/Chi and worked on in ''Referat Vauck'', named and managed by
Wilhelm Vauck.
* Some agents traffic was picked up independently of FU III, by the regular police, the
Ordnungspolizei
The ''Ordnungspolizei'' (''Orpo'', , meaning "Order Police") were the uniformed police force in Nazi Germany from 1936 to 1945. The Orpo was absorbed into the Nazi monopoly of power after regional police jurisdiction was removed in favour of t ...
, known colloquially as the Orpo, who sent their traffic to Kurt Sauerbier at the
Research Office of the Reich Air Ministry (FA), Principle Department IV, Referat 9c. There existed an entirely independent relationship between the Orpo and the Sauerbier and Sauerbier senior officer. Sauerbier's direct senior officer in the FA was Specialist Wenzer, who was an expert in Agents' ciphers and was sent from FU III to the FA to assist Lt. Schubert, of the OKH/GDNA, to assist on Polish Resistance Movement Traffic, in January 1944.
There was, consequently, a certain duplication of effort and a certain amount of confusion as a result of this arrangement. There were also conflicting opinions of the opinions of the successes achieved. Schubert reported that ''Russian agents systems were tried by Dr Vauck, who stated they could not be solved. Later, he said that they were digit substitutions and P/L enciphered with a one-time running key derived from a book. Schubert thought that in the middle of 1944, e.g. the Soviets had about 3,000 agents in the field, and it was impossible to pick out one system and say that it was used in one area. Moreover, Schubert pointed out that he himself had worked on only Partisan and Kundschafter traffic and knew of other systems only indirectly.
Agent codes technical description
For the W/T traffic of the Soviet Partisans and the spies there were used:
* Double Transposition
* Subtractor Reciphers
* Occasional simple substitution systems
The subtractor systems consist of 3 Cipher elements:
* The basic cipher i.e. the substitution of the plain text by a substitution system
* The recipher with the figure subtractor
* The reciphering of the
indicators
Indicator may refer to:
Biology
* Environmental indicator of environmental health (pressures, conditions and responses)
* Ecological indicator of ecosystem health (ecological processes)
* Health indicator, which is used to describe the health ...
''The Basic Cipher''
* On certain links, a 3 or 4-figure code was used as basic cipher.
* In General, however, simple substitution systems were used, which substituted a 1 or 2-figure number for each letter, and were such that seven letters, which usually formed a key-word, were substituted by single figures, and the other three figures were used as tens for the other letters. The following is an example:
Special points of this substitution system are as follows;
* When plain text is enciphered by this system, in the cipher text 2 mostly, or all three, tens-figures occur with particular frequency. The frequencies of the figures vary.
* A letter is not substituted by two like letters. For example., the squares 22,44,66 are empty. This in normal text, no figure can come three times in succession.
* Numbers are recipher by repeating each figure three times: e.g. 1945=111999444555.
:There are two ways of using this system:
* The basic cipher is the same for all messages.
* The basic cipher is variable, i.e. it changes from message to message, with the indicator. The indicator is constructed of five different figures.
* These are written over the letters of the key and completed with the remaining five figures.
The tens figures are taken from empty squares.
The following is an example, with an Indicator of 37245
* There are occasional simple substitution systems which substitute each letter by a 2-figure number.
''The Composition of the Subtractor''
The figure subtractors used are of three different kinds:
:* They are printed on T/P rolls
:* They are taken from tables
:* They are built up from an indicator
* The subtractors printed on T/P rolls were most frequently used and increasingly replaced the other systems, and had the soviet name of ''Blocknot rulon''. The instructions for use stated that each reciphering strip was to be destroyed when it had been used once. There were different rolls for ''in'' and ''out'' messages. Thus an unbreakable individual reciphering is achieved. A subtractor group from the roll, which is not used for reciphering and is sent in the clear, gives the starting point on the strip of the roll used.
:Research into regularities in captured subtractor rules showed that:
:* The rolls are made up on several machines, clearly show by the use of several type-faces.
:* Longish repeats do not occur in a roll.
::The rolls have 5-figure numbers, which are given in clear as indicators in Partisan traffic, but not in Spy-traffic.
* The use of subtractor tables comprises in the main, 4 different systems:
:*There is a simple reciphering with a table of 100-300 groups. The starting point is given by a indicator which gives line and column of the first recipher groups: e.g. 11511=line 11, Column 5. Systems of his kind come especially in the traffic of
NKGB Saint Petersburg
Saint Petersburg, formerly known as Petrograd and later Leningrad, is the List of cities and towns in Russia by population, second-largest city in Russia after Moscow. It is situated on the Neva, River Neva, at the head of the Gulf of Finland ...
(Leningrad), and were solved.
:*There are 100 recipher pages. The first two figures of a 5-figure indicator, made up of five different figures, gives the page used. At the same time the basic cipher is changed by the indicator. This system too occurred especially in the traffic of the
NKGB Saint Petersburg
Saint Petersburg, formerly known as Petrograd and later Leningrad, is the List of cities and towns in Russia by population, second-largest city in Russia after Moscow. It is situated on the Neva, River Neva, at the head of the Gulf of Finland ...
(Leningrad).
:* There is a double recipher. For this is a table of 30 lines of 10 groups. The first recipher is taken from the first 18 lines, the second from lines 19-30. The starting point of the first recipher is given by an indicators, as bullet point 1, the second recipher always begins with the first group of the 19th line. This was also solved.
:* There were besides other isolated systems using independent double recipherment. The system is shown by example. Two groups are table from a simple subtractor table, at a starting point, given by the indicator. e.g.
::
:The following groups in the subtractor table are next changed. This gives the recipher, but of course, has not been solved.
:Note: The marking off into blocks of 1,2 and 3 figures was apparently done to transpose the figures in these blocks according to the key provided by the top line.
*Figure subtractors arithmetically constructed. The subtractors are built up from a 5-figure indicator, which contains five different figures. The methods of building them are demonstrated by examples.
:* A) Simple addition in columns. The most usual type of this subtractor construction are the following: There are two substitution series, e.g.:
::
:The indicator, e.g. 27345 is written down then substituted according to a) and the result written underneath. Then the indicator is substituted according to b) and the answer written at the side of the right:
:27345 69820
:92183
:The groups on the left are now added, and the result written under on the right. Then the two groups on the right are added, and the result put below on the left, and so on:
:27345 69820
:92183 19428
:78248 60321
:79749 47987
:07208 ----- etc.
:The groups are used as subtractor, starting from the second or third line. In some systems, the right hand column is pushed down a line, which was solved. In some cases, the substitution series b) is derived from a). by pushing it along one or more places. The case also occurred of their being only one substitution series, with addition in one column only.
*Simple cross addition. Starting with the indicator, each pair of adjacent figures is added, and the result written alongside. The following is an example:
:Indicator 27345
:Subtractor 27345 90794 97633 63969
:This system occurred only as an emergency cipher, that was solved. There is a variation, in which one skips a figure:
:27345 51896 30426
:or one may add in normal fashion three times and then skips a figure twice:
:27345 90735 97022 .....
:These last systems were in use in conjunction with a changing basic cipher. This was solvable.
*Addition in columns with a key phrase. The basic key varies by the indicator. A key group or phrase is enciphered in accordance with the basic key so that five groups of five are produced. The indicator is written under the first of these groups, the total of these two groups is put under the adjacent one, and so on:
:
:The subtractor is obtained either by adding these two rows and every subsequent row being the total of the last two rows or by containing the addition. This was solved.
*Cross addition with key phrase. By enciphering a key phrase with the fixed basic key, you have a 5 -- 5-figure groups. The indicator is written under the first of these groups; as the next group you take the missing five numbers in ascending order and by cross addition, the five groups are filled in. The first row of the subtractor is produced by adding both rows. For example:
:
:By cross addition of the groups of the first subtractor row, four groups are formed for each original group and these are entered underneath. You then get a block of 25 groups.
:
:From the first group of the block, a key is made up by indicating the figures according to numerical orders by the numbers 1-5.
:23451
:66793
:In accordance with this key, the columns are read out from the columns of the first subtractor block, commencing with the right column. From this, the second subtractor block is created:
:
:The third subtractor block comes correspondingly from the second by re-arranging the second group of the first subtractor row. This was solved. In a variation of this system, the first subtractor block is composed differently, the first subtractor row is exactly the same. The cross addition from the indicator is, however, extended to six groups. The sixth group is put under the first subtractor group. After the formation of the subtractor proceeds as described under c). This was solved. In this last type variable basic keys are also used.
*Substituted cross addition. The indicator is substituted by a table. Five groups are formed by cross addition from the result. These were then converted into the same substitution table. From this, the first subtractor row is obtained.
*Subtractor Boxes. First the figures 1-0 are written down and underneath the indicator and remaining figures. By adding every 2 rows, 9 further rows are formed. The 2-11th row are numbered 1–0. The following is an example.
:
:Then figure pairs are extracted from a particular row, e.g. row 3, and these indicate from which point each 5-figure group is to be read out of the box. This produces:
:56=31420
:69=70169
:92=05050 etc.
:This system appeared in conjunction with the variable basic key. A variation consists in a key phrase being enciphered on a basic key and from this, the first rows of the box are formed. This was not solved. Recognition of the subtractor system and its solution was achieved by the appearance of similar message endings and beginnings.
''Indicators''
Indicators for the subtractor, based on the roll, were always inserted ''plain''. In the other systems there were several ways of putting in the indicator. Apart from a few exceptions, there were always two indicators. Possibilities regarding reciphering of these indicators were as follows:
*Indicator groups plain
*A certain 5-figure number is added to every indicator and the number is a constant
*A certain group of the message is added to every indicator group.
*Like bullet list 3, with the different that groups in the message are converted according to a substitution table
*Like bullet list 4, where different substitution tables are used for the two groups of the message to be converted
*Like bullet list 3, except that figures of the message groups are arranged in order and then added to the indicator group
*Certain figures are extracted from several groups of the message, which are almost invariably the first five groups, for instance, the last figures of the first five groups and then added to the indicator group
*Like bullet list 7, but substitution the adders in accordance with a substitution table.
*Combinations of two of the above methods, doubled recipher of indicator groups, e.g. 2 with 3, 2 with 4, 2 with 5, twice 3.
In general both indicators are reciphered on the same process, where one indicator is included at the beginning and one at the end of the message. The groups used for enciphering are also taken one each from the beginning and the end of the message.
Miscellaneous cryptanalysis
1939 to 1941
German Army Cryptanalytic Effort 1939-1941
In the early years of the war, the cryptanalytic staff of the
ef 5.1were unable to cope with the added burden of the wartime traffic. The British section of the HLS was unable to solve British systems. The failure of the British section of the to achieve any success with British ciphers and codes continued. In 1940, the six people comprising the section were moved to
Bad Godesberg where no successes were achieved despite an abundance of material with which to work on. Dr
Otto Buggisch who, in 1942, looked over the files of the British section regarding work on the British high grade machine,
Typex, characterised the work of Inspector Breede who worked in the winter of 1939–1940 on the British "big machine" as complete nonsense. Buggisch stated that Breede described an imaginary machine which had nothing whatever to do with Typex. No cryptanalytic success was recorded in this period. In April 1940, however, the British section received a copy of the British War Office Code captured in
Bergen
Bergen (, ) is a city and municipalities of Norway, municipality in Vestland county on the Western Norway, west coast of Norway. Bergen is the list of towns and cities in Norway, second-largest city in Norway after the capital Oslo.
By May 20 ...
during the
Norwegian Campaign. A second copy was obtained at
Dunkirk
Dunkirk ( ; ; ; Picard language, Picard: ''Dunkèke''; ; or ) is a major port city in the Departments of France, department of Nord (French department), Nord in northern France. It lies from the Belgium, Belgian border. It has the third-larg ...
. Successes with this system were therefore possible, since the British continued to use this system until 1943.
The failure of the cryptanalysts of the Horchleitstelle to solve independently the French Army succeeding the F110 was another indication of their inadequacy. In early autumn 1939, the French replaced the peacetime ciphers, the F90 and F110 cipher with a new wartime cipher whose names was not known to
TICOM
TICOM (Target Intelligence Committee) was a secret Allied project formed in World War II to find and seize German intelligence assets, particularly in the field of cryptology and signals intelligence.
It operated alongside other Western Allied ...
sources. The French section was forced to call upon the services of the
Cipher Department of the High Command of the Wehrmacht
The Cipher Department of the High Command of the Wehrmacht () (also ''Oberkommando der Wehrmacht Chiffrierabteilung'' or ''Chiffrierabteilung of the High Command of the Wehrmacht'' or ''Chiffrierabteilung of the OKW'' or ''OKW/Chi'' or ''Chi'') ...
(''OKW/Chi'') to aid in the solution of French Army systems.
Erich Hüttenhain was sent to the Army Intercept Station in
Frankfurt
Frankfurt am Main () is the most populous city in the States of Germany, German state of Hesse. Its 773,068 inhabitants as of 2022 make it the List of cities in Germany by population, fifth-most populous city in Germany. Located in the forela ...
to aid in the solution. Among his papers were two memoranda, where Hüttenhain reported that the task was accomplished with his own colleagues at OKW/Chi by October 1939. Among those who worked with Hüttenhain, when on 2 September 1939, the old French Army F110 code was changed was Professor
Ludwig Föppl
Karl Ludwig Föppl (27 February 1887 – 13 May 1976) was a German mechanical engineer who succeeded his father, August Föppl as professor of technical mechanics at the Technical University of Munich. During World War I, Föppl worked as a cr ...
of HLS with Trappe and Schmidt of OKW/Chi. There were not enough cryptanalysts on HLS to furnish the forward units with adequate staffs. The system worked so successfully that all the September material could be read retrospectively. The system continued to be worked on successfully through to November. Hüttenhain returned to his own agency with the system solved. It may be noted that the head of the Army station requested of Hüttenhain to convey the thanks of the army to OKW/Chi for the assistance given to HLS's section and remarked that in his opinion such a large cryptographic task could not be done by the Army Command either then or in the near future.
The system was solved until the German offensive in the spring of 1940. At this time, the French began to use systems in forward echelons which Horchleitstelle was unable to solve. Mettig remarked that the Army cryptanalysts both of the forward units and the HLS finally concentrated on two machine systems, the
C-36 cipher machine and the
B-211. Neither was solved however, until after the
Armistice of 22 June 1940
The Armistice of 22 June 1940, sometimes referred to as the Second Armistice at Compiègne, was an agreement signed at 18:36 on 22 June 1940 near Compiègne, France by officials of Nazi Germany and the French Third Republic. It became effective a ...
and a considerable quantity of captured documents. According to Mettig, the final solution of these two machines rated lower than that of the preceding system since it was not timely and was done only with the aid of captured material.
In the winter of 1939, the dearth of field cryptanalysts became apparent to the German Army. When the (KONA) signal intelligence regiments were preparing to move into the field, the army found that there were no trained cryptanalyst personnel to send with them. Colonel
Kunibert Randewig, the commander of all intercept units in the west, was able to procure cryptographers for intercept units around Berlin and filled out that number with mathematicians and linguists.
=Summary
=
HLS achievements during this period were minor, their success in intercepting traffic and solving known systems was a great aid to the
German Army
The German Army (, 'army') is the land component of the armed forces of Federal Republic of Germany, Germany. The present-day German Army was founded in 1955 as part of the newly formed West German together with the German Navy, ''Marine'' (G ...
. Mettig stated that all messages which succeeded the F110 cipher were read from late 1939 and these messages, despite their administrative nature helped to reveal the tactical layout of the French. For example, the strength of units on the training ground at
Mourmelon was estimated by statistics of water bottles and blankets. It was possible to deduce facts about the shortage of armour-piercing ammunition with the French infantry units. Similarly, the conversion of the
Second
The second (symbol: s) is a unit of time derived from the division of the day first into 24 hours, then to 60 minutes, and finally to 60 seconds each (24 × 60 × 60 = 86400). The current and formal definition in the International System of U ...
and Third French Cavalry Divisions into Armoured Divisions in the area north-east of Paris was ascertained in December 1939. By the end of 1939, the complete
order of battle
Order of battle of an armed force participating in a military operation or campaign shows the hierarchical organization, command structure, strength, disposition of personnel, and equipment of units and formations of the armed force. Various abbr ...
of the
French Army
The French Army, officially known as the Land Army (, , ), is the principal Army, land warfare force of France, and the largest component of the French Armed Forces; it is responsible to the Government of France, alongside the French Navy, Fren ...
was known to Germany. The capture of a copy of the British War Office Code in Norway in 1940 and a copy in Dunkirk in June of that year, afforded the British section its first successes and furnished a constant and important source of information from that time until 1943, when the British discontinued use of the code.
In this period, the Germans realised the inadequacy of their personnel effort, and set about correcting them.
Period from 1941 to 1945
German Army Cryptanalytic effort 1941-1945
Western and Southwestern Cryptanalysis 1941-1944
Western and southwestern cryptanalysis was handled at ''In 7/VI'' by British section with outposts in North Africa, Athens, Paris and Bergen, Norway. The American and the French section with subsections for the Swiss, Spanish,
Portuguese and Brazilian traffic. The Italian section was within this group. The field units which handled western and southwestern traffic were the western field units,
KONA 5 and
KONA 7. The
Swedish Army
The Swedish Army () is the army, land force of the Swedish Armed Forces of the Kingdom of Sweden. Beginning with its service in 1521, the Swedish Army has been active for more than 500 years.
History
Svea Life Guards dates back to the year 1 ...
traffic was handled by a special unit of
Feste 9 in Norway.
Work on British traffic 1941-1944
=War Office Code
=
During the years 1941–1943, the main success of the British section was the reading of the British
War Office Code (WOC), two copies which had been captured in early 1940, from Dunkirk and in Bergen, Norway. The code was numerical 4-Figure groups, enciphered by means of a subtractor. After the capture of these documents, the British section under Inspektor Liedtke was successful in reading messages from North Africa during the spring of 1941, encoded with WOC and superenciphered with additives. British traffic encoded with WOC was read constantly throughout 1941. In March of that year, a considerable volume of messages was read during the British Cyrenaic Offensive
Operation Compass
Operation Compass (also ) was the first large British military operation of the Western Desert Campaign (1940–1943) during the Second World War. British metropolitan, Imperial and Commonwealth forces attacked the Italian and Libyan forces of ...
of the British
8th Army under General
Archibald Wavell
Field Marshal Archibald Percival Wavell, 1st Earl Wavell, (5 May 1883 – 24 May 1950) was a senior officer of the British Army. He served in the Second Boer War, the Bazar Valley Campaign and the First World War, during which he was wounded ...
. The organisation of the base services and the Order of Battle of the Army were recognised. During the late summer of 1941, General
Erwin Rommel
Johannes Erwin Eugen Rommel (; 15 November 1891 – 14 October 1944), popularly known as The Desert Fox (, ), was a German '' Generalfeldmarschall'' (field marshal) during World War II. He served in the ''Wehrmacht'' (armed forces) of ...
's counter-attack took place leading to the
Siege of Tobruk
The siege of Tobruk () took place between 10 April and 27 November 1941, during the Western Desert campaign (1940–1943) of the World War II, Second World War. An Allies of World War II, Allied force, consisting mostly of the 9th Division ...
. The besieged fortress was solely dependent on radio for its signal communications to the 8th Army and
Cairo
Cairo ( ; , ) is the Capital city, capital and largest city of Egypt and the Cairo Governorate, being home to more than 10 million people. It is also part of the List of urban agglomerations in Africa, largest urban agglomeration in Africa, L ...
, and as it used the WOC with an enciphering table almost exclusively, its traffic was read by ''OKH/Chi''. The British section followed accurately the British 8th Army's relief attempts in November 1941, which led to the cutting off of Rommel between Tobruk,
Sidi Omar and
Sallum, eventually leading to Rommel's break-out to the west as
Sidi Rezegh.
As the result of the success with the WOC in Berlin, a special detachment of eight
cryptanalysts was sent to the evaluation centre of KONA 4 at
Athens
Athens ( ) is the Capital city, capital and List of cities and towns in Greece, largest city of Greece. A significant coastal urban area in the Mediterranean, Athens is also the capital of the Attica (region), Attica region and is the southe ...
to solve traffic at that point and thereby reduce the time wasted in sending the traffic back to Berlin. Unfortunately for ''OKH/Chi'' about the time the party started in December 1941, certain difficulties were encountered in the solution of the War Office Code which prevented the solution of the WOC for the following eight or nine months. During this time period the British section suffered a further blow through the capture in July 1942 of the greater part of
FAK 621, which had been in operation in
North Africa
North Africa (sometimes Northern Africa) is a region encompassing the northern portion of the African continent. There is no singularly accepted scope for the region. However, it is sometimes defined as stretching from the Atlantic shores of t ...
under the aristocratic Seebohm. Although the remnants of the unit continued to operate under a Captain Habel, information gained from the captured part of the unit provided evidence to the British that their code was being read and from that time, the British section had no success with the code.
Heinz Wolfgang Herzfeld stated in interrogation, that after his return to Berlin in October 1942, there was a little WOC traffic but that its volume was too small for successful exploitation. From December 1942 to March 1943, the British used enciphered indicators, and in March and April 1943 changed to a form of
One-time pad
The one-time pad (OTP) is an encryption technique that cannot be Cryptanalysis, cracked in cryptography. It requires the use of a single-use pre-shared key that is larger than or equal to the size of the message being sent. In this technique, ...
s for enciphering tables. The British section had no success with these innovations although Liedtke worked for a year attempting to break into the new system.
=Slidex
=
From 1942 to end of the war, the only success attained was with the British low-level traffic, particularly
Slidex. Slidex was designated by Germany as English Code () (EC), followed by a number to denote the variations of the basic system. Slidex was used by the British and later by the American and Canadian Army in front line units and in air support networks. The variations of the EC system mentioned in
TICOM
TICOM (Target Intelligence Committee) was a secret Allied project formed in World War II to find and seize German intelligence assets, particularly in the field of cryptology and signals intelligence.
It operated alongside other Western Allied ...
sources are:
[IF-120 p. 3]
After D-day,
Slidex was also used by the American Army. When Germany found that American
military police
Military police (MP) are law enforcement agencies connected with, or part of, the military of a state. Not to be confused with civilian police, who are legally part of the civilian populace. In wartime operations, the military police may supp ...
units were using Slidex to report all Army units which passed their control points, the deciphering of Slidex was given high priority.
[I-80 p. 3] Slidex messages were also particularly valuable for identifying bombing and artillery objects. The time estimate for the solution of Slidex was one to three hours if the basic cards were at hand, five or six hours if they were not. 65% of the work is said to have been done with the cards available.
=Low grade codes and ciphers
=
Not much material concerning other British low-grade systems solved was found by
TICOM
TICOM (Target Intelligence Committee) was a secret Allied project formed in World War II to find and seize German intelligence assets, particularly in the field of cryptology and signals intelligence.
It operated alongside other Western Allied ...
. Hentze of KONA 5 stated that Maplay code was worked on throughout 1944, but this code was harder to break than Slidex, and were successful only with a great deal of traffic. Codex was solved by ''OKH/Chi'' largely with the help of a captured specimen which had been in the possession of Germany since the days of the
Leros Invasion.
It was read by Feste 9 in 1944–1945, when that unit was in Italy.
A Tiger-code, so called from its use during
Exercise Tiger, was solved by ''OKH/Chi'' after six month's work. Solution was made possible by a long report in a British paper giving the names of the units, officers, etc. Another British system, the ''999'' code which was used during the pre-invasion period, was solved by ''In 7/VI'', but was never used operationally. KONA 5 is said to have had considerable success with the Tiger-code and to have achieved a solution on the 4th or 5th day after its regular monthly changes. Matin, another
British Army
The British Army is the principal Army, land warfare force of the United Kingdom. the British Army comprises 73,847 regular full-time personnel, 4,127 Brigade of Gurkhas, Gurkhas, 25,742 Army Reserve (United Kingdom), volunteer reserve perso ...
system, was never solved. Rudolf Hentze stated that Germany arrived at the decision that Matin was a small machine, but he does not say whether research on this system was carried out at ''OKH/Chi'' or in KONA 5.
=Failures
=
The outstanding failure of the British section of ''OKH/Chi'' and of ''OKH/Chi'' in general, was the failure to solve the British ''big machine'',
Typex. Mettig states that had ''OKH/Chi'' been able to solve this system, it would have been their outstanding achievement.
Mettig stated that Typex was read in 1942 from which time ''OKH/Chi'' had no more success.
[I-48 p. 3] Ultra sources state that FAK 621 in
North Africa
North Africa (sometimes Northern Africa) is a region encompassing the northern portion of the African continent. There is no singularly accepted scope for the region. However, it is sometimes defined as stretching from the Atlantic shores of t ...
had been reading Typex at the time of its capture in North Africa in July and November 1942, brought about a thorough investigation of this subject by TICOM interrogators. The story in brief was that in June 1943 one of the prisoners claimed that he had worked on British machine methods from 1937 to 1940 and that messages which could not be decoded by FAK 621, were sent to ''In 7/VI'' in Berlin. Two prisoners from FAK 621, Haunhorst and Possel, stated that all high grade traffic was handled by a Warrant Officer named Wagner. Wagner had one or two Typex machines at his disposal which had been captured in
Tobruk
Tobruk ( ; ; ) is a port city on Libya's eastern Mediterranean coast, near the border with Egypt. It is the capital of the Butnan District (formerly Tobruk District) and has a population of 120,000 (2011 est.)."Tobruk" (history), ''Encyclop� ...
. The evidence given by Wagner was later contradicted by Dr
Erich Hüttenhain, Dr
Walter Fricke of the
OKW/Chi and Colonel Mettig emphatically denied having solved or heard of a solution to Typex. They had never seen a Typex machine with rotors although all admitted that a Typex machine without rotors had been captured at Dunkirk. The TICOM interrogators of Hüttenhain and Fricke reported:
:''Should it turn out that some experts named above, e.g. Mettig were in possession of a complete Typex machine and have achieved successes, both these people (POW's) would lose their last faith in their fellow beings''.
Mettig, moreover, stated categorically that a success of this nature would have been mentioned in the list of German cryptographic success which was drawn up for him, prior to his visit to
Supreme Headquarters Allied Expeditionary Force
Supreme Headquarters Allied Expeditionary Force (SHAEF; ) was the headquarters of the Commander of Allies of World War II, Allied forces in northwest Europe, from late 1943 until the end of World War II. US General Dwight D. Eisenhower was the ...
. Mettig's statement about Typex (being read in North Africa) may have been misstatement for Slidex. At least, the interrogators assumed Hüttenhain, Fricke and Mettig were speaking the truth.
Although it is almost certain that ''OKH/Chi'' never solved Typex, a great deal of effort was expended on the project from 1940 to 1943. In January 1942, the files relating to the work on Typex were handed over to
Otto Buggisch, who found work dating back to 1940, when Inspector Breede of the British section had attempted to solve the system. Breede recognised the traffic as machine traffic but described a purely imaginary machine, which Buggisch says bore no relation to the actual Typex, and as complete nonsense. In 1941, some mathematical studies were made on Typex, and in January 1942, Buggisch made a study of the system, from which he made the following conclusions:
* The system was similar to that of the Enigma, according to a single letter frequency counts based on 10,000 cipher letters.
* Certain relationships between the two message-settings frequently existed.
There was no evidence that Buggisch proceeded further than this in his investigation. There seem to be no knowledge of how many rotors the Typex had. Buggisch estimated up to 25. No one at ''OKH/Chi'' knew the inner wiring of the wheels, nor how many wheels there were, so the question of cryptanalysis was of no practical interest. The whole matter was evidently permanently abandoned sometime in 1943.
Work on USA Traffic 1941-1944
The USA section of ''In 7/VI'' was created with the entry of the United States into the war in early December 1941.The section, made up of personnel who had been drafted from the mathematical section of ''OKH/Chi'', was placed under the leadership of Friedrich Steinberg, a leading mathematician. Initial attempts at breaking USA traffic was fraught with difficulties. Due to the size of the US wireless network and the use of alternative frequencies by USA operators, considerable trouble was experienced in identifying the various links and sorting the different systems. After a few weeks however, order was established through the reading of
Call sign
In broadcasting and radio communications, a call sign (also known as a call name or call letters—and historically as a call signal—or abbreviated as a call) is a unique identifier for a transmitter station. A call sign can be formally as ...
s and the sorting of discriminants.
The first major success of the US section was in the summer of 1942 when the
M-94 device was solved. In 7 designated the M-94 unit, either ''URSAL'', ''CDAF'', strip and ''ACr2''. URSAL was given to the system from the fact that traffic from the US weather stations in
Greenland
Greenland is an autonomous territory in the Danish Realm, Kingdom of Denmark. It is by far the largest geographically of three constituent parts of the kingdom; the other two are metropolitan Denmark and the Faroe Islands. Citizens of Greenlan ...
which used URSAL as an indicator provided the first breaks into the system. CDAF was found in the traffic emanating from the Caribbean Defense Area.
[IF-107 p. 4] Strip and ACr2 () stem from the fact that this system was long thought to be a strip system. The solution of the M-94 was achieved by Friedrich Steinberg and Hans-Peter Luzius, mathematicians of the US section, who are said to have written a 25-page report on their work. After the cryptanalytic solution was achieved, a USA manual (FM 11–5) with a complete description of the M-94 was found in a Berlin library.
Current solution of the M-94 from 1942 to 1943 was done both at ''OKH/Chi'' and at KONA 5 at St. Germanin. The work consisted of finding the daily key. A set of 25 charts of synoptic tables, corresponding to the 25 discs of the machine was constructed, apparently similar to the
synoptic tables used by American cryptanalysts. The daily key was found by assuming a beginning, and using the charts to discover possible disc arrangements. Later,
IBM
International Business Machines Corporation (using the trademark IBM), nicknamed Big Blue, is an American Multinational corporation, multinational technology company headquartered in Armonk, New York, and present in over 175 countries. It is ...
machinery was used to eliminate impossible charts. Graupe of NAAS 5 stated that it usually took two days to recover the order of the discs and that only fifty groups were required for the system to be broken.
Estimates on the amount of material solved range from 70% to 90%.
The M-94 was succeeded in 1943 by the
M-209, which was first solved by the Germans in the autumn of 1943,
[IF-107 p. 5] and continued to be solved with some success throughout the remaining years of the war. The breaking of M-209 was achieved in ''OKH/Chi'' by Steinberg and Luzius, who were aided by the knowledge that the US government had brought the Hagelin machine which had once been offered to the German government.
At first only relative settings could be recovered, but later the section refined its technique of recovering absolute settings so that not only paired messages but in a large number of cases, a whole day's traffic could be read. The technique of achieving true settings was passed on by ''OKH/Chi'' to the Kriegsmarine and the Luftwaffe.
Work on an operational level was carried out jointly by the US section of ''OKH/Chi'' and NAAS 5 at St. Germain. Early in 1944, NAAS 4 had been supplied with a group of cryptanalysts skilled in work on the M-209, and this small group competed with the section at ''In 7/VI'' in the quick solution of M-209 traffic. It estimated that 10%-20% of all M-209 messages intercepted were read by establishing the true settings of the wheels, and that about half of these settings were established at ''OKH/Chi'', half at NAAS 5.
[IF-153 p. 1] To insure speedy solution all subordinated to KONA 5 were ordered to teleprint to NAAS 5 all messages on the same settings or with
Indicators
Indicator may refer to:
Biology
* Environmental indicator of environmental health (pressures, conditions and responses)
* Ecological indicator of ecosystem health (ecological processes)
* Health indicator, which is used to describe the health ...
differing only in the first two letters. Under the most favourable circumstances two days were needed to solve a
depth, and two more days to reconstruct the absolute settings. There were times, however, when captured lists of keys or settings made possible a quick solution of the traffic. During the
Allied invasion of Sicily
The Allied invasion of Sicily, also known as the Battle of Sicily and Operation Husky, was a major campaign of World War II in which the Allies of World War II, Allied forces invaded the island of Sicily in July 1943 and took it from the Axis p ...
and the
Allied invasion of Italy
The Allied invasion of Italy was the Allies of World War II, Allied Amphibious warfare, amphibious landing on mainland Italy that took place from 3 September 1943, during the Italian campaign (World War II), Italian campaign of World War II. T ...
, messages of great tactical value were decoded using captured booklets containing M-209 settings.
At the time of the
Normandy landings
The Normandy landings were the landing operations and associated airborne operations on 6 June 1944 of the Allies of World War II, Allied invasion of Normandy in Operation Overlord during the Second World War. Codenamed Operation Neptune and ...
, the M-209 keys of the
82nd Airborne Division
The 82nd Airborne Division is an Airborne forces, airborne infantry division (military), division of the United States Army specializing in Paratrooper, parachute assault operations into hostile areasSof, Eric"82nd Airborne Division" ''Spec Ops ...
and
101st Airborne Division
The 101st Airborne Division (Air Assault) ("Screaming Eagles") is a light infantry division (military), division of the United States Army that specializes in air assault military operation, operations. The 101st is designed to plan, coordinat ...
which covered the critical days of 6–11 June were captured and all traffic on those days was read.
''In 7/VI'' knew of the existence of a ''big American machine'' which was designated the AM1 (), but it was clear that ''OKH/Chi'' never solved this machine and had no idea about its construction.
[IF-153 p. 2] Hentze stated that his unit (KONA 5) never succeeded in getting a model of the machine. Other statements by ''OKH/ChiI'' that the machine was tackled in Berlin was considered ''utter nonsense''.
''OKH/Chi'' were successful with American codes. The Army Administrative Code, designated by ''In 7/VI'' as AC 1 () had been captured before 1939, and photostatic copies of the code had been distributed to all field cryptanalytic units.
The code was a 5-letter code with 60,000 groups, each page containing 90 groups.
[IF-120 p. 4] Feste 9, intercepted and read traffic from this code from the summer of 1942 to the autumn of 1943, while stationed in Bergen, Norway.
Although no traffic of strategic value was passed, the intelligence was valuable enough so that when AC 1 was succeeded by a simplified version designated as
TELWA, Feste 9 reconstructed the code.
Feste 9, aided by the US section of ''OKH/Chi'', also broke the simple codes used by the US Army units stationed in
Iceland
Iceland is a Nordic countries, Nordic island country between the Atlantic Ocean, North Atlantic and Arctic Oceans, on the Mid-Atlantic Ridge between North America and Europe. It is culturally and politically linked with Europe and is the regi ...
and the
Caribbean
The Caribbean ( , ; ; ; ) is a region in the middle of the Americas centered around the Caribbean Sea in the Atlantic Ocean, North Atlantic Ocean, mostly overlapping with the West Indies. Bordered by North America to the north, Central America ...
. These were designated as Divisional Field Code (DFC) followed by a number indicating the variation of the system. The variations described in TICOM sources were: DFC 15, 16, 17, 21, 25, 28, 29.
Mention should also be made of the success of the US section of ''OKH/Chi'' with the Air Transport Code used for air cargo and passenger transport circuits to Africa and South America.
This code, consisting of two-figure elements from 00 to 99, was successfully decoded by ''In 7/VI'' from May 1942 until early 1943, when it was given to the German Air Force, the
Luftwaffe
The Luftwaffe () was the aerial warfare, aerial-warfare branch of the before and during World War II. German Empire, Germany's military air arms during World War I, the of the Imperial German Army, Imperial Army and the of the Imperial Ge ...
.
=Summary
=
The work on ''OKH/Chi'', USA section, appears to have been successful in low-grade ciphers and in some medium grade ciphers such as M-94 and M-209. Mettig rated the solution of the M-209 as the outstanding achievement of this section and one of the best of ''In 7/VI''. It is clear also from references concerning the work on this system made by members of other agencies such as
Wilhelm Tranow and
Ferdinand Voegele, that the US section of ''OKH/Chi'' evolved the best technique of solving the M-208 and led the other German Signals Agencies in the work on this system.
Work on French traffic 1941-1944
French traffic from 1941 to 1944 was of two main types,
Vichy France
Vichy France (; 10 July 1940 – 9 August 1944), officially the French State ('), was a French rump state headed by Marshal Philippe Pétain during World War II, established as a result of the French capitulation after the Battle of France, ...
and
Free France
Free France () was a resistance government
claiming to be the legitimate government of France following the dissolution of the Third French Republic, Third Republic during World War II. Led by General , Free France was established as a gover ...
. Vichy French traffic which was under the direct control of the
French Armistice Commission at
Wiesbaden
Wiesbaden (; ) is the capital of the German state of Hesse, and the second-largest Hessian city after Frankfurt am Main. With around 283,000 inhabitants, it is List of cities in Germany by population, Germany's 24th-largest city. Wiesbaden form ...
was monitored by the French section of ''In 7/VI''. By agreement with the Vichy government, the French were to inform Germany of their code and cipher procedures, but wary watch was kept on their traffic. The work on Free French traffic which emanated during this period from Free French troops in Syria and in North, West and Equatorial Africa was carried out by ''OKH/Chi'' and the Sig. Int. Evaluation centres of Signal Intelligence Regiment (KONA)#Kona 4, KONA 4 in
Athens
Athens ( ) is the Capital city, capital and List of cities and towns in Greece, largest city of Greece. A significant coastal urban area in the Mediterranean, Athens is also the capital of the Attica (region), Attica region and is the southe ...
where the traffic was easily intercepted.
In a list compiled by the director of the French section, of the Free French systems worked on by ''In 7/VI'' and NAAS 4, the following systems were mentioned as being used in Syria:
* A 3-Letter system: code table with fortnightly key change. This system appeared from about 1942 to the middle of 1944 in Syria, but was not intercepted after this. Content is described as moderate to good.
* A variant of the above code which passed technical details of wireless traffic. A 3-Letter system: code table with fortnightly key change. Appeared in 1943 to middle of 1944. Sometimes it was used for passing weekly changing call-signs.
* Police systems which appeared rarely, according to Kühn, that were either 2-Figure substitution tables or simple transpositions.
* A 4-Figure code with daily key change. Appeared in 1944 in the Syrian coastal network. Message traffic described ship movements in the coastal area.
From other sources may be added the Charles de Gaulle, de Gaullist's systems, two of which are named: Control Beduoin and Service Politique. These were initially read from traffic intercept at the French garrison at Bir Hakeim, but had proved impossible until the same cipher was used in Syria by the de Gaulle party. The work on French systems of KONA 4 was summarised by two members of KONA 4 who stated:
:''All Syrian traffic was read and a complete picture obtained of the French armed forces''.
Among the Free French systems from North Africa which were solved and read by the units were listed by Kühn:
* 5-Letter messages from a diagonal transposition system with monthly, later semi-monthly changes, used in West Africa from 1943 to 1945. It was later discovered from a captured document that this system has been in use from
World War I
World War I or the First World War (28 July 1914 – 11 November 1918), also known as the Great War, was a World war, global conflict between two coalitions: the Allies of World War I, Allies (or Entente) and the Central Powers. Fighting to ...
, and was resurrected evidently for use in West Africa.
* TTSF code. This was a 4-Letter code reciphered by letter substitution into 4 letter cipher text. The first group of the message was always TTSD; the last group the indicator. The code was used in North Africa from 1944 to 1945 for routine messages.
* 5-Letter messages from a diagonal transposition used in Equatorial Africa in 1943–1944.
* 5-Figure messages from a 4-Figure hatted code, designated ''ATM 43'' Hans Wolfgang Kühn, who was Director of Referat 3 of ''OKH/Chi'', notes that ATM 43 derived its name from the fact that it was possible to use the vocabulary of the pre-war French code, the ATM, in the reconstruction of this code.
* 4-Figure code with subtractor used towards the end of the war, on the Italian front.
* 3-Figure messages from a 4-Figure code with subtractor. This system was used in
North Africa
North Africa (sometimes Northern Africa) is a region encompassing the northern portion of the African continent. There is no singularly accepted scope for the region. However, it is sometimes defined as stretching from the Atlantic shores of t ...
in 1944 for transport work.
A 5-Figure de Gaulle code was used in North, West, and Equatorial Africa, and later in France, which had not been solved by the end of the year despite efforts made by ''In 7/VI'' from 1941 to 1942. In 1041
Otto Buggisch stated that he worked on this code for Werner Kunze, a Pers Z S cryptanalyst. However, no success was obtained, until compromise revealed that the code was transposed with daily changing keys. No further headway was made with this system.
The French section had solved the
C-36 and the
B-211, the machine cipher similar to the Soviet K-37 cipher machine system, after the French campaign in 1940. When the de Gaullist troops in North Africa and Corsica began to use the C-36 machine for their traffic, the French section already had a solution and it was easily solved during 1943. When a new indicator system based on numbers was introduced in early 1944, a high percentage of the traffic continued to be solved through the use of cribs and statistics. The indicator system itself was broken in the autumn of 1944.
At the end of the TICOM ''homework'' written by Kühn, on the French systems treated by the French section of ''In 7/VI'' and KONA 4, Kühn stated that the French section was greatly aided by certain fundamental weaknesses in French cryptography, which lead to easy solutions of most of their systems. These weaknesses were described by Kühn, stated thus:
* The extraordinary conservatism of the French regarding the construction of their code systems or reciphering methods. Systems which must have been used in
World War I
World War I or the First World War (28 July 1914 – 11 November 1918), also known as the Great War, was a World war, global conflict between two coalitions: the Allies of World War I, Allies (or Entente) and the Central Powers. Fighting to ...
, were used in slightly modified form up to 1945, in West Africa. Reciphering methods are regularly of two types: either subtraction with finite subtractors or transposition with keywords taken from the code.
* The habitual use by the French of stereotyped message beginnings and endings which facilitates breaking into the systems.
* The idiosyncrasy of the French of communicating cipher matters or key changes by radio. For instance, through the diagonal system in West Africa, ''OKH/Chi'' was able on several occasions to break the key for the
C-36 cipher machine and once a key change for the ATM 43 code was announced.
With these weaknesses, it was possible for the French section to read all or most of Free French traffic during the years 1941–1944. Their previous experience with the C-36 and B-211, provided ''In 7/VI'' with solutions to the cipher traffic as it was being used by the Charles de Gaulle party. No high grade traffic appears to have been passed by the French during this period.
Work on Swiss, Spanish and Portuguese and Brazilian traffic
From the 1941–1944, the French section of ''OKH/Chi'' had subsections for Swiss, Spanish, Portuguese and Brazilian traffic. As Kühn stated, the volume of traffic was small and unimportant.
Otto Buggisch worked with Kunze of Pers Z S on the solution of the Swiss Enigma machine#Enigma K, Enigma K. Although they worked on a theoretical solution of the machine, and applied the solution to trial enciphered text, created by Buggisch himself, the theory was never applied at ''In 7/VI'' to Swiss traffic, as the volume of traffic did not warrant the effort. Moreover, easy solution of the traffic was precluded by the fact that the Swiss did their own wiring of the Enigma wheels and changed these frequently.
Monitoring of Spanish, Portuguese and Brazilian traffic was coordinated by the French section of the unit, and was carried out by various KONA field units. From 1939 to 1942, Signal Intelligence Regiment (KONA)#Feste 3, from 1942 to 1943, it was Signal Intelligence Regiment (KONA)#FAK 624, FAK 624 and from 1944, by FAK 624 and Signal Intelligence Regiment (KONA)#Feste 12, Feste 12. The amount of traffic read in these units was evidently small enough to be handled by the personnel stationed there. A Spanish military transposition code and a Spanish digit with variant codes were read. Of seven Brazilians systems known, five were read.
Work on Italian traffic 1941-1944
From the beginning of the war, the security of the Italian systems was a matter of constant concern to Germany. An Italian section under Captain Dr. Fiala was established in the unit to check the security of Italian traffic, particularly on the route from Italy to North Africa. Germany feared that Afrika Korps troop movements in North Africa, were being betrayed by the insecurity of the Italian codes and ciphers.
As early as 1941, Dr. Fiala paid a visit to Rome to notify the Italians of the weaknesses of their systems and to request greater security. The visit made little impression on the Italians who remained confident of their own systems. An attempt to improve Italian security as well as to demonstrate the use of Unit record equipment, IBM Hollerith machinery section of ''In 7/VI''. Captain Bigi, who was a cryptanalyst of the Servizio Informazioni Militare, the cipher bureau of the Italian Army was sent, but his report did not result in any changes in Italian cryptography. Captain Bigi's next visit to Berlin met only with coldness on the part of ''OKH/Chi'' staff. By late 1942, the general impression among the Germans was that the Italians were incapable of improving their own systems, even with Inspectorate 7 monitoring them. The Italian section of the unit was disbanded in 1942 when a leader order () was issued by Hitler.
In June 1943, with the Armistice of Cassibile (Italy's defection from a German viewpoint) to the Allies, the work on the Italian Referat was restarted at ''OKH/Chi''. The section consisted of small cadre, with Manaigo as section head. Heinz Wolfgang Herzfeld gave an account of this section's work to TICOM. Herzfeld worked on 400 messages that had been intercepted in May, to July 1943. Herzfeld worked on the material which consisted of 5-Figure messages. In the beginning of September 1943, an Italian reciphering table and some messages had been taken from the office of the Italian Commanantura in Athens, arrived in the section. When Benito Mussolini had been arrested, and the armistice had been signed, some German officers of KONA 4, stationed at the Neo Phaliron Velodrome, drove to the Commanantura on Amerikis Street in Athens, walked into the cipher office and started collecting material lying on the tables in the office, and packing it into a case, in front of Italian staff. When Italian officers came in, began shouting, and a scuffle started, the Germans left with the case. The reciphering table was used in the Ellade code and the Piave code.
In November 1943, the section was again dissolved, this time by Major Lechner. The decision to disband the section the second time, was justified such that after the fall of Leros, no more Italian wireless traffic was intercepted.
The two codes worked on by the section, in the later period was the Ellade and Piave codes. The enciphering tables captured in Italy enabled the Piave code to be reconstructed and enabled many messages to be captured from Northern Italy. The Ellade code was partly reconstructed when the section was dissolved from lack of current traffic.
At the end of the war,
KONA 7 was ordered to cover the traffic of Italian bands in Northern Italy.
Work on Swedish traffic 1941-1944
Work on Swedish Army traffic from 1941 to 1944 was handled by a special detachment of
Feste 9 called Out Station Halden, named from the fact that it was located in Halden. For administrative purposes the station was attached to the Halden Police. According to Bartel, a German cryptanalyst who worked on these systems, the following Swedish Army systems were worked on:
* SRA 1, SRA 5: A revolving grille system. Numerous cases of compromises occurred and the systems continuously read. First broken in the spring or summer of 1943.
* HGA grille: A more difficult system not read by NAA 11 or Feste 9 in Norway. This was worked on by Pers Z S but without success.
* SC 2: read in May 1943. A simple field code like Slidex.
* SC 3: read in April 1943. Simple, partly alphabetical 3-letter field code without reciphering.
* SC 4: read in June 1943. 3-letter alphabetical code without recipher.
The first Swedish cipher machine () () was worked on in Norway in 1944 and was identified as similar to a small Hagelin cipher machine like the
M-209. Messages were read at Halden with cribs, by errors in the cryptography, or by having two messages in the same key. The second machine (SM 2) was thought to be a ''large Hagelin'' machine. Two copies of the traffic on this machine were made, one for ''In 7/VI'', and one for the station at Halden.
[IF-149 p. 2] A member of the station at Halden, thought during TICOM interrogation that SM 2 traffic was read.
The intelligence gained from breaking of traffic of SM 1 and the simple field codes allowed Germany, during the spring manoeuvres of Feb-March 1945, to build up a complete tactical picture of the Swedish Army in two months. However, neither the high grade grille (HGA), nor the ''large'' Swedish machine was solved.
Work on Balkan (Southeastern) traffic 1941-1944
Southeastern cryptanalysis was handled at the unit by the Balkan section under the leadership of
Rudolf Bailovic and in the field, by Signal Intelligence Regiment (KONA)#Kona 4, KONA. Kona had been stationed in the
Balkans
The Balkans ( , ), corresponding partially with the Balkan Peninsula, is a geographical area in southeastern Europe with various geographical and historical definitions. The region takes its name from the Balkan Mountains that stretch throug ...
area during the entire period of the war, and in addition to its regular task of intercepting the traffic emanating from Syria and
North Africa
North Africa (sometimes Northern Africa) is a region encompassing the northern portion of the African continent. There is no singularly accepted scope for the region. However, it is sometimes defined as stretching from the Atlantic shores of t ...
, it had been given the task of monitoring the traffic of the occupied countries in the Balkan area. The Balkan countries whose systems were worked on by the ''OKH/Chi'' unit and KONA 4 were:
Greece
Greece, officially the Hellenic Republic, is a country in Southeast Europe. Located on the southern tip of the Balkan peninsula, it shares land borders with Albania to the northwest, North Macedonia and Bulgaria to the north, and Turkey to th ...
, Hungary,
Romania
Romania is a country located at the crossroads of Central Europe, Central, Eastern Europe, Eastern and Southeast Europe. It borders Ukraine to the north and east, Hungary to the west, Serbia to the southwest, Bulgaria to the south, Moldova to ...
, Yugoslavia, Albania,
Turkey
Turkey, officially the Republic of Türkiye, is a country mainly located in Anatolia in West Asia, with a relatively small part called East Thrace in Southeast Europe. It borders the Black Sea to the north; Georgia (country), Georgia, Armen ...
and Bulgaria. The work done on the traffic of each of these countries is given below.
Work on Greek traffic 1941-1944
Otto Karl Winkler provided the most information to TICOM regarding Greek ciphers and codes, from a single TICOM ''home work''. Winkler was a translator and cryptanalyst with KONA 4 from the spring of 1941 to May 1945.
According to Winkler, work on Greek systems started in 1941 when KONA 4 was stationed in Bucharest. The first system was a Hellenic Air Force, Greek Air Force system which consisted of a single transposition send in 3-letter groups. Winkler stated that nearly all messages were read by the use of stereo-typed beginnings. Although the messages were of insignificant value, a continuous check on officer personalities, deliveries of stores and information concerning airfields contributed to tactical knowledge of the Greek forces.
KONA 4 worked at this time also on Greek Army and Navy messages, but without success until the conquest of Greece. At that time, Winkler stated ''Codes'' were captured which were used by Greeks during the attack on Crete.
The only other Greek system mentioned as having been attacked in 1941 was a 5-letter code with a cyclic recipherment which Buggisch says he worked on in the unit. Plaintext traffic was becoming rapid when the Greek campaign ended.
After KONA 4 moved its evaluation centre to Athens in May 1941, no more work was undertaken on these systems until NAAS 4 Withdrawal (military), withdrew from Athens in autumn 1943. At the time, Greek Resistance, Greek Partisan traffic began to be intercepted. In the spring of 1944, KONA 4 gave Winkler the task of forming a small Greek unit to handle traffic of the traffic of the Greek People's Liberation Army (ELAS). The unit consisted of six people, chief among whom were called Strobl, a cryptanalyst who solved a double transposition system of ELAS while Winkler concentrated on translating the traffic already readable. The work became more important and the unit, now increased to 16 people, was attached to a Signal Intelligence Regiment (KONA)#Close Range Signal Intelligence Platoons (NAZ), Close Range Signal Intelligence Platoons NAZ G
Winkler stated that in the beginning the Greeks sent their traffic in two figure substitution with alternative groups. As few messages were sent on the same substitution, it took several days to break and read these codes. ELAS soon went over exclusively to letter traffic based on double transposition, which was successfully solved largely through the aid given by the carelessness of the Greek cryptographers.
Winkler estimated that 50-60% of the traffic tackled by NAZ G was solved. From these messages, the unit was able to build up an almost complete picture of the organisation and composition of the Greek People's Liberation Army and the National Liberation Front (Greece), National Liberation Front. The unit also compiled lists of leading Greek personalities and officers and informed the competent German political and military authorities about many planned military and political actions, acts of sabotage, ambushes, Dynamite, dynamiting and so on. In addition, the messages provided the exact location of Allied airfields in the Greek mountains, regarding the position, strength and activity of the Allied military missions and various British Commandos, about Greek internal and inter-allied crises and struggles, about the British tactics for the occupation of Greece.
Work on Greek systems ceased on 15 October 1944 when Naz G was transferred to Sarajevo.
Work on Hungarian traffic 1941-1944
The Hungarians used the commercial model of the Enigma cipher machine, and had the rotors for the machine made by the German firm of Konski and Krüger. This firm usually turned over the records of the rotor wirings to the Armed Forces Radio Communications Branch (Ag WNV/Fu) which in turn gave them to ''OKH/Chi''. However, Hungarians connected with the firm took the rotors at night and changed the wirings enough to make the firm's records incorrect. No effort appears to have been made on the part of ''OKH/Chi'' to recover the wirings or to prevent the sabotage. It is difficult to suppose that the unit could have been so easily duped had they wished to press the matter. Evidently, they did not consider the traffic worth causing embarrassment to the Hungarians.
With the onset of the war, however, ''OKH/Chi'' grew more cautious, particularly with the movement of German soldiers through Hungary.
During the spring and summer of 1941, the radio traffic of the Hungarian State Railways was monitored from a Feste in Tulin. The code being used at that time by the railways was a turning grille (Grille (cryptography)#Turning grilles, Raster Code) with permanent squares which could be turned in four different positions, and reversed to give four additional positions. The code was solved by Dr S. Döring of the mathematical section of ''In 7/VI''. After the check of the railway authorities had proved that they were dependable, interception was stopped.
Watch on Hungarian traffic was dropped from 1941 to 1943 due to the high priority given to Russian traffic. In 1943, however, interest again developed and a detail was sent from Signal Intelligence Regiment (KONA)#Feste 6, Feste 6, the former Army Fixed Intercept Station at Tulln an der Donau, Tulln, to Slovakia, near Bratislava (Pressburg) to monitor Hungarian traffic.
Some tenseness in the relations of Germany and Hungary may be reflected by the fact that all members of the detail wore civilian clothing. Also at that time, ''OKH/Chi'' began to resume its work on Hungarian traffic. Count Esterhazy of the Balkan section began work on a Hungarian code and turning grille. Messages enciphered with a 2-figure substitution key were also worked on.
Work on Hungarian traffic was done by the Balkan section of ''OKH/Chi'' only when the Army thought it necessary to check up on the Hungarian allies, but the attempts that were made were apparently successful. The solution in 1941 by Dr. Döring of the Hungarian grille, while not of great strategic or tactical importance, was characterised by
Otto Buggisch as ''brilliant''.
Work on Rumanian traffic 1941-1944
Very little is known of the work of the Balkan section on Rumanian traffic from 1941 to 1944. According to Mettig, the monitoring of Rumanian traffic ceased in 1941, due to the high priority given to Russian traffic and the chronic shortage of staff. However, in 1941, monitoring appears to have resumed. ''In 7/VI'' stated that Rumanian traffic was completely monitored at that time, and that the Balkan section was reading a Transposition cipher which was decoded with comparative ease.
[IF-126 p. 4] Other references to Rumanian systems were found in Herzfelds brief statement that the cryptanalysts of the Balkan section were working on Rumanian diplomatic code consisting of 5 or 6 figure groups. KONA 4 evaluation centre while stationed in Belgrade from September to December 1944 worked on Rumanian traffic.
Work on Yugoslav traffic 1941-1944
With the insistence of the German government that Yugoslavia align itself with Nazism, Nazi party policy in the spring of 1941, and the consequent wave of World War II in Yugoslavia, Yugoslav national resistance, the Balkan section of the unit and KONA 4 undertook the heavy burden on monitoring the various types of Yugoslav traffic.
These types were:
* The traffic of the friendly (to Germany) Croatian Home Guard (World War II), (Domobrani) and the Ustaše military units of the puppet government established by Germany in 1941.
* The traffic of the Chetniks under General Draža Mihailović in communication with the Yugoslav government in exile, who resisted German aggression.
* The traffic of the Yugoslav Partisans under Marshall Josip Broz Tito.
* The traffic of the Croatian Peasant Party led by Dr Vladko Maček.
When the German government established the puppet government of Croatia in 1941, the Croats were given the commercial model of the Enigma for use by the Army and Secret police (State Security Administration) The traffic of these units was read by the Balkan section currently without any delay. According to Buggisch, the solution of this traffic was not an outstanding cryptanalytic achievement for the following reasons:
* The machine used was the Enigma machine#Enigma K, Enigma K with three wheels and no stecker or Enigma machine#Plugboard, Plugboard.
* The wheels of the machine were wired for the Croats by the German firm of Konski and Krüger which habitually gave the wiring to the Armed Forces Radio Communications who gave them to ''OKH/Chi''.
* A single key was used throughout the entire Croat Army and area, and this consisted of a list of 100 settings per month.
* The ring setting () (Enigma machine#Rotors) of the wheels remained at the position of ''AAA''.
* The wheel order 1,2,3 was always used.
Just to make sure, however, Buggisch added;
:''the Germans paid for one of the first keys used, and with this decoded traffic were able to establish stereotypes and solve almost 100% of the traffic from the first.''
Although Buggisch did not recall the contents in details, he stated in interrogation that there were some interesting messages about actions against Tito. He also stated that Germany had intended equipping the Croats with the plugboard Enigma, but they had decided against this since they believed the corrupt Croats would continue to sell the keys to British agents. In that case, ''OKH/Chi'' would have to pay for the keys used by the Croats instead of solving them as they could with the commercial Enigma.
Rudolf Hentze of ''In 7/VI'' stated that the Balkan section was successful with the Transposition cipher, double transposition used by Croats but nothing is known of this system.
Herzfeld stated that the Dombrani and Ustaše used a 5-Figure code based on a former Yugoslav military code. Evidence is lacking about the actual results obtained but it is probable that the system was solved since the former code was known.
Solution of the systems of General Draža Mihailović and Marshall Josip Broz Tito was divided between a unit of Signal Intelligence Regiment (KONA)#Kona 4, KONA 4 in Belgrade and the Balkan section of ''OKH/Chi''. The breaking of easy guerilla techniques, particularly the solution of daily reciphering, was carried on at Belgrade by a special detachment, Signal Intelligence Regiment (KONA)#NAZ W, NAZ W which had served in 1941 under Wollny as an evaluation centre for Section III Armed Forces Radio Communication Branch () (AgWNV/FU III). With the assumption by the unit of work against the enemies Tito and Mihailović, the detachment came under Army control and was attached to KONA 4.
The solution of the more difficult systems was carried on at ''OKH/Chi'' by the Balkan section under the immediate supervision of
Rudolf Bailovic, who was a specialist in Slavic traffic, and a specialist in the systems of Mihailović and Tito.
Herzfeld, a member of the Balkan section of ''OKH/Chi'' from 1941 to the capitulation, had written two reports, or ''homework'' for TICOM, specifically I-52 and I-69, that has a full discussion of the Yugoslav systems worked on by that section. The traffic of Mihailović was entirely double transposition with fixed key length and key word. They were regularly, if slowly, solved at ''In 7/VI'' with the aid of stereotyped phrases, frequency charts, and other well known cryptanalytic methods. Herzfeld stated that it took one to three days to break a single message.
The systems of Tito were far more varied, most of them of Russian origin. In I-69, Herefels lists among the Tito systems broken at ''In 7/VI'' as:
* A simple letter or 2-figure substitution system used for enciphering messages sent by brigades and partisan units to Tito Division (military), divisions in 1944.
* A simple substitution key with short reciphering set used below division level in 1944.
* Simple 2-figure substitution key with nulls and short reciphering set used below division level in northern and western Yugoslavia and Bosnia (region), Bosnia in 1944, possibly also used in Serbia and Vardar Macedonia, Macedonia.
* Multi-columnar substitution key used for traffic between divisions and brigades in Slovenia, western Croatia and western Bosnia in 1944.
* An Albanian multiple substitution key used by Tito partisans of Albanian nationality (National Liberation Movement (Albania), National Liberation Movement).
* Variable substitution key with short reciphering set, the main cipher above division until June 1944.
The system which succeeded the variable substitution key with short reciphering set was called Tito's ''Novo Sifra''. It was used after June 1944 above division level and was not broken by ''In 7/VI''. Herzfeld claims that it could have been broken with sufficient traffic and close scrutiny.
For a while the new system proved secure but regional commands obviously found it cumbersome and reverted to old insecure systems. Thus the Germans could read a lot of Partisan traffic even after mid-1944. Marshall Tito had close relations with the Soviet Union and during the war he was in constant contact with Moscow through a radio link. This traffic obviously became a target for the Germans and they investigated it in 1944 without finding a theoretical solution.
In the autumn of 1944, work on Tito traffic was increased. Besides the unit stationed in Belgrade under Wollny, the Evaluation Centre of KONA 4 was moved from Athens to Belgrade and began work on Tito ciphers. NAZ G, which had been working on Greek Partisan traffic was also moved from Thessaloniki to Sarajevo to cover Yugoslav traffic.
The only reference to the work of the Balkan section of ''OKH/Chi'' on Croatian resistance movement ciphers was that they were cryptanalysed by KONA 4 and rechecked by the ''OKH/Chi'' Balkan section.
In general, it may be said that the work on Yugoslav ciphers and codes was successful. The ciphers of Tito and Mihailović formed the most important part of the work of that section with
Rudolf Bailovic performing the bulk of the work.
Work on Turkish traffic 1941-1944
Both the intercept and decoding of Turkish traffic was handled largely by signal units subordinate to KONA 4. Signal Intelligence Regiment (KONA)#NAZ T, NAZ T, which was stationed in
Graz
Graz () is the capital of the Austrian Federal states of Austria, federal state of Styria and the List of cities and towns in Austria, second-largest city in Austria, after Vienna. On 1 January 2025, Graz had a population of 306,068 (343,461 inc ...
, worked only in Turkish traffic. At first it had intercepted Turkish Naval Forces, Turkish Navy and Merchant Marine traffic as well as Turkish Land Forces and General Directorate of Security (Turkey), Police traffic, but certain disagreements arose with the Kriegsmarine over the interception of the Navy and the Marine traffic and this was abandoned.
[IF-126 p. 9]
The police traffic of Turkey is described as:
* Simple transposition used by the police departments of Ankara, Edirne, Istanbul, İzmir for police matters only
* Two letter or figure code used for police Counterintelligence, counter-intelligence with police agents
* Two or three letter code used for agent traffic
The Turkish Army codes were mainly transposition codes with a key word, sent in five letter groups preceded by a 4-figure number.
[IF-126] All these systems were decoded by NAZ T and were set to ''OKH/Chi'' simply for the purpose of checking all work.
One special Turkish code is mentioned as having been read by either ''OKH/Chi'' or NAZ T, and that was the special code used by the President of Turkey İsmet İnönü, while sailing on the State Yacht, the ''Savarona''. This code was used in 1943 for radio messages, while the President was on the yacht, and not used afterwards.
Sometime in 1942 to 1943, ''OKH/Chi'' received from the
Research Office of the Reich Air Ministry (), the mission of solving certain Turkish diplomatic traffic. This the Balkan section did under the supervision of Bailovic, with the decoded traffic being sent to the . The traffic was used by the military attaches for their reports from Russia, Bulgaria and Italy, and that it was read continually by ''In 7/VI''.
TICOM knew from other sources that this traffic proved to be a very valuable source of information concerning Russia. Mettig remembered a number of reports from the winter of 1943–1944 on the Russian military situation and the preparations for an offensive. Despite many warnings from British sources that the traffic was being read, Turkey failed to change the system, and the reading of Turkish diplomatic traffic remained a constant source of information.
Work on agents traffic 1941–1944
The Agents section of ''OKH/Chi'' was established in 1942. Before that time, the activities of this section which consisted of radio security inside Germany and monitoring of illegal transmissions had been carried out by Section III of the Armed Forces Signal Communication Group (AgWBNV), Radio Communication Group 3 () (AgWNV/FU III). The unit was subordinated to
Generalleutnant
() is the German-language variant of lieutenant general, used in some German speaking countries.
Austria
Generalleutnant is the second highest general officer rank in the Austrian Armed Forces (''Bundesheer''), roughly equivalent to the NATO ...
Fritz Thiele
Fritz Thiele (14 April 1894 – 4 September 1944) was a member of the German resistance to Nazism, German resistance who also served as the communications chief of the German Army (1935-1945), German Army during World War II. Life
Thiele was bor ...
. Thiele was succeeded by
Wilhelm Gimmler when Thiele was hanged on piano wire on 4 September 1944 at Plötzensee Prison in Berlin.
In 1942, however, it seemed necessary to establish a deciphering section specialising in agents' ciphers. Fu III wanted to set the unit up within its own organisation but the Supreme Command of the Armed Forces and the Army High Command opposed the establishment of another cryptanalytic agency. As a result of their opposition, it was agreed to set up a section for agents' traffic with an existing cryptanalytic organisation. ''In 7/VI'' was chosen as OKW could not spare the personnel, in light of the fact that ''OKH/Chi'' had previously raided OKW/Chi for personnel to establish ''In 7''. The agents section was thus attached to ''OKH/Chi'' although it appears to have maintained the close relation with Fu III, housing itself near FU III and moving with it, in November 1943 to
Jüterbog
Jüterbog () is a historic town in north-eastern Germany, in the Teltow-Fläming district of Brandenburg. It is on the Nuthe river at the northern slope of the Fläming hill range, about southwest of Berlin.
History
The Polabian Slavs, Slavic se ...
.
The agents section was commonly called the Vauck section or Vauck Referat or Referat Vauck and named after its chief cryptanalysis, cryptanlayist
Wilhelm Vauck. Mettig gave great credit to the work of Vauck saying that this section achieved good results because of Vauck's leadership and his personnel cryptanalytic successes. The section was not large consisting of about 35 people in the main section, ten at outposts in Paris and Brussels, and other cities, with eight lent to the Polish section of
OKW/Chi. Recognised traffic was decoded in the outstations, the rest was sent to Berlin. All traffic, moreover, was sent to Berlin in duplicate.
The cryptanalytic methods employed by the Vauck section differed from normal methods of solution because of the peculiar nature of the Agents' systems.When in spring 1942, when Referat Vauck started work on finding a solution to Allied agents' traffic, it was confronted with a completely new and difficult task. Success could not be achieved using the normal methods of cryptanalysis on Army or diplomatic ciphers. The peculiar construction of agents' ciphers and in particular the frequent changes of ciphers, demanded a new method of approach. Agent cryptographers had not only to be highly enthusiastic about their work and very flexible in their approach, but it was also desirable that a percentage, that was considerably higher than normal cryptography, had to be expert linguists.
The early research work of the Referat, carried out in close cooperation with the evaluation section of Fu III, was devoted to clarifying the use of
Call sign
In broadcasting and radio communications, a call sign (also known as a call name or call letters—and historically as a call signal—or abbreviated as a call) is a unique identifier for a transmitter station. A call sign can be formally as ...
s, and to ascertaining systems of
indicator
Indicator may refer to:
Biology
* Environmental indicator of environmental health (pressures, conditions and responses)
* Ecological indicator of ecosystem health (ecological processes)
* Health indicator, which is used to describe the health o ...
groups and coding tables in different procedures. Material, in the shape of old messages which had been gathered in the past, was re-examined. Simultaneously a search began for possible source of compromise within the various ciphers under investigation.
To supplement this research work an arrangement was made with the appropriate agencies to allow representatives of Referat Vauck to take part in important arrests and in the interrogation of agents. Owing to a shortage of personnel in the Referat it was impossible to take full advantage of this concession. The concession was granted as it was recognised that when an agent was arrested and no cryptographer was present, cipher material, which was usually well camouflaged, was not recognised as such and therefore could not be properly utilised. Furthermore, the material was often not evaluated correctly and delays ensued in forwarding it. Sometimes ambitious amateurs wished to earn credit for themselves by exploiting cipher material. Another danger lay in the fact that when cipher experts were not present, agents might tend to give false or imaginary cipher information. In these cases the presence of an expert was of great value. Agents under interrogation who saw that their cipher methods had been compromised usually gave good signals information. Once the value of Dr Vauck's assistance was recognised, his section were frequently called in to assist the Abwehr and Gestapo in their work.
It became possible, with the advice of Referat Vauck, either to turn around more agents, or to play back the agent's wireless personality using German personnel. Errors occurred in this field when signals personnel were not present. Thus in the beginning of 1944, it was ascertained that two allied agents, who had been turned around by the Abwehr, were operating in a villa southeast of Bordeaux and were being handed clear messages for encipherment and transmission, without any supervision.
Work on Czech agents traffic
The Vauck section worked on Agents' traffic of the Resistance in German-occupied Czechoslovakia, Czechoslovak Resistance movement. Mettig believed that the solving of the 1942-1943 of two links running to England made possible the arrest of British agents in
Czechoslovakia
Czechoslovakia ( ; Czech language, Czech and , ''Česko-Slovensko'') was a landlocked country in Central Europe, created in 1918, when it declared its independence from Austria-Hungary. In 1938, after the Munich Agreement, the Sudetenland beca ...
, one of them a captain. The greatest success was achieved by intercepting the wireless communication of the Czechoslovak Resistance movement in London. This was the only case in which Mettig is certain that it was possible for the Vauck section to solve an agent network by purely cryptanalytic means, and this was largely through breaches of security on the part of the Czech chief. After the system had been solved, the book for enciphering was found and the key recovered. In September 1942, the Czechs were about to go over to a new system, but were foolish enough to name in the old system, the book to be used for enciphering in the new system. Contents of messages solved on this link were nearly always concerned with reports on the political situation and activities of the Czech Resistance Movement, and were so important that for a long time, the W/T traffic was allowed to continue unhindered.
Work on Yugoslav agents traffic
Work on Yugoslav Agents' traffic was carried on by a detachment in Belgrade under Lt. Wollny. This detachment had been under Funkabwehr, Group III of FU III but was attached in 1942 to KONA 4 because all fighting against hostile organisations such as Draža Mihailović and Josip Broz Tito was directed by the Army. Traffic which was not solved in this detachment was sent to the Balkan section of ''OKH/Chi'' for a solution.
Work on Southern France and Spain agents traffic
Agents' traffic in southern France and Spain emanated largely from the United States, Great Britain and Spanish Republican Army who were in radio contact with stations in Spain. To cope with this traffic, a camouflaged branch station was established in Madrid and the intercepted traffic passed to Referat Vauck for processing.
Work on Soviet Union Agents traffic
Mettig knew of three important Russian Agents' networks: The Red Three (espionage), Red 3 (), the Schulze-Boysen case, named after its leader, Harro Schulze-Boysen and the two links running from Brussels. Mettig stated that these last named links were, as far as he knew, not solved. However it was known that this was the Red Orchestra (espionage)#The Trepper Group named after Leopold Trepper who eventually became a double agent, working against the Soviet Union. Mettig perhaps was not privy to this knowledge.
In addition to Mettig's account of the Red 3, two memoranda were written by Wilhelm Fenner, the chief cryptanalyst of
OKW/Chi. Fenner reported that on 23 February 1943, his agency was asked by Vauck section to collaborate in work on certain messages of Soviet agents on the Red 2 net. By the end of March, the Vauck section had furnished Fenner's cryptanalysts,
Peter Novopashenny, Trappe and Schmidt, with all the traffic in that system since September 1941 so that a start was made on a solution. Fundamental findings were communicated to ''OKH/Chi'' which enabled that organisation to solve the system roughly at the time, as did Fenner's group. After the initial solution, it was agreed that ''OKH/Chi'' should continue to work on the system, and Mettig stated that from this help the Vauck section discovered that the system was based on a book text. In the autumn of 1944, Vauck was reported to have told Mettig that the exact sending position of this net had been determined to be in Switzerland. A raid was planned but had to be cancelled as Swiss authorities had forestalled the Germans. The station, according to Metting, was evacuated and destroyed before the Germans could take action.
The story of the second Soviet net, the Shulze-Boysen net operating from Berlin in 1942, is equally dramatic. This net received its name from First lieutenant ) Harro Schulze-Boysen, whose house was the centre of a communist inspired espionage agency operating on a large scale. When the first inroad into this traffic was made by the Vauck section, Dr. Lenz, one of the members of Vauck's section, mentioned the name Schulze-Boysen to another member of the Vauck section named Haymann who frequented the Schulze-Boysen house. Haymann warned Mrs Schulze-Boysen. Subsequently, both Haymann and Dr. Lenz were arrested, and Haymann condemned to death. Lenz was released and transferred to an out-station in Paris. With the aid of knowledge obtained from decoded traffic, the Gestapo made arrests of from 79 to 80 people of whom 70 were condemned to death. The case was kept strictly secret because many of the accused were employed in various agencies and were betraying secrets to Russia.
Work on Polish resistance movement traffic
The most notable results in the Agents' section were achieved in the interception and solution of the systems used by the Polish Resistance Movement, particularly during the Warsaw Uprising, Polish uprising in
Warsaw
Warsaw, officially the Capital City of Warsaw, is the capital and List of cities and towns in Poland, largest city of Poland. The metropolis stands on the Vistula, River Vistula in east-central Poland. Its population is officially estimated at ...
in 1944. From information passed on this system, the dispositions of the Polish liberation troops as well as friction between them and the Russians could be established. It was possible, moreover, to solve all wireless traffic which the Polish government in London carried on with its organisations in Poland. In order to preserve secrecy and to insure quicker delivery of the solved message traffic, eight members of the Vauck section were transferred in the autumn of 1943 to the Polish section of ''OKW/Chi'' for work there. The Plain text was published by the ''OKW/Chi'' as Cipher Department of the High Command of the Wehrmacht#Linguistic output, Reliable Reports, with an extremely restricted distribution. To ensure complete radio intercept coverage, ''OKW/Chi'' ordered its outstation at Lauf an der Pegnitz also to intercept the traffic. Schubert, a cryptanalyst at ''GdNA'', wrote a brief account of the systems used by the Polish resistance movement in which he stated that systems 006, 117, 118 and 181 were broken and that others were worked on. Most of them were simple 2-figure substitutions used without an indicator, with some variations in development and the use of basic keys and key phrases.
Work on German traitors traffic
Mettig stated that he once saw a report concerning a German who transmitted, by wireless to England, details of a newly constructed signals shelter in Berlin urgently requesting that it be bombed. No details of these were known by TICOM.
Linguistic research 1941-1944
Linguistic research during the years 1941-1944 was carried on at the ''OKH/Chi'', by the section designated as the Linguistic Research Department (). Metting listed this section as one of the twelve sections of the original unit in 1942. Köhler was named by Mettig to manage this section in 1942 and Köhler remained head of the unit throughout the war, until November 1944, when the section was transferred from the ''GdNA'' to the ''OKW/Chi''. Mettig claimed that it was contemplated that the members of the linguistic research section would advise the cryptanalysts on language problems and direct all matters of the Armed Forces concerning foreign languages. Although the plans were never realised, the nature of the work of the section can be inferred from these plans. It was known that the section would have had an exceedingly well stocked cryptographic library, including foreign maps in a large number of scales, journals, transport time tables, foreign reference works, extensive biographies of the enemy and other important categories of information related to cryptography in a wide variety of sources.
Mathematical research 1941-1944
According to Metting, Dr.
Hans Pietsch was the Director of the Mathematical Research section. Pietsch had managed to collect the best available cryptanalysts, i.e. the best mathematical brains. The work of this section was twofold:
*The investigation of all unsolved traffic from the various sections of ''OKH/Chi'' so long as it was necessary to achieve an inroad by purely analytics means.
*The investigation of the security of current German Army systems.
To achieve these purposes, three subsections were found necessary. Subsections ''F'', ''7'' and ''13'' are described above in 5.6.1.
=Cryptanalysis work on subsection ''F'' 1941-1944
=
Subsection ''F'' of the mathematical section appears to have done some excellent work in the solution of the more simple machine systems used by foreign countries. The following are examples of solutions:
* The discovery of theoretical methods of solving traffic in the Russian K-37 cipher machine (a B-211 cipher machine, after capture of a model in 1941).
* Development of a technique for converting the relative settings, recovered for wheels of Converter
M-209 on days when such solution was possible through reading of some of the traffic, into absolute settings, thus making it possible to read all the traffic sent on those days.
* The discovery in 1943 of theoretical methods of solving messages send in the French B-211 cipher machine.
* The reading of the de Gaulle traffic enciphered by the
C-36 cipher machine.
* The solution in 1944 of the Swedish Boris Hagelin, Hagelin, the BC-38 by
Johannes Marquart and Hilburg.
Dr S. Döring's solution in 1941 of the Hungarian grille should be counted as one of the achievements of this section. As has been stated previously, this section had no success with the large cipher machines such as the British
Typex, the USA SIGABA, or the large Swedish Hagelin machine. The outstanding men of this section were named by Buggisch as Fritz Hilburg, Willi Rinow and Wuenoche.
Use of IBM in cryptanalysis 1941-1944
The
Hollerith (IBM) section of ''OKH/Chi'' was derived from the IBM section established in 1939-1940 by the ''In 7/VI'', at the suggestion of the mathematicians and former actuaries of this section, who knew Hollerith methods from civil life. It was natural that in 1942, when the study of the security of the German Army system was transferred from ''In 7/IV'' to ''In 7/VI'', the use of Hollerith (IBM) machinery for security studies was transferred to ''OKH/Chi'' and quickly adapted for cryptanalytic work on foreign systems. The machinery used by ''OKH/Chi'' was mostly of German make, although a number of captured French IBM machines were included in the unit. The Hollerith section grew considerably in the course of time, both in respect of the number of machines the unit had and of the personnel engaged. In 1943, there were perhaps 20-30 female punchers engaged and about 20-30 soldiers who were Hollerith mechanics and such like in civilian life. Baurat Schencke was in charge. Hentze stated that in 1944, there were 30 key punchers, and 2 tabulators.
Some of the bigger Hollerith machines were always being provided with special new wirings for special cryptanalytic purposes, e.g. for non-carrying addition and subtraction in codes work. Most of the tasks, however, consisted of the usual statistic (bigrams, trigrams, chain statistics (), column statistics () and of simple figure-calculations, e.g. in work on Hagelin machines. Buggisch stated that as a rule, no tasks were undertaken which could not have been carried out by hand by perhaps 100 people in a reasonable time.
=New Hollerith section
=
The limited width of the Hollerith card was soon found to be inconvenient, particularly in counting out of repeats for the purpose of lining-up () 2-cipher texts. The obvious solution appeared to be in this case to work with perforated strips and a 5-unit alphabet. Orders were given at the beginning of 1943 for the construction of such a machine. As Group VI only had a completely inadequate workshop at its disposal, and by that time it was already impossible to get any more tools, etc., an agreement was made with the Hollerith firm that a few more rooms, together with workshop machines and tools, in the factory buildings in Lichterfelde (Berlin), Lichterfelde Ost be placed at the disposal of Section VI. An engineer from the Hollerith firm was placed in charge of this new section, but was found to be unsuitable. The repeat counting machine was ready in the autumn of 1943. It worked by the Electromechanics, electromechanical principle, its speed was not considered very high, around 40 pairs of letters a second, and there was an ''idling period'' () that was considered inconvenient. Buggisch stated that when the Hollerith section was completed, none of the specialist sections performing practical cryptanalysis had any use for it, so that the question was justifiably raised as to why such an apparatus had been built at all.
=Mechanical aids
=
In late 1943 to early 1944, the workshop began to be engaged on the construction of various mechanical aids, that cannot be described as cryptanalytic machines. A machine was created that automatically punched on Hollerith Punched cards, the Soviet T/P traffic taken on perforated strips with a 5-unit alphabet. Plans were made in the spring of 1944 for machines which were to perform certain calculation tasks such as arose during work on Hagelin machines, that were considered special calculating machines. Buggisch stated that, in short, Ag N/NA (OKH/Chi) had until June 1944, when Buggisch moved to OKW/Chi, no cryptanalytic machine which could be used for the practical solution of any codes or ciphers.
=Summary
=
The major success obtained was the work on the Soviet 5-figure traffic. In the early stages of the Soviet campaign, it was comparatively simple to establish depths in these messages without the use of IBM, but by 1943 IBM machinery was indispensable for location Cryptanalysis#Depth, depths. Buggisch stated that the lack of Hollerith machinery spurred the analysts of
OKW/Chi to the development of new and better types of analytic devices while the ''OKH/Chi'' remained content with the inferior adaptations of IBM machinery. The German Army's general attitude concerning IBM machinery is hinted at in Buggisch's statement that the Enigma machine, Enigma could probably be solved by a large enough array of Hollerith machinery, but it never occurred to him, evidently, that such would be contemplated by the enemy.
Towards the end of the war, the Hollerith machinery were outworn, outmoded and irreplaceable. The factories which had been producing parts were bombed out, and as the machines wore out, their work became inaccurate. In some instances, work by machine was abandoned. Mettig cited an example, in late 1944–1945, when ''In 7/VI'', now reorganised as the GdNA, was to provide units below regimental level with signal tables. The values were to be set up by the Hollerith section, but the machine was no longer working correctly. As a result, the trigrams were not being reciprocally enciphered, so other methods of producing them had to be developed. In early 1945, the Hollerith section was offered to OKW/Chi, but Mettig stated that matter was never settled due to the confusion at the end of the war.
German Army cryptanalysis effort 1945
With the establishment of the GDNA in late 1944, all operational cryptanalysis was carried on by sections 2,3,4 of Group IV of the GdNA. There is no record of any new or difficult systems being solved after late 1944. The main effort of the GdNA was apparently directed to the deciphering of systems already solved and to the simple necessity of finding a place to operate. From February 1945 until the capitulation, Group V of the GdNA was constantly on the move seeking refuge in the south from the Allied advance.
German Army cryptographic systems
Training
Liaison
Liaison with the OKW/Chi
The relations of the GdNA and the OKW/Chi were conditioned by a number of important facts.
* The office of Chief Signal Officer of the Armed Forces () (OKW/WFSt/Chef WNV) and Chief Signal Officer Army () (OKH/Chef HNW) were combined from August 1939 to the capitulation. The close relationship which evolved from this combined office is outlined by a German officer, interrogated by Combined Services Detailed Interrogation Centre (CDSIC), who was Aide-de-camp, aide de campe to General
Albert Praun Chef WNV and Chef HNV, who held the position from September 1944 until the capitulation. As Chef WNV, General Praun and his predecessors was directly subordinated to Alfred Jodl of Armed Forces Operations Staff () (WFST) was responsible for all signal operations and policy from inter-service and policy from an inter-service point of view. As Chef HNW, Praun was responsible for signal operations and policy with the Field Army, and in this capacity was subordinate to Heinz Guderian.
* The GdNA and the OKW/Chi stemmed from a common origin, the Code and Ciphers section of the German Defense Ministry, as explained in [Ref 5.1], [Ref 4]
:The close inter-relationship of these three organisations is reflected in the relationship among the officers who controlled them. Colonel Fritz Boetzel, who was codenamed ''Olga'', in the
Lucy spy ring
The Lucy spy ring () was an anti-Nazi World War II espionage operation headquartered in Switzerland and run by Rudolf Roessler, a German refugee. Its story was only published in 1966, and very little is clear about the ring, Roessler, or the effo ...
, and passed secrets to Soviet Russia
and Chief of the GdNA, had been from 1934 to 1939 head of the Code and Cipher section of the Defense Ministry.
[I-123 p. 4] Erich Fellgiebel, who had been head of the Code and Cipher section of the Defense Ministry from 1931 to 1932 held of the office of Chef HNW and Chief Signal Officer Armed Forces (Chef WNF) from 1939 until 20 July 1944.
Colonel
Hugo Kettler who ended the war as head of OKW/Chi had also been head of HLS Ost. Lt. Col. Mettig, second in command of OKW/Chi and Director of ''OKH/In 7/VI'' from November 1941 to June 1943.
:Close collaboration of OKW/Chi and the GdNA can be traced in a number of recorded instances from 1939 to the capitulation. In 1939, Dr
Erich Hüttenhain, chief cryptanalyst of OKW/Chi was sent by that organisation to the Intercept Station of the Army at
Frankfurt
Frankfurt am Main () is the most populous city in the States of Germany, German state of Hesse. Its 773,068 inhabitants as of 2022 make it the List of cities in Germany by population, fifth-most populous city in Germany. Located in the forela ...
to collaborate with the Army on the solution of the new French Army system,[Ref Section 8]. The most cordial relationship between the organisations is manifest in his memoranda on his visit to Frankfurt. He stated:
::"When I was saying goodbye to the military head of the evaluation section of
Army Group C
Army Group C () was an army group of the German Wehrmacht during World War II. In its first deployment between 1939 and 1941, its main assignment was the defense of the Franco-German border during the Phony War and the Western Campaign, after whi ...
at the termination of my attachment in Frankfurt. the head of the evaluation section expressed his regret to me that he could not present to me with some sign of outward recognition for work successfully carried out in Frankfurt. To that I replied that success attained was not due to the effort of an individual but was the result of development and common effort and that if outward recognition should reward this work, Herrn Trappe (Chi OKW), Schmidt (chi OKW) and Professor Dr.
Ludwig Föppl
Karl Ludwig Föppl (27 February 1887 – 13 May 1976) was a German mechanical engineer who succeeded his father, August Föppl as professor of technical mechanics at the Technical University of Munich. During World War I, Föppl worked as a cr ...
should likewise be remembered. The head of the project thereupon told me that these gentlemen would be similarly distinguished. In the course of the conversation, I said that for us, the finest recognition, was the knowledge that important intelligence, which could serve as the basis for the further conduct of the war, had been sent to GHQ. The head of the project replied that he quite understood this attitute but he would like to make military departments appreciate our work at the full value, for up to now they have shown little understanding of the difficulties of such work. At the same time, the head of the project requested me to convey his thanks to the OKW/Chi for the assistance given to the military deciphering section and remarked that in his opinion such a large deciphering (deciphering) task could not be done by OKH either now or in the near future".
In 1942, OKW/Chi sent a special Soviet ''party'' to the HLS Ost to collaborate with cryptanalysts there in the solution of a Russian 5-figure code. Professor Dr.
Peter Novopashenny who was Director of the party returned to Berlin in the autumn of 1943, but his cryptanalysts were absorbed into the unit at HLS Ost.
OKW/Chi also collaborated with the Agents section of ''OKH/Chi'' [Ref 8.2.7.7] on the solution of Soviet agent traffic. The memoranda of Wilhelm Fenner, chief linguist at OKW/Chi, give a detailed picture of the nature of this collaboration.
On 23 February 1943, Fenner's department was asked by Section III of the AgWNV, i.e. Radio Communication Group 3 (AgWNV/FU III) to collaborate with the Agents' section of ''OKH/Chi'' in work on certain Soviet agents' traffic. By the end of March ''In 7/VI'' had furnished Fenner's section with all traffic in that system intercepted since September 1941, so that a start was made on solution. Fundamental findings were communicated to ''In 7/VI'', which enabled its Agents' section to break into the system roughly at the same time as did Fenner's group. After the initial solution, however, it was agreed that ''OKH/Chi'' should continue the work on this system, while the ''OKW/Chi'' started work on another system. From then on, relations became somewhat strained because of the non-cooperative traffic to Fenner's section. The basic cooperation of the two departments, however, is noteworthy.
One of the most striking instances of cooperation between the
OKW/Chi and the GdNA and ''OKH/Chi'' its predecessors is manifest in the work of the two agencies on Polish Resistance Movement Systems. During the years of 1943 and 1944, the Agents' section of AgN/NA was able to intercept and solve the systems used by the Poles in their traffic with the Polish government-in-exile in London. From this traffic the disposition of the Polish liberation troops as well as the friction between them and the Soviets could be established. The traffic was considered so important that the 8 members of the Agents' section were transferred in the autumn 1943 to the Polish section of OKW/Chi to work on solving the systems. The
Plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
was published by the ''In 7/VI'' in bulletins with extremely restricted distribution. The ''OKH/Chi'' also cooperated by intercepting this traffic at their own station at
Lauf in order to be certain that it was completely covered. Speed in solving the traffic was obtained by having the messages sent to the IBM (Hollerith) section of AgN/NA for sorting. The work on Polish traffic thus appears to have been as much a joint project as is possible for two separate agencies to attempt.
Long before the time of official ''Chi-conferences'' held by Generalleutnant
Wilhelm Gimmler, chief of the Armed Forces Communications Branch () (Chef AgWNV), the Army and the Armed Forces, Signal Intelligence Services worked together on security studies of German cryptographic machines and issued joint resolutions concerning their investigations. Among the papers of Dr.
Erich Hüttenhain of OKW/Chi are memoranda, describing this cooperation. As early as December 1942, ''OKH/Chi'', OKW/Chi, and Wa Prüf 7 proposed issuing a statement concerning improvements for the teleprinter Siemens and Halske T52, T-52c to be submitted to the ''big executive committee'' Although it is known specifically what is meant by the big executive committee, it is possible that it may have been composed of officials of these same organisations. Throughout 1943, Generalmajor
Fritz Thiele
Fritz Thiele (14 April 1894 – 4 September 1944) was a member of the German resistance to Nazism, German resistance who also served as the communications chief of the German Army (1935-1945), German Army during World War II. Life
Thiele was bor ...
, who held the position of Chief of the Army Communications Chief () (Chef AfHNW) called conferences of representatives of the various services concerning matters of security.
Otto Buggisch who worked in ''OKH/Chi'' early in the war, was one of the mathematicians of ''In 7/VI'' mentions conferences at which Dr. Karl Stein (mathematician), Karl Stein and Dr. Gisbert Hasenjaeger both of OKW/Chi were both stated to be present. The minutes of one of these conferences, dated 13 December 1943, have been published. It should be noted regarding these conferences, they were called by ''In 7/VI'', and was held in the office of that unit at Mathaikirchlatz 4, Berlin. Those who took part were Major Kempe, Fricke, Kehren, mathematicians of ''OKH/Chi'', Hans Pietsch, Döring of AgN/NA; representatives of Wa Prüf 7 and Hüttenhain, Stein and Hasenjaeger, mathematicians of ''OKW/Chi''. From this evidence, it was clear that the later ''Chi-conferences'' called by Gimmler in 1944 were only a formal exteriorisation of an already existing relationship. This was the reason that Buggisch and Hüttenhain were able to minimise the efforts of Gimmler. Both observe that the conferences did not foster a closer relationship among the services. The cooperation of Army and Armed Forces had been one of the closest nature for many years, but the collaboration with other services was not improved.
At the formal ''Chi-conferences'' and at the official Army-Air-Naval conferences of 1944, the Armed forces could always depend upon the full cooperation of the Army. The completeness of this cooperation is illustrated by the fact that when OKW/Chi was ordered to take over the supervision of all duties of all security studies within the Armed Forces, on the order of
Albert Praun, the Army compiled by transferring to OKW/Chi all personnel of ''In 7/VI'' and of the security sections of the Mathematical Section of AgN/NA.
In the field of machinery used for general cryptanalysis and security studies, the OKW/Chi (Armed Forces) and the ''In 7/VI'' (Army) appear to have informed each other fully concerning their respective developments although no exchange of machinery was made. As early as 1939 to 1940, the mathematicians and former actuaries who had been drawn (conscripted) into ''OKH/Chi'' suggested the use of
Hollerith (IBM) equipment for statistical studies. This led to an extensive use of the kit for these types of studies. When the studies were transferred from the ''In 7/IV'' to ''OKW/Chi'' in 1942, the Hollerith machine kit was developed by the unit for both security studies and cryptanalytic work. It is not known whether the OKW/Chi (Cipher Department of the High Command of the Wehrmacht#Rapid analytic machinery, OKW/Chi Machinery) had its own Hollerith section separate from those of the Army or not.
Mettig and Buggisch both state that it had no Hollerith unit, but had a certain dependency on the ''In 7/IV'' unit. It was known later, that OKW/Chi had to build its own custom machinery, as it was unable to obtain sufficient Hollerith machinery. The ''In 7/IV'' unit Hollerith kit was used at the request of the OKW/Chi for instance, when for example, the preparation of 3-Letter codes for the use of Army, was performed at the Hollerith unit. In early 1945, the Hollerith unit was offered to OKW/Chi but was never carried out. It was known that the machinery was exceedingly out of calibration, and needing extensive repairs, that were never done due to severe lack of material and resources.
The relations of the OKW/Chi and GdNA could be summarised as complete cooperation. Although the problem domains of the two units were quite distinct, with OKW/Chi dealing specifically with diplomatic traffic, the GdNA with a variety of Army and Hand ciphers and codes, joint problems were dealt with by the two agencies, and in complete accord.
The general lack of collaboration between OKW/Chi and GdNA did not point to lack of coordination at senior administrative function, nor to professional jealously between the two agencies. Essentially the two agencies had two distinct operational foci. OKW/Chi was diplomatic and OKH/Chi was a military agency. Therefore, there was little need for detailed collaboration.
Liaison with the B-Dienst
The Signal Intelligence agency of the Kriegsmarine (navy) was B-Dienst of () III of the Oberkommando der Marine (OKM/4 SKL III) or colloquially as B-Dienst, appeared to have little liaison with the GdNA and its predecessors.
Wilhelm Tranow, the chief cryptanalyst of B-Dienst, stated that the Navy cooperated with the Army until early 1944, but that thereafter the attempt at cooperation was given up since no results of value were obtained.
The collaboration, where it existed, between the two agencies dealt principally with,
M-209 and Hollerith procedures. In both instances, it so happened that the Navy received more from the Army than it gave.
* Collaboration between B-Dienst and ''In 7/VI'' began in 1943 when OKH/Chi passed over to the B-Dienst and Luftnachrichten Abteilung 350, Luftwaffe Luftnachrichten Abteilung 350, the technique of recovering true settings from relative settings in the M-209 solution. Thereafter, according to Lt. Müntz of B-Dienst there was considerable liaison between the three services in regard to M-209 and they all exchanged all techniques. Shulze another cryptanalyst with B-Dienst, stated that in his investigations of the M-209 he met Dr S. Steinberg of OKH/Chi and that they had a detailed discussion of the methods used by the German Army, Navy and Air Force for solution of this system. From these discussions, Shulze concluded that B-Dienst was superior in the matter of solving a trafficked message, the OKH/Chi in reconstructing the internal settings. This was primarily due to the OKH/Chi having more material to work on, and could depend upon having a few messages in
depth, whereas the B-Dienst never got traffic with identical settings. Schulze persuaded the OKH/Chi to give B-Dienst some M-209 material in depth with which they could carry out experiments in OKM/4 SKL III to expedite the solution of the message.
* In regard to collaboration of Hollerith procedures,
Wilhelm Tranow readily admitted that the Army first conceived of using IBM Hollerith machinery for cryptanalysis.
[I-146 p. 17] In March 1942, the B-Dienst, the Luftwaffe Luftnachrichten Abteiling 350 and Hermann Göring, Görings
Research Office of the Reich Air Ministry (FA) visited the Hollerith section of ''In 7/VI'' in Berlin. Tranow stated:
::''On this occasion, I came to the conclusion that there were enormous possibilities in the Hollerith system for our work also''
:Tranow immediately started working to obtain some of the Hollerith machinery for B-Dienst, but found it difficult at that time. From March to May 1942, B-Dienst sent work to the Naval Armaments Economic Section for processing. The Economic section agreed to do the work if Tranow could furnish his own staff. Here again Tranow had trouble, since B-Dienst had very few Hollerith specialists. Tranow was forced to approach OKW/Chi to obtain personnel in a like for like basis. By May 1942, Tranow stated that B-Dienst was able to carry out the task.
According to Mettig, however, in June 1942, OKH/Chi undertook a considerable volume of Hollerith work for B-Dienst. It seems reasonable to suppose that this was true, and that Tranow conveniently ''forgot'' this favour on the part of the OKH/Chi. In September 1944, according to a Navy document, B-Dienst was still ''collaborating'' with the Army on Hollerith procedure. Tranow never considered the matter of obtaining Hollerith to be true collaboration as it did not involve any solution to B-Dienst ciphers.
As a matter of general policy, B-Dienst High Command disapproved of indiscriminate exchanges amongst the Military cipher bureaux. Lt Müntz stated that the Director of his section Franke, disapproved of contact with other agencies, and maintained contact with OKH/Chi regarding M-209 solution matters, due to it being seen as a security risk.
Leutnant
() is the lowest junior officer rank in the armed forces of Germany ( Bundeswehr), the Austrian Armed Forces, and the military of Switzerland.
History
The German noun (with the meaning "" (in English "deputy") from Middle High German «locum ...
Schubert of GdNA stated that he personally could not bring about closer relations between the two agencies.
:''I endeavoured to achieve cooperation between OKH/Chi and B-Dienst. This task was of no concern to me. A naval officer was detached for six weeks who looked at all Army systems originating in the west and east and I went with him to attempt some settlement. I tried to collaborate but later events upset things. There are practically no points of contact between the Army and Navy''
Wilhelm Tranow of the B-Dienst knew Dr Schauffler slightly and they had once collaborated over Japanese intercepts, but Tranow never had the time to address them.
Tranow later stated that, with the Army, the Navy had few occasions to work with them. Their operational and tactical problem domains were too dissimilar to stimulate effective collaboration. Admiral Karl Dönitz, stated:
:''[he] had no knowledge of the cryptanalytic bureau's maintained by the other services and departments... As for civil bureau's, he had never tried to find out, [as] they were of no use to him''.
Liaison with the Luftwaffe Luftnachrichten Abteilung 350
Before the
Luftwaffe
The Luftwaffe () was the aerial warfare, aerial-warfare branch of the before and during World War II. German Empire, Germany's military air arms during World War I, the of the Imperial German Army, Imperial Army and the of the Imperial Ge ...
established its own Signals Intelligence Agency, (OKL/LN Abt 350), in 1937, the Army fixed Intercept Station, the Signal Intelligence Regiment (KONA)#Stationary Intercept Company (FESTE), Feste associated with Army Groups, worked with the corresponding intercepted Air Signals Abteilingen, to intercept traffic. According to Ferdinand Feichtner of the Luftwaffe, the German Army (Wehrmacht), Army did not give air traffic sufficient attention as it was required, and the Luftwaffe became increasingly dissatisfied with the Army's work. In 1936, the Luftwaffe began the formation of its own Signal Intelligence Service, although for three years, it had a close relationship with the Army. Luftwaffe airmen underwent familiarisation training at Feste units and the first Luftwaffe intercept stations were established according to the Army's prototypes. By 1939, the dependence of OKL/LN Abt 350 on the Army was ended.
During the succeeding period (1939-1945) relations between the two agencies were particularly good in field operations. This was fostered by such means as unification of signal regulations, a regular exchange of liaison officers, working personnel, equipment, reports, raw traffic and cryptanalytic methods, between the two agencies.
Minutes from a ''Chi-conference'' held in October 1944, stated that the OKH/Chi and LN Abt 350 attempted to coordinate their signal regulations. According to the minutes preserved among the papers of
Erich Hüttenhain, Generalleutnant Wilhelm Gimmler, Chef AgWNV, stated that one special difficulty in signal communications was the fact that the diverse parts of the Armed Forces used different wireless and cipher phraseology. In response to this, Lt. Col. Schulze of the Luftwaffe stated that by means of far-reaching assimilation of Heer and Luftwaffe regulations, the difficulties arising in those services from different wireless and cipher phraseology would soon be overcome. This attitude of cooperation between the Heer and the Luftwaffe is typical and extended to all echelons.
A regular exchange of liaison officers between the German Army (Wehrmacht), Heer and the
Luftwaffe
The Luftwaffe () was the aerial warfare, aerial-warfare branch of the before and during World War II. German Empire, Germany's military air arms during World War I, the of the Imperial German Army, Imperial Army and the of the Imperial Ge ...
field units was maintained both on the Eastern Front (World War II), eastern and Western Front (World War II), western fronts. In the west, from 1942, a Luftwaffe liaison officer had been stationed with Signal Intelligence Regiment (KONA)#NAAS 5, NAAS 5 of KONA 5 stationed at St. Germain. Major Hentze of KONA 5, stated that the two units worked closely together, and Hentze showed familiarity with the unit there, its complement and its work.
One of the chief duties of the OKH/Chi liaison officer at the Luftwaffe post was to keep the ground situation map up to date from Luftwaffe reports. Of the OKL/LN Abt 350 liaison officer at an OKH/Chi post, among other duties, they passed requests to Luftwaffe for support.
Friendly liaison between commanders and men of units of the Luftwaffe and Heer that were closely associated in the field was a source of contact. Muegge was commander of Signal Intelligence Regiment (KONA)#Kona 4, KONA 4 and Rosenkrantz, who was an old friend of Muegge had a Luftwaffe Signals station there. When Muegge moved to Italy in 1943 as commander of
KONA 7, Rosenkrantz was also posted to the same location.
Much of the interchange of men and equipment between field units of the Luftwaffe and Heer was caused by the fact that the Heer had no very long distance-finding sets, and depended upon equipment and reports from the Luftewaffe to compensate for this deficiency. Major Franze Oelijeschläger, Chief of III/LN. Rgt. 4, the Signal Intelligence Service of Luftflotte 4 of the Luftwaffe, with about 800 personnel, stated that the KONA regiments willingly detached direction-finding parties to reinforce the Luftwaffe effort and the Luftwaffe was always open to receive Army requests for use of D/F equipment.
[I-41 p. 3] Muegge told interrogators that as commander of
KONA 7 in Italy, he borrowed two Luftwaffe D/F sets with Longwave, long and Shortwave radio, short.
The field unit
NAA 11 stationed in Finland relied on the D/F reports from the Luftwaffe.
Intelligence of all types were exchanged at every level. Army Group HQ received from the local Luftwaffe office the ''Immediate Reports'', the ''Daily Reports'' and the ''Fortnightly Reports''.
Liaison with Pers Z S
There were few examples of collaboration between the GdNA and Pers Z S at the senior administrative level. Dr
Otto Buggisch, formerly of Inspektorate 7/VI and later OKW/Chi, gave the only available information to TICOM. Dr Buggisch worked in the French language group in ''OKH/Chi'' from November 1941 until August 1942 and during this period he collaborated with Dr Kunze on a five-digit DeGaulle code. He also worked with Kunze regarding the Swiss Enigma General Alfred Jodl, Chief of the Armed Forces Operations Staff (
Oberkommando der Wehrmacht
The (; abbreviated OKW ː kaːˈveArmed Forces High Command) was the Command (military formation), supreme military command and control Staff (military), staff of Nazi Germany during World War II, that was directly subordinated to Adolf ...
) stated he did not receive any decodes as they went directly to the Foreign minister, but knew in a general way Pers Z S professionalism and commitment. The general lack of collaboration between Pers Z S and ''In 7/Vi'' did not point to lack of coordination at senior administrative function, nor to professional jealously between the two agencies. Essentially the two agencies had two distinct operational foci. Pers Z S was diplomatic and OKH/Chi was a military agency. Therefore, there was little need for detailed collaboration.
Liaison with the
Liaison between the and ''In 7/VI'' was characterised in general by narrowness of approach and mutual animosity of feeling. This was true, apparently at every level. Alfred Jodl, Chief of Operations of the Armed Forces, told interrogators that he knew little of
Hermann Göring
Hermann Wilhelm Göring (or Goering; ; 12 January 1893 – 15 October 1946) was a German Nazism, Nazi politician, aviator, military leader, and convicted war criminal. He was one of the most powerful figures in the Nazi Party, which gov ...
's
Research Office of the Reich Air Ministry ():
:"..it was a large office and efficiently organised, but Göring's special affair, he only knew about it from conversation and indirect hearsay. There seemed to him to be a great deal of duplication going on."
Buggisch of ''In 7'' stated that this was because Mettig, Director of ''In 7/VI'' from 1941 to 1943, was opposed to the Storm Trooper taint of the Research Bureau. Sauerbier of the RLM/, claimed that narrowness of the Directors of the , affected relations of that organisation with other bureaux, including the GdNA.
[I-162 p. 4]
Whenever liaison did occur, it was via a single representative, and never involved any exchange of visits. Klautsche, who was the RLM/ liaison officer after 1943, maintained an office at the OKW/Chi and passed material to the B-Dienst,
Luftwaffe
The Luftwaffe () was the aerial warfare, aerial-warfare branch of the before and during World War II. German Empire, Germany's military air arms during World War I, the of the Imperial German Army, Imperial Army and the of the Imperial Ge ...
and
German Army
The German Army (, 'army') is the land component of the armed forces of Federal Republic of Germany, Germany. The present-day German Army was founded in 1955 as part of the newly formed West German together with the German Navy, ''Marine'' (G ...
. Klautsche is said to have passed on intelligence material to the Army General Staff, Western Armies Branch and Eastern Armies Branch.
The lack of contact between personnel of the (FA) and the GdNA was very apparent from interrogations. Fricke, who was a prominent mathematician in ''OKH/Chi'' who was later transferred to ''OKW/Chi'', stated that he had never seen any personnel from the until the war was over and they turned up in prison camps. Kurt Sauerbier of the stated under interrogation that he did not know a single person in another cipher bureau.
There are a few instances of cooperation between the two agencies, but
Otto Buggisch insisted it was very rare.
Liaison with Finland
The main Finnish unit was the RTK, the ''Radio Telepgraf Kompanie''. Liaison with Finland was always close, both at HLS Ost, and in the eastern field units. Formal liaison at HLS Ost was maintained by a Finnish liaison officer stationed there, in
Giżycko
Giżycko (former or ''Łuczany''; ) is a town in northeastern Poland with 28,597 inhabitants as of December 2021. It is situated between Lake Kisajno and Lake Niegocin in the region of Masuria, within the Warmian-Masurian Voivodeship. It is ...
(Lotzen). This officer from 1942 onwards was a Lt. Mikko, and he was succeeded by Oberleutnant Ohn. The Finnish General Staff is said to have passed a copy of the Soviet 5-Figure cipher book to Germany, that was used in the first year of the war. OKH/Chi had a high opinion of Finnish cryptanalysts. Alexis Dettman stated that he had visited Finland in 1942, and had a very high opinion of the cipher bureau. Dettman had exchanged technical letters ever since that time. Liaison in the field is known in some detail from the reports of NAA 11, when it was subordinated to a unit in Finland. The first German Liaison officer to Finland was Hauptmann
Johannes Marquart, who would later be Director of Referat Ia of Group IV of the GdNA and was later succeeded by Oberleutnant Riemerschmidt, stationed at Sortavala. Riemerschmidt had a direct link to
NAA 11.
Liaison on all cryptographic matters was excellent. The liaison between NAA 11 and the Finns was divided into several types, including traffic liaison, cryptographic liaison and technical liaison. Results were exchanged every two or three days and NAA 11 varied its cryptographic priorities to give full attention to any special links required by the Finns, the request coming via Riemerschmidt. The Finnish crypt personnel were considered outstanding and the exchange of great benefit to NAA 11. Riemerschmidt also passed to NAA 11 information and solutions received at Sortavala from the LNA itself, and on one occasion, (the captured RZ 18000 code), this was faster than the direct transmission from LNA to NAA 11. The Finns solved 3Z and 4Z code extensively with emphasis on NKWD material. The Finns has no success with 5Z traffic and never captured any copies of these codes.
Finnish traffic analysis () was rated less highly. It was thought that this was due to the Finnish success with solving codes. Although they had about 20 men in the sector, they did not work systematically nor were they adept at grasping intelligence from the analysis of small amounts of traffic. Thus NAA 11 was able to give more than they got in this respect.
Technical liaison was also handled by Riemerschmidt and was far more helpful to RTK than to NAA 11. Finnish equipment was mostly German, with some British and American receiver units. Germany gave the Finns much advice but no physical help. On one occasion they put their own apparatus and men at the disposal of a Russian offensive, but otherwise there was no pooling or sharing of equipment. Much of the Finnish equipment was pre-1939, and old Marconi Electronic Systems, Marconi D/F equipment.
Liaison with Italy
Liaison between Germany and Italy was negligible as Germany had a complete lack of confidence in the Italians.
Liaison with Japan
According to all evidence, there was very little liaison between the Army and Japan. In 1943, two Japanese officers visited HLS Ost at
Giżycko
Giżycko (former or ''Łuczany''; ) is a town in northeastern Poland with 28,597 inhabitants as of December 2021. It is situated between Lake Kisajno and Lake Niegocin in the region of Masuria, within the Warmian-Masurian Voivodeship. It is ...
(Lotzen) for about half a day. According to Lt. Alexis Dettmann, of Referat III of Group IV, they were given a polite reception but shown very little of anything and were give no hints as to what solutions the OKH/Chi had reached on Russian traffic. The Japanese officials stated that they had solved the Russian ''OKK 6'' and ''OKK 7'' but just what help they provided the OKH/Chi, on these systems was not mentioned. Buggisch emphatically stated that he had never seen any Japanese ''in the flesh'' and knew of no liaison with Japan.
At the end of the war, Germany had decided to send a cryptologic mission to Japan by submarine. Including among the officers were Major Opitz, a German intercept officer, Schubert of HLS Ost and Morgenroth, a B-Dienst cryptanalyst. How little they knew about the Japanese Intelligence agencies is shown by the fact that they did not know whom they were to contact when they arrived in Japan, but were to ask the German Counter Intelligence unit in Japan for further instructions. The plan was not carried out due to the end of the war.
Notes
References
Citations
Bibliography
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
TICOM and CSDIC reports
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
*
External links
German Radio Intelligence by Lieutenant-General Albert Praun
{{DEFAULTSORT:General der Nachrichtenaufklarung
Cryptography organizations
History of telecommunications in Germany
Signals intelligence agencies of World War II
Research and development in Nazi Germany
Military history of Germany during World War II

 * Agn/Gen. der. Nachr. Aufkl – Fritz Boetzel
* Chief of Staff () – Andrea
*
* Agn/Gen. der. Nachr. Aufkl – Fritz Boetzel
* Chief of Staff () – Andrea
*  During the early years of World War II, substantial change occurred within the German Army signal intelligence service. The main developments were:
* The intercept service mission was narrowed to include only Army Traffic. With the formation of OKW/Chi, the signals intelligence agency of the Supreme Command of the Armed Forces, in 1939, OKW/Chi took over all diplomatic intercept traffic. To help facilitate message interception, the Army transferred two interception stations at Lauf and Treuenbrietzen.
* The intercept service expanded. In 1939, the Army established two new branch stations for the intercept of foreign Army communications from the east. The branch stations were created as
During the early years of World War II, substantial change occurred within the German Army signal intelligence service. The main developments were:
* The intercept service mission was narrowed to include only Army Traffic. With the formation of OKW/Chi, the signals intelligence agency of the Supreme Command of the Armed Forces, in 1939, OKW/Chi took over all diplomatic intercept traffic. To help facilitate message interception, the Army transferred two interception stations at Lauf and Treuenbrietzen.
* The intercept service expanded. In 1939, the Army established two new branch stations for the intercept of foreign Army communications from the east. The branch stations were created as 
 In October 1944, the various organisations of the German Army signal intelligence service was completely changed again, through the amalgamation of the three central agencies. The ''In 7/VI'' (later AgN/NA), the LNA, and HLS Ost was combined into one central cryptanalytic and evaluation agency: OKH/GDNA. This combined unit was the logical result of the retreat of HLS Ost together with the German Army, from East Prussia to Zeppelin bunker near Zossen where ''In 7/VI'' and LNA were situated.
The KONA signal intelligence regiments were not greatly affected by the amalgamation of the central agencies into the GdNA, although the KONA units did come under closer centralised control in matters of administration and signal intelligence policy. The main change to the Armies field organisations in 1944 were brought on by the Allied invasion of France in June 1944. To cope with the situation, KONA 6 was moved from the eastern front to the western, and a Senior Commander of the Signal Intelligence () () was created to coordinate and control KONA 5 and KONA 6. In late 1944 and early 1945, two additional KONA regiments were created, KONA 8 and KONA Nord, but it is worth noting that these KONA regiments were largely borrowed from other eastern front regiments, and were not a mark of expansion, merely a redeployment to areas under stress.
Colonel Boetzel, chief of the OKH/GdNA stated that KONA 4 was transferred to the west at the end of the war. A captured document indicated that KONA 4 had been succeeded by a signal battalion, () () 16, in February 1945 but did not mention its transfer to the west. It is probable that the KONA disintegrated and that various parts were sent to the different fronts.
The organisation of the signal intelligence service at the end of World War II consisted of the following:
* The Signal Intelligence Agency of the Army High Command (OKH/GdNA), a central cryptanalytic and evaluation agency for all traffic.
* A Senior Commander of the Signal Intelligence (Hoeh Kdr d NA) with control over the KONA stationed in the west and responsibility for all the
In October 1944, the various organisations of the German Army signal intelligence service was completely changed again, through the amalgamation of the three central agencies. The ''In 7/VI'' (later AgN/NA), the LNA, and HLS Ost was combined into one central cryptanalytic and evaluation agency: OKH/GDNA. This combined unit was the logical result of the retreat of HLS Ost together with the German Army, from East Prussia to Zeppelin bunker near Zossen where ''In 7/VI'' and LNA were situated.
The KONA signal intelligence regiments were not greatly affected by the amalgamation of the central agencies into the GdNA, although the KONA units did come under closer centralised control in matters of administration and signal intelligence policy. The main change to the Armies field organisations in 1944 were brought on by the Allied invasion of France in June 1944. To cope with the situation, KONA 6 was moved from the eastern front to the western, and a Senior Commander of the Signal Intelligence () () was created to coordinate and control KONA 5 and KONA 6. In late 1944 and early 1945, two additional KONA regiments were created, KONA 8 and KONA Nord, but it is worth noting that these KONA regiments were largely borrowed from other eastern front regiments, and were not a mark of expansion, merely a redeployment to areas under stress.
Colonel Boetzel, chief of the OKH/GdNA stated that KONA 4 was transferred to the west at the end of the war. A captured document indicated that KONA 4 had been succeeded by a signal battalion, () () 16, in February 1945 but did not mention its transfer to the west. It is probable that the KONA disintegrated and that various parts were sent to the different fronts.
The organisation of the signal intelligence service at the end of World War II consisted of the following:
* The Signal Intelligence Agency of the Army High Command (OKH/GdNA), a central cryptanalytic and evaluation agency for all traffic.
* A Senior Commander of the Signal Intelligence (Hoeh Kdr d NA) with control over the KONA stationed in the west and responsibility for all the  Before the war,
Before the war,  This organisation of OKH/GdNA was in effect from November 1944 to the end of the war. Approximately 700 people were employed by the unit.
*''Headquarters Unit''. The HQ unit of OKH/GDNA, was managed by () (colonel) Fritz Boetzel, his chief of staff, (lieutenant colonel) Andrea, the Adjutant Lieutenant Moravec and staff officer Lieutenant () Koebe. As well as all staff being subordinate to the unit, the unit also controlled two intercept stations, Feste 6 and Feste 11 ( KONA Unit), who specialised in intercepting
This organisation of OKH/GdNA was in effect from November 1944 to the end of the war. Approximately 700 people were employed by the unit.
*''Headquarters Unit''. The HQ unit of OKH/GDNA, was managed by () (colonel) Fritz Boetzel, his chief of staff, (lieutenant colonel) Andrea, the Adjutant Lieutenant Moravec and staff officer Lieutenant () Koebe. As well as all staff being subordinate to the unit, the unit also controlled two intercept stations, Feste 6 and Feste 11 ( KONA Unit), who specialised in intercepting  With the opening of the
With the opening of the  The Soviet Union state used various military cryptographic systems in order to secure its communication. Two organisations prepared and evaluated cipher procedures. This was the
The Soviet Union state used various military cryptographic systems in order to secure its communication. Two organisations prepared and evaluated cipher procedures. This was the  Interrogations of personnel from Feste 10 and KONA 1: ''By the time of Stalingrad practically every Army engaged in the battle had its own 3-digit cipher.'' Dettman and Samsonov do not discuss any 3-digit codes as such, so it must be assumed that they considered these types of codes similar to the 2-digit PT series, and did not warrant discussion as a special sub-type.
Interrogations of personnel from Feste 10 and KONA 1: ''By the time of Stalingrad practically every Army engaged in the battle had its own 3-digit cipher.'' Dettman and Samsonov do not discuss any 3-digit codes as such, so it must be assumed that they considered these types of codes similar to the 2-digit PT series, and did not warrant discussion as a special sub-type.
 Soon afterwards the letters of the alphabet were put in their alphabetic position in the book. See Fig V.
Besides the above types of codes, syllabic codes contained few words but practically all the possible syllables which could be formed out of 2 or 3 letters. All codes of this kind which were broken were alphabetic. See Fig. VII
Soon afterwards the letters of the alphabet were put in their alphabetic position in the book. See Fig V.
Besides the above types of codes, syllabic codes contained few words but practically all the possible syllables which could be formed out of 2 or 3 letters. All codes of this kind which were broken were alphabetic. See Fig. VII
 After some months, the strictly alphabetic nature of the books was given up and the alphabeticity only maintained within the area of a letter. The numbers were at the same time distributed at random over the page. See Fig VI. The book could have 1000 groups, but Oberleutnant Schubert stated that the average number of groups was 300–800, stating: '' in general small scope, but frequent change.'' If the codes were smaller than 1000 groups, alternatives were given either to pages or first figures of the lines. The substitutions could be constructed without any recognizable system or they could be made up from a Latin square, with the square usually lasting about one month, although with the Air Force, it sometimes lasted longer. Schubert stated that towards the end of the war, there appeared quite isolated 4 to 7-digit substitution, presumably private systems of the respective cipher departments, but appeared very seldom.
From the beginning of 1943, most 3-digit codes no longer contained single letters but used the initial letter of the words for this purpose. In order to indicate which meaning was to be used two groups were introduced:
:: 736 1) Read the initial letter
:: 737 2) Read the whole word
After some months, the strictly alphabetic nature of the books was given up and the alphabeticity only maintained within the area of a letter. The numbers were at the same time distributed at random over the page. See Fig VI. The book could have 1000 groups, but Oberleutnant Schubert stated that the average number of groups was 300–800, stating: '' in general small scope, but frequent change.'' If the codes were smaller than 1000 groups, alternatives were given either to pages or first figures of the lines. The substitutions could be constructed without any recognizable system or they could be made up from a Latin square, with the square usually lasting about one month, although with the Air Force, it sometimes lasted longer. Schubert stated that towards the end of the war, there appeared quite isolated 4 to 7-digit substitution, presumably private systems of the respective cipher departments, but appeared very seldom.
From the beginning of 1943, most 3-digit codes no longer contained single letters but used the initial letter of the words for this purpose. In order to indicate which meaning was to be used two groups were introduced:
:: 736 1) Read the initial letter
:: 737 2) Read the whole word
 The 3-digit groups were read in the order of page-line. The recipher of 3-digit ciphers was as varied as in the case of 2-figure ciphers. Each figure was re-enciphered separately. This is to say, for the page numbers, a hatted order of the figures 1 to 0 was substituted. Thus Page 1 became 4, 2 became 6 and so on. Fig. VIII.
3-digit code ''R3ZC'' which was mentioned by Corporal A. Faure of NAA 11 and was discovered as part of the Norway codes. It was a code with 10 pages of 100 positions each, 10 x 10 alphabetically arranged. One column of each page, the 8th was empty. Only the 100's and 10's figures of each group were reciphered.
The 3-figure code, it is clear from all interrogations, was mainly used by the Army, but also by the Air Forces. According to a report by Uffz. Karrenberg of Group VI, on regimental networks and for less important messages on the level of assault armies, mainly the 3-digit codes (with a 2-digit Latin square encipherment) was used. KONA 1 personnel stated that every Army Group down to Battalion had its own 3-digit code.
A good deal of
The 3-digit groups were read in the order of page-line. The recipher of 3-digit ciphers was as varied as in the case of 2-figure ciphers. Each figure was re-enciphered separately. This is to say, for the page numbers, a hatted order of the figures 1 to 0 was substituted. Thus Page 1 became 4, 2 became 6 and so on. Fig. VIII.
3-digit code ''R3ZC'' which was mentioned by Corporal A. Faure of NAA 11 and was discovered as part of the Norway codes. It was a code with 10 pages of 100 positions each, 10 x 10 alphabetically arranged. One column of each page, the 8th was empty. Only the 100's and 10's figures of each group were reciphered.
The 3-figure code, it is clear from all interrogations, was mainly used by the Army, but also by the Air Forces. According to a report by Uffz. Karrenberg of Group VI, on regimental networks and for less important messages on the level of assault armies, mainly the 3-digit codes (with a 2-digit Latin square encipherment) was used. KONA 1 personnel stated that every Army Group down to Battalion had its own 3-digit code.
A good deal of  3-Figure (3-Digit, or 3-F) Address codes were used in conjunction with 5-Digit messages to enable wireless stations to ensure that messages arrived at their proper destination. Their construction was similar to that of the PT-39 or PT-42 codes, described above, but they contained only figures, unit designations, authorities, words such as ''for'' or ''from''. See Fig X.
Example of an address:
A code of this type was first used at the beginning of 1944 on the 1st and 2nd Ukrainian and the 1st White Russian Fronts for communications between their Army Groups and their respective Armies and independent Corps. In the summer of 1944 armies began to use similar codes with their subordinates units and latterly the use of such codes increased still further.
The solution to these codes, given a fair amount of material, was generally easy. They were often simpler than the example given in Fig. X and sometimes appeared in the form of straightforward lists with each meaning numbered consecutively of 100 pages instead of 10. See Fig XI.
The same variations in construction occur as with three-figure.
* Alphabetic with the letters of the alphabet grouped at the end of the Code.
* Each letter of the alphabet placed before the part devoted to words beginning with that letter.
* Semi-hatted, i.e. with all the words beginning with one letter grouped together but the groups in random order.
* Letters of the alphabet with alternatives.
* Syllabic Codes (with words distributed over the code).
* Letters of the alphabet with alternatives.
:* Read the initial letter.
:* Read the word.
* With the two groups directly above appearing several times, often on each page.
Codes had anything from 5 to 100 pages. The Air Force Codes usually had about 10,000 groups and the Army 5000 or fewer. According to members of KONA 1, the solution of these codes given a fair amount of material, was generally easy. Members of the NAA 11 stated the following:
:''Addresses to personal names rather than titles were common in all Russian traffic and this suggested the use of initials. The vagueness of this answer surprised the interrogator who asked if the addresses, being enciphered on the PT table, were not read currently. The answer was that unless the same address was used frequently and some outside hint was given they were unusually unable to read the address. They supposed it used values which had special local meanings added to the table.''
3-Figure (3-Digit, or 3-F) Address codes were used in conjunction with 5-Digit messages to enable wireless stations to ensure that messages arrived at their proper destination. Their construction was similar to that of the PT-39 or PT-42 codes, described above, but they contained only figures, unit designations, authorities, words such as ''for'' or ''from''. See Fig X.
Example of an address:
A code of this type was first used at the beginning of 1944 on the 1st and 2nd Ukrainian and the 1st White Russian Fronts for communications between their Army Groups and their respective Armies and independent Corps. In the summer of 1944 armies began to use similar codes with their subordinates units and latterly the use of such codes increased still further.
The solution to these codes, given a fair amount of material, was generally easy. They were often simpler than the example given in Fig. X and sometimes appeared in the form of straightforward lists with each meaning numbered consecutively of 100 pages instead of 10. See Fig XI.
The same variations in construction occur as with three-figure.
* Alphabetic with the letters of the alphabet grouped at the end of the Code.
* Each letter of the alphabet placed before the part devoted to words beginning with that letter.
* Semi-hatted, i.e. with all the words beginning with one letter grouped together but the groups in random order.
* Letters of the alphabet with alternatives.
* Syllabic Codes (with words distributed over the code).
* Letters of the alphabet with alternatives.
:* Read the initial letter.
:* Read the word.
* With the two groups directly above appearing several times, often on each page.
Codes had anything from 5 to 100 pages. The Air Force Codes usually had about 10,000 groups and the Army 5000 or fewer. According to members of KONA 1, the solution of these codes given a fair amount of material, was generally easy. Members of the NAA 11 stated the following:
:''Addresses to personal names rather than titles were common in all Russian traffic and this suggested the use of initials. The vagueness of this answer surprised the interrogator who asked if the addresses, being enciphered on the PT table, were not read currently. The answer was that unless the same address was used frequently and some outside hint was given they were unusually unable to read the address. They supposed it used values which had special local meanings added to the table.''
 Two forms of four-letter codes first appeared in practice traffic between Army Groups and Armies and Independent Corps of the
Two forms of four-letter codes first appeared in practice traffic between Army Groups and Armies and Independent Corps of the  From the middle of 1944, a word code was used in the area of the
From the middle of 1944, a word code was used in the area of the 
 The ''R4 Z C 1800'' code, had since October 1943 had 50 pages, each consisting of 50 lines and totalling 2,500 clear groups, alphabetically arranged. Each page is shifted by means of Cipher square () and the
The ''R4 Z C 1800'' code, had since October 1943 had 50 pages, each consisting of 50 lines and totalling 2,500 clear groups, alphabetically arranged. Each page is shifted by means of Cipher square () and the