Aircrack-ng on:
[Wikipedia]
[Google]
[Amazon]
Aircrack-ng is a network software suite consisting of a detector,
 Wired Equivalent Privacy was the first security
Wired Equivalent Privacy was the first security



 packetforge-ng can create and modify packets for injection. It supports packets such as arp requests, UDP, ICMP and custom packets. It was originally written by Martin Beck.
packetforge-ng can create and modify packets for injection. It supports packets such as arp requests, UDP, ICMP and custom packets. It was originally written by Martin Beck.
packet sniffer
A packet analyzer (also packet sniffer or network analyzer) is a computer program or computer hardware such as a packet capture appliance that can Traffic analysis, analyze and Logging (computing), log traffic that passes over a computer netwo ...
, WEP and WPA/ WPA2-PSK cracker and analysis tool for 802.11 wireless LAN
A wireless LAN (WLAN) is a wireless computer network that links two or more devices using wireless communication to form a local area network (LAN) within a limited area such as a home, school, computer laboratory, campus, or office building ...
s. It works with any wireless network interface controller
Wireless communication (or just wireless, when the context allows) is the transfer of information (''telecommunication'') between two or more points without the use of an electrical conductor, optical fiber or other continuous guided med ...
whose driver supports raw monitoring mode and can sniff 802.11a, 802.11b and 802.11g traffic. Packages are released for Linux
Linux ( ) is a family of open source Unix-like operating systems based on the Linux kernel, an kernel (operating system), operating system kernel first released on September 17, 1991, by Linus Torvalds. Linux is typically package manager, pac ...
and Windows
Windows is a Product lining, product line of Proprietary software, proprietary graphical user interface, graphical operating systems developed and marketed by Microsoft. It is grouped into families and subfamilies that cater to particular sec ...
.
Aircrack-ng is a fork of the original Aircrack project. It can be found as a preinstalled tool in many security-focused Linux distributions such as Kali Linux
Kali Linux is a Linux distribution designed for digital forensics and penetration testing. It is maintained and funded by Offensive Security. The software is based on the Debian''Testing'' branch: most packages Kali uses are imported from the De ...
or Parrot Security OS, which share common attributes, as they are developed under the same project (Debian
Debian () is a free and open-source software, free and open source Linux distribution, developed by the Debian Project, which was established by Ian Murdock in August 1993. Debian is one of the oldest operating systems based on the Linux kerne ...
).
Development
Aircrack was originally developed by French security researcher Christophe Devine. Its main goal was to recover 802.11 wireless networks WEP keys using an implementation of the Fluhrer, Mantin and Shamir (FMS) attack alongside the ones shared by a hacker named KoreK. Aircrack was forked by Thomas D'Otreppe in February 2006 and released as Aircrack-ng (Aircrack Next Generation).Wi-Fi security history
WEP
algorithm
In mathematics and computer science, an algorithm () is a finite sequence of Rigour#Mathematics, mathematically rigorous instructions, typically used to solve a class of specific Computational problem, problems or to perform a computation. Algo ...
to be released, with the intention of providing data confidentiality comparable to that of a traditional wired network. It was introduced in 1997 as part of the IEEE 802.11 technical standard and based on the RC4 cipher and the CRC-32 checksum
A checksum is a small-sized block of data derived from another block of digital data for the purpose of detecting errors that may have been introduced during its transmission or storage. By themselves, checksums are often used to verify dat ...
algorithm for integrity
Integrity is the quality of being honest and having a consistent and uncompromising adherence to strong moral and ethical principles and values.
In ethics, integrity is regarded as the honesty and Honesty, truthfulness or of one's actions. Integr ...
.
Due to U.S. restrictions on the export of cryptographic algorithms, WEP was effectively limited to 64- bit encryption. Of this, 40 bits were allocated to the key and 24 bits to the initialization vector
In cryptography, an initialization vector (IV) or starting variable is an input to a cryptographic primitive being used to provide the initial state. The IV is typically required to be random or pseudorandom, but sometimes an IV only needs to be un ...
(IV), to form the RC4 key. After the restrictions were lifted, versions of WEP with a stronger encryption were released with 128 bits: 104 bits for the key size
In cryptography, key size or key length refers to the number of bits in a key used by a cryptographic algorithm (such as a cipher).
Key length defines the upper-bound on an algorithm's security (i.e. a logarithmic measure of the fastest known a ...
and 24 bits for the initialization vector, known as WEP2.
The initialization vector works as a seed
In botany, a seed is a plant structure containing an embryo and stored nutrients in a protective coat called a ''testa''. More generally, the term "seed" means anything that can be Sowing, sown, which may include seed and husk or tuber. Seeds ...
, which is prepended to the key. Via the key-scheduling algorithm (KSA), the seed is used to initialize the RC4 cipher's state. The output of RC4's pseudo random generation algorithm (PRGA) follows a XOR operation in combination with the plaintext
In cryptography, plaintext usually means unencrypted information pending input into cryptographic algorithms, usually encryption algorithms. This usually refers to data that is transmitted or stored unencrypted.
Overview
With the advent of comp ...
, and produces the ciphertext
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext ...
.
The IV is constrained to 24 bits, which means that its maximum values are 16,777,216 (224), regardless of the key size. Since the IV values will eventually be reused and collide (given enough packets and time), WEP is vulnerable to statistical attacks. William Arbaugh notes that a 50% chance of a collision exists after 4823 packets.
In 2003, the Wi-Fi Alliance
The Wi-Fi Alliance is a non-profit organization that owns the Wi-Fi trademark. Manufacturers may use the trademark to brand products certified for Wi-Fi interoperability. It is based in Austin, Texas.
History
Early IEEE 802.11, 802.11 product ...
announced that WEP had been superseded by Wi-Fi Protected Access
Wi-Fi Protected Access (WPA) (Wireless Protected Access), Wi-Fi Protected Access 2 (WPA2), and Wi-Fi Protected Access 3 (WPA3) are the three security certification programs developed after 2000 by the Wi-Fi Alliance to secure wireless computer n ...
(WPA). In 2004, with the ratification of the full 802.11i standard (i.e. WPA2), the IEEE declared that both WEP and WEP2 have been deprecated.
WPA
Wi-Fi Protected Access
Wi-Fi Protected Access (WPA) (Wireless Protected Access), Wi-Fi Protected Access 2 (WPA2), and Wi-Fi Protected Access 3 (WPA3) are the three security certification programs developed after 2000 by the Wi-Fi Alliance to secure wireless computer n ...
(WPA) was designed to be implemented through firmware updates rather than requiring dedicated hardware. While still using RC4 at its core, it introduced significant improvements over its predecessor. WPA included two modes: WPA-PSK (WPA Personal) and WPA Enterprise.
WPA-PSK (Wi-Fi Protected Access Pre-Shared Key), also known as WPA Personal, used a variant of the Temporal Key Integrity Protocol
Temporal Key Integrity Protocol (TKIP ) is a security protocol used in the IEEE 802.11 wireless networking standard. TKIP was designed by the IEEE 802.11i task group and the Wi-Fi Alliance as an interim solution to replace Wired Equivalent Privac ...
(TKIP) encryption protocol. It improved security by implementing the following features:
*A 56-bit cryptographic message integrity code (MIC) called ''Michael'', compared to the 32-bit CRC-32 used in WEP.
* An initialization vector
In cryptography, an initialization vector (IV) or starting variable is an input to a cryptographic primitive being used to provide the initial state. The IV is typically required to be random or pseudorandom, but sometimes an IV only needs to be un ...
(''IV) sequencing discipline'' designed to prevent replay attacks.
* A ''key mixing function'' to defeat a class of attacks on WEP.
* A ''rekeying method'' to prevent key reuse.
TKIP allocated 48 bits to the IV compared to the 24 bits of WEP, so the maximum number is 281,474,976,710,656 (248).
In WPA-PSK, each packet was individually encrypted using the IV information, the MAC address
A MAC address (short for medium access control address or media access control address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment. This use i ...
, and the pre-shared key as inputs. The RC4 cipher was used to encrypt the packet content with the derived encryption key.
Additionally, WPA introduced WPA Enterprise, which provided enhanced security for enterprise-level networks. WPA Enterprise employed a more robust authentication mechanism known as Extensible Authentication Protocol (EAP). This mode required the use of an Authentication Server (AS) such as RADIUS
In classical geometry, a radius (: radii or radiuses) of a circle or sphere is any of the line segments from its Centre (geometry), center to its perimeter, and in more modern usage, it is also their length. The radius of a regular polygon is th ...
(Remote Authentication Dial-In User Service) to validate user credentials and grant access to the network.
In 2015, the Wi-Fi Alliance recommended in a technical note that network administrators should discourage the use of WPA and that vendors should remove support for it and rely instead on the newer WPA2 standard.
WPA2
WPA2 (Wi-Fi Protected Access 2) was developed as an upgrade to the original WPA standard and ratified in 2004, and became mandatory for Wi-Fi certified products in 2006. Like WPA, WPA2 provides two modes: WPA2-PSK (WPA2 Personal) and WPA2 Enterprise. Unlike WPA, WPA2-PSK uses the more secureAdvanced Encryption Standard
The Advanced Encryption Standard (AES), also known by its original name Rijndael (), is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001.
AES is a variant ...
(AES) in CCM mode
CCM mode (counter with cipher block chaining message authentication code; counter with CBC-MAC) is a mode of operation for cryptographic block ciphers. It is an authenticated encryption algorithm designed to provide both authentication and con ...
(Counter-Mode-CBC-MAC Protocol), instead of TKIP. AES provides stronger authentication, encryption and is less vulnerable to attacks. A backward compatible version, called WPA/WPA2 (Personal) still made use of TKIP.
WPA2-PSK replaces the message integrity code ''Michael'' with CCMP.
Timeline of the attacks
WEP
In 1995, before the WEP standard was available, computer scientist David Wagner of thePrinceton University
Princeton University is a private university, private Ivy League research university in Princeton, New Jersey, United States. Founded in 1746 in Elizabeth, New Jersey, Elizabeth as the College of New Jersey, Princeton is the List of Colonial ...
discussed a potential vulnerability in RC4.
In March 2000, a presentation by Dan Simon, Bernard Aboba, and Tim Moore of Microsoft
Microsoft Corporation is an American multinational corporation and technology company, technology conglomerate headquartered in Redmond, Washington. Founded in 1975, the company became influential in the History of personal computers#The ear ...
provided a summary of 802.11 vulnerabilities. They noted that denial of service
In computing, a denial-of-service attack (DoS attack) is a cyberattack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host co ...
deauthentication attacks are possible because the messages are unauthenticated and unencrypted (later implemented by the aireplay-ng tool). In addition, they wrote that because some implementations of WEP derive the key from a password, dictionary attacks are easier than pure brute force.
In May 2001, William A. Arbaugh of the University of Maryland
The University of Maryland, College Park (University of Maryland, UMD, or simply Maryland) is a public land-grant research university in College Park, Maryland, United States. Founded in 1856, UMD is the flagship institution of the Univ ...
presented his inductive chosen-plaintext attack
A chosen-plaintext attack (CPA) is an attack model for cryptanalysis which presumes that the attacker can obtain the ciphertexts for arbitrary plaintexts.Ross Anderson, ''Security Engineering: A Guide to Building Dependable Distributed Systems'' ...
against WEP with the conclusion that the protocol is vulnerable to packet forgery.
In July 2001, Borisov et al. published a comprehensive paper on the status of WEP and its various vulnerabilities.
In August 2001, in the paper ''Weaknesses in the Key Scheduling Algorithm of RC4'', authors Scott Fluhrer, Itsik Mantin, and Adi Shamir
Adi Shamir (; born July 6, 1952) is an Israeli cryptographer and inventor. He is a co-inventor of the Rivest–Shamir–Adleman (RSA) algorithm (along with Ron Rivest and Len Adleman), a co-inventor of the Feige–Fiat–Shamir identification sc ...
performed a cryptoanalysis of the KSA, citing Wagner among others. They stated that they had not conducted an attack against WEP, and therefore couldn't claim that WEP was vulnerable. However, other researchers implemented the attack and were able to demonstrate the protocol's insecurity.
In 2004, a hacker using the pseudonym KoreK posted a series of attacks on the NetStumbler.org forum, which were incorporated into the original aircrack 1.2 by Christophe Devine. That same month, aircrack began supporting replay attacks against WEP, which use ARP requests to generate more IVs and make key recovery easier.
Later that year, KoreK released the Chopchop attack, an active packet injector for WEP. The name of the attack derives from its inherent working: a packet is intercepted, "chops" off a part of it and sends a modified version to the Access Point, who will drop it if not valid. By repeatedly trying multiple values, the message can gradually be decrypted. The Chopchop attack was later improved by independent researchers.
In 2005, security researcher Andrea Bittau presented the paper ''The Fragmentation Attack in Practice.'' The homonymous attack exploits the fact that WEP splits the data into smaller fragments, which are reassembled by the receiver. Taking advantage of the fact that at least part of the plaintext of some packets may be known, and that the fragments may have the same IV, data can be injected at will, flooding the network to statistically increase the chances of recovering the key.
In April 2007 a team at the Darmstadt University of Technology
Darmstadt () is a city in the States of Germany, state of Hesse in Germany, located in the southern part of the Frankfurt Rhine Main Area, Rhine-Main-Area (Frankfurt Metropolitan Region). Darmstadt has around 160,000 inhabitants, making it the ...
in Germany
Germany, officially the Federal Republic of Germany, is a country in Central Europe. It lies between the Baltic Sea and the North Sea to the north and the Alps to the south. Its sixteen States of Germany, constituent states have a total popu ...
presented a new attack, named "PTW" (from the researchers' names, Pyshkin, Tews, Weinmann). It decreased the number of initialization vectors or IVs needed to decrypt a WEP key and has been included in the aircrack-ng suite since the 0.9 release.
WPA
The first known attack on WPA was described by Martin Beck and Erik Tews in November 2008. They described an attack against TKIP in the paper ''Practical Attacks Against WEP and WPA''. The proof of concept resulted in the creation of ''tkiptun-ng''. In 2009, their attack was improved and demonstrated by a research group from Norway.Features
The aircrack-ng software suite includes:aircrack-ng
aircrack-ng supports cracking WEP ( FMS, PTW, KoreK and dictionary attacks), WPA/WPA2 and WPA2 keys (using dictionary attacks). While it doesn't support direct attacks on WPA3 (introduced in 2018), it has been used successfully in combination with a downgrade attack.airbase-ng
airbase-ng incorporates techniques for attacking clients, instead of Access Points. Some of its features include an implementation of the Caffe Latte attack (developed by security researcher Vivek Ramachandran) and the Hirte attack (developed by Martin Beck). The WEP Hirte attack is a method of creating an Access Point with the same SSID of the network to be exploited (similar to an evil twin attack). If a client (that was previously connected to the victim's access point) is configured to automatically reconnect, it will try the rogue AP. At this point, ARP packets are sent in the process of obtaining a local IP address, and airbase-ng can collect IVs that can later be used by aircrack-ng to recover the key.
aireplay-ng
aireplay-ng is aninjector
An injector is a system of ducting and nozzles used to direct the flow of a high-pressure fluid in such a way that a lower pressure fluid is Entrainment (hydrodynamics), entrained in the jet and carried through a duct to a region of higher pres ...
and frame replay tool. Deauthentication attacks are supported. Deauthentication refers to a feature of IEEE 802.11 which is described as "sanctioned technique to inform a rogue station that they have been disconnected from the network". Since this management frame doesn't need to be encrypted and can be generated knowing only the client's MAC address
A MAC address (short for medium access control address or media access control address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment. This use i ...
, aireplay-ng can force a client to disconnect and capture the handshake
A handshake is a globally widespread, brief greeting or parting tradition in which two people grasp one of each other's hands, and in most cases, it is accompanied by a brief up-and-down movement of the grasped hands. Customs surrounding hands ...
(or to perform a Denial of service
In computing, a denial-of-service attack (DoS attack) is a cyberattack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host co ...
attack). In addition, a client deauthentication and subsequent reconnection will reveal a hidden SSID.
Other features include the ability to perform fake authentification, ARP request replay, fragmentation attack, the Caffe Latte and Chopchop attacks.
airmon-ng
airmon-ng can place supported wireless cards in monitor mode. Monitor mode refers to a provision in the IEEE 802.11 standard for auditing and design purposes, in which a wireless card can capture packets in air range. It is able to detect potential programs that could interfere with proper operation and kill them.
airodump-ng
airodump-ng is apacket sniffer
A packet analyzer (also packet sniffer or network analyzer) is a computer program or computer hardware such as a packet capture appliance that can Traffic analysis, analyze and Logging (computing), log traffic that passes over a computer netwo ...
. It can store information in various formats, making it compatible with software other than the aircrack-ng suite. It supports channel-hopping.
airserv-ng
airserv-ng is a wireless card server, which allows multiple wireless programs to use a card independently.airtun-ng
Virtual tunnel interface creator. Its main uses are monitoring the traffic as anintrusion detection system
An intrusion detection system (IDS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any intrusion activity or violation is typically either reported to an administrator or collec ...
, and inject arbitrary traffic in a network.
besside-ng
A tool to automatize WEP cracking and logging of WPA handshakes.easside-ng
easside-ng is an automated tool which attempts connection to a WEP Access Point without knowing theencryption key
A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic algorithm, can encode or decode cryptographic data. Based on the used method, the key ...
. It uses the fragmentation attack and a remote server (which can be hosted with the tool ''buddy-ng'') in the attempt to recover an encrypted packet, exploiting the AP which will decrypt it for the attacker.
tkiptun-ng
tkiptun-ng is a WPA/ TKIP attack tool developed by Martin Beck.wesside-ng
wesside-ng is a proof of concept based on the tool ''wesside'', originally written by Andrea Bittau to demonstrate his fragmentation attack. It is a tool designed to automate the process of recovering a WEP key.airdecap-ng
airdecap-ng decrypts WEP or WPA encrypted capture files with known key. It was formally known as airunwep and 802ether.airdecloak-ng
airdecloak-ng can remove WEP cloaked frames from pcap files. Cloaking refers to a technique for use by wireless intrusion prevention systems (which rely on WEP encryption) to inject packets encrypted with random keys into the air, in the attempt to make cracking more difficult.airolib-ng
airolib-ng can create a database of pre-computed hash tables by computing the Pairwise Master Keys (PMK) captured during the 4-way handshaking process. In WPA and WPA2, the PMK are derived from the password selected by the user, the SSID name, its length, the number of hashing iterations, and the key length. During the 4-way handshaking process, the PMK is used, among other parameters, to generate a Pairwise Transient Key (PTK), which is used to encrypt data between the client and Access Point. The hash tables can be reused, provided the SSID is the same. Pre-computed tables for the most common SSIDs are available online.
besside-ng-crawler
Performs operations on a directory to search for pcap files and filter out relevant data.buddy-ng
buddy-ng is a tool used in conjunction with the tool easside-ng, running on a remote computer. It is the receiving end that allows a packet decrypted by the access point to be captured.ivstools
ivstools can extract initialization vectors from a capture file (.cap).kstats
kstats is a tool for displaying the Fluhrer, Mantin and Shamir attack algorithm votes for an IVS dump with a given WEP key.makeivs-ng
makeivs-ng is a testing tool used to generate an IVS file with a given WEP key.packetforge-ng
 packetforge-ng can create and modify packets for injection. It supports packets such as arp requests, UDP, ICMP and custom packets. It was originally written by Martin Beck.
packetforge-ng can create and modify packets for injection. It supports packets such as arp requests, UDP, ICMP and custom packets. It was originally written by Martin Beck.
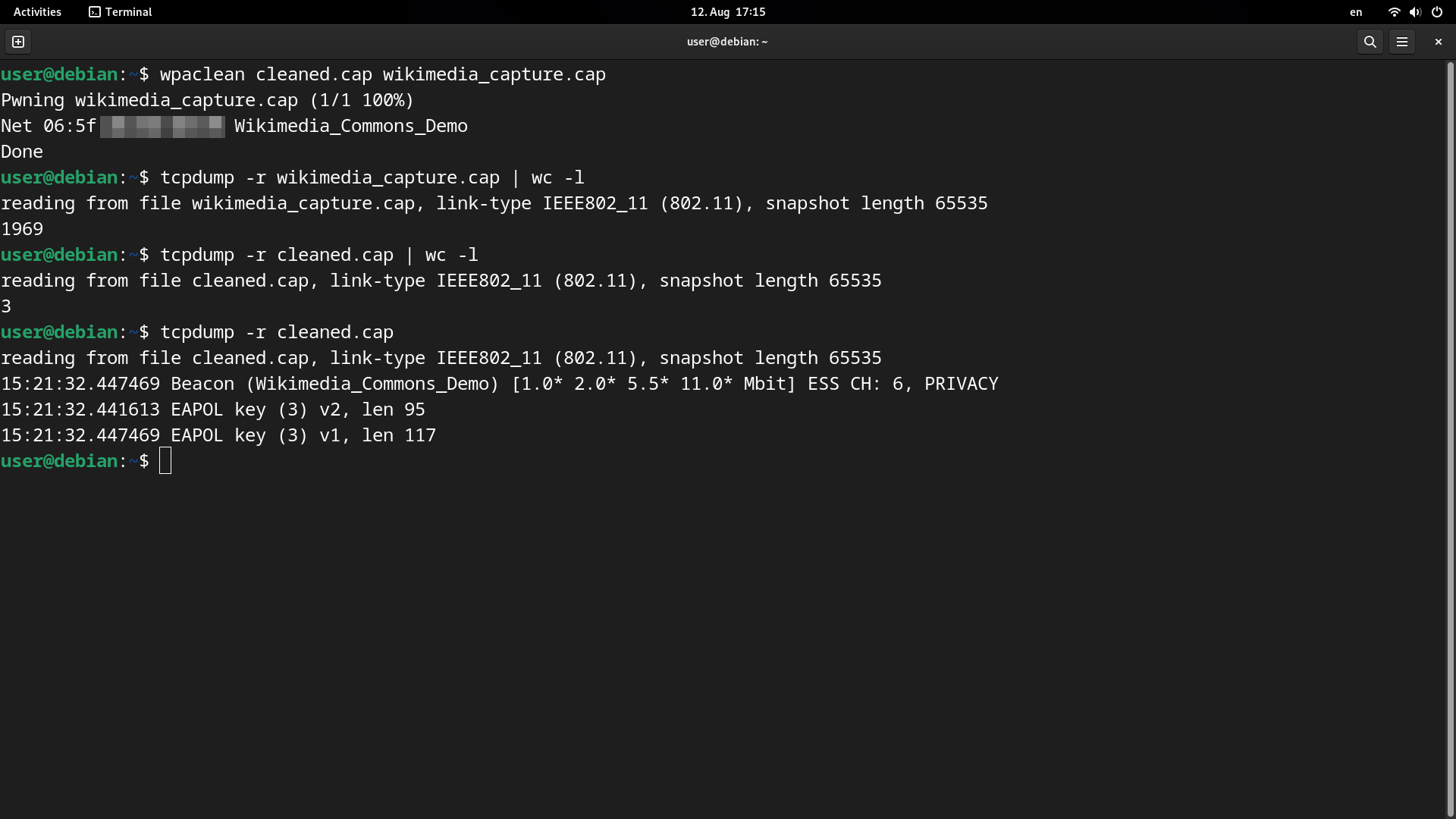
wpaclean
wpaclean reduces the contents of the capture file (generated by airodump-ng) by keeping only what is related to the 4-wayhandshake
A handshake is a globally widespread, brief greeting or parting tradition in which two people grasp one of each other's hands, and in most cases, it is accompanied by a brief up-and-down movement of the grasped hands. Customs surrounding hands ...
and a beacon. The former refers to a cryptographic process that establishes encryption without publicly revealing the key. Meanwhile, the beacon frame is sent by the Access Point to announce its presence and other information to nearby clients.
airventriloquist-ng
airventriloquist-ng is a tool that can perform injection on encrypted packets.Version history
See also
*Kali Linux
Kali Linux is a Linux distribution designed for digital forensics and penetration testing. It is maintained and funded by Offensive Security. The software is based on the Debian''Testing'' branch: most packages Kali uses are imported from the De ...
(Linux distribution for digital forensics
Digital forensics (sometimes known as digital forensic science) is a branch of forensic science encompassing the recovery, investigation, examination, and analysis of material found in digital devices, often in relation to mobile devices and com ...
and penetration test
A penetration test, colloquially known as a pentest, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system; this is not to be confused with a vulnerability assessment. The test is perform ...
ing)
** BackTrack, its predecessor
* TCP sequence prediction attack
Notes
References
External links
* {{Official website, https://www.aircrack-ng.org/ Network analyzers Free security software Cryptanalytic software Cryptographic attacks Password cracking software