|
Overlay Network
An overlay network is a logical computer network that is protocol layering, layered on top of a physical network. The concept of overlay networking is distinct from the traditional model of OSI model, OSI layered networks, and almost always assumes that the underlay network is an IP network of some kind. Some examples of overlay networking technologies are, VXLAN, Border Gateway Protocol, BGP VPNs, and IP over IP technologies, such as Generic Routing Encapsulation, GRE, IPSEC tunnels, or SD-WAN. Structure Node (networking), Nodes in an overlay network can be thought of as being connected by virtual or logical links, each of which corresponds to a path, perhaps through many physical links, in the underlying network. For example, distributed systems such as peer-to-peer networks are overlay networks because their nodes form networks over existing network connections. The Internet was originally built as an overlay upon the telephone network, while today (through the advent of V ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Network
A computer network is a collection of communicating computers and other devices, such as printers and smart phones. In order to communicate, the computers and devices must be connected by wired media like copper cables, optical fibers, or by wireless communication. The devices may be connected in a variety of network topologies. In order to communicate over the network, computers use agreed-on rules, called communication protocols, over whatever medium is used. The computer network can include personal computers, Server (computing), servers, networking hardware, or other specialized or general-purpose Host (network), hosts. They are identified by network addresses and may have hostnames. Hostnames serve as memorable labels for the nodes and are rarely changed after initial assignment. Network addresses serve for locating and identifying the nodes by communication protocols such as the Internet Protocol. Computer networks may be classified by many criteria, including the tr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Resilience (network)
High availability (HA) is a characteristic of a system that aims to ensure an agreed level of operational performance, usually uptime, for a higher than normal period. There is now more dependence on these systems as a result of modernization. For example, to carry out their regular daily tasks, hospitals and data centers need their systems to be highly available. Availability refers to the ability of the user to access a service or system, whether to submit new work, update or modify existing work, or retrieve the results of previous work. If a user cannot access the system, it is considered ''unavailable from the user's perspective''. The term ''downtime'' is generally used to refer to describe periods when a system is unavailable. Resilience High availability is a property of network resilience, the ability to "provide and maintain an acceptable level of service in the face of faults and challenges to normal operation." Threats and challenges for services can range from sim ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Private Network
Virtual private network (VPN) is a network architecture for virtually extending a private network (i.e. any computer network which is not the public Internet) across one or multiple other networks which are either untrusted (as they are not controlled by the entity aiming to implement the VPN) or need to be isolated (thus making the lower network invisible or not directly usable). A VPN can extend access to a private network to users who do not have direct access to it, such as an office network allowing secure access from off-site over the Internet. This is achieved by creating a link between computing devices and computer networks by the use of network tunneling protocols. It is possible to make a VPN secure to use on top of insecure communication medium (such as the public internet) by choosing a tunneling protocol that implements encryption. This kind of VPN implementation has the benefit of reduced costs and greater flexibility, with respect to dedicated communication li ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
MPLS
Multiprotocol Label Switching (MPLS) is a routing technique in telecommunications networks that directs data from one node to the next based on labels rather than network addresses. Whereas network addresses identify endpoints, the labels identify established paths between endpoints. MPLS can encapsulate packets of various network protocols, hence the ''multiprotocol'' component of the name. MPLS supports a range of access technologies, including T1/ E1, ATM, Frame Relay, and DSL. Role and functioning In an MPLS network, labels are assigned to data packets. Packet-forwarding decisions are made solely on the contents of this label, without the need to examine the packet itself. This allows one to create end-to-end circuits across any type of transport medium, using any protocol. The primary benefit is to eliminate dependence on a particular OSI model data link layer (layer 2) technology, and eliminate the need for multiple layer-2 networks to satisfy different types of traffic. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Packet Switching
In telecommunications, packet switching is a method of grouping Data (computing), data into short messages in fixed format, i.e. ''network packet, packets,'' that are transmitted over a digital Telecommunications network, network. Packets consist of a header (computing), header and a payload (computing), payload. Data in the header is used by networking hardware to direct the packet to its destination, where the payload is extracted and used by an operating system, application software, or Protocol stack, higher layer protocols. Packet switching is the primary basis for data communications in computer networks worldwide. During the early 1960s, American engineer Paul Baran developed a concept he called ''distributed adaptive message block switching'', with the goal of providing a fault-tolerant, efficient routing method for telecommunication messages as part of a research program at the RAND Corporation, funded by the United States Department of Defense. His ideas contradicted t ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Asynchronous Transfer Mode
Asynchronous Transfer Mode (ATM) is a telecommunications standard defined by the American National Standards Institute and International Telecommunication Union Telecommunication Standardization Sector (ITU-T, formerly CCITT) for digital transmission of multiple types of traffic. ATM was developed to meet the needs of the Broadband Integrated Services Digital Network as defined in the late 1980s, and designed to integrate telecommunication networks. It can handle both traditional high-throughput data traffic and Real-time computing, real-time, low-latency content such as telephony (voice) and video.ATM Forum, The User Network Interface (UNI), v. 3.1, , Prentice Hall PTR, 1995, page 2. ATM is a cell switching technology, providing functionality that combines features of circuit switching and packet switching networks by using asynchronous communication, asynchronous time-division multiplexing.McDysan (1999), p. 287. ATM was seen in the 1990s as a competitor to Ethernet and networ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Frame Relay
Frame Relay (FR) is a standardized wide area network (WAN) technology that specifies the Physical layer, physical and data link layers of digital telecommunications channels using a packet switching methodology. Frame Relay was originally developed as a simplified version of the X.25 system designed to be carried over the emerging Integrated Services Digital Network (ISDN) networks. X.25 had been designed to operate over normal telephone lines that were subject to noise that would result in lost data, and the protocol featured extensive error correction to address this. ISDN offered dramatically lower error rates, in effect zero, and the extensive error correction overhead was no longer needed. The new protocol suite was essentially a cut-down X.25 with no error correction, leading to lower overhead, better channel efficiency, and often significantly overall higher performance than X.25. Like X.25, Frame Relay is normally used in a circuit switched layout, where connections betw ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Telecommunication Network
A telecommunications network is a group of nodes interconnected by telecommunications links that are used to exchange messages between the nodes. The links may use a variety of technologies based on the methodologies of circuit switching, message switching, or packet switching, to pass messages and signals. Multiple nodes may cooperate to pass the message from an originating node to the destination node, via multiple network hops. For this routing function, each node in the network is assigned a network address for identification and locating it on the network. The collection of addresses in the network is called the address space of the network. Examples of telecommunications networks include computer networks, the Internet, the public switched telephone network (PSTN), the global Telex network, the aeronautical ACARS network, and the wireless radio networks of cell phone telecommunication providers. Network structure this is the structure of network general, every teleco ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
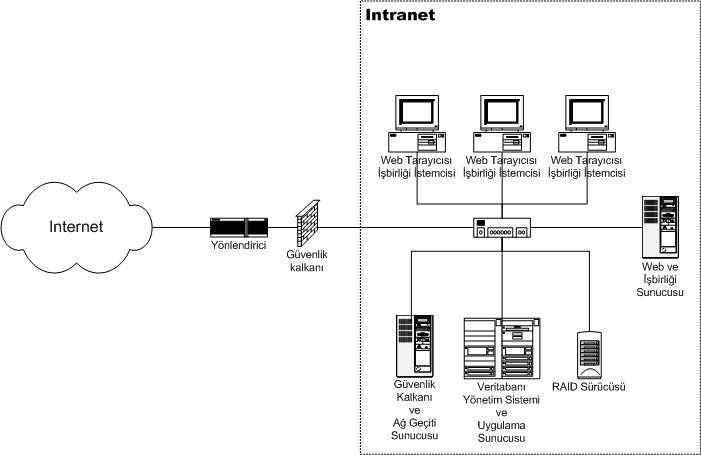
Enterprise Private Network
An intranet is a computer network for sharing information, easier communication, collaboration tools, operational systems, and other computing services within an organization, usually to the exclusion of access by outsiders. The term is used in contrast to public networks, such as the Internet, but uses the same technology based on the Internet protocol suite. An organization-wide intranet can constitute an important focal point of internal communication and collaboration, and provide a single starting point to access internal and external resources. In its simplest form, an intranet is established with the technologies for local area networks (LANs) and wide area networks (WANs). Many modern intranets have search engines, user profiles, blogs, mobile apps with notifications, and events planning within their infrastructure. An intranet is sometimes contrasted to an extranet. While an intranet is generally restricted to employees of the organization, extranets may also be accesse ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Kubernetes Cluster
Kubernetes (), also known as K8s is an open-source container orchestration system for automating software deployment, scaling, and management. Originally designed by Google, the project is now maintained by a worldwide community of contributors, and the trademark is held by the Cloud Native Computing Foundation. The name ''Kubernetes'' originates from the Greek κυβερνήτης (kubernḗtēs), meaning 'governor', 'helmsman' or 'pilot'. ''Kubernetes'' is often abbreviated as ''K8s'', counting the eight letters between the ''K'' and the ''s'' (a numeronym). Kubernetes assembles one or more computers, either virtual machines or bare metal, into a cluster which can run workloads in containers. It works with various container runtimes, such as containerd and CRI-O. Its suitability for running and managing workloads of all sizes and styles has led to its widespread adoption in clouds and data centers. There are multiple distributions of this platform – from independent softwa ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Virtual Machine
In computing, a virtual machine (VM) is the virtualization or emulator, emulation of a computer system. Virtual machines are based on computer architectures and provide the functionality of a physical computer. Their implementations may involve specialized hardware, software, or a combination of the two. Virtual machines differ and are organized by their function, shown here: * ''System virtual machines'' (also called full virtualization VMs, or SysVMs) provide a substitute for a real machine. They provide the functionality needed to execute entire operating systems. A hypervisor uses native code, native execution to share and manage hardware, allowing for multiple environments that are isolated from one another yet exist on the same physical machine. Modern hypervisors use hardware-assisted virtualization, with virtualization-specific hardware features on the host CPUs providing assistance to hypervisors. * ''Process virtual machines'' are designed to execute computer programs ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Wide Area Network
A wide area network (WAN) is a telecommunications network that extends over a large geographic area. Wide area networks are often established with leased telecommunication circuits. Businesses, as well as schools and government entities, use wide area networks to relay data to staff, students, clients, buyers and suppliers from various locations around the world. In essence, this mode of telecommunication allows a business to effectively carry out its daily function regardless of location. The Internet may be considered a WAN. Many WANs are, however, built for one particular organization and are private. WANs can be separated from local area networks (LANs) in that the latter refers to physically proximal networks. Design options The textbook definition of a WAN is a computer network spanning regions, countries, or even the world. However, in terms of the application of communication protocols and concepts, it may be best to view WANs as computer networking technologies used ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |